Shopping centre security
SAFR, a pioneer in AI-powered security solutions, announced the launch of SAFR® Guard, a powerful new product purpose-built for the Retail Loss Prevention and Asset Protection market. Designed to prevent shoplifting and retail crime before it happens, SAFR Guard makes shopping better and safer for both customers and employees. SAFR Guard delivers unmatched accuracy, speed, and simplicity while also respecting consumer privacy. SAFR’s proven AI platform SAFR Guard brin...
Anyone who has been in a proverbial cave for the last couple of years faced a language barrier at this year’s ISC West 2025 trade show. The industry’s latest wave of innovation has brought with it a new bounty of jargon and buzzwords, some of which I heard at ISC West for the first time. As a public service, we are happy to provide the following partial glossary to promote better understanding of the newer terms. (Some are new to the security industry but have been around in the IT...
Hailo, the pioneering provider of edge AI processors, will demonstrate smart security cameras empowered by its vision processing units (VPUs) as well as video management systems empowered by its AI accelerators at ISC West 2025 in Las Vegas, Nevada at booth #31065 of the Venetian Expo. At the heart of Hailo’s showcase is its full suite of AI processors, including the Hailo-15 vision processors, which integrate seamlessly into pioneering security cameras to deliver superior image quality a...
iDenfy, a globally recognised pioneer in regulatory technology specialising in identity verification (KYC), anti-money laundering (AML), and business verification (KYB), introduced its new KYC solution for Shopify merchants. The new app is listed on Shopify as a user-friendly, no-code solution for Shopify users who don’t want to build an ID verification solution from scratch. Automated verification system iDenfy’s integration provides online businesses with an automated verificati...
As Taiwan's security industry continues to evolve with technological advancements and increased diversification, various vertical markets are poised for significant growth. Secutech, scheduled for 7–9 May 2025 at the Taipei Nangang Exhibition Centre, aims to capitalise on this burgeoning demand. Around 400 international and local exhibitors are set to showcase the latest technologies and solutions across six zones and pavilions at the fair, which serves as a vital platform to connect secu...
Retailers now often find themself in a precarious situation. Profit margins are being squeezed by widespread shoplifting: The Council on Criminal Justice reports that between the first half of 2023 and the first half of 2024, shoplifting reports increased by 24%. Meanwhile, the strategies used by shops to deal with this situation are alienating consumers and affecting total sales. Andy Jassy, the CEO of Amazon, stated during an earnings call that customers are now purchasing more pharmaceutica...
News
Omada by TP-Link and VIGI by TP-Link, TP-Link Systems Inc.’s exclusive business solutions brands, are set to make waves at ISC West 2025 with the debut of their groundbreaking unified networking and surveillance solutions. At the event, the brands will showcase a seamless integration of VIGI’s cutting-edge surveillance solutions, Omada’s comprehensive networking systems, and the Omada Central platform—a revolutionary cloud-based solution that unifies the management of networking and surveillance under one roof. Secure & scalable Focused exclusively on the B2B market, Omada and VIGI deliver reliable, secure, and intuitive networking and surveillance products tailored to the unique needs of SMBs and enterprises. Designed to address diverse scenarios—including retail, hospitality, offices, MDUs, and outdoor environments—Omada and VIGI empower businesses to enhance security, streamline operations, and drive efficiency. Unified networking and surveillance solutions Integrating networking and surveillance into a single platform, TP-Link eliminates the system managment complecity By integrating networking and surveillance into a single platform, TP-Link eliminates the complexity of managing multiple systems. This unified approach enables unified management; easy deployment and setup; and remote troubleshooting, reducing operational overhead while enhancing efficiency, scalability, and security for businesses across industries. Omada Central is the cornerstone of TP-Link’s unified approach, offering a single platform to manage both Omada networking devices and VIGI surveillance systems. This next-generation solution enables businesses to seamlessly manage gateways, switches, access points, and security surveillance equipment across multiple locations. Simplified Management It simplifies setup with intelligent device recognition, auto surveillance VLAN, and Zero-Touch Provisioning while reducing total cost of ownership with a single-vendor solution. The platform also offers a free version, Omada Central Essentials, making it accessible for businesses of all sizes. VIGI: professional surveillance solutions VIGI provides professional, reliable, and comprehensive surveillance solutions tailored for businesses. Offering a diverse product range—including bullet, turret, dome, and fisheye cameras, 4/8/16/32/64-channel NVRs, 90W/180W solar power systems, cloud and local VMS, and user-friendly apps—VIGI ensures robust security while enhancing operational efficiency and profitability. VIGI offers a comprehensive range of durable cameras designed to deliver guaranteed high-quality images. The product lineup includes: 180° Panoramic 4K Cameras with Red-Blue Warning Lights Dual-Lens Stitching 4K Cameras 4G Outdoor Cameras with 3 LAN Ports AI ISP-Powered ColorPro 2.0 Cameras 5X Optical Zoom Cameras Complementing these cameras are 64-Channel H.265+ NVRs featuring 4 SATAs with a up to 64TB storage capability and 320Mbps incoming/outgoing bandwidth. Additionally, VIGI’s easy-to-install and stable solar power solution ensures long standby performance, making it ideal for off-grid locations. VIGI CVM System VIGI’s Cloud Video Management System (VMS) provides free, centralised management for multiple sites, leveraging AWS-based reliability and zero-touch maintenance to reduce on-site troubleshooting costs and ensure seamless surveillance. Complementing this is VIGI’s NPU-powered AI technology, offering advanced detection and analysis capabilities such as Behavior and Object Detection; People and Vehicle Attributes Analysis; and Precise People Counting. Together, these innovations deliver smarter, more efficient security solutions that enhance operational efficiency and drive business success. Omada: Comprehensive Networking Solutions Omada delivers a complete set of SDN solutions, designed to meet the needs of businesses With a full portfolio that includes access points, gateways, hardware controllers, cloud controllers, and a diverse range of switches, Omada provides end-to-end networking solutions tailored for scalability, performance, and ease of management. Omada’s full lineup of Wi-Fi 7 access points redefine wireless connectivity, offering unparalleled speed and reliability for both indoor and outdoor environments. Complementing these are Outdoor 4G Wi-Fi Gateways and connectivity solutions, such as the Outdoor PoE Switch and Wireless Long-Range PtMP/PtP Bridge, which ensure reliable networking even in remote or challenging locations. The switch portfolio spans from unmanaged switches for plug-and-play simplicity to easy-managed switches and advanced L3/L2 + switches, catering to businesses of all sizes and complexities. Effortless surveillance connectivity The Agile Series of Easy Managed PoE Switches with Free Cloud, designed specifically for surveillance systems. Paired with Omada Central Essentials for free cloud access, the Agile Series features Auto IP Camera/NVR Recognition, Extend Mode for PoE up to 250m, enhanced PoE Auto Recovery, and Remote Troubleshooting Tools with Cable Test, Reboot PoE Port Management, and SSH to minimise downtime, making it an ideal choice for businesses seeking efficient and scalable networking solutions tailored to surveillance needs. Seamless connectivity Omada & VIGI unified networking and surveillance solutions are tailored to meet the needs of diverse industries, including retail, hospitality, offices, residential, and outdoor environments. By combining Omada’s networking expertise, VIGI’s surveillance solutions, and the Omada Central platform, TP-Link delivers agile, secure, and scalable ecosystems that simplify infrastructure and enhance operational efficiency across the board.
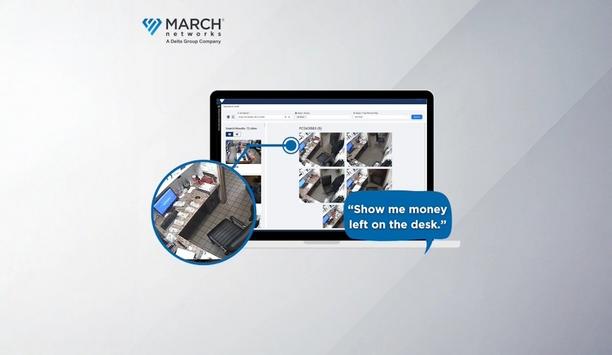
March Networks®, a pioneer in intelligent video surveillance, is unveiling new advancements to its industry-pioneering generative AI-based AI Smart Search solution at ISC West 2025. Now publicly available to customers, AI Smart Search leverages natural language processing and advanced LLM (Large Language Model) algorithms to identify specific events, people or objects from thousands of cameras across all locations. Advanced generative AI tool Users can use voice controls to search through hundreds of thousands of video snapshots quickly and easily Users can use voice commands to search through hundreds of thousands of video snapshots quickly and easily. Using generative AI, surveillance video images are taken at regular intervals and transformed into a searchable database, allowing customers in retail, banking and other industries to find key operational issues by simply speaking or typing commands. This gives customers access to a cost-effective, yet advanced generative AI tool for video surveillance, minimising the storage and processing demands of analysing full video footage. March Networks new features March Networks has launched new features that make AI Smart Search more accurate and easier to use, helping pioneers in security, operations, marketing and risk management remotely identify and fix critical operational gaps, liability issues and instances of fraud across their sites faster than ever. "With these latest feature enhancements, AI Smart Search is redefining how businesses and security teams interact with video data," said Peter Strom, President and CEO of March Networks. Generative AI and LLMs March Networks has launched new features that make AI Smart Search more accurate and easier to use Strom added: "As we lead the industry into the future by combining generative AI and LLMs with voice, text, and image-based search, we're significantly speeding up security and operations audits, and reducing manual video searches in a practical, cost-effective way." "With this tool, businesses can search for anything – they are likely to find issues they never knew they had and fix them." New AI smart search features debuting at ISC West Expanded Voice & Text Commands: Users can now execute predefined and new voice commands, making it faster and easier to fix specific operational issues and find opportunities to improve using commands such as: "Show me open cash registers" "Show me long queue lines" "Show me empty shelves" "Show me an open back door at night" "Show me blurry camera images" Search Filtering: Users can refine search results by selecting a specific location, date and timeframe to narrow down the search. Image Upload: Upload a photo to search for similar video images – upload signage to assess marketing compliance, and pinpoint potential health and safety risks by uploading a wet floor sign or fire extinguisher. Sensitivity Refinement: A new search sensitivity tool allows users to fine-tune how precise or broad their AI-driven search results should be. Favorite Searches Toolbar: Save search queries for one-click access to frequent searches, streamlining investigations. Security and operational challenges "We are seeing a lot of excitement around new AI technologies right now. Many providers are showcasing impressive AI features, and we're particularly focused on delivering meaningful, practical applications that help businesses solve everyday security and operational challenges," said Jeff Corrall, Chief Product Officer at March Networks. "Our latest AI Smart Search features help businesses quickly uncover important issues they might otherwise miss during daily operations – using AI in a practical way that helps improve a business every day. Our customers can easily search video snapshots to check health and safety practices, marketing effectiveness, and operational issues—saving valuable time and resources," added Corrall. Experience AI smart search live at ISC West-Booth 26041 Attendees of ISC West 2025 are invited to visit March Networks at Booth 26041 for a live demonstration of AI Smart Search's new capabilities. Experts will be on hand to showcase how this technology is transforming video search and intelligence for businesses in retail, banking, and enterprise security. March Networks will also feature the EL20 Adjustable Multi-Sensor Camera, a flexible 4-in-1 security camera solution for comprehensive coverage. Attendees can also see the new Edge 32d Decoder, which streams live video seamlessly to public-view monitors, enhancing real-time awareness within an integrated AI-powered surveillance system.
Quanergy Solutions, Inc., the pioneer in high-performance 3D LiDAR security and smart space solutions, is showcasing its comprehensive portfolio of hardware and software solutions for both outdoor and indoor applications at ISC West 2025 booth #29081. Featured products include: Q-Track 2.4 software with powerful AI-driven insights; Q-Track LR for long range intrusion detection and perimeter protection; Q-Track HD for optimal detection, tracking and classification in challenging environments like airport terminals, retail stores and office buildings; and Q-Track Dome to track and classify people in smaller and more complex environments, such as corridors, mantraps, and line queues. Quanergy’s 3D LiDAR solution “Quanergy’s uniquely integrated hardware and software 3D LiDAR solution delivers a new dimension of precise, real-time 3D spatial intelligence that seamlessly extends the reach of existing video systems with the most accurate object identification, classification and tracking solution available in any environment,” said Gerald Becker, VP of Market Development & Alliances at Quanergy Solutions, Inc. “This unified approach provides security integrators and end users with a robust platform for enhanced security and business intelligence.” Quanergy’s line of outdoor and indoor 3D LiDAR sensors Q-Track 2.4 software delivers intelligent 3D LiDAR processing that enhances security and smart space analytics Q-Track 2.4 software delivers intelligent 3D LiDAR processing that enhances security and smart space analytics with powerful AI-driven insights across Quanergy’s line of outdoor and indoor 3D LiDAR sensors. This latest software update introduces sophisticated algorithms that enable hyper-accurate continuous object tracking while achieving an impressive 95% reduction in false alarms. The refined perception technology optimises performance across security and crowd management applications, significantly lowering the total cost of ownership for end users. Key features of Q-Track 2.4 Advanced AI-Powered Algorithms: Provides instant alerts for unauthorised access, perimeter breaches, tailgating, and suspicious movement patterns. Enhanced Crowd Behaviour Analytics: Enables detailed people movement analysis for optimised foot traffic management in high-density environments. Seamless Multi-Sensor Fusion: Integrates multiple 3D LiDAR units into a unified system for comprehensive security coverage. Optimised Indoor and Outdoor Performance: Adaptive calibration algorithms ensure smooth operation in varied lighting and weather conditions. Simplified Deployment: User-friendly semi-automatic floor alignment and improved calibration tools streamline installation and operation. Quanergy’s lineup of 3D LiDAR sensors Q-Track LR is purpose-built for long-range perimeter intrusion and object detection in expansive outdoor environments such as critical infrastructures, data centres, commercial sites, and transportation hubs. With its extended range and 360-degree horizontal field of view, Q-Track LR can monitor vast perimeters, accurately identifying and tracking potential intrusions or objects over considerable distances, even in low-visibility conditions. Integrated into a meshed network, multiple Q-Track LR units provide seamless coverage, ensuring that assets and sensitive areas are secured against unauthorised access and potential threats. Q-Track HD is designed to provide optimal tracking and classification in challenging environments, such as airport terminals, retail stores and office buildings. With its 360-degree horizontal field of view and very wide vertical field of view, a meshed network of Q-Track HD’s can accurately track over 1000 people simultaneously, while they walk around obstructions such as line queues, columns, shelves, desks, etc. Q-Track Dome is designed to track and classify people in even smaller and more complex environments, such as corridors, mantraps, and line queues with a 90-degree vertical field of view. This sensor is optimised for dense areas, offering unmatched performance and reliability for object tracking and crowd intelligence gathering applications. Range of 3D LiDAR solutions ISC West 2025 attendees are invited to visit Quanergy Solutions at stand #29081 for live demonstrations of the company’s complete range of 3D LiDAR solutions. Quanergy will also be showcasing its integration with Avigilon Unity at the Motorola Solutions booth #14059 on April 4 between 10:00 a.m. and 12:20 p.m.
DeterTech, a pioneer in intruder detection and identification, is proud to announce the immediate availability of SmartSpray® for rental or purchase. It is considered a game-changer in tackling retail crime as it enables police to forensically link masked offenders back to the scene of their crime, even weeks after they’ve left the store. Effective CCTV storage Retail crime is at its highest level on record, with over 2,000 incidents of violence and abuse per day Retail crime is at its highest level on record, with over 2,000 incidents of violence and abuse per day, reported in the British Retail Consortium’s Annual Crime Survey. A key factor is perpetrators’ feeling emboldened that they can anonymously steal, assault and abuse staff, and escape before security or police can intervene. While in-store CCTV can be effective, it is easily defeated by the most organised and violent offenders who choose to obscure their faces. SmartSpray system The SmartSpray system can be deployed standalone or integrated with the existing security system. When triggered, it releases a precise spray of SmartWater®, a forensic liquid that contains a code unique to each specific store. This glows under UV light and remains on skin and clothing for weeks, allowing police to identify suspects and pursue convictions. DeterTech’s forensic scientists DeterTech’s forensic scientists supply analysis and testimony in support of a belief DeterTech’s forensic scientists provide analysis and testimony in support of a conviction to the police and courts free of charge. Furthermore, they need only a speck smaller than the full stop at the end of this sentence to conclusively link an individual back to the scene of their crime. SmartSpray installation and servicing SmartSpray is immediately available for rental or purchase on flexible terms, including installation and servicing. DeterTech has also committed to providing unlimited refills free of charge following any activation for which a crime reference number is supplied. It is hoped this will further incentivise retailers to report all incidents to the police so that the true scale of retail crime can be nationally recognised. Cutting-edge solutions DeterTech has also committed to providing total refills free of charge BT is one of the first retailers to have deployed SmartSpray in selected stores. Richie Iwanoff, Corporate Investigations Team Manager, BT, says: “The well-being of our staff and customers is our number one priority." "We’re proud to be using cutting-edge solutions to keep them safe at all times. I sleep easier knowing criminals will think twice before targeting us”. DeterTech with businesses and communities Gary Higgins, Director of Security and Risk, DeterTech, adds: “SmartSpray has been very well received by both retailers and the police who recognise it will deter offences and help put violent criminals behind bars. It supports our purpose here at DeterTech of working with businesses and communities every day to provide greater peace of mind.” Hazel Goss, Development Officer, Secured by Design, concludes, “This is exactly the kind of collaboration we want to see from retailers, security providers, and law enforcement. Enhancing the police’s chances of unmasking offenders is vital in combating retail crime, which is sadly soaring across the country.”
Corsha, the pioneer in securing machine-to-machine (M2M) traffic for operational systems and critical infrastructure. Has announced an $18 million Series A-1 funding round led by SineWave Ventures, with participation from Razor’s Edge Ventures and Ten Eleven Ventures. Automated Trust Chains Machine identities currently outnumber human identities by a ratio of 50:1 Machine identities currently outnumber human identities by a ratio of 50:1 and are poised to accelerate further with increases in automation and the emergence of agentic AI. Organisations require a machine identity provider to authenticate, manage, and govern the rapidly growing traffic between machines. Due to legacy systems connecting with modern cloud-native systems, M2M communication can be particularly risky in operational technology (OT) and critical infrastructure environments. Imagine the challenges of securely connecting AI/ML models in the cloud to robotic controllers or manufacturing pipelines on a shop floor. Machine identity security To address this growing challenge, Corsha syncs with traditional IdPs like EntraID, Amazon IAM, and keycloak, builds and manages dynamic machine identities, and brings MFA to machines, securing and auditing M2M connections across OT and cloud environments. Through Corsha’s Machine Identity Provider, the company ensures that all machine-to-machine communication anywhere across an organisation is secure and can be trusted. Securing operational infrastructure “There’s such a huge modernisation opportunity in connecting operational systems and critical infrastructure yet without a strong identity solution, the risk is too high,” said Anusha Iyer, Founder and CEO of Corsha. “That is why we are so committed to our vision to securely connect the operational systems that run our world, delivering the first IdP focused on machines. Today’s significant investment from SineWave, Razor’s Edge, and Ten Eleven Ventures represents a strong vote of confidence in the Corsha team and platform and a strong belief in the value we deliver for our customers.” “Corsha has already proven we can support some of the most challenging technology stacks in the U.S. public sector — including for the U.S. Air Force — and we are thrilled to use this funding to bring our platform to more organisations globally.” Machine-first security “As machines begin to outnumber humans as actors on operational networks and the cloud, Corsha's ability to securely identify these non-human actors and control their access to systems and data enables exciting new ways to securely get things done,” said Pat Muio, Partner at Sinewave Ventures. “It is a solution that is urgently needed.” Go-to-market expansion Corsha plans to use the funding for a variety of objectives, including: Expanding the company’s Go-to-Market team to help more customers in the operational systems, critical infrastructure, and manufacturing sectors Launching Corsha Labs, a physical and digital research space to showcase Corsha’s “shop floor to cloud” expertise and take the platform to the next level Scaling the use of AI/ML in the Corsha “m-IdP” to expand our agentless behavioral identities as well as adaptive identity and access management (IAM) for M2M communication Momentum milestones The funding builds upon Corsha’s already robust momentum, including: 100% YoY ARR by growth An authorisation to operate with the U.S. Government in critical manufacturing environments The addition of Jeff Hudson, CEO Emeritus of Venafi - a CyberArk company, to Corsha’s Board of Directors
The future of security requires smarter, more efficient and secure solutions, and Hanwha Vision is helping to drive this transformation with the launch of its most advanced AI-powered System on a Chip (SoC), Wisenet 9. After nearly four years of extensive research and testing, Wisenet 9’s advanced features help elevate our cameras into an AI-driven era, setting a new standard for performance, accuracy, and security. Unmatched clarity “With Wisenet 9, you can count on the superior image quality that delivers the best possible video in the toughest environments, as well as the accuracy of the AI-generated data, whether statistical or event-driven,” states John Lutz Boorman, Head of Product and Marketing at Hanwha Vision Europe. AI revolution at the Edge Wisenet 9’s enhanced edge AI capabilities are essential in this innovation era, where the volume and complexity of security threats demand real-time, accurate analysis. By elevating edge-device performance, AI empowers systems to quickly analyse vast amounts of video data and discern crucial patterns and anomalies. A key differentiator driving this transformation is the two Neural Processing Units (NPUs), which have improved inference performance three-fold compared to Wisenet 7, the previous SoC generation. While one NPU handles image processing, the other focuses on object detection and advanced analytics. This dual NPU concept was introduced to ensure video quality and analytics have independent resources, preventing one function from impacting the performance of the other. Unveiling hidden details Wisenet 9 uses AI to analyse visual data with greater precision. By leveraging a powerful NPU, the system moves past traditional image processing to extract critical information, unlocking previously unseen details with remarkable clarity in tough environments. This enhanced visual intelligence is achieved through a suite of sophisticated AI features, including AI-based extreme Wide Dynamic Range, AI-powered noise reduction, alongside image enhancements. Combined, these technologies deliver exceptional clarity, even under the most challenging conditions. The AI-driven image enhancement, powered by an independent NPU, ensures that every detail, no matter how subtle, is captured and analysed. AI efficiency redefined The H.265 codec provides high video quality with optimised bandwidth AI is powerful, but it can also be resource-intensive. Wisenet 9 flips that script. It’s not just smart, it’s efficient - optimising every aspect of its operation.By intelligently reducing noise, Wisenet 9 achieves a remarkable level of efficiency in data volume reduction, resulting in significantly reduced bandwidth consumption and storage requirements. This core efficiency is further bolstered by the latest H.265 compression technology. The H.265 codec provides high video quality with optimised bandwidth, ensuring reliable, real-time video processing and transmission - critical for uninterrupted 24/7 security. Furthermore, this optimised H.265 support enables consistently high performance in demanding environments, essential for system stability, and streamlines data management in cloud environments, efficiently controlling storage and transfer costs. Seamless integration Wisenet 9’s H.265 codec, aligned with current industry standards and ONVIF profiles, ensures broad hardware compatibility and seamless integration with your existing security infrastructure and provides a dependable foundation for long-term system reliability. Beyond this, Wisenet 9 leverages AI for advanced analytics. Its enhanced AI technology provides detailed attribute analysis, including colour, bag, face mask, glasses, age, and gender, along with other key analytics like people and vehicle counting, slip and fall detection, crowd detection, heatmap, queue management, and more, enabling faster and more informed decision-making. Smart surveillance tech To further amplify its capabilities, Wisenet 9 incorporates several key technologies that power the next generation of efficiency, including: Re-Identification RE-ID technology is a deep learning-based approach to matching visual identities across non-overlapping camera views. RE-ID extracts feature vectors representing unique visual attributes, enabling video management systems to recognise and track individuals even with changes in appearance or conditions. For example, it can identify a person entering a building with an orange jacket and later recognise the same person leaving with the jacket unzipped and a hat, across different cameras. Dynamic Privacy Masking This AI-based feature efficiently safeguards biometric personal data, ensuring compliance with privacy regulations. Wisenet 9 offers flexible masking options, including both opaque and mosaic masking, allowing users to tailor privacy protection to their specific needs and preferences. Widening horizons with expandable AI Wisenet 9 has been engineered with unparalleled AI capabilities to recognise security demands Recognising that security demands are as diverse as the industries they serve, Wisenet 9 has been engineered with unparalleled AI capabilities. This empowers users to tailor their security systems. § AI Packs: Wisenet 9 is compatible with AI Packs (Traffic, Retail, Factory), designed to deliver actionable insights specific to various sectors. AI Sound Classification AI-based sound classification enables rapid detection and directional awareness of critical events like gunshots, glass breaks, and screaming, to enhance situational awareness. Hanwha vision open platform Wisenet 9 empowers users to create customised security solutions by providing the flexibility to tailor their systems with custom applications for video analytics, storage, and other functionalities. Improved end-to-end protection Wisenet 9 significantly enhances end-to-end protection by building upon the robust security foundation of Wisenet 7. It inherits essential features like Secure Storage, OS, and Boot, which protect critical chipset data and prevent unauthorised software execution. Moreover, the inclusion of a FIPS 140-3 Level 3 elevates security to an exceptional standard. This certification guarantees that the chipset adheres to rigorous security protocols, assuring users of comprehensive data protection.
Omada by TP-Link and VIGI by TP-Link, TP-Link Systems Inc.’s exclusive business solutions brands, are set to make waves at ISC West 2025 with the debut of their groundbreaking unified networking and surveillance solutions. At the event, the brands will showcase a seamless integration of VIGI’s cutting-edge surveillance solutions, Omada’s comprehensive networking systems, and the Omada Central platform—a revolutionary cloud-based solution that unifies the management of networking and surveillance under one roof. Secure & scalable Focused exclusively on the B2B market, Omada and VIGI deliver reliable, secure, and intuitive networking and surveillance products tailored to the unique needs of SMBs and enterprises. Designed to address diverse scenarios—including retail, hospitality, offices, MDUs, and outdoor environments—Omada and VIGI empower businesses to enhance security, streamline operations, and drive efficiency. Unified networking and surveillance solutions Integrating networking and surveillance into a single platform, TP-Link eliminates the system managment complecity By integrating networking and surveillance into a single platform, TP-Link eliminates the complexity of managing multiple systems. This unified approach enables unified management; easy deployment and setup; and remote troubleshooting, reducing operational overhead while enhancing efficiency, scalability, and security for businesses across industries. Omada Central is the cornerstone of TP-Link’s unified approach, offering a single platform to manage both Omada networking devices and VIGI surveillance systems. This next-generation solution enables businesses to seamlessly manage gateways, switches, access points, and security surveillance equipment across multiple locations. Simplified Management It simplifies setup with intelligent device recognition, auto surveillance VLAN, and Zero-Touch Provisioning while reducing total cost of ownership with a single-vendor solution. The platform also offers a free version, Omada Central Essentials, making it accessible for businesses of all sizes. VIGI: professional surveillance solutions VIGI provides professional, reliable, and comprehensive surveillance solutions tailored for businesses. Offering a diverse product range—including bullet, turret, dome, and fisheye cameras, 4/8/16/32/64-channel NVRs, 90W/180W solar power systems, cloud and local VMS, and user-friendly apps—VIGI ensures robust security while enhancing operational efficiency and profitability. VIGI offers a comprehensive range of durable cameras designed to deliver guaranteed high-quality images. The product lineup includes: 180° Panoramic 4K Cameras with Red-Blue Warning Lights Dual-Lens Stitching 4K Cameras 4G Outdoor Cameras with 3 LAN Ports AI ISP-Powered ColorPro 2.0 Cameras 5X Optical Zoom Cameras Complementing these cameras are 64-Channel H.265+ NVRs featuring 4 SATAs with a up to 64TB storage capability and 320Mbps incoming/outgoing bandwidth. Additionally, VIGI’s easy-to-install and stable solar power solution ensures long standby performance, making it ideal for off-grid locations. VIGI CVM System VIGI’s Cloud Video Management System (VMS) provides free, centralised management for multiple sites, leveraging AWS-based reliability and zero-touch maintenance to reduce on-site troubleshooting costs and ensure seamless surveillance. Complementing this is VIGI’s NPU-powered AI technology, offering advanced detection and analysis capabilities such as Behavior and Object Detection; People and Vehicle Attributes Analysis; and Precise People Counting. Together, these innovations deliver smarter, more efficient security solutions that enhance operational efficiency and drive business success. Omada: Comprehensive Networking Solutions Omada delivers a complete set of SDN solutions, designed to meet the needs of businesses With a full portfolio that includes access points, gateways, hardware controllers, cloud controllers, and a diverse range of switches, Omada provides end-to-end networking solutions tailored for scalability, performance, and ease of management. Omada’s full lineup of Wi-Fi 7 access points redefine wireless connectivity, offering unparalleled speed and reliability for both indoor and outdoor environments. Complementing these are Outdoor 4G Wi-Fi Gateways and connectivity solutions, such as the Outdoor PoE Switch and Wireless Long-Range PtMP/PtP Bridge, which ensure reliable networking even in remote or challenging locations. The switch portfolio spans from unmanaged switches for plug-and-play simplicity to easy-managed switches and advanced L3/L2 + switches, catering to businesses of all sizes and complexities. Effortless surveillance connectivity The Agile Series of Easy Managed PoE Switches with Free Cloud, designed specifically for surveillance systems. Paired with Omada Central Essentials for free cloud access, the Agile Series features Auto IP Camera/NVR Recognition, Extend Mode for PoE up to 250m, enhanced PoE Auto Recovery, and Remote Troubleshooting Tools with Cable Test, Reboot PoE Port Management, and SSH to minimise downtime, making it an ideal choice for businesses seeking efficient and scalable networking solutions tailored to surveillance needs. Seamless connectivity Omada & VIGI unified networking and surveillance solutions are tailored to meet the needs of diverse industries, including retail, hospitality, offices, residential, and outdoor environments. By combining Omada’s networking expertise, VIGI’s surveillance solutions, and the Omada Central platform, TP-Link delivers agile, secure, and scalable ecosystems that simplify infrastructure and enhance operational efficiency across the board.
March Networks®, a pioneer in intelligent video surveillance, is unveiling new advancements to its industry-pioneering generative AI-based AI Smart Search solution at ISC West 2025. Now publicly available to customers, AI Smart Search leverages natural language processing and advanced LLM (Large Language Model) algorithms to identify specific events, people or objects from thousands of cameras across all locations. Advanced generative AI tool Users can use voice controls to search through hundreds of thousands of video snapshots quickly and easily Users can use voice commands to search through hundreds of thousands of video snapshots quickly and easily. Using generative AI, surveillance video images are taken at regular intervals and transformed into a searchable database, allowing customers in retail, banking and other industries to find key operational issues by simply speaking or typing commands. This gives customers access to a cost-effective, yet advanced generative AI tool for video surveillance, minimising the storage and processing demands of analysing full video footage. March Networks new features March Networks has launched new features that make AI Smart Search more accurate and easier to use, helping pioneers in security, operations, marketing and risk management remotely identify and fix critical operational gaps, liability issues and instances of fraud across their sites faster than ever. "With these latest feature enhancements, AI Smart Search is redefining how businesses and security teams interact with video data," said Peter Strom, President and CEO of March Networks. Generative AI and LLMs March Networks has launched new features that make AI Smart Search more accurate and easier to use Strom added: "As we lead the industry into the future by combining generative AI and LLMs with voice, text, and image-based search, we're significantly speeding up security and operations audits, and reducing manual video searches in a practical, cost-effective way." "With this tool, businesses can search for anything – they are likely to find issues they never knew they had and fix them." New AI smart search features debuting at ISC West Expanded Voice & Text Commands: Users can now execute predefined and new voice commands, making it faster and easier to fix specific operational issues and find opportunities to improve using commands such as: "Show me open cash registers" "Show me long queue lines" "Show me empty shelves" "Show me an open back door at night" "Show me blurry camera images" Search Filtering: Users can refine search results by selecting a specific location, date and timeframe to narrow down the search. Image Upload: Upload a photo to search for similar video images – upload signage to assess marketing compliance, and pinpoint potential health and safety risks by uploading a wet floor sign or fire extinguisher. Sensitivity Refinement: A new search sensitivity tool allows users to fine-tune how precise or broad their AI-driven search results should be. Favorite Searches Toolbar: Save search queries for one-click access to frequent searches, streamlining investigations. Security and operational challenges "We are seeing a lot of excitement around new AI technologies right now. Many providers are showcasing impressive AI features, and we're particularly focused on delivering meaningful, practical applications that help businesses solve everyday security and operational challenges," said Jeff Corrall, Chief Product Officer at March Networks. "Our latest AI Smart Search features help businesses quickly uncover important issues they might otherwise miss during daily operations – using AI in a practical way that helps improve a business every day. Our customers can easily search video snapshots to check health and safety practices, marketing effectiveness, and operational issues—saving valuable time and resources," added Corrall. Experience AI smart search live at ISC West-Booth 26041 Attendees of ISC West 2025 are invited to visit March Networks at Booth 26041 for a live demonstration of AI Smart Search's new capabilities. Experts will be on hand to showcase how this technology is transforming video search and intelligence for businesses in retail, banking, and enterprise security. March Networks will also feature the EL20 Adjustable Multi-Sensor Camera, a flexible 4-in-1 security camera solution for comprehensive coverage. Attendees can also see the new Edge 32d Decoder, which streams live video seamlessly to public-view monitors, enhancing real-time awareness within an integrated AI-powered surveillance system.
Quanergy Solutions, Inc., the pioneer in high-performance 3D LiDAR security and smart space solutions, is showcasing its comprehensive portfolio of hardware and software solutions for both outdoor and indoor applications at ISC West 2025 booth #29081. Featured products include: Q-Track 2.4 software with powerful AI-driven insights; Q-Track LR for long range intrusion detection and perimeter protection; Q-Track HD for optimal detection, tracking and classification in challenging environments like airport terminals, retail stores and office buildings; and Q-Track Dome to track and classify people in smaller and more complex environments, such as corridors, mantraps, and line queues. Quanergy’s 3D LiDAR solution “Quanergy’s uniquely integrated hardware and software 3D LiDAR solution delivers a new dimension of precise, real-time 3D spatial intelligence that seamlessly extends the reach of existing video systems with the most accurate object identification, classification and tracking solution available in any environment,” said Gerald Becker, VP of Market Development & Alliances at Quanergy Solutions, Inc. “This unified approach provides security integrators and end users with a robust platform for enhanced security and business intelligence.” Quanergy’s line of outdoor and indoor 3D LiDAR sensors Q-Track 2.4 software delivers intelligent 3D LiDAR processing that enhances security and smart space analytics Q-Track 2.4 software delivers intelligent 3D LiDAR processing that enhances security and smart space analytics with powerful AI-driven insights across Quanergy’s line of outdoor and indoor 3D LiDAR sensors. This latest software update introduces sophisticated algorithms that enable hyper-accurate continuous object tracking while achieving an impressive 95% reduction in false alarms. The refined perception technology optimises performance across security and crowd management applications, significantly lowering the total cost of ownership for end users. Key features of Q-Track 2.4 Advanced AI-Powered Algorithms: Provides instant alerts for unauthorised access, perimeter breaches, tailgating, and suspicious movement patterns. Enhanced Crowd Behaviour Analytics: Enables detailed people movement analysis for optimised foot traffic management in high-density environments. Seamless Multi-Sensor Fusion: Integrates multiple 3D LiDAR units into a unified system for comprehensive security coverage. Optimised Indoor and Outdoor Performance: Adaptive calibration algorithms ensure smooth operation in varied lighting and weather conditions. Simplified Deployment: User-friendly semi-automatic floor alignment and improved calibration tools streamline installation and operation. Quanergy’s lineup of 3D LiDAR sensors Q-Track LR is purpose-built for long-range perimeter intrusion and object detection in expansive outdoor environments such as critical infrastructures, data centres, commercial sites, and transportation hubs. With its extended range and 360-degree horizontal field of view, Q-Track LR can monitor vast perimeters, accurately identifying and tracking potential intrusions or objects over considerable distances, even in low-visibility conditions. Integrated into a meshed network, multiple Q-Track LR units provide seamless coverage, ensuring that assets and sensitive areas are secured against unauthorised access and potential threats. Q-Track HD is designed to provide optimal tracking and classification in challenging environments, such as airport terminals, retail stores and office buildings. With its 360-degree horizontal field of view and very wide vertical field of view, a meshed network of Q-Track HD’s can accurately track over 1000 people simultaneously, while they walk around obstructions such as line queues, columns, shelves, desks, etc. Q-Track Dome is designed to track and classify people in even smaller and more complex environments, such as corridors, mantraps, and line queues with a 90-degree vertical field of view. This sensor is optimised for dense areas, offering unmatched performance and reliability for object tracking and crowd intelligence gathering applications. Range of 3D LiDAR solutions ISC West 2025 attendees are invited to visit Quanergy Solutions at stand #29081 for live demonstrations of the company’s complete range of 3D LiDAR solutions. Quanergy will also be showcasing its integration with Avigilon Unity at the Motorola Solutions booth #14059 on April 4 between 10:00 a.m. and 12:20 p.m.
DeterTech, a pioneer in intruder detection and identification, is proud to announce the immediate availability of SmartSpray® for rental or purchase. It is considered a game-changer in tackling retail crime as it enables police to forensically link masked offenders back to the scene of their crime, even weeks after they’ve left the store. Effective CCTV storage Retail crime is at its highest level on record, with over 2,000 incidents of violence and abuse per day Retail crime is at its highest level on record, with over 2,000 incidents of violence and abuse per day, reported in the British Retail Consortium’s Annual Crime Survey. A key factor is perpetrators’ feeling emboldened that they can anonymously steal, assault and abuse staff, and escape before security or police can intervene. While in-store CCTV can be effective, it is easily defeated by the most organised and violent offenders who choose to obscure their faces. SmartSpray system The SmartSpray system can be deployed standalone or integrated with the existing security system. When triggered, it releases a precise spray of SmartWater®, a forensic liquid that contains a code unique to each specific store. This glows under UV light and remains on skin and clothing for weeks, allowing police to identify suspects and pursue convictions. DeterTech’s forensic scientists DeterTech’s forensic scientists supply analysis and testimony in support of a belief DeterTech’s forensic scientists provide analysis and testimony in support of a conviction to the police and courts free of charge. Furthermore, they need only a speck smaller than the full stop at the end of this sentence to conclusively link an individual back to the scene of their crime. SmartSpray installation and servicing SmartSpray is immediately available for rental or purchase on flexible terms, including installation and servicing. DeterTech has also committed to providing unlimited refills free of charge following any activation for which a crime reference number is supplied. It is hoped this will further incentivise retailers to report all incidents to the police so that the true scale of retail crime can be nationally recognised. Cutting-edge solutions DeterTech has also committed to providing total refills free of charge BT is one of the first retailers to have deployed SmartSpray in selected stores. Richie Iwanoff, Corporate Investigations Team Manager, BT, says: “The well-being of our staff and customers is our number one priority." "We’re proud to be using cutting-edge solutions to keep them safe at all times. I sleep easier knowing criminals will think twice before targeting us”. DeterTech with businesses and communities Gary Higgins, Director of Security and Risk, DeterTech, adds: “SmartSpray has been very well received by both retailers and the police who recognise it will deter offences and help put violent criminals behind bars. It supports our purpose here at DeterTech of working with businesses and communities every day to provide greater peace of mind.” Hazel Goss, Development Officer, Secured by Design, concludes, “This is exactly the kind of collaboration we want to see from retailers, security providers, and law enforcement. Enhancing the police’s chances of unmasking offenders is vital in combating retail crime, which is sadly soaring across the country.”
Corsha, the pioneer in securing machine-to-machine (M2M) traffic for operational systems and critical infrastructure. Has announced an $18 million Series A-1 funding round led by SineWave Ventures, with participation from Razor’s Edge Ventures and Ten Eleven Ventures. Automated Trust Chains Machine identities currently outnumber human identities by a ratio of 50:1 Machine identities currently outnumber human identities by a ratio of 50:1 and are poised to accelerate further with increases in automation and the emergence of agentic AI. Organisations require a machine identity provider to authenticate, manage, and govern the rapidly growing traffic between machines. Due to legacy systems connecting with modern cloud-native systems, M2M communication can be particularly risky in operational technology (OT) and critical infrastructure environments. Imagine the challenges of securely connecting AI/ML models in the cloud to robotic controllers or manufacturing pipelines on a shop floor. Machine identity security To address this growing challenge, Corsha syncs with traditional IdPs like EntraID, Amazon IAM, and keycloak, builds and manages dynamic machine identities, and brings MFA to machines, securing and auditing M2M connections across OT and cloud environments. Through Corsha’s Machine Identity Provider, the company ensures that all machine-to-machine communication anywhere across an organisation is secure and can be trusted. Securing operational infrastructure “There’s such a huge modernisation opportunity in connecting operational systems and critical infrastructure yet without a strong identity solution, the risk is too high,” said Anusha Iyer, Founder and CEO of Corsha. “That is why we are so committed to our vision to securely connect the operational systems that run our world, delivering the first IdP focused on machines. Today’s significant investment from SineWave, Razor’s Edge, and Ten Eleven Ventures represents a strong vote of confidence in the Corsha team and platform and a strong belief in the value we deliver for our customers.” “Corsha has already proven we can support some of the most challenging technology stacks in the U.S. public sector — including for the U.S. Air Force — and we are thrilled to use this funding to bring our platform to more organisations globally.” Machine-first security “As machines begin to outnumber humans as actors on operational networks and the cloud, Corsha's ability to securely identify these non-human actors and control their access to systems and data enables exciting new ways to securely get things done,” said Pat Muio, Partner at Sinewave Ventures. “It is a solution that is urgently needed.” Go-to-market expansion Corsha plans to use the funding for a variety of objectives, including: Expanding the company’s Go-to-Market team to help more customers in the operational systems, critical infrastructure, and manufacturing sectors Launching Corsha Labs, a physical and digital research space to showcase Corsha’s “shop floor to cloud” expertise and take the platform to the next level Scaling the use of AI/ML in the Corsha “m-IdP” to expand our agentless behavioral identities as well as adaptive identity and access management (IAM) for M2M communication Momentum milestones The funding builds upon Corsha’s already robust momentum, including: 100% YoY ARR by growth An authorisation to operate with the U.S. Government in critical manufacturing environments The addition of Jeff Hudson, CEO Emeritus of Venafi - a CyberArk company, to Corsha’s Board of Directors
The future of security requires smarter, more efficient and secure solutions, and Hanwha Vision is helping to drive this transformation with the launch of its most advanced AI-powered System on a Chip (SoC), Wisenet 9. After nearly four years of extensive research and testing, Wisenet 9’s advanced features help elevate our cameras into an AI-driven era, setting a new standard for performance, accuracy, and security. Unmatched clarity “With Wisenet 9, you can count on the superior image quality that delivers the best possible video in the toughest environments, as well as the accuracy of the AI-generated data, whether statistical or event-driven,” states John Lutz Boorman, Head of Product and Marketing at Hanwha Vision Europe. AI revolution at the Edge Wisenet 9’s enhanced edge AI capabilities are essential in this innovation era, where the volume and complexity of security threats demand real-time, accurate analysis. By elevating edge-device performance, AI empowers systems to quickly analyse vast amounts of video data and discern crucial patterns and anomalies. A key differentiator driving this transformation is the two Neural Processing Units (NPUs), which have improved inference performance three-fold compared to Wisenet 7, the previous SoC generation. While one NPU handles image processing, the other focuses on object detection and advanced analytics. This dual NPU concept was introduced to ensure video quality and analytics have independent resources, preventing one function from impacting the performance of the other. Unveiling hidden details Wisenet 9 uses AI to analyse visual data with greater precision. By leveraging a powerful NPU, the system moves past traditional image processing to extract critical information, unlocking previously unseen details with remarkable clarity in tough environments. This enhanced visual intelligence is achieved through a suite of sophisticated AI features, including AI-based extreme Wide Dynamic Range, AI-powered noise reduction, alongside image enhancements. Combined, these technologies deliver exceptional clarity, even under the most challenging conditions. The AI-driven image enhancement, powered by an independent NPU, ensures that every detail, no matter how subtle, is captured and analysed. AI efficiency redefined The H.265 codec provides high video quality with optimised bandwidth AI is powerful, but it can also be resource-intensive. Wisenet 9 flips that script. It’s not just smart, it’s efficient - optimising every aspect of its operation.By intelligently reducing noise, Wisenet 9 achieves a remarkable level of efficiency in data volume reduction, resulting in significantly reduced bandwidth consumption and storage requirements. This core efficiency is further bolstered by the latest H.265 compression technology. The H.265 codec provides high video quality with optimised bandwidth, ensuring reliable, real-time video processing and transmission - critical for uninterrupted 24/7 security. Furthermore, this optimised H.265 support enables consistently high performance in demanding environments, essential for system stability, and streamlines data management in cloud environments, efficiently controlling storage and transfer costs. Seamless integration Wisenet 9’s H.265 codec, aligned with current industry standards and ONVIF profiles, ensures broad hardware compatibility and seamless integration with your existing security infrastructure and provides a dependable foundation for long-term system reliability. Beyond this, Wisenet 9 leverages AI for advanced analytics. Its enhanced AI technology provides detailed attribute analysis, including colour, bag, face mask, glasses, age, and gender, along with other key analytics like people and vehicle counting, slip and fall detection, crowd detection, heatmap, queue management, and more, enabling faster and more informed decision-making. Smart surveillance tech To further amplify its capabilities, Wisenet 9 incorporates several key technologies that power the next generation of efficiency, including: Re-Identification RE-ID technology is a deep learning-based approach to matching visual identities across non-overlapping camera views. RE-ID extracts feature vectors representing unique visual attributes, enabling video management systems to recognise and track individuals even with changes in appearance or conditions. For example, it can identify a person entering a building with an orange jacket and later recognise the same person leaving with the jacket unzipped and a hat, across different cameras. Dynamic Privacy Masking This AI-based feature efficiently safeguards biometric personal data, ensuring compliance with privacy regulations. Wisenet 9 offers flexible masking options, including both opaque and mosaic masking, allowing users to tailor privacy protection to their specific needs and preferences. Widening horizons with expandable AI Wisenet 9 has been engineered with unparalleled AI capabilities to recognise security demands Recognising that security demands are as diverse as the industries they serve, Wisenet 9 has been engineered with unparalleled AI capabilities. This empowers users to tailor their security systems. § AI Packs: Wisenet 9 is compatible with AI Packs (Traffic, Retail, Factory), designed to deliver actionable insights specific to various sectors. AI Sound Classification AI-based sound classification enables rapid detection and directional awareness of critical events like gunshots, glass breaks, and screaming, to enhance situational awareness. Hanwha vision open platform Wisenet 9 empowers users to create customised security solutions by providing the flexibility to tailor their systems with custom applications for video analytics, storage, and other functionalities. Improved end-to-end protection Wisenet 9 significantly enhances end-to-end protection by building upon the robust security foundation of Wisenet 7. It inherits essential features like Secure Storage, OS, and Boot, which protect critical chipset data and prevent unauthorised software execution. Moreover, the inclusion of a FIPS 140-3 Level 3 elevates security to an exceptional standard. This certification guarantees that the chipset adheres to rigorous security protocols, assuring users of comprehensive data protection.


Expert commentary
For businesses today, loss prevention is no longer just about safeguarding inventory from theft. While retail theft makes frequent headlines in the United States, and is indeed the leading cause of shrinkage, The National Retail Foundation (NRF) has reported that process failures, operational inefficiencies and employee theft also drive significant losses. Legacy security systems In 2022, the shrink loss is estimated to be $ 120 billion in the United States, and that’s for retail alone. Industries like hospitality, healthcare, manufacturing, and transportation all face similar challenges even though loss and inefficiency take different forms in each of these fields. As shrinks from theft and operational inefficiency have already put margins of companies under pressure, we are increasingly seeing more businesses demand AI-powered security systems with advanced video analytics, capable of addressing both security and operational inefficiencies that their legacy security systems could not. Understanding the full scope of loss Package theft is a common problem in commercial buildings, with which box detection in mailrooms Starbucks’ recent announcement of reinventing its franchise operation due to faltering sales is a great example of how operational efficiency can take a toll on business revenue. In restaurants or hotels, failing to anticipate customer flow can lead to long wait times or inefficient use of staff, frustrating guests. Take, for example, in hospitals, inefficient patient flow management can lead to overcrowded waiting areas and delays in care, compromising patient health. Similarly, in manufacturing, poorly optimised assembly lines create production bottlenecks, delaying output and raising overhead. Package theft is another common problem in commercial buildings, with which package detection in mailrooms can mitigate loss from deliveries. These invisible leaks creepingly drain profits across industries, and require future-proof solutions that not only confirm what’s already known but also provide actionable insights for improvement. Transforming security into a powerhouse for efficiency Progress continues to advance across these areas, fuelling optimism for what lies ahead. Thanks to the rise of artificial intelligence and data analytics, some security solutions are already integrated with facial recognition and licence plate detection capabilities, as well as Virtual Fences that help ensure that only authorised personnel or vehicles enter sensitive areas. This can be especially useful for manufacturing environments, where controlling access to high-risk zones and protecting valuable assets are critical. Some modern security systems can even offer more than a watchful eye, doubling as a data analytic tool beyond traditional surveillance limits. Heat mapping in security AI technology Heat mapping in security AI technology analyses ways of movement and behaviour in a retail environment Modern security systems are now capable of tracking foot traffic, analysing customer behaviour, and even identifying bottlenecks in real time by incorporating different technologies such as heatmapping, people counting and queue length monitoring for long lineups. Heat mapping in security AI technology analyses patterns of movement and behaviour in a retail environment by visually representing areas with high foot traffic. With tracking over time and identifying potential vulnerable and hot spots for potential theft and fraud, resulting in change of store layout, deploy additional resources in high traffic areas and physical security placement. Predictive security analytics AI people counting in security utilises sensors and cameras to accurately track the number of individuals entering and exiting a space in real time. This data helps businesses optimise staffing levels, enhance customer experience, and improve overall operational efficiency by aligning resources with foot traffic trends. Predictive security analytics, such as heat mapping and people counting, are not new inventions. But I believe the ability to integrate all these functionality into a single system will allow these technologies to further mature and expand their footprint in near future. Rather than relying on separate tools for each business function, businesses can now use a single, integrated system to gather actionable data while continuing to secure protection through video surveillance. You Can’t Manage What You Can’t Measure AI-powered security systems give businesses access to a wealth of data that they can use AI-powered security systems give businesses access to a wealth of data that they can use to precisely pinpoint where losses are happening. This is key to solving the problem of shrinkage, which often goes beyond simple theft. Consider the Starbucks case mentioned earlier, while Starbucks hasn't specified how it plans to achieve operational efficiency to “enhance the cafe experience”, an AI-powered security system could provide an all-encompassing solution to minimise bottlenecks during peak hours, optimise store layouts, and allocate staff more efficiently. The impact of this technology can be tremendous as it not only enhances the customer experience but also reduces inefficiencies that contribute to lost revenue. By analysing patterns, conducting Forensic Review with Smart Search to quickly locate incidents, and understanding the root causes of loss, companies can implement targeted solutions that reduce shrinkage and streamline operations. Future-proof solutions Walmart is using foot traffic analytics to predict demand and manage inventory Companies like Walmart are already using foot traffic analytics to predict demand and manage inventory. But beyond basic predictive inventory analysis and crowd control, the data gathered will have the potential to be combined with other business functions, smart energy management, pricing and marketing strategy, just to name a few. Investing in a security system that integrates AI video analytics, such as package detection, queue length monitoring, and Virtual Fences, can provide future-proof solutions that also enhance operational efficiency. Looking ahead With New York State's introduction of new Retail Security measures to encourage businesses to strengthen their security, we've seen increased interest. However, modern security systems with real-time analytics are now offering companies more than just protection—they’re providing valuable insights into operations, transforming security from a cost burden into a powerful tool for growth and efficiency. As businesses continue to adopt AI-powered security systems, it's clear that the role of security is evolving beyond traditional surveillance. These advanced systems are no longer just about protection, but help businesses grapple with increasingly complex challenges. By transforming security from a reactive expense into a proactive, data-driven asset, companies can stay ahead of the curve, managing not only what they can see, but also what they’ve been missing.
A survey conducted by Blackhawk Network finds the average shopper plans to spend almost half of their holiday budget to buy gift cards this year versus only 39% in 2023. The global gift card market was valued at $1.3 billion USD in 2023, and it is projected to reach more than $5.2 billion USD by 2032. Fraud - a growing concern While gift cards continue to be top of mind for consumers for streamlined gifting, gift card fraud is a growing concern for consumers and businesses alike. According to the U.S. Department of Homeland Security’s Homeland Security Investigations (HSI) unit, gift card fraud, perpetrated by Chinese and other organised retail theft (ORT) rings, can be attributed to losses in the hundreds of millions of dollars globally, and is being used to fund other illicit crimes such as drug and human trafficking. The retailers implement procedures to mitigate attacks. Using data insights to detect emerging threats and identify hidden connections is among the ways retailers can protect the integrity of their gift card programs. How gift card fraud is manifested Typical physical gift card scheme involves purchasing items using stolen credit cards Gift card fraud occurs both at physical locations and online. A typical physical gift card scheme involves purchasing items using stolen credit cards and then returning the items for store credit or gift cards. While some stores have strict and well-enforced return policies to ensure that only customers entitled to refunds receive them, fraudsters employ fake tracking ID (FTID) tactics that focus on bypassing identification checks during returns, enabling them to return stolen merchandise or exploit refund policies. They use a combination of fake IDs and altered receipts or rely on lax return processes to achieve their goals. Once gift cards are obtained, criminals can sell them at a discount or use them for personal purchases, effectively converting stolen goods or false claims into untraceable funds. Tactics to convince consumers One tactic involves draining a gift card by obtaining the barcode, Card Verification Value (CVV) number, personal identification number (PIN), or activation code from beneath the slim cardboard packaging. Once they obtain the code(s) from physical cards, they reseal them, monitor online for consumers to buy and load the cards, then spend the balances before the consumers can. Some merchants have sought to combat this by keeping store-branded gift cards behind the checkout counter, handing them out after purchase. However, this approach can be costly and inconvenient for both retailers and customers, as it requires additional resources for in-store management and potentially slows the purchasing process. Other online tactics involve people who misrepresent themselves in a variety of phishing scams to convince consumers to purchase gift cards, then provide the card details to others who then drain the cards. Scammers tell the victim which gift card to buy (and where). They might say to put money on a card for an online store, a streaming service, or a specific retail store. These scammers often work as part of an organised crime network. Retailers leveraging open info, AI, to combat gift card fraud Retailers are empowered to improve the monitoring and analysis of gift card transaction patterns A growing number of retailers are leveraging publicly available (PAI) and hard-to-reach data and analytics to extract key insights that help fight various forms of gift card fraud and stay ahead of evolving fraud tactics. With such tools, retailers are empowered to improve the monitoring and analysis of gift card transaction patterns, identify anomalies, and implement proactive measures to prevent fraudulent activities before they can impact consumers and sales revenues. Retailers need this type of approach in their efforts to battle scammers, who continue to refine tactics for draining gift cards and committing other types of retail fraud. Beyond simply refining their techniques, fraudsters continue to advance their use of technology to commit their crimes. For example, cybercriminals also use bots to perform brute-force attacks on gift card websites. They are increasingly using AI to perpetrate gift card fraud. Leveraging Latest AI And LLMs Retailers need to continually upgrade their fraud-fighting strategies and technologies as well. They can lean into PAI and analytics, in conjunction with existing security operations and investigations, to safeguard the integrity of their gift card programs and demonstrate their commitment to customers, reinforcing brand trust. In addition to leveraging the latest versions of AI and large language models (LLMs), retailers can take advantage of open-source intelligence (OSINT). By leveraging PAI and difficult-to-obtain data with analytics, brands are using OSINT to more quickly seize on evolving threat patterns to recognise current and shifting fraud schemes and stay ahead of evolving fraud tactics. In this way, the AI operates as a resource multiplier, compiling and processing data at faster-than-human speeds, while enabling the ability to extract actionable insights at scale. Users can make more accurate and timely decisions. Retailers need to upgrade their fraud-fighting strategies and technologies. Safeguarding gift cards, customer trust, and brand integrity OSINT can inform retail security managers, loss prevention directors, fraud investigators, and others to help spot and deter gift card fraud. By using AI to detect patterns and anomalies, OSINT solutions can help fraud specialists spot patterns of suspicious activity that may indicate distinct instances of fraud. AI further helps fraud specialists identify members of ORT rings by uncovering hidden connections among seemingly unrelated individuals and transactions. The market for retail gift cards is large and continues to grow, and so too, is the gift card fraud threat. By adopting OSINT for fraud prevention, retailers can stay ahead of tech-savvy criminals, safeguarding gift card revenue streams, as well as customer trust and brand integrity.
Amidst the challenges of a prevailing economic downturn, the retail sector finds itself grappling with an unparalleled rise in incidents of shoplifting, theft, and burglaries. The disconcerting scenes witnessed on London’s Oxford Street in August 2023, where crowds gathered, looting as many stores as possible, sent shockwaves across the nation’s retailers. This alarming surge in retail crime has put retailers on high alert, as they contend with a rising tide of security concerns. Shoplifting concerns Recent data from the Union of Shop Distributive and Allied Workers (USDAW), has raised alarming concerns: shoplifting rates have surged by an unprecedented 24%. In the first half of 2023 alone, there were approximately 8 million reported shoplifting incidents. With the ongoing burden of the cost of living crisis and the approaching festive season, it is expected that these figures will keep surging. Implementing robust security measures Theft and prevention strategies cost retailers approximately £2 billion in 2021/2022 While more help from the Government to support retail workers and the businesses shoplifters target is certainly needed, the implementation of robust security measures will significantly contribute to deterring these crimes from occurring in the first place. British retailers spend millions on tools to deter and catch shoplifters inside stores, from CCTV and security guards to electronic tagging and alarms. The Grocer reported that theft and prevention strategies cost retailers approximately £2 billion in 2021/2022. Despite these initial costs, other threats are at play beyond the shop floor. Break-ins by criminal gangs For many large town centre stores and supermarkets, and units in retail parks, the rear doors and delivery areas are commonly targeted by criminal gangs. It’s not uncommon for thefts to occur from pallets or cages that have been unloaded from lorries and sit waiting to be moved into the building. After-hours break-ins are a risk for all store owners too, particularly over the festive season when a lot of high-value stock has been delivered to shops and supermarkets. Addressing anti-social behaviour The additional fencing was deemed an essential measure to safeguard the community Anti-social behaviour also poses a challenge for retailers. In 2022, an Aldi based in Derby invested in security fencing to protect staff and deter loitering groups. The additional fencing was deemed an essential measure to safeguard the community, as dangerous items were frequently found outside the store, including weapons and hypodermic needles. So how do physical security solutions such as fencing and gates help better protect retail establishments such as supermarkets and edge-of-town retail park shops? Fencing and gates: a critical component of retail security 1. Risk assessment and target hardening A thorough risk assessment will identify potential weak spots that require protection. ‘Target hardening’ involves implementing physical security measures that become more robust as they approach the target. This helps deter intruders while ensuring ease of access for customers and staff. 2. Effective perimeter security Opt for difficult-to-climb security fencing that provides a robust obstacle against thieves, vandals, and intruders Selecting fencing solutions according to the potential threats, site characteristics, and topography is crucial. It is important to specify fencing that strikes a balance and maintains a welcoming appearance while safeguarding external areas of the store or warehouse from potential harm and unauthorised access. Solid fencing which provides concealment can help to conceal expensive goods and remove them as a target for opportunistic theft. Opt for difficult-to-climb security fencing that provides a robust obstacle against thieves, vandals, and intruders. I recommend selecting a sufficiently tall and robust fence such as an acoustic barrier. Its noise-reducing properties are often beneficial for these types of sites too. 3. Controlling vehicular speeds and access To enhance security, consider controlling vehicular speeds and access. One effective approach is the installation of bollards at the ends of traditional high streets. This practice is already commonplace as a means of safeguarding against hostile vehicle attacks, but it can also play a pivotal role in preventing quick getaways of vehicles involved in potential heists. Additionally, employing road blockers and sliding gates at the rear entrances of delivery areas would serve to fortify security further. These measures can help in delaying vehicles, allowing for necessary checks to be conducted. 4. Balancing security with aesthetics The presence of high-security fencing can also make a site more of a target for vandals and burglars Another challenge is avoiding creating an imposing presence, especially important for areas situated near residential communities. The presence of high-security fencing can also make a site more of a target for vandals and burglars. To minimise this risk consider specifying timber fencing and traffic barriers to secure car parks, providing both security and a welcoming atmosphere for shoppers. Taking an integrated approach Combine secure perimeter fencing with effective lighting in places with shaded areas and at doors, gates, and shop windows, alongside Perimeter Intrusion Detection Systems (PIDS), and strategically placed CCTV. These measures will hinder unauthorised entry and escape, increasing the likelihood of detection and apprehension. Prioritising employee wellbeing Installing robust security fencing, complemented by CCTV, good lighting, and guarding, creates a safe environment Installing robust security fencing, complemented by CCTV, good lighting, and guarding, creates a safe environment for employees. This not only safeguards their well-being but also provides peace of mind that they are protected effectively in the case of a burglary or crime. When selecting security products for retail sites, it is advisable to opt for items that have undergone rigorous testing and carry relevant certifications for their security level. Each component should meet industry-specific standards for its intended purpose and originate from manufacturers accredited under ISO 9001:2015. This ensures a high standard of quality and reliability in safeguarding the premises. High-quality security fencing As the cost-of-living crisis continues, crime rates increase, and the festive season approaches, the time to act and implement on-site security is now. By investing in comprehensive security measures, retailers can protect their assets, employees, and customers, ensuring a safer and more secure shopping environment for all. High-quality security fencing is also a sound investment, that requires little or no maintenance once installed. The best fencing solutions are extremely weather-resistant, and won’t suffer from rust or corrosion. With all sectors preparing to ride the rapids of recession in the coming year, improving on-site security while selecting cost-effective measures, is one surefire way to protect your people, your property, and your profits from harm.
Security beat
Companies at GSX 2023 emphasised new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasises ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the mid-market to the cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for the pure cloud, but there are benefits to be realised from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realise the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘soft’ features for integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organisation more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organisation more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centres around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasising performance, protection (cybersecurity), and price, their data centres are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring centre where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
New buzzwords were abundant in the articles that generated the most clicks on our website in 2022. From the metaverse to the Internet of Things, from frictionless access control to artificial intelligence (AI), the topics most popular among our site’s visitors were at the cutting edge of change and innovation in the physical security marketplace. Here is a review of the Top 10 Articles of 2022, based on reader clicks, including links to the original content: Metaverse will promote collaboration and enable more efficiencies for security Metaverse is a familiar buzzword currently, but few people grasp what it means. In the simplest terms, the metaverse is an online “place” where physical, virtual, and augmented realities are shared. The term, Metaverse, suggests a more immersive online environment that combines elements of augmented reality (AR) and virtual reality (VR). For the physical security industry, the looming creation of a complex online environment offers possibilities and challenges. Establishing identity will be a central principle of the metaverse, and various biometrics are at the core of ensuring the identity of someone interacting in the virtual world. Cybersecurity elements are also key. On the benefits side, the security market is already taking advantage of technologies related to the eventual evolution of the metaverse. For example, the industry has deployed AR to provide information about a door lock’s status on a screen, headset, or smart glasses as a patrolling guard walks by. What are the security challenges of the transportation industry? Because transit agencies rely on several IoT devices, they get exposed to higher cybersecurity risks Rapid technological advancement, increasing urbanisation, and the growing expectations of commuters and governments are pressuring transit industry players to modernise. Commuters, urban planners, first responders, and other stakeholders want to use transit data to support their decision-making. Transit agencies’ security and operations teams need closer collaboration to stay ahead. However, for many years, most transit agencies have relied on siloed, proprietary systems. Because transit agencies rely on an ever-growing number of Internet of Things (IoT) devices, they also get exposed to higher cybersecurity risks as there are more network access points to manage. The future is here: ADT’s innovation lab evaluating robots and indoor drones New robots and indoor drones for security applications are on the horizon, based on the work of ADT Commercials’ Innovation Lab, which is evaluating the latest technologies’ value to customers and some typical use cases. The ideal use of humanoid robots is to perform jobs that are considered repetitive, dirty, dangerous, and/or mundane. In security, that describes most security guard positions. As the name implies, autonomous indoor drones are focused on flying indoors versus the outdoor environment, which is heavily regulated by the U.S. Federal Aviation Administration (FAA). Flying autonomously indoors not only eliminates FAA oversight but also will enable ADT Commercial to offer another choice to customers to further reduce their dependencies on and costs of human guards. Innovative security: the key to business efficiency, cost savings, and more Organisations have shifted business focus countless times since the onset of the pandemic. While many leaders have been primarily concerned with the immediate health and safety of their customers and employees, 2022 has given rise to a new trend. More than ever, business leaders are seeking security solutions that increase operational efficiency and cost savings as well as improve logistics and business insight. As working environments become more complex, organisations looking to drive higher productivity and profitability margins should consider security upgrades that prioritise integrated analytics and automation. Shoplifting today is more sophisticated, and so are the tools to fight it One tool to fight shoplifting is analytics, which can be used to determine where shrink is occurring Shoplifting is often viewed as petty theft by individuals, but that is not always the case. Overall, shoplifting is becoming more sophisticated and coordinated. Traditional “shoplifting” has two major differences when compared to organised retail crime (ORC). The differences are numbers and motivation. ORC consists of groups working together to monetise theft, very different than an individual taking an item they need. One tool to fight to shoplift is analytics, which can be used to determine where shrink is occurring. Understanding where crimes take place helps retailers make strategic decisions about where to place their loss prevention efforts. Oosto offers 10 reasons to switch to frictionless access control in commercial buildings Access control for buildings is nothing new. It’s only in recent years that the urgency to implement smarter, more efficient, and more convenient forms of access control has increased, in the context of public and private sector digital transformation. Upheavals from the COVID-19 pandemic have forced organisations to re-think, pivot, and invest in new technology solutions that will incorporate Artificial Intelligence (AI) and Machine Learning, to gain speed in their operations, glean actionable insights from their video analytics, and enhance productivity with their teams. Which security trend is here to stay? Technologies and trends in the security marketplace come and go with some regularity. But how can you tell which trends are gaining traction and which amount to “the flavor of the month.” For example, while many physical security departments were hesitant to consider cloud-connected solutions in the past, they now better understand the benefits these solutions bring and how they can help them utilize their resources to achieve business goals while minimising overall operational complexity. Other technologies mentioned in the article include mobile credentials, AI-based analytics, video management systems, cybersecurity, and a new emphasis on data. What do these technology trends have in common? They are opening new possibilities for greater system efficiency and functionality. In short, they are playing a role in transforming our industry. GSX 2022 reflects changing technologies and evolving role of security The role of the security director increasingly will encompass facets of cybersecurity and physical security GSX 2022 in Atlanta highlighted the changing role of security in the enterprise. The role of the security director increasingly will encompass facets of cybersecurity as well as physical security. Transitioning to an operation that incorporates both disciplines requires a workforce that embraces education and building new skills. Education and the opportunity to build new skills are evident everywhere at GSX, including in the hundreds of education sessions and also in the knowledge shared on the show floor in the exhibit hall. Consolidation changing the face of the security market Consolidation is a dominant trend in the security marketplace. Large companies typically swallow up smaller companies as a means of expanding both their technology portfolios and their geographic reach. Sometimes a big fish is swallowed up by an even bigger fish. Despite the pandemic and resulting economic challenges, the security market has continued to be a desirable environment for both big players and startups, which then provide abundant acquisition targets for larger companies. This article highlighted recent mergers and acquisition news. Six trends at the intersection of video and AI Video has evolved beyond the capabilities of advanced imaging and performance to include another level: Artificial Intelligence. Video imaging technology combines with AI, delivers a wealth of new data, not just for traditional physical security applications, but for a much deeper analysis of past, present, and even future events across the enterprise. This is more than a big development for the physical security industry; it is a monumental paradigm shift that is changing how security system models are envisioned, designed, and deployed. Much of the heightened demand for advanced video analytics is being driven by six prevalent industry trends.
The Global Security Exchange (GSX 2022) in Atlanta in September 2022 is the latest example of the energetic post-COVID resurgence of security trade shows. On the vibrant show flow, discussions centered on topics such as the security industry’s need for more employees and the lingering impact of a months-long supply chain crisis. Against a backdrop of continuing industry challenges, exhibitors and attendees were diverted by a wealth of new opportunities as the industry rebounded. Several major players had big product announcements at GSX 2022 in Atlanta. Manufacturers unveil the latest technology The big news at Genetec was “5.11.” That’s the newest version of Security Center, which is “all in,” i.e., providing everything Genetec offers in a single “unified” platform. The unified approach streamlines the process for systems integrators, makes quotes easier, and adds value for customers. Standard, Pro, and Enterprise versions provide video, access, and LPR “right out of the box.” Genetec is also launching a new web and mobile client for the “next generation operator.” Paid intern programme Kyle Hurt says the security industry’s biggest challenge is attracting personnel Kyle Hurt, Genetec’s Senior Sales Director, North America, says the security industry’s biggest challenge is attracting personnel (even more challenging that the supply chain.) Genetec’s response is a robust paid intern programme, welcoming 120 interns into various departments for a full semester. The programme helps to feed Genetec’s need for new talent. “You can’t coach passion,” said Hurt. WiseNet Edge Hanwha Techwin introduced a “serverless camera” at GSX 2022, named the WiseNet Edge. It is a video camera with a built-in solid-state hard drive for storage. The camera can store its own video and take in other camera feeds. In effect, it operates like an NVR but is less expensive and with an internal solid-state drive. Video can be viewed through a cloud browser, and Hanwha’s WAVE software, loaded on the camera, enables the management of several cameras at a site. High-res video is stored inside the camera, and any information can be shared with the cloud according to the needs of the application. i-PRO Mini i-PRO launches its own Video Insight video management system and MonitorCast access control i-PRO has fully transitioned away from Panasonic and is charting its own ambitious future path. Seeking to be “bold, trusted, and flexible,” the company is releasing a raft of new products, filling in previous gaps in the line, and bringing forward new innovations, including a full complement of AI. In addition to hardware, they have their own Video Insight video management system and MonitorCast access control, which was part of the Video Insight acquisition in 2015. An i-PRO Mini is a tiny camera, smaller than a smartphone. All cameras are NDAA compliant. People are coming together “The show has been phenomenal,” said Josh Letourneau, Chief Commercial Officer, Prosegur USA. “It’s very nice to see that people are coming back. After the pandemic, we are finally in a position of coming together. Lots of organisations are coming to see us.” Intelligence-led risk management Prosegur is a global company looking to expand aggressively in the United States, creating multiple “metropolitan service areas,” where the company’s fully integrated offerings are available. What makes the company unique is its “intelligence-led risk management,” says Josh Letourneau, adding “It’s more than AI, it’s about human intelligence, too." Prosegur sees evolution and growth opportunities in the U.S. market. “We are one of the largest companies no one has heard of,” adds Letourneau. “The show seems as back to normal as possible,” said Keith Bobrosky, President of Delta Scientific, who attended the show although his company did not exhibit, adding “There seems to be a generally positive spirit about the show this year.” Physical security protocols Bobrosky sees data centres as the next big market for his company’s vehicle barriers Bobrosky’s company has worked aggressively to avoid the impact of supply chain issues, ordering plenty of extra inventory to avoid the possibility of a part running out of stock. “We got ahead of it and are past the worst of it,” he said. Bobrosky sees data centres as the next big market for his company’s vehicle barriers. “The government will mandate physical security protocols for cybersecurity locations because they house data that affects national security,” he says. Robots and indoor drones ADT Commercial highlighted robots and indoor drones for security apps at their booth. The newest versions of the humanlike robots offer extra padding, more fluid movement, and 360-degree viewing for a better virtual reality (VR) experience, including better peripheral vision. Robots can operate for four hours without a charge and “know” when to return to the charger (to “top off” every hour). Fully autonomous indoor drones can also replace guards, flying near the ceiling and generally after business hours. The use of either robots or drones can lower costs when compared to hiring human guards. Varied uses for canines in security Glen Kucera, Chief Executive Officer, MSA Security, highlighted the capabilities of canines for explosives and firearms detection. “People don’t realise the flexibility of what they can do,” he said. Kucera says canines provide a sophisticated solution to address the escalating active shooter and criminal threat. MSA Security was acquired last year by Allied Universal, adding to the company’s varied offerings for threat detection and management. Rather than individual products, Allied Universal’s emphasis at the show was on bringing solutions together. Their message: Risk is multi-dimensional and different from one client to the next. Access control Access control needs to develop more modern interfaces to compete with new technology companies AMAG’s news at the show included a new president, David Sullivan, who highlighted AMAG’s role as one of the “last independent access control companies.” He said, “The beauty of AMAG is its installed base and loyal integrator channel.” Sullivan sees changing trends in how office space is managed in the wake of the pandemic. More workplace management applications will emerge, with one of the elements being access control. Access control also needs to develop more modern interfaces to compete with new technology companies entering the market. An encouraging sign is that AMAG had its best year ever in 2021. Orion Entrance Control Orion Entrance Control showed off one of its modern new turnstiles at the RealNetworks/SAFR booth at GSX 2022. The turnstile incorporates an access control module from Elatec to update and expand card reader functionality. Using the module streamlines Orion’s processes and avoids having to update a customer’s readers individually. The turnstile at GSX also incorporated a facial recognition system from SAFR, which could be used instead of, or in addition to, the access control reader. Balancing the cloud and on-premise systems Salient Systems is looking to balance the use of on-premise and cloud systems and emphasise data instead of video. Rather than a single market, Salient sees security as a variety of smaller markets, each focused on different needs. Salient’s customers are typically larger and have multi-site deployments with thousands of cameras. On-premise systems appeal here because they offer an element of control. Open-platform APIs Internal teams at customer sites are seeking out and finding new ways to leverage the data from video systems “People have a keen interest in control and ownership of their data,” says Sanjay Challa, Chief Product Officer, Salient Systems. Internal teams at customer sites are seeking out and finding new ways to leverage the data from video systems, and some of the uses fall outside the traditional “security” market. Open-platform application programming interfaces (APIs) enable more integration with various systems, and broader applications enable customers to leverage budgets from other stakeholders in an organisation. Add-on services “They’re unwilling to shift the entire solution to the cloud, but they want to leverage cloud technologies,” says Challa. For Salient, a cloud system provides remote access to monitor and service video installation remotely. “We enable the integrator to reach into your system to provide a higher level of service,” says Sanjay Challa. He concludes, “Our add-on services bring the best of the cloud to on-premise systems, and integrators don’t have to roll a truck to solve a problem with the system. We are focused on helping integrators succeed.”
Case studies
Up-to-date and accurate maps of the waterways are a prerequisite for safe and efficient shipping in Germany. Authorities such as the Federal Maritime and Hydrographic Agency, but also private harbour operators, are obliged to provide these in an up-to-date form at all times. The main reason for this is to avoid accidents caused by an incorrect or outdated card. This includes the classification of federal waterways, their kilometres, existing locks, lifting and barrages, other surrounding waters, places and borders. Currently, mapping is carried out by conventional ships with trained personnel, which is time-consuming and expensive. This can result in long intervals between measurements at a particular location. 3D map of the surroundings Bank areas and surface forms are monitored by an optical plan with two integrated cameras (Semi-)automated monitoring of waterways by autonomous platforms with obstacle avoidance and traffic detection could optimise this process and provide maps in less time. To this end, the Fraunhofer Institute of Optronics, System Technologies and Image Exploitation IOSB has developed an autonomous surface vehicle capable of autonomously surveying bodies of water as part of a three-year in-house research project. For this purpose, the river bed is recorded using sonar. Furthermore, the bank areas and surface structures are monitored by an optical system with two integrated industrial cameras from IDS Imaging Development Systems GmbH. The information obtained in this way is then merged and transferred to a 3D map of the surroundings. Application The precise surveying of water bodies is a demanding task. TAPS, the Fraunhofer IOSB's semi-automatic direction-finding system for rivers and lakes is able to perform this task both under and above water. The vehicle, which measures approximately 2 x 1.5 x 1 metres, travels along the relevant waterway and automatically avoids obstacles, whether stationary or moving. At a speed of two knots - which corresponds to around 3.7 kilometres per hour - such a mission can last up to 20 hours. For visual mapping of the shore areas, TAPS has two cameras attached to a mast, each pointing to starboard or port and whose fields of view do not overlap. Due to their high resolution, they allow a visual inspection of relevant infrastructure, such as quay walls, as well as 3D modelling of the shore area based on the recorded image data. Orientation of the TAPS platform GNSS and IMU data serve as the basis for picking the position and exposure of the TAPS platform "We use an automated system for intelligent image capture. As soon as one or both cameras are focussed on a predefined area of interest, image recording is started. The vehicle's own movement is also used to store only image data that is recorded from different angles and therefore offers added value in terms of content," explains Boitumelo Ruf, expert in photogrammetry in the Autonomous Robot Systems research group at Fraunhofer IOSB. GNSS (Global Navigation Satellite Systems, such as GPS) and IMU (Inertial Measurement Unit for position determination) data serve as the basis for determining the position and orientation of the TAPS platform. "When the images are captured, they are enriched with the current GNSS position data. The latter are required later for the assignment of precise coordinates," Ruf continues. COLMAP photogrammetric toolbox After data acquisition, the recorded images are transmitted together with the GNSS data to a ground control station, where a photogrammetric reconstruction is carried out. Boitumelo Ruf describes the procedure in more detail: "Among other things, we use the COLMAP photogrammetric toolbox. It uses outstanding image features to first compare the input images, calculate their relative positions and create a true-to-life 3D model of the environment." "We then use the tool to match the images pixel by pixel, i.e. we search for corresponding pixels and merge them exactly. The result is a dense 3D point cloud that is georeferenced using the GNSS positions, i.e. provided with the corresponding current coordinates." The 3D model can then be used for other tasks, such as visual inspections or bank monitoring. Robust industrial cameras defy wind and weather On the camera side, the Fraunhofer Institute relies on two uEye FA industrial cameras from IDS. The robust and resilient models with PoE are ideal for demanding environments. Camera housings, lens tubes and the screwable connectors meet the requirements of IP code IP65/67 and are thus optimally protected against dirt, dust and splash water. The robust and resilient models with PoE are ideal for demanding environments The model used has the large-format 1.1" CMOS sensor IMX304 from Sony and delivers very clear, noise-free images with a resolution of 4096 x 3000 pixels. Thanks to its remarkable dynamic range and very high sensitivity, the global shutter sensor of the second pixel generation of the Pregius series is particularly suitable for metrology applications, among others. It was precisely these characteristics that were decisive for the Fraunhofer IOSB's choice of camera. In addition to robustness and weather protection, important requirements for the cameras included a compact form factor and high image resolution to enable detailed visual inspections. The sensor should also offer a high dynamic range in order to capture images with a high level of detail in both sunny and shady areas. Integration via the standard GigE Vision interface enables the development and use of one driver for several systems with different cameras. Outlook The shortage of skilled labour is also a major issue in the surveying of waterways. Automated mapping of the waterways could not only reduce costs but also the time and, above all, the labour required. The aim of the TAPS project was to develop a prototype for this task and to demonstrate its potential in relevant scenarios. As a research organisation, Fraunhofer typically develops technologies up to a level at which the functionality and suitability of the system have been proven. The next step is now cooperation with industrial partners. Dr. Janko Petereit, head of the Autonomous Robot Systems research group at Fraunhofer IOSB, explains: "We are actively looking for partners to take this final step towards commercialisation together. In view of the positive results of our initial tests and the increasing demand for accurate, up-to-date waterway maps, we expect strong demand for our technology in the coming years. The knowledge gained can be used in a variety of ways. Autonomous watercraft can be used to transport people and goods by sea or inland waterways. The excavation of waterways and the autonomous surveying of fairways are also conceivable. “ The project demonstrates the high potential of the interaction between robot systems and digital image processing. The cards could be reshuffled in the future, particularly with regard to visual environment detection and scene interpretation.
IDEMIA Public Security North America, the premium provider of convenient and trusted biometric-based solutions, has announced the launch of the Iowa mobile ID to Samsung Wallet, in collaboration with the Iowa Department of Transportation (Iowa DOT) and Samsung. Iowa residents can now securely store their mobile ID in their Samsung Wallet and start using it to easily assert their identity from their mobile phone at TSA checkpoints at the Des Moines and Eastern Iowa airports, as well as 25 other participating airports in the country and other participating businesses. Free Iowa Mobile ID app Iowans can easily access their mobile ID in the Samsung Wallet by simply tapping their phone The launch of Iowa mobile ID in the Samsung Wallet brings elevated convenience and security for Iowans with Samsung smartphones for airport security screening, age-restricted products, and other identity checks. Iowans can easily access their mobile ID in the Samsung Wallet by simply tapping their phone near the mobile ID reader or having the mobile ID reader scan the QR code. Iowans can also continue to access their mobile ID through the free Iowa Mobile ID app, which IDEMIA built and rolled out for Iowa in October 2023. "We are pleased to add the Iowa mobile ID in the Samsung Wallet to the list of acceptable IDs at our security checkpoints. Travellers who want to take advantage of this new capability will find that their Iowa mobile ID is a convenient option when going through the security process. TSA will continue to embrace technology that improves security effectiveness while streamlining the passenger experience at airports," John Bright, TSA Iowa Federal Security Director. Partnership with Samsung "We are proud to expand our partnership with Samsung and the Iowa Department of Transportation (Iowa DOT) to bring mobile driver’s licences and state IDs to Samsung Wallet in Iowa and help accelerate the adoption of mobile ID in the state." Mobile IDs are authenticated and issued by state DMVs or MVDs" "As a convenient and highly secure way to store state-issued IDs and drivers licenses, mobile IDs are authenticated and issued by state DMVs or MVDs and ensure personal information is securely stored on the user’s device, with only the user having control over what personal information is shared," Donnie Scott, CEO of IDEMIA Public Security North America. Long-standing partnership As a pioneer in identity solutions and credentials issuance with a long-standing partnership with government agencies and a commitment to privacy by design, end-to-end security and interoperability, the Iowa DOT partnered with IDEMIA to launch mobile ID in Iowa in October 2023. Later that year, in December 2023, Samsung collaborated with IDEMIA, alongside the Arizona Department of Transportation Motor Vehicle Division (AZ MVD), to roll out mobile ID to the Samsung Wallet in Arizona.
Geekplus, the global pioneer in mobile robot and smart logistics solutions, has deployed the first Shelf-to-Person PopPick project in the Nordics for one of the biggest online pharmacy wholesalers in the region, Med24.dk. System Teknik partnered on the Denmark project, which includes three PopPick stations and 30 Shelf-to-Person robots, bringing a flexible solution to a region where fixed automation still dominates. "With the rise of e-commerce, Med24.dk had been struggling with huge sales growth coupled with fast delivery demands from customers in Denmark, Norway, Sweden searching for pharmacy, health and beauty products. Peak season events had also caused considerable strain to their operations," said Blond Shkodrani, channel partner manager for the Nordics at Geekplus. "Due to their overwhelming success, Med24.dk needed a modular, automated order fulfilment solution for fast, efficient order fulfilment." Order fulfilment challenges Shelf-to-Person takes goods of all sizes while removing the need for infrastructure investment The Geekplus modular Shelf-to-Person solution optimises warehouse operations using mobile robots to transport shelves. In a region where fixed and cubic solutions have been the trend during recent years, Shelf-to-Person handles goods of all sizes while removing the need for infrastructure investment, making it the most flexible response to order fulfilment challenges. PopPick workstations use two retrieval arms and four presentation locations to present pickers with multiple, moveable 78-tote racks at one time, resulting in an industry-pioneering throughput of 450 totes per hour. PopPick can store goods of all types and sizes; the solution is not limited to small pieces and improves ergonomics for workers while picking. It also takes up less space than traditional systems, so customers can use more stations without adding facility space. Mobile order fulfilment solutions "We are very pleased to invest in flooring robots from Geekplus," said Med24.dk CEO Nils Træholt. "We believe that this new and innovative technology can help us realise our growth ambitions, while maintaining good delivery times for the benefit of our customers." Morten Kirch, System Teknik's CSO, added: "Due to Med24.dk's growth, we are thrilled to be able to deliver a tailor-made, automated solution that matches their needs." Geekplus offers a suite of Goods-to-Person mobile order fulfilment solutions-the only comprehensive robotic offering controlled by a single software platform. "Through trusted partners like System Teknik, we're showing customers all over Europe that Geekplus truly is a one-stop shop for modular warehouse automation," Shkodrani said.
Richard Thorp has been fascinated with aviation since childhood. A self-described “aviation geek,” Thorp is now the Chief Technology Officer at Swissport International AG, where he leads IT infrastructure strategy for the world’s largest ground-handling company, ensuring seamless operations across 276 airports in 45 countries, handling approximately 247 million airline passengers per year, as of the end of 2024. “If we were an airline, we’d actually be the biggest airline in the world in terms of a number of passengers we support and handle,” he says. Security challenges Swissport’s goal is to make a tangible impact on people’s lives by enabling smooth air travel Swissport’s goal is to make a tangible impact on people’s lives by enabling smooth air travel. “If the things we do get people to their destinations safely and on time, then magically, we become more successful and profitable as an organisation,” he says. But casting that spell had been challenging for Swissport. Three years ago, legacy IT leadership at Swissport had overcome network challenges with Cato, but more work was needed to address their security challenges, particularly in securing endpoints. Thorp and Swissport CISO, Giles Ashton-Roberts, joined Swissport in the middle of the Cato deployment. Having deep experience with a legacy zero trust provider, they were skeptical that Cato could meet Swissport’s requirements. Cato platform Over the next 10 months of meetings, investigation, and testing Thorp and Ashton-Roberts challenged Cato, ultimately changing their perspective. “IT is no longer seen as a blocker; it just works,” says Thorp. “I relax a bit more with the Cato platform around. It’s given us holistic way of protecting ourselves today, and a secure foundation for everything we want to do in the future.” The challenges of a global, always-on operation Swissport’s network helps millions of passengers, cargo shipments, and lounges worldwide Swissport’s network supports millions of passengers, cargo shipments, and lounges worldwide. Three years ago, scale was an enormous challenge—ensuring reliable connectivity for operations spanning locations and time zones. The company relied on a mix of MPLS and regional SD-WAN solutions across its now 320+ sites and airport locations. But bandwidth limitations and performance variability impacted many applications, including cloud-based, mission-critical applications. As a result of that complicated network, expanding to new locations was resource-intensive, requiring manual setup and multiple vendor dependencies. Differences between networking tools made troubleshooting inconsistent and time-consuming. The IT team in turn had to maintain expertise in multiple networking technologies, increasing operational overhead. What security inspection existed for unencrypted traffic Visibility was an enormous challenge. With multiple network platforms in place, Swissport’s IT team lacked a centralised view of network performance and security threats. “In the past, working with multiple systems meant inconsistency,” says Thorp. “Different platforms required different configurations, which complicated troubleshooting and made security enforcement a challenge.” Swissport relied on a patchwork of security appliances, including firewalls and web gateways. Remote users are connected through different VPN servers deployed across different regions. The complex appliance stack required manual maintenance and lacked centralised visibility and control. Security patching was manual and error-prone and implementing consistent security policies was practically impossible, weakening Swissport’s security posture. What security inspection existed was relegated to unencrypted traffic due to the well-founded concern that inspecting encrypted traffic could break the application experience that in this case were airline partners’ systems. Finally, the lack of consistent, advanced threat detection worldwide limited Swissport’s ability to detect and stop threats. Visibility differentiates the Cato SASE cloud platform Thorp and the IT team had initially leaned away towards deploying that architecture Recognising these inefficiencies, Swissport’s legacy IT team initiated the Cato relationship, connecting many of the now 320+ sites and instances in AWS and Azure to the Cato SASE Cloud Platform. When Thorp and the new IT leadership joined Swissport, about two-thirds of the connections had been deployed. Having been familiar with a legacy cybersecurity provider, Thorp and the IT team had initially leaned away towards deploying that architecture. Hearing about the value of Cato they decided to have a closer look. “What really drew me to Cato is the visibility the platform provides. It’s incredibly easy to pinpoint connectivity issues, analyse traffic patterns, and secure our network from a single interface,” says Thorp. Cato uniquely stores the metadata of all enterprise traffic crossing the Cato SASE Cloud Platform — whether to the Internet or another location — from all endpoints — in the office and outside of it — in a single data store. This incredible resource provides Cato customers with deep, end-to-end insight into their complete network. Much improved security and a better network With a platform that is resilient, secure, and easy to manage, Swissport has been able to take a more proactive approach to security, streamline IT processes, and ensure a seamless digital experience for employees across the globe. Advanced threat prevention now operates globally and protects against malware and ransomware even in encrypted traffic. “Cato’s TLS Inspection gives us the ability to inspect encrypted traffic while avoiding unintended service disruptions,” says Ashton-Roberts. “It’s been a major improvement to our security posture.” Fine-grained access control through the always-on Cato Client connects remote users to Cato, granting access only to permitted resources. The Cato Client fully implements zero trust principles and operates outside and inside the office under one common policy set. “With Cato, every device—whether in a Swissport office or in an airport lounge—operates under the same set of security policies. That level of consistency wasn’t possible before,” says Ashton-Roberts. Deploying new network sites Cato not only delivers optimised network version worldwide but also makes deploying new networks Access is across the Cato Global Private Backbone built into the Cato SASE Cloud Platform, delivering an exceptional, secure user experience anywhere in the world. Cato not only delivers optimised network performance worldwide but also makes deploying new network sites effortless. “Connecting new airlines or contracts now takes just a few clicks,” says Thorp. Thorp’s team has also dramatically reduced network resolution times. “We recently identified and solved a performance issue in a South African location that would have taken us days before Cato,” says Thorp. “Within 15 minutes, our team identified excessive database traffic, blocked the device, and restored normal operations.” Transforming IT by transforming the infrastructure The transformative impact of the Cato SASE Cloud Platform on the IT team has been profound. Previously, managing multiple networking platforms required maintaining expertise in diverse technologies, creating an operational burden. The IT staff was constantly troubleshooting connectivity issues, manually configuring security appliances, and dealing with inconsistent policies across different locations. The shift to Cato not only simplified management but also allowed the IT team to focus on higher-value strategic initiatives. “Before Cato, we had to maintain different skill sets for different platforms, which spread the team thin. Now, we have one standardised system that allows us to be much more efficient,” Thorp says. Newfound network visibility Swissport has been able to optimise resource allocation and improve overall productivity By consolidating security and networking into a single platform, Swissport has been able to optimise resource allocation and improve overall productivity. The newfound network visibility has also brought a shift from reactive to a proactive IT strategy that has helped the company ensure consistent service delivery across its global operations. “For me, Cato future proofs Swissport’s IT infrastructure,” says Thorp. “The platform constantly evolves, adapts to new technologies, and provides the visibility and security we need to support our business today and tomorrow.” Partnership with Cato proved unique The success of Swissport’s IT transformation was built on more than just technology—it was about forming a strong, collaborative relationship with Cato Networks. From the start, Cato worked closely with Swissport to understand its unique challenges and deliver tailored solutions that addressed its global security and networking needs. “We worked directly with Cato’s product team to enhance capabilities—not just for us, but for all customers,” says Thorp. The success of Swissport’s IT transformation was built on more than just technology Features requested by Swissport were implemented on schedule, unlike other vendors who provided only lip service. Thorp says, “Many vendors say they listen, but Cato actually delivers on what they promise.” This close partnership has given Swissport confidence that its evolving needs will continue to be met as Cato refines its platform. “With Cato, we’re not just another customer; we’re part of a continuous innovation cycle that ensures our IT infrastructure remains future-ready,” says Thorp. “It’s rare to find a vendor so responsive and committed to delivering what they promise.” Looking ahead to the future Swissport IT requirements continue to evolve with Cato remaining a key pillar. “With Cato in place, we know that our network is not the limiting factor in our growth,” Thorp explains. The ongoing partnership between Swissport and Cato ensures that as technology continues to evolve, Swissport’s IT infrastructure remains secure, scalable, and adaptable to the demands of a fast-paced aviation industry. On a personal level, Cato has given Thorp peace of mind. “I relax a bit more with the Cato platform around. It’s given us a holistic way of protecting ourselves today and a secure foundation for everything we want to do in the future. Swissport’s IT leadership now can focus on innovation rather than crisis management.”
Like any retail franchise, car dealerships that have multiple locations nationwide require comprehensive, reliable, and scalable video surveillance solutions to protect their businesses. With dealership theft increasing by 7% since 2021, protecting high-value inventory, mitigating liability risks, and ensuring compliance with video data retention standards have become critical priorities. Future surveillance solutions BCD is vital to guarding functions, protecting valuable assets, and maintaining peace of mind Additionally, managing surveillance across multiple sites demands systems that are easy to deploy, cyber-hardened, and capable of centralised oversight. As dealerships continue to expand, investing in future-ready surveillance solutions with a trusted systems builder like BCD is essential to safeguarding operations, protecting valuable assets, and maintaining peace of mind. The challenge Car dealerships face distinct challenges when it comes to security and operations, such as: Asset Protection: Showrooms and lots house high-value vehicles and parts, making them prime targets for theft and vandalism. Cybersecurity Threats: Surveillance systems needed to be cyber-hardened to prevent breaches that could compromise sensitive footage or customer information. Reliable Recording: Continuous operation is essential to ensure no gaps in security coverage, particularly during off-hours or high-traffic events. Scalable Storage Across Locations: With multiple sites generating large volumes of video footage, dealerships need a solution to store data for 30-90 days to comply with industry regulations and internal policies. Centralised Management: Managing surveillance across dozens of locations required a solution that simplified oversight while enabling scalability for future growth. The solution BCD’s All-in-One Hybrid Cloud NVR is a cutting-edge video surveillance solution designed to address these challenges. The solution offers: Integrated PoE Switch: The All-in-One NVR includes a built-in Power over Ethernet (PoE) switch, simplifying installation and reducing the need for additional network infrastructure, which saves time and costs while simplifying the overall infrastructure. Cyber-Hardened Security: BCD’s solutions are all certified as cyber-hardened solutions to maximise data protection and minimise the risk of data breaches. Always-On Recording: With features like RAID storage for redundancy and failover capabilities, along with the Harmonise Remote Monitoring and Management plugin, the All-in-One solution ensures uninterrupted recording, and with customised notifications, can mitigate hardware or network disruptions. Hybrid Cloud Architecture: The All-in-One NVR provides 80TB of local storage for immediate access to live footage while seamlessly integrating with cloud storage for long-term retention. This hybrid approach ensures franchises can store footage for 30 days or more without overwhelming local resources. Centralised, Scalable Management: BCD’s solution is simple to deploy and typically takes 30 minutes or less, allowing franchises to monitor and manage surveillance across all locations from a single interface, simplifying administration and reducing operational overhead. The results Deploying BCD’s All-in-One Hybrid Cloud solution has the potential to drive significant improvements across multiple aspects of a franchise’s video surveillance operations, including: Enhanced Security: Reliable and cyber-hardened surveillance protect valuable inventory and reduce the risk of theft or vandalism. Continuous Uptime: The system’s failover mechanisms along with Harmonise Remote Monitoring and Management Plug-in ensures 24/7 recording with no interruptions, providing full coverage for liability and security events. Regulatory Compliance: Hybrid cloud storage allows each location to easily meet the 30-90-day retention requirement without costly local storage upgrades. Operational Efficiency: Centralized management and user-friendly tools reduce the complexity of overseeing surveillance across multiple locations, cutting costs and improving oversight. Future-Ready Scalability: As franchises expand, BCD’s solutions are designed to scale effortlessly to accommodate new locations and increased storage demands, providing a future-proof investment. Conclusion BCD’s All-in-One Hybrid Cloud NVR is an ideal solution for national franchises, such as car dealerships, and offers a secure, reliable, and scalable video data infrastructure. By leveraging hybrid cloud technology and simplified management, franchises will experience peace of mind knowing their assets are protected, compliance requirements are met, and their operations will be optimised for growth.
Established in 1997, Dubai-based BMA International operates fashion retail in the Middle East and Asia across the Kingdom of Saudi Arabia (KSA), United Arab Emirates (UAE), Bahrain, Oman, Kuwait and Qatar with more than 250 stores offering two major brands — Redtag and twenty4. BMA’s steady growth is a testament to its focus on building trust with its shoppers, employees, suppliers and stakeholders to create a company that is people-centric, ambitious and results-oriented. Challenge Fraud is a common problem in the retail sector, particularly within large chains with hundreds of locations and tens of thousands of employees. BMA’s retail stores were no exception. Following an internal audit, security of point-of-sale (POS) terminals in retail outlets were identified as a serious concern, particularly the misuse of floor supervisors’ credentials to access terminals and modify or cancel transactions. The problem persisted even after BMA switched from passwords to a smart card-based authentication system The problem persisted even after BMA switched from passwords to a smart card-based authentication system. The most common issues involved supervisors leaving smart cards with cashiers to use in their absence and failing to return the cards when separation from an employer occurs — a frequent occurrence as many of BMA’s retail employees are expatriates who often return to their home countries. Fraudulent use of the smart card was also a common problem. Once a sale was completed and the customer had left the store with their purchased items, the smart card could be used to improperly access the system so the cashier could void the transaction and pocket the “refund,” resulting in both monetary and inventory losses. Biometric-based system “BMA’s internal auditors were concerned with the lack of control over the cards and the potential for fraudulent transactions due to their mishandling. They observed clear gaps in security and authentication practices that led directly to fraud and revenue leakage, resulting in the Internal Audit Committee recommending to the BMA Board of Directors that action be taken to plug the security holes by tightening the authentication process,” said Nainan M. Kurian, CEO of Technowave International LLC. The decision was made to transition authentication to a biometric-based system that would provide the required security at a competitive price that aligned with the aesthetics of the retail stores. The system also needed to be compatible with the Oracle Retail Xstore Office Cloud Service, which BMA International was adopting across its brands. Solution A fingerprint reader from HID is ideal for use by multiple people in a shared environment BMA International and its technology partner, Technowave International LLC, determined that the HID DigitalPersona® 4500 Fingerprint Reader met all their requirements — a decision supported by recommendations from other retailers that had deployed the product, and by the fact that competitive solutions were incompatible with Oracle Retail Xstore, a crucial requirement. A USB peripheral with a compact design to conserve space, this fingerprint reader from HID is ideal for use by multiple people in a shared environment. Its professional, modern design looks elegant in retail settings while offering superior authentication control via biometric functionality that uses optical scanning technology to achieve excellent image quality and reliability. HID DigitalPersona 4500 Fingerprint Reader With this easy-to-use technology, floor supervisors simply place their finger on the reader window, which rapidly captures and encrypts the fingerprint image, and then provides a red flash as a visual cue indicating that it was properly captured. That image is sent to the DigitalPersona FingerJetTM biometric engine for verification, and once the user has been authenticated, access to the POS terminal is granted. “Deploying the HID DigitalPersona 4500 Fingerprint Reader was simple and caused no disruption to retail operations. It paved the way for significant reduction in the malpractice that had been occurring with the smart card system,” said Kurian. Result Since deploying more than 1,100 HID fingerprint readers in retail outlets across KSA, UAE, Oman, Bahrain, Kuwait and Qatar, BMA has eliminated nearly all POS fraud and abuse. The system has also driven tangible improvements in the attendance and punctuality of floor supervisors, who must now be physically present in the store for authentication to take place. The HID authentication system is also capable of multiple types of authentications — providing flexibility that is appreciated by users who work at multiple locations. “Because the HID DigitalPersona 4500 Fingerprint Reader requires proof of presence for authentication, there is greater accountability among supervisors which resulted in immediate cessation of POS fraud and stopped both revenue and inventory leakage. The exceptional support provided by HID Global has also allowed BMA to take full advantage of the system’s functionality and flexibility,” said Kurian.
Up-to-date and accurate maps of the waterways are a prerequisite for safe and efficient shipping in Germany. Authorities such as the Federal Maritime and Hydrographic Agency, but also private harbour operators, are obliged to provide these in an up-to-date form at all times. The main reason for this is to avoid accidents caused by an incorrect or outdated card. This includes the classification of federal waterways, their kilometres, existing locks, lifting and barrages, other surrounding waters, places and borders. Currently, mapping is carried out by conventional ships with trained personnel, which is time-consuming and expensive. This can result in long intervals between measurements at a particular location. 3D map of the surroundings Bank areas and surface forms are monitored by an optical plan with two integrated cameras (Semi-)automated monitoring of waterways by autonomous platforms with obstacle avoidance and traffic detection could optimise this process and provide maps in less time. To this end, the Fraunhofer Institute of Optronics, System Technologies and Image Exploitation IOSB has developed an autonomous surface vehicle capable of autonomously surveying bodies of water as part of a three-year in-house research project. For this purpose, the river bed is recorded using sonar. Furthermore, the bank areas and surface structures are monitored by an optical system with two integrated industrial cameras from IDS Imaging Development Systems GmbH. The information obtained in this way is then merged and transferred to a 3D map of the surroundings. Application The precise surveying of water bodies is a demanding task. TAPS, the Fraunhofer IOSB's semi-automatic direction-finding system for rivers and lakes is able to perform this task both under and above water. The vehicle, which measures approximately 2 x 1.5 x 1 metres, travels along the relevant waterway and automatically avoids obstacles, whether stationary or moving. At a speed of two knots - which corresponds to around 3.7 kilometres per hour - such a mission can last up to 20 hours. For visual mapping of the shore areas, TAPS has two cameras attached to a mast, each pointing to starboard or port and whose fields of view do not overlap. Due to their high resolution, they allow a visual inspection of relevant infrastructure, such as quay walls, as well as 3D modelling of the shore area based on the recorded image data. Orientation of the TAPS platform GNSS and IMU data serve as the basis for picking the position and exposure of the TAPS platform "We use an automated system for intelligent image capture. As soon as one or both cameras are focussed on a predefined area of interest, image recording is started. The vehicle's own movement is also used to store only image data that is recorded from different angles and therefore offers added value in terms of content," explains Boitumelo Ruf, expert in photogrammetry in the Autonomous Robot Systems research group at Fraunhofer IOSB. GNSS (Global Navigation Satellite Systems, such as GPS) and IMU (Inertial Measurement Unit for position determination) data serve as the basis for determining the position and orientation of the TAPS platform. "When the images are captured, they are enriched with the current GNSS position data. The latter are required later for the assignment of precise coordinates," Ruf continues. COLMAP photogrammetric toolbox After data acquisition, the recorded images are transmitted together with the GNSS data to a ground control station, where a photogrammetric reconstruction is carried out. Boitumelo Ruf describes the procedure in more detail: "Among other things, we use the COLMAP photogrammetric toolbox. It uses outstanding image features to first compare the input images, calculate their relative positions and create a true-to-life 3D model of the environment." "We then use the tool to match the images pixel by pixel, i.e. we search for corresponding pixels and merge them exactly. The result is a dense 3D point cloud that is georeferenced using the GNSS positions, i.e. provided with the corresponding current coordinates." The 3D model can then be used for other tasks, such as visual inspections or bank monitoring. Robust industrial cameras defy wind and weather On the camera side, the Fraunhofer Institute relies on two uEye FA industrial cameras from IDS. The robust and resilient models with PoE are ideal for demanding environments. Camera housings, lens tubes and the screwable connectors meet the requirements of IP code IP65/67 and are thus optimally protected against dirt, dust and splash water. The robust and resilient models with PoE are ideal for demanding environments The model used has the large-format 1.1" CMOS sensor IMX304 from Sony and delivers very clear, noise-free images with a resolution of 4096 x 3000 pixels. Thanks to its remarkable dynamic range and very high sensitivity, the global shutter sensor of the second pixel generation of the Pregius series is particularly suitable for metrology applications, among others. It was precisely these characteristics that were decisive for the Fraunhofer IOSB's choice of camera. In addition to robustness and weather protection, important requirements for the cameras included a compact form factor and high image resolution to enable detailed visual inspections. The sensor should also offer a high dynamic range in order to capture images with a high level of detail in both sunny and shady areas. Integration via the standard GigE Vision interface enables the development and use of one driver for several systems with different cameras. Outlook The shortage of skilled labour is also a major issue in the surveying of waterways. Automated mapping of the waterways could not only reduce costs but also the time and, above all, the labour required. The aim of the TAPS project was to develop a prototype for this task and to demonstrate its potential in relevant scenarios. As a research organisation, Fraunhofer typically develops technologies up to a level at which the functionality and suitability of the system have been proven. The next step is now cooperation with industrial partners. Dr. Janko Petereit, head of the Autonomous Robot Systems research group at Fraunhofer IOSB, explains: "We are actively looking for partners to take this final step towards commercialisation together. In view of the positive results of our initial tests and the increasing demand for accurate, up-to-date waterway maps, we expect strong demand for our technology in the coming years. The knowledge gained can be used in a variety of ways. Autonomous watercraft can be used to transport people and goods by sea or inland waterways. The excavation of waterways and the autonomous surveying of fairways are also conceivable. “ The project demonstrates the high potential of the interaction between robot systems and digital image processing. The cards could be reshuffled in the future, particularly with regard to visual environment detection and scene interpretation.
IDEMIA Public Security North America, the premium provider of convenient and trusted biometric-based solutions, has announced the launch of the Iowa mobile ID to Samsung Wallet, in collaboration with the Iowa Department of Transportation (Iowa DOT) and Samsung. Iowa residents can now securely store their mobile ID in their Samsung Wallet and start using it to easily assert their identity from their mobile phone at TSA checkpoints at the Des Moines and Eastern Iowa airports, as well as 25 other participating airports in the country and other participating businesses. Free Iowa Mobile ID app Iowans can easily access their mobile ID in the Samsung Wallet by simply tapping their phone The launch of Iowa mobile ID in the Samsung Wallet brings elevated convenience and security for Iowans with Samsung smartphones for airport security screening, age-restricted products, and other identity checks. Iowans can easily access their mobile ID in the Samsung Wallet by simply tapping their phone near the mobile ID reader or having the mobile ID reader scan the QR code. Iowans can also continue to access their mobile ID through the free Iowa Mobile ID app, which IDEMIA built and rolled out for Iowa in October 2023. "We are pleased to add the Iowa mobile ID in the Samsung Wallet to the list of acceptable IDs at our security checkpoints. Travellers who want to take advantage of this new capability will find that their Iowa mobile ID is a convenient option when going through the security process. TSA will continue to embrace technology that improves security effectiveness while streamlining the passenger experience at airports," John Bright, TSA Iowa Federal Security Director. Partnership with Samsung "We are proud to expand our partnership with Samsung and the Iowa Department of Transportation (Iowa DOT) to bring mobile driver’s licences and state IDs to Samsung Wallet in Iowa and help accelerate the adoption of mobile ID in the state." Mobile IDs are authenticated and issued by state DMVs or MVDs" "As a convenient and highly secure way to store state-issued IDs and drivers licenses, mobile IDs are authenticated and issued by state DMVs or MVDs and ensure personal information is securely stored on the user’s device, with only the user having control over what personal information is shared," Donnie Scott, CEO of IDEMIA Public Security North America. Long-standing partnership As a pioneer in identity solutions and credentials issuance with a long-standing partnership with government agencies and a commitment to privacy by design, end-to-end security and interoperability, the Iowa DOT partnered with IDEMIA to launch mobile ID in Iowa in October 2023. Later that year, in December 2023, Samsung collaborated with IDEMIA, alongside the Arizona Department of Transportation Motor Vehicle Division (AZ MVD), to roll out mobile ID to the Samsung Wallet in Arizona.
Geekplus, the global pioneer in mobile robot and smart logistics solutions, has deployed the first Shelf-to-Person PopPick project in the Nordics for one of the biggest online pharmacy wholesalers in the region, Med24.dk. System Teknik partnered on the Denmark project, which includes three PopPick stations and 30 Shelf-to-Person robots, bringing a flexible solution to a region where fixed automation still dominates. "With the rise of e-commerce, Med24.dk had been struggling with huge sales growth coupled with fast delivery demands from customers in Denmark, Norway, Sweden searching for pharmacy, health and beauty products. Peak season events had also caused considerable strain to their operations," said Blond Shkodrani, channel partner manager for the Nordics at Geekplus. "Due to their overwhelming success, Med24.dk needed a modular, automated order fulfilment solution for fast, efficient order fulfilment." Order fulfilment challenges Shelf-to-Person takes goods of all sizes while removing the need for infrastructure investment The Geekplus modular Shelf-to-Person solution optimises warehouse operations using mobile robots to transport shelves. In a region where fixed and cubic solutions have been the trend during recent years, Shelf-to-Person handles goods of all sizes while removing the need for infrastructure investment, making it the most flexible response to order fulfilment challenges. PopPick workstations use two retrieval arms and four presentation locations to present pickers with multiple, moveable 78-tote racks at one time, resulting in an industry-pioneering throughput of 450 totes per hour. PopPick can store goods of all types and sizes; the solution is not limited to small pieces and improves ergonomics for workers while picking. It also takes up less space than traditional systems, so customers can use more stations without adding facility space. Mobile order fulfilment solutions "We are very pleased to invest in flooring robots from Geekplus," said Med24.dk CEO Nils Træholt. "We believe that this new and innovative technology can help us realise our growth ambitions, while maintaining good delivery times for the benefit of our customers." Morten Kirch, System Teknik's CSO, added: "Due to Med24.dk's growth, we are thrilled to be able to deliver a tailor-made, automated solution that matches their needs." Geekplus offers a suite of Goods-to-Person mobile order fulfilment solutions-the only comprehensive robotic offering controlled by a single software platform. "Through trusted partners like System Teknik, we're showing customers all over Europe that Geekplus truly is a one-stop shop for modular warehouse automation," Shkodrani said.
Richard Thorp has been fascinated with aviation since childhood. A self-described “aviation geek,” Thorp is now the Chief Technology Officer at Swissport International AG, where he leads IT infrastructure strategy for the world’s largest ground-handling company, ensuring seamless operations across 276 airports in 45 countries, handling approximately 247 million airline passengers per year, as of the end of 2024. “If we were an airline, we’d actually be the biggest airline in the world in terms of a number of passengers we support and handle,” he says. Security challenges Swissport’s goal is to make a tangible impact on people’s lives by enabling smooth air travel Swissport’s goal is to make a tangible impact on people’s lives by enabling smooth air travel. “If the things we do get people to their destinations safely and on time, then magically, we become more successful and profitable as an organisation,” he says. But casting that spell had been challenging for Swissport. Three years ago, legacy IT leadership at Swissport had overcome network challenges with Cato, but more work was needed to address their security challenges, particularly in securing endpoints. Thorp and Swissport CISO, Giles Ashton-Roberts, joined Swissport in the middle of the Cato deployment. Having deep experience with a legacy zero trust provider, they were skeptical that Cato could meet Swissport’s requirements. Cato platform Over the next 10 months of meetings, investigation, and testing Thorp and Ashton-Roberts challenged Cato, ultimately changing their perspective. “IT is no longer seen as a blocker; it just works,” says Thorp. “I relax a bit more with the Cato platform around. It’s given us holistic way of protecting ourselves today, and a secure foundation for everything we want to do in the future.” The challenges of a global, always-on operation Swissport’s network helps millions of passengers, cargo shipments, and lounges worldwide Swissport’s network supports millions of passengers, cargo shipments, and lounges worldwide. Three years ago, scale was an enormous challenge—ensuring reliable connectivity for operations spanning locations and time zones. The company relied on a mix of MPLS and regional SD-WAN solutions across its now 320+ sites and airport locations. But bandwidth limitations and performance variability impacted many applications, including cloud-based, mission-critical applications. As a result of that complicated network, expanding to new locations was resource-intensive, requiring manual setup and multiple vendor dependencies. Differences between networking tools made troubleshooting inconsistent and time-consuming. The IT team in turn had to maintain expertise in multiple networking technologies, increasing operational overhead. What security inspection existed for unencrypted traffic Visibility was an enormous challenge. With multiple network platforms in place, Swissport’s IT team lacked a centralised view of network performance and security threats. “In the past, working with multiple systems meant inconsistency,” says Thorp. “Different platforms required different configurations, which complicated troubleshooting and made security enforcement a challenge.” Swissport relied on a patchwork of security appliances, including firewalls and web gateways. Remote users are connected through different VPN servers deployed across different regions. The complex appliance stack required manual maintenance and lacked centralised visibility and control. Security patching was manual and error-prone and implementing consistent security policies was practically impossible, weakening Swissport’s security posture. What security inspection existed was relegated to unencrypted traffic due to the well-founded concern that inspecting encrypted traffic could break the application experience that in this case were airline partners’ systems. Finally, the lack of consistent, advanced threat detection worldwide limited Swissport’s ability to detect and stop threats. Visibility differentiates the Cato SASE cloud platform Thorp and the IT team had initially leaned away towards deploying that architecture Recognising these inefficiencies, Swissport’s legacy IT team initiated the Cato relationship, connecting many of the now 320+ sites and instances in AWS and Azure to the Cato SASE Cloud Platform. When Thorp and the new IT leadership joined Swissport, about two-thirds of the connections had been deployed. Having been familiar with a legacy cybersecurity provider, Thorp and the IT team had initially leaned away towards deploying that architecture. Hearing about the value of Cato they decided to have a closer look. “What really drew me to Cato is the visibility the platform provides. It’s incredibly easy to pinpoint connectivity issues, analyse traffic patterns, and secure our network from a single interface,” says Thorp. Cato uniquely stores the metadata of all enterprise traffic crossing the Cato SASE Cloud Platform — whether to the Internet or another location — from all endpoints — in the office and outside of it — in a single data store. This incredible resource provides Cato customers with deep, end-to-end insight into their complete network. Much improved security and a better network With a platform that is resilient, secure, and easy to manage, Swissport has been able to take a more proactive approach to security, streamline IT processes, and ensure a seamless digital experience for employees across the globe. Advanced threat prevention now operates globally and protects against malware and ransomware even in encrypted traffic. “Cato’s TLS Inspection gives us the ability to inspect encrypted traffic while avoiding unintended service disruptions,” says Ashton-Roberts. “It’s been a major improvement to our security posture.” Fine-grained access control through the always-on Cato Client connects remote users to Cato, granting access only to permitted resources. The Cato Client fully implements zero trust principles and operates outside and inside the office under one common policy set. “With Cato, every device—whether in a Swissport office or in an airport lounge—operates under the same set of security policies. That level of consistency wasn’t possible before,” says Ashton-Roberts. Deploying new network sites Cato not only delivers optimised network version worldwide but also makes deploying new networks Access is across the Cato Global Private Backbone built into the Cato SASE Cloud Platform, delivering an exceptional, secure user experience anywhere in the world. Cato not only delivers optimised network performance worldwide but also makes deploying new network sites effortless. “Connecting new airlines or contracts now takes just a few clicks,” says Thorp. Thorp’s team has also dramatically reduced network resolution times. “We recently identified and solved a performance issue in a South African location that would have taken us days before Cato,” says Thorp. “Within 15 minutes, our team identified excessive database traffic, blocked the device, and restored normal operations.” Transforming IT by transforming the infrastructure The transformative impact of the Cato SASE Cloud Platform on the IT team has been profound. Previously, managing multiple networking platforms required maintaining expertise in diverse technologies, creating an operational burden. The IT staff was constantly troubleshooting connectivity issues, manually configuring security appliances, and dealing with inconsistent policies across different locations. The shift to Cato not only simplified management but also allowed the IT team to focus on higher-value strategic initiatives. “Before Cato, we had to maintain different skill sets for different platforms, which spread the team thin. Now, we have one standardised system that allows us to be much more efficient,” Thorp says. Newfound network visibility Swissport has been able to optimise resource allocation and improve overall productivity By consolidating security and networking into a single platform, Swissport has been able to optimise resource allocation and improve overall productivity. The newfound network visibility has also brought a shift from reactive to a proactive IT strategy that has helped the company ensure consistent service delivery across its global operations. “For me, Cato future proofs Swissport’s IT infrastructure,” says Thorp. “The platform constantly evolves, adapts to new technologies, and provides the visibility and security we need to support our business today and tomorrow.” Partnership with Cato proved unique The success of Swissport’s IT transformation was built on more than just technology—it was about forming a strong, collaborative relationship with Cato Networks. From the start, Cato worked closely with Swissport to understand its unique challenges and deliver tailored solutions that addressed its global security and networking needs. “We worked directly with Cato’s product team to enhance capabilities—not just for us, but for all customers,” says Thorp. The success of Swissport’s IT transformation was built on more than just technology Features requested by Swissport were implemented on schedule, unlike other vendors who provided only lip service. Thorp says, “Many vendors say they listen, but Cato actually delivers on what they promise.” This close partnership has given Swissport confidence that its evolving needs will continue to be met as Cato refines its platform. “With Cato, we’re not just another customer; we’re part of a continuous innovation cycle that ensures our IT infrastructure remains future-ready,” says Thorp. “It’s rare to find a vendor so responsive and committed to delivering what they promise.” Looking ahead to the future Swissport IT requirements continue to evolve with Cato remaining a key pillar. “With Cato in place, we know that our network is not the limiting factor in our growth,” Thorp explains. The ongoing partnership between Swissport and Cato ensures that as technology continues to evolve, Swissport’s IT infrastructure remains secure, scalable, and adaptable to the demands of a fast-paced aviation industry. On a personal level, Cato has given Thorp peace of mind. “I relax a bit more with the Cato platform around. It’s given us a holistic way of protecting ourselves today and a secure foundation for everything we want to do in the future. Swissport’s IT leadership now can focus on innovation rather than crisis management.”
Like any retail franchise, car dealerships that have multiple locations nationwide require comprehensive, reliable, and scalable video surveillance solutions to protect their businesses. With dealership theft increasing by 7% since 2021, protecting high-value inventory, mitigating liability risks, and ensuring compliance with video data retention standards have become critical priorities. Future surveillance solutions BCD is vital to guarding functions, protecting valuable assets, and maintaining peace of mind Additionally, managing surveillance across multiple sites demands systems that are easy to deploy, cyber-hardened, and capable of centralised oversight. As dealerships continue to expand, investing in future-ready surveillance solutions with a trusted systems builder like BCD is essential to safeguarding operations, protecting valuable assets, and maintaining peace of mind. The challenge Car dealerships face distinct challenges when it comes to security and operations, such as: Asset Protection: Showrooms and lots house high-value vehicles and parts, making them prime targets for theft and vandalism. Cybersecurity Threats: Surveillance systems needed to be cyber-hardened to prevent breaches that could compromise sensitive footage or customer information. Reliable Recording: Continuous operation is essential to ensure no gaps in security coverage, particularly during off-hours or high-traffic events. Scalable Storage Across Locations: With multiple sites generating large volumes of video footage, dealerships need a solution to store data for 30-90 days to comply with industry regulations and internal policies. Centralised Management: Managing surveillance across dozens of locations required a solution that simplified oversight while enabling scalability for future growth. The solution BCD’s All-in-One Hybrid Cloud NVR is a cutting-edge video surveillance solution designed to address these challenges. The solution offers: Integrated PoE Switch: The All-in-One NVR includes a built-in Power over Ethernet (PoE) switch, simplifying installation and reducing the need for additional network infrastructure, which saves time and costs while simplifying the overall infrastructure. Cyber-Hardened Security: BCD’s solutions are all certified as cyber-hardened solutions to maximise data protection and minimise the risk of data breaches. Always-On Recording: With features like RAID storage for redundancy and failover capabilities, along with the Harmonise Remote Monitoring and Management plugin, the All-in-One solution ensures uninterrupted recording, and with customised notifications, can mitigate hardware or network disruptions. Hybrid Cloud Architecture: The All-in-One NVR provides 80TB of local storage for immediate access to live footage while seamlessly integrating with cloud storage for long-term retention. This hybrid approach ensures franchises can store footage for 30 days or more without overwhelming local resources. Centralised, Scalable Management: BCD’s solution is simple to deploy and typically takes 30 minutes or less, allowing franchises to monitor and manage surveillance across all locations from a single interface, simplifying administration and reducing operational overhead. The results Deploying BCD’s All-in-One Hybrid Cloud solution has the potential to drive significant improvements across multiple aspects of a franchise’s video surveillance operations, including: Enhanced Security: Reliable and cyber-hardened surveillance protect valuable inventory and reduce the risk of theft or vandalism. Continuous Uptime: The system’s failover mechanisms along with Harmonise Remote Monitoring and Management Plug-in ensures 24/7 recording with no interruptions, providing full coverage for liability and security events. Regulatory Compliance: Hybrid cloud storage allows each location to easily meet the 30-90-day retention requirement without costly local storage upgrades. Operational Efficiency: Centralized management and user-friendly tools reduce the complexity of overseeing surveillance across multiple locations, cutting costs and improving oversight. Future-Ready Scalability: As franchises expand, BCD’s solutions are designed to scale effortlessly to accommodate new locations and increased storage demands, providing a future-proof investment. Conclusion BCD’s All-in-One Hybrid Cloud NVR is an ideal solution for national franchises, such as car dealerships, and offers a secure, reliable, and scalable video data infrastructure. By leveraging hybrid cloud technology and simplified management, franchises will experience peace of mind knowing their assets are protected, compliance requirements are met, and their operations will be optimised for growth.
Established in 1997, Dubai-based BMA International operates fashion retail in the Middle East and Asia across the Kingdom of Saudi Arabia (KSA), United Arab Emirates (UAE), Bahrain, Oman, Kuwait and Qatar with more than 250 stores offering two major brands — Redtag and twenty4. BMA’s steady growth is a testament to its focus on building trust with its shoppers, employees, suppliers and stakeholders to create a company that is people-centric, ambitious and results-oriented. Challenge Fraud is a common problem in the retail sector, particularly within large chains with hundreds of locations and tens of thousands of employees. BMA’s retail stores were no exception. Following an internal audit, security of point-of-sale (POS) terminals in retail outlets were identified as a serious concern, particularly the misuse of floor supervisors’ credentials to access terminals and modify or cancel transactions. The problem persisted even after BMA switched from passwords to a smart card-based authentication system The problem persisted even after BMA switched from passwords to a smart card-based authentication system. The most common issues involved supervisors leaving smart cards with cashiers to use in their absence and failing to return the cards when separation from an employer occurs — a frequent occurrence as many of BMA’s retail employees are expatriates who often return to their home countries. Fraudulent use of the smart card was also a common problem. Once a sale was completed and the customer had left the store with their purchased items, the smart card could be used to improperly access the system so the cashier could void the transaction and pocket the “refund,” resulting in both monetary and inventory losses. Biometric-based system “BMA’s internal auditors were concerned with the lack of control over the cards and the potential for fraudulent transactions due to their mishandling. They observed clear gaps in security and authentication practices that led directly to fraud and revenue leakage, resulting in the Internal Audit Committee recommending to the BMA Board of Directors that action be taken to plug the security holes by tightening the authentication process,” said Nainan M. Kurian, CEO of Technowave International LLC. The decision was made to transition authentication to a biometric-based system that would provide the required security at a competitive price that aligned with the aesthetics of the retail stores. The system also needed to be compatible with the Oracle Retail Xstore Office Cloud Service, which BMA International was adopting across its brands. Solution A fingerprint reader from HID is ideal for use by multiple people in a shared environment BMA International and its technology partner, Technowave International LLC, determined that the HID DigitalPersona® 4500 Fingerprint Reader met all their requirements — a decision supported by recommendations from other retailers that had deployed the product, and by the fact that competitive solutions were incompatible with Oracle Retail Xstore, a crucial requirement. A USB peripheral with a compact design to conserve space, this fingerprint reader from HID is ideal for use by multiple people in a shared environment. Its professional, modern design looks elegant in retail settings while offering superior authentication control via biometric functionality that uses optical scanning technology to achieve excellent image quality and reliability. HID DigitalPersona 4500 Fingerprint Reader With this easy-to-use technology, floor supervisors simply place their finger on the reader window, which rapidly captures and encrypts the fingerprint image, and then provides a red flash as a visual cue indicating that it was properly captured. That image is sent to the DigitalPersona FingerJetTM biometric engine for verification, and once the user has been authenticated, access to the POS terminal is granted. “Deploying the HID DigitalPersona 4500 Fingerprint Reader was simple and caused no disruption to retail operations. It paved the way for significant reduction in the malpractice that had been occurring with the smart card system,” said Kurian. Result Since deploying more than 1,100 HID fingerprint readers in retail outlets across KSA, UAE, Oman, Bahrain, Kuwait and Qatar, BMA has eliminated nearly all POS fraud and abuse. The system has also driven tangible improvements in the attendance and punctuality of floor supervisors, who must now be physically present in the store for authentication to take place. The HID authentication system is also capable of multiple types of authentications — providing flexibility that is appreciated by users who work at multiple locations. “Because the HID DigitalPersona 4500 Fingerprint Reader requires proof of presence for authentication, there is greater accountability among supervisors which resulted in immediate cessation of POS fraud and stopped both revenue and inventory leakage. The exceptional support provided by HID Global has also allowed BMA to take full advantage of the system’s functionality and flexibility,” said Kurian.


Round table discussion
Video storage has come a long way since rooms full of VCRs stored video from an entire system of cameras. Video storage equates to data storage, and there are multiple options ranging from hard disk storage to the cloud to storage on each individual camera using SD cards. Increasingly, cloud-based storage is an attractive option to store video footage conveniently and safely. We asked this week’s Expert Panel Roundtable: How is expansion of video storage capabilities impacting the security industry?
Headlines of violence in our schools are a reminder of the need to keep educational institutions safe. In fact, if there is a positive aspect to the constant bombardment of headlines, it is that it keeps our attention perpetually focused on how to improve school security. But what is the role of physical security systems? As the new school year begins, we asked this week’s Expert Panel Roundtable: Are schools safer because of physical security systems? Why or why not?
As physical security technologies become more complex, it is incumbent on the dealer/integrator to have the skills and expertise needed to ensure that a system operates smoothly. The value of integrators increasingly rests on the skill sets they bring to bear when installing a system. If the skills are missing, there is a problem. We asked this week’s Expert Panel Roundtable: What missing skills among security integrators can cause problems for customers?
Products


Videos
Shopping centre security: Manufacturers & Suppliers

Using artificial intelligence (AI) to automate physical security systems
Download
A modern guide to data loss prevention
Download
7 proven solutions for law enforcement key control and asset management
Download
The truth behind 9 mobile access myths
Download
Access control system planning phase 2
Download