Milestone Systems - Experts & Thought Leaders
White papers from Milestone Systems
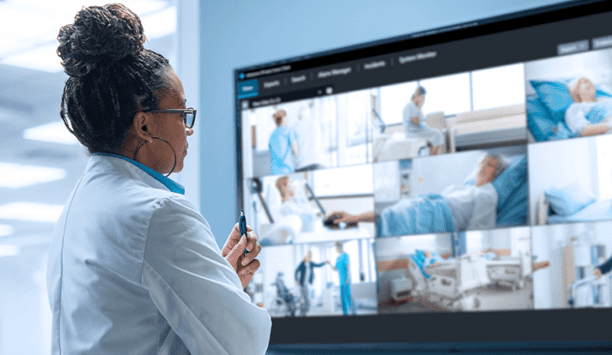
The future of healthcare security is connectivity
DownloadImproving city mobility using connected video technology
DownloadVideo technology: making cities safer & improving lives
DownloadCharting the path to safe cities
Download14 success stories about how video technology is improving city life
DownloadEssential data security strategies for healthcare
DownloadVideo technology strategies for hospitals are moving beyond security
DownloadSafeguard Students With New Techniques And Technology
DownloadLevelling up with campus safety
DownloadAssessing safety readiness for education campuses
DownloadThe future of healthcare security is connectivity
DownloadImproving city mobility using connected video technology
DownloadVideo technology: making cities safer & improving lives
DownloadCharting the path to safe cities
Download14 success stories about how video technology is improving city life
DownloadEssential data security strategies for healthcare
DownloadVideo technology strategies for hospitals are moving beyond security
DownloadSafeguard Students With New Techniques And Technology
DownloadLevelling up with campus safety
DownloadAssessing safety readiness for education campuses
DownloadLatest Milestone Systems news & announcements
With 1,300 cameras recording 24/7 and more than 1,000 investigations to process per year, Massachusetts General Hospital’s security team was not able to keep up with the vast amounts of recorded video. Now, BriefCam Syndex Pro for fast video review, search and analysis, embedded within a Milestone XProtect video management software (VMS) platform is making efficient and effective video investigation possible. Unique challenges to security Massachusetts General Hospital’s (MGH) Police, Security and Outside Services Department provides some security services to many other Partners hospitals and facilities. Following its recent digital conversion, unified on the Milestone XProtect VMS platform, MGH’s security team was able to expand camera coverage by adding new Axis network cameras directly to the existing IP network. The hospital environment presents unique challenges to security, Michelman points out “The number of investigations we were doing was taking huge amounts of time in terms of reviewing video, and that was really a waste of time,” said Bonnie Michelman, MGH Executive Director of Police, Security and Outside Services and Consultant for Partners Healthcare. The hospital environment presents unique challenges to security, Michelman points out. MGH’s 17-acre urban campus, comprising 29 contiguous and 14 separate buildings (including underground and freestanding garage facilities), is complex. The security team must also take into account not only the main location, but also dozens of satellite facilities around the Boston area. Enterprise risk management “We can’t cover all of these facilities with security staff,” said Michelman. “We need to augment heavily with very good, state-of-the-art technology that allows us to combine our intelligence, labour, policies and procedures, in order to create a better holistic approach to enterprise risk management.” Charged with creating a safe environment, MGH’s security team at the same time is challenged by the clinical team’s needs for increased efficiency through lowering length of stay and moving patients through the hospital as quickly as possible. The 24-hour Emergency Room, with its anxious, highly volatile population presents challenges of its own. In addition, patient elopement and patient wandering – unauthorised departures from the medical facility, whether intentional or unintentional – pose liability threats that can be very damaging to a hospital. Providing customer satisfaction A unified system was required to balance the video surveillance needs of a busy hospital campus A unified system was required to balance the video surveillance needs of a busy hospital campus with remote satellite locations while upholding the highest level of security possible, maintaining operational flow, and providing customer satisfaction that includes expectations of privacy. Michelman, together with MGH Senior Manager, Systems and Technology Robert Leahy, decided on the Milestone XProtect VMS platform. Camera count was increased from 400 to 1,300, and standardised with Axis network cameras connected directly to the IP network. To deal with the marked increase in video data, MGH’s team chose BriefCam Syndex Pro, a powerful set of tools intended to reduce the time and effort needed to conduct video reviews, post-event video investigation and real-time video monitoring. The BriefCam solution ties in seamlessly with the Milestone video management solution, providing efficient workflow for investigators. Presenting video metadata According to Michelman, BriefCam has already proven invaluable. A two year long ROI examination of video surveillance use at MGH has shown a progressive rise in success rates with the use of video in incident investigations. According to Michelman, BriefCam has already proven invaluable “I see BriefCam as a very important part of our toolbox of excellent practices for protecting what is a very complex environment of tangible and intangible assets,” said Michelman. BriefCam Syndex Pro’s ability to present video metadata in graphic visualisation format, such as bar graphs, pie charts and the like, has opened up new realms of possibilities to extend the role of CCTV video beyond security into organisational efficiency and more informed, data-driven decision making. Better investigative focus “In the past, there might have been things that would have been a ‘nice to do,’ but we couldn’t do it because we didn’t have resources to watch many hours of video,” said Michelman. “Now we can manage the content and we can see trends, which in turn can drive redeployment of resources, and by extension, facilitate a better investigative focus and success.” BriefCam Syndex Pro embedded within Milestone XProtect VMS platform is helping MGH in its mission to effectively and efficiently protect and safeguard the hospital community. Michelman said: “We’re happy with these products, but it’s not just about the quality of the technology, it’s about the quality of the partnership. You know, it’s easy to sell a product, but to sustain it, service it, and be there after it is in is really very critical for us.”
Being isolated on the edge of wilderness means there’s a need for a video system that’s both reliable and flexible. For that reason, the team at Jackson Hole Airport (JAC) since 2009 has relied on video management software (VMS) from Milestone Systems to enhance security, safety, and efficiency. Challenge - Help to keep scaling At the edge of the frontier, Jackson Hole Airport has experienced considerable growth over the years. Significant capital investments in expansions have made new video system integrations possible several times, and Milestone XProtect has supported the airport’s needs along the way. As of 2020, over 220 cameras were in use, and the airport shows no signs of slowing down As of 2020, over 220 cameras were in use, and the airport shows no signs of slowing down. New projects will include building a fuel farm, a car wash and expanded parking facilities. XProtect’s open platform software As the need to increase security continues, XProtect’s open platform software will continue to enable both IT team growth and the seamless integration of new cameras and data storage capabilities. Solution - Integrations are in the fly zone Milestone XProtect Professional Plus and Smart Client Network cameras from Axis Communications and Panasonic Optimised video server hardware from Razberi Integrated video analytics from Agent Vi All video is stored for up to a full year, with most of the system’s 200 cameras set for motion recording, 24/7. Result - Greater situational awareness for higher security The video system has enabled improvements throughout the entire airport. For example, Jackson Hole Airport has to contend with a great deal of plane de-icing for several months each year. This occurs at a distance from the main buildings and, thanks to the video expansion, each airline is now able to monitor the de-icing of their planes. Allowing clients to monitor progress on their own has saved airport staff time and resources. The airport uses the system to closely monitor the security checkpoint, too, capturing video documentation in case of an incident. Baggage areas are also monitored, so it’s possible to investigate lost bags and left-behind items by reviewing video. New 4K, multi-sensor cameras New 4K, multi-sensor cameras support a largely unmanned investigatory system New 4K, multi-sensor cameras support a largely unmanned investigatory system. They capture everything and provide enough data to zoom in after the fact, if needed. Additionally, the team has deployed video analytics from Agent Vi to provide a layer of automated alarms and notifications for flagging abnormal occurrences. Video analytics can detect events, such as travelers moving against the foot traffic flow and crossing into restricted areas. Milestone’s XProtect Smart Client Milestone’s XProtect Smart Client has shifted general situational awareness in the airport, as a new standard for authorising users’ remote access to the surveillance from multiple locations. It provides seamless viewing of live and recorded video, instant control of cameras and connected security devices, and a comprehensive overview of activity. The ongoing use of Milestone Systems’ video management software (VMS) makes it possible to maintain the independence and efficiency of a small team of personnel, thereby delivering maximum security at the base of the Grand Teton Mountains. Situational awareness for the JAC team and their clients Andrew Wells, the IT Manager for the Jackson Hole Airport (JAC), said “Situational awareness for our team and our clients allows us to be as secure and efficient as possible with our small team. The flexibility of the open platform VMS allows us to scale our system and add the features we need now and in the future.” Jackson Hole Airport (JAC) lies seven miles north of Jackson, Wyoming, at the base of the Teton Mountains, in USA. It is unique for being entirely within Grand Teton National Park. It is the busiest airport in the US state of Wyoming, with nearly 500,000 in-bound passengers annually. The airport covers over 500 acres and has one runway that supports 11 hard-stands, nine boarding gates and three baggage carousels.
The Commonwealth of Puerto Rico needed to implement a centralised and efficient perimeter security system for all public schools on the island. Intrusions and assaults at educational institutions have increased, and Hurricane Maria further exacerbated problems with the destruction of infrastructure. The solution: The need to repair hurricane damage also provided opportunities to invest in modern improvements. The Department of Education chose to install a video surveillance system with more than 10,000 cameras, speakers, and other security devices in 856 schools. In the same way, a centralised control centre was established using the Corporate version of Milestone Systems XProtect® video management software (VMS). Devices installed Milestone Systems: XProtect VMS Software XProtect Smart Client Milestone Interconnect Cameras from Axis Communications and Uniview DH-Vision Seneca Servers and Optex Sensors The advantages: Audiovisual material captured by the system helps agencies to evaluate and manage areas for public use Endowed with the same annual budget that allowed the monitoring of 250 institutions, the new system enabled the Puerto Rico Department of Education to cover all 856 public schools. Since the system has been operational, there has been a 97% reduction in intrusions within educational institutions. In addition to protecting the educational programme, the audiovisual material captured by the system helps other government agencies to evaluate and manage areas for public use and investigate incidents. Need for a centralised security system Ensuring a safe environment is a growing challenge for schools and colleges: theft, fights, and bullying are some of the problems that not only affect students, but also teachers, employees, and, ultimately, the government entities that subsidize the educational system. In Puerto Rico, for example, the Department of Education was concerned about the increase in unauthorised intrusions, robberies, and assaults within its schools. This index shot up after Hurricane Maria destroyed much of the island’s infrastructure in 2017. Even before this natural phenomenon, there was no centralised security system that integrated an overview of all schools. There were disparate installations of video surveillance equipment (cameras, alarms, and lighting) but only in approximately 250 of the schools. Centralised command centre González said, the proposal was born to begin the process to acquire a video surveillance system for public schools After the hurricane, top priority was given to providing perimeter security for all schools through an effective centralised command centre instead of investing in the repair and purchase of separate systems. “The hurricane damaged the island’s communication and lighting systems, a circumstance that promoted intrusions into schools and increased vandalism. We had no visibility of what was happening and we could not find a way to avoid these escalations,” said César González Cordero, Security Commissioner for the Puerto Rico Department of Education. He adds, “However, we could not afford to buy and repair equipment individually for all schools, so a centralised and coordinated effort was necessary.” Based on this context, González said, the proposal was born to begin the process to acquire a video surveillance system for public schools in Puerto Rico, focused on perimeter security. Perimeter security for all schools Genesis Security Services, Inc. of Puerto Rico was selected to develop the perimeter security project for the 856 public schools on the island. This Puerto Rican corporation was founded in 1997 in Yabucoa, Puerto Rico by brothers Roberto and Emilio Morales, who are leaders in security services at the government level. “We have been providing security to the Department of Education for more than 15 years through our onsite guard service. That is why we knew the design, location, assets, and vulnerabilities of various educational establishments. This was a great advantage when executing the project,” said Yasel Morales, Technology Director at Genesis. Video system Milestone XProtect video management software supports more than 8,500 security and surveillance devices In October 2018, the installation of cameras and other devices began in all schools. The video system mission control was built inside the Genesis Central Station, located in the Carolina municipality (in the island's northeast region). Video data from all schools are returned to Central Station, where it is managed with the Milestone Systems XProtect Corporate open platform VMS. Leveraging the power of the open platform, Milestone XProtect video management software supports more than 8,500 security and surveillance devices, and more than 450 software integrations from more than 3,500 technology partners. NVRs, DVRs and cloud solutions Alliance partners include providers of network video cameras, cloud solutions, DVRs and NVRs, servers and storage equipment, alarm and detection systems, video analytics, GPS technology, laser and radar scanners, boxes of emergency calls, and more. “At the Central Station, we have fifteen workstations, with the same number of operators per shift. There we have a videowall of ten monitors distributed between the stations. Likewise, we have two dispatch centers that serve as backup: one in the municipality of Yauco and the other in the municipality of San Juan,” Morales explained. Uniview DH-Vision 4-megapixel cameras, audio speakers As part of the project, approximately 10,000 Uniview DH-Vision 4-megapixel cameras were installed in 856 schools (an average of 12 cameras per campus). Audio speakers from Axis Communications and a range of Optex sensors also were integrated. The combination of these technologies made it possible for every school to have an anti-intrusions system with its alerts feeding back to the Central Station. XProtect Express+, Milestone Interconnect Milestone Interconnect connects remote sites for a low-cost video surveillance solution Each campus has a Seneca brand server with the XProtect Express+ software installed. This communicates with the Corporate version at the Central Station through Milestone Interconnect™, a licensing platform that opens a communication channel between different hardware that normally cannot communicate with each other. Milestone Interconnect connects remote sites for a low-cost video surveillance solution. It is the ideal surveillance for a wide variety of industries that want an inexpensive way to get centralised supervision of multiple locations spread across one region. Remote management and monitoring With Milestone Interconnect, engineers and managers can easily monitor critical and remote areas from one central location. This means faster intrusion management because operators in the central system can access the video and receive alarms from remotely connected sites. This reduces the need to have local security personnel, maintenance, operation, and other costs, including visits onsite. Virtual gates Genesis created virtual gates using cameras that, in addition to protecting school spaces, also ensure the safety of substations and solar panels, which are considered important assets for institutions. If someone crosses the virtual gate, an alert is generated locally and passed to the Central Station through Interconnect. Operators then make a visual confirmation and, if applicable, the emergency protocol is activated. “The emergency protocol is to contact the Security Commissioner and the Department of Operations. For this liaison, we internally designate an inspector. Once informed, they activate the security officers at the sites, who are trained to give quick responses and inform the police,” said Morales. Identifying suspicious activities Due to the management software, Genesis can easily find any recording of the schools Due to the management software, Genesis can easily find any recording of the schools and send it to the Security Commissioner, who can also receive the alerts directly through an application on his mobile phone. It should be noted that all personnel handling the system, both operators and technicians, have Milestone Systems certifications, which they obtained on the manufacturer’s website. Security Commissioner González explained that the directors and residents of the schools may contact the Central Station if they wish to report any suspicious activity within a school after regular hours. Genesis operations centre González also clarified that “if for any reason a school principal requires a recording, he must contact us, and we request the information from the Genesis operations centre. This protocol is designed to respect the right to be in a place without feeling guarded at all times, as stipulated in the public policy of Puerto Rico. In total, this system directly benefits almost 400,000 people.” Increased security at a lower cost According to the Security Commissioner, since the first camera was installed, they went from two or three intrusions per day to one or zero. Even in October 2018, they had no record of intrusions. Genesis Security Services, Inc. confirmed that since the system has been operational, there has been a 97% reduction in school intrusions. Reduced physical assaults Video technology has helped dispel theft of property by employees and has helped reduce rates of physical assault Video technology has helped dispel problems such as theft of property by employees and, more importantly, has helped reduce rates of physical assault and bullying among students. These results have helped build trust among Puerto Rican families when they enroll their children in schools. “The system provides agility and precision. It is more efficient and immediate than communicating with a guard who has to enter a facility to verify what is happening. It’s great working with a system that has visibility 24/7 in schools,” said González. Cost savings On the other hand, due to this project, it was possible to reduce the cost of security in schools using technology, one of the main objectives of the Department of Education at the beginning. “We spent about $25 million annually covering just 250 schools with the guard system, and we had almost 600 schools left unattended. This project gave us the possibility of covering 100% of the public schools in Puerto Rico with the same budget,” González reported. Finally, it is important to note that many of these schools are located in vulnerable places on the island, so the system is also helping the Police and the Prosecutor’s Office to resolve cases that occurred around the educational facilities, and in general to contribute with the welfare of the community. Future projects On behalf of the Department of Education, the Puerto Rican Government is seeking ways to integrate this type of video analytics system with software programmes and databases of organisations that advocate for sexual assault victims. “In the future, we want to have a system that is capable of identifying if a sex offender crosses the perimeter in school zones so that we can warn in time,” said González. On the Genesis side, Morales said that the next step with this project would be to develop video analytics for the VMS, not only to give perimeter security but also statistics such as counting people and vehicles. They also plan on integrating access control systems into all schools.
Insights & Opinions from thought leaders at Milestone Systems
ISC West 2025 in Las Vegas showcased the latest advancements in security technology, offering security professionals a glimpse into the future of the industry. This year's expo highlighted the growing influence of artificial intelligence (AI), cloud computing, and enhanced integration. The pioneering comprehensive and converged security event attracted nearly 29,000 industry professionals to the Venetian Convention Centre. Integration into unified platforms Several companies emphasised the importance of cloud-based solutions and the integration of diverse security components into unified platforms. For example, Brivo's Security Suite provides “everything in one platform” – not just access control. Customers only pay for what they use because the system is flexible and scalable from a single door to enterprise level applications. Brivo’s suite includes video, but the system can also tie in with third-party “partners.” Genetec's Security Centre allows for more frequent updates through the cloud. Milestone is undergoing a two-year transition to bring its Xprotect system into the future by incorporating Arcules and Briefcam into a video-as-a service product. Suprema introduced BioStar X, which integrates access control and video analytics into a single platform. AI and mobile credentials Axis Communications’ Cloud Connect product announced three new partnerships at ISC West 2025 Axis Communications’ Cloud Connect product announced three new partnerships at ISC West – Eagle Eye Networks, SecuriThings, and Wesco. They join the three partners announced during the first year of Axis Cloud Connect – Genetec, Kone (elevators) and Milestone. AI and mobile credentials were still hot topics at ISC West 2025, but the conversation has evolved beyond amazement at the technologies’ capabilities and now centres on more practical aspects. From the theoretical to the practical “AI and mobility are still the ‘flavors de jour,’ but messages are evolving to manifest AI for better outcomes,” says Heather Torrey, General Manager, Commercial Security, Americas, for Honeywell Building Automation. The company has reframed its security portfolio to be very building- and business-focused, continuing to grow and evolve after the recent acquisition of LenelS2. “From the theoretical to the practical, we want customers to be part of the conversation so we can deliver AI that is meaningful to them, focusing on what’s most important,” says Torrey. Under Honeywell’s new ownership structure, “each part of the business can be more focused on customers’ needs,” she says. Honeywell continues its journey around mobile access and credentialing and migrating to cloud solutions. Innovations in Access Control Gallagher’s new Quickswitch access control board simplifies the migration from legacy systems Access control remains a critical component of security systems, and ISC West 2025 showcased several innovations in this area. Acre is releasing “Gallery,” its version of the App Store for access control. DormaKaba is launching the Keyscan KC Series door controller with TCP/IP connectivity and enhanced features. Gallagher’s new Quickswitch access control board simplifies the migration from legacy systems. Johnson Controls highlighted its C-Cure command centre and C-Cure IQ web client, offering a unified approach to access control and video. Hardware integrations for security panels For service provider Alarm.com, hardware products prepare a path to greater customer experiences, says Abe Kinney, Alarm.com’s Director, Product Management, who oversees hardware integrations for security panels, sensors, video, etc., and drives new product development. “We are looking to bridge the physical world to digital world,” he says. “We want to bring an advantage to our dealers that they can bring to customers.” Because Alarm.com’s customers pay a monthly fee, the products must be durable and economical, says Kinney. “It should work with no need for truck rolls.” The importance of longevity and flexibility Products are evaluated based on features, price, and ease of installation Products are evaluated based on features, price, and ease of installation. In particular, longevity is important for the Alarm.com’s pro channel. There is also a growing emphasis on deterrence industrywide. Says Kinney: “We recognise that detection is part of it, but we need to prevent problems from happening in the first place. And the industry is re-evaluating.” When it comes to cloud intelligence, Eagle Eye Networks puts the emphasis on flexibility. They offer AI that can perform anywhere on the system infrastructure, on the camera, on their on-site bridge device, or in the cloud. They support their own AI and also any AI product from a third party. “We focus on what customers want from the data AI detects,” says Hans Kahler, Eagle Eye Networks’ Chief Operating Officer. Integration with other systems A timely alert from gun detection could save a life, but AI can also generate information that might be used and analysed later, such as point-of-sale information, dwell time, foot traffic, etc. “What people want is the ability to work with the data for business intelligence,” says Kahler. Integration with other systems provides new opportunities for customers: For example, a licence plate reader at a restaurant drive-thru could trigger customisation of the menu board digital signage based on the customer’s previous buying pattern. Relentless Innovation Assa Abloy handles more than 40 million SKUs for all its various brands, faked in 28 factories in the US Assa Abloy handles more than 40 million stock keeping units (SKUs) for all its various brands manufactured in 28 factories in the United States. Merely complying with regulations such as the “Buy American Act” is a monumental effort considering the massive product line, attendees heard at Assa Abloy’s Annual ISC West Breakfast focusing on compliance challenges in the security market. Meanwhile, back at the trade show booth, Assa Abloy focused on “relentless innovation” in every corner of its product line. Assa Abloy’s message: Innovation in security does not have to be about AI or automation. In fact, inventive approaches to products come in all shapes and sizes and at every level of the product portfolio, and innovation is happening faster than ever. For example, the Safebolt product from Securitech, a brand recently acquired by Assa Abloy, can quickly lock down existing doors with the press of a red button on a cylindrical or mortise lock. Temporary Systems to Secure Events Securing events is the focus of Allied Signal’s Unified Command Solutions, which specialises in setting up temporary security systems for conventions, trade shows, festivals, construction sites, parades, and other events. They can add technology to situations where previously mostly security officers were used, providing safety/security and enabling more efficient event operation. “We can put cameras anywhere, whether they need power or not, use cell service or WiFi, a localised network or the internet, or whatever,” says Andrew LaMadrid, VP, Sales for Allied Signal’s Unified Command Solutions. Event operation and management IDIS came to ISC West looking to leverage new products that they did not promote in the past The focus is on easy implementation, flexibility, and fast setup and removal. “We look for a solution to solve each customer’s pain points,” says LaMadrid. They specialise in setting up and deploying surveillance cameras for safety/security and for event operation and management. Mobile surveillance is a relatively new “piece of our puzzle” when it comes to protecting high-profile events. “People are excited about what we can offer that’s new,” says LaMadrid. Unified Command Solutions has been around for about 12 years and was acquired by Allied Signal last summer. IDIS came to ISC West looking to leverage new products that they did not promote in the past, and visitors were very interested in those solutions, says Scott Switzer, IDIS CEO. “The progression of our product line has been tremendous,” he says. Last year, the IDIS booth offered only basic analytics, but this year they had 30 different advanced analytics including gun and aggression detection using the advanced solution “IDIS Vaidio AI.” What Makes You Different? The most common question IDIS hears at their trade show booth is: “What makes you different?” The answer: They offer an end-to-end solution, including cameras; they manage, control, design from end-to-end; and there is no need for multiple integrations. The time needed to install an IDIS system is significantly less because of the simplicity. “We have customers we have supported and grown together for over 20 years,” says Switzer. The company previously deployed IDIS cameras under the Costar brand before the Korean IDIS brand was introduced into the U.S. (IDIS purchased Costar and changed the name to IDIS America.) “This has been a tremendous show for us; we are looking to build our momentum and let more people know about IDIS,” says Switzer. Managing real AI at the edge The depth of their metadata enables new applications, whether for security or business operations Based in Prague, Czech Republic, and with U.S. offices in Pennsylvania, FF Group provides licence plate recognition for harsh environments. Using Axis cameras, they offer “managed real AI at the edge,” selling through a nationwide distributed network, says Alex Osypov, CEO and Founder of FF Group. Markets include parking lots, cities/municipalities, police, government, water systems, etc. The depth of their metadata enables new applications, whether for security or business operations. They are looking to combine and correlate data including LIDAR, RADAR, etc. to exploit the advantages of “data fusion.” Osypov says: “The market is growing because we are involving other adjacent markets.” Unified platforms and advanced tools Several companies are focusing on enhancing security operations centres (SOCs) by providing unified platforms and advanced tools. Axon’s Fusus system “layers” onto existing infrastructure, tying together various sensors into a single interface for real-time monitoring and information sharing. Increasingly, enterprises have invested in a lot of technologies – ac, video, asset trackers – but none of it talks together. Fusus ties all the systems together so that operators no longer have to look at 10 different screens. Rather, there is a “single pane of glass” that shows everything and facilitates sharing of information with law enforcement. Motorola also showcased its Security Operations Centre, which integrates hardware, software, smart sensors, communication radios, and broadband devices to streamline incident management.
For all the emphasis on cloud systems and centralised servers at ISC West, a lot of innovation in security video systems is happening at the edge. New advancements inside video cameras are boosting capabilities at the edge, from advancements in processing power to artificial intelligence (AI) and machine learning (ML) algorithms that can now be deployed directly on the cameras or edge devices. Advancements in AI algorithms The progress of video systems becoming smarter at the edge is driven by the need for real-time insights, lower latency, bandwidth efficiency, enhanced privacy, and improved reliability. Advancements in edge computing hardware and AI algorithms are enabling a range of intelligent video applications across various industries, including physical security. Smarter functionality at the edge is a benefit of new computer systems-on-chips (SoCs) that are driving new heights of performance for today’s cameras. Axis Communications’ ARTPEC-9 Axis Communications’ new ARTPEC-9 SoC offers advanced video compression to reduce bandwidth Axis Communication’s new ARTPEC-9 system-on-chip (SoC) offers advanced video compression to reduce bandwidth and storage needs. With a low bitrate, the SoC helps deliver high-quality imaging with outstanding forensic detail. ARTPEC-9 also offers enhanced deep learning capabilities to allow users to leverage the latest video analytics and accelerate the implementation of AI technology. Axis maintains control over all aspects of the chip’s development to ensure high quality and cybersecurity. Among the benefits of ARTPEC-9 are better AI and deep learning, better image quality, better cybersecurity, and AV1 license-free video compression (see below). Hanwha Vision’s Wisenet 9 Hanwha Vision has launched Wisenet 9, its most advanced AI-powered System on Chip (SoC). Wisenet 9’s enhanced edge AI capabilities increase performance as the volume and complexity of security threats demand real-time, accurate analysis. By elevating edge-device performance, AI empowers systems to quickly analyse vast amounts of video data and discern crucial patterns and anomalies. A key differentiator driving Wisenet 9 is deployment of two Neural Processing Units (NPUs), which improve performance three-fold compared to Wisenet 7, the previous SoC generation. While one NPU handles image processing, the other focuses on object detection and advanced analytics. This dual NPU concept was introduced to ensure video quality and analytics have independent resources, thus preventing one function from impacting the performance of the other. The latest from Ambarella Ambarella is a supplier of edge AI systems-on-chips to multiple video camera manufacturers Off the ISC West trade show floor in a nearby meeting room, semiconductor company Ambarella demonstrated how it will continue to push the envelope of what is possible with generative AI at the edge. Ambarella is a supplier of edge AI systems-on-chips to multiple video camera manufacturers and recently achieved the milestone of 30 million cumulative units shipped. The demonstrations highlight Ambarella’s ability to enable scalable, high-performance reasoning and vision AI applications across its ultra-efficient, edge-inference CVflow 3.0 AI SoC portfolio. The company’s DeepSeek GenAI models run on three different price/performance levels of its SoC portfolio. In addition to advancements in GenAI processing at the edge, Ambarella integrates image processing, encoding and system-level functions into all its AI SoCs. New standard for video encoding: AV1 AV1 compression is a next-generation video coding technology that offers significant improvements in compression efficiency and video quality, especially at lower bitrates. Its royalty-free nature positions it as a crucial codec for the future of internet video. AV1 compression is a next-generation video coding technology. Axis Communication’s ARTPEC-9 chip now supports the AV1 video encoding standard. By embracing this standard, which is new to the physical security market although it was introduced in 2018, Axis sets the stage for AV1 compression to eventually become the industry standard, replacing H.264 and H.265. Network video transmission AV1 is an open-source, license-free coding format designed mainly for efficient network video transmission AV1 is an open-source, license-free coding format designed specifically for efficient network video transmission. It delivers high-quality video at low bitrates, reducing bandwidth consumption and storage costs. The codec was developed by the Alliance for Open Media (AOM), a nonprofit organisation founded in 2015 by Google, Intel, Amazon, Microsoft, Netflix, and Mozilla (among others), to provide open-standard, next-gen video coding technology. AV1 is ideal for cloud solutions—making streaming applications more robust, scalable, and capable of delivering real-time insights. Now the ARTPEC-9 chipset brings these benefits to the surveillance industry, and AV1 is currently supported by AXIS Camera Station. Providers of major video management solutions (VMS) such as Genetec and Milestone will be adding support for AV1, with further developments already underway. More intelligence at the edge Intelligence inside video cameras comes from the processing power and algorithms that enable them to perform tasks beyond simply capturing and recording images. This "intelligence" allows cameras to analyse the video stream in real-time, identify objects, detect events, and make decisions or provide alerts based on what they "see." New and improved SoCs are driving performance improvements at the edge. The increasing power of embedded processors and advancements in AI are continuously expanding the capabilities of intelligent video cameras.
As cutting-edge trends go, convergence has been around for at least two decades. The meaning has shifted over the years, and if anything, the idea of convergence has gotten even more aspirational. Unfortunately, the widespread use of the term has also paradoxically undermined its meaning and power. However, today's concept of convergence has matured to provide new levels of benefit for security professionals. We asked our Expert Panel Roundtable: How has the meaning of “convergence” evolved in the security market? How are systems today more converged than ever?
Using artificial intelligence (AI) to automate physical security systems
DownloadA modern guide to data loss prevention
Download7 proven solutions for law enforcement key control and asset management
DownloadThe truth behind 9 mobile access myths
DownloadAccess control system planning phase 2
Download