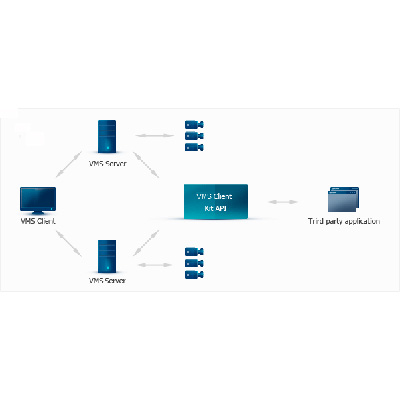
Integration software
ThingsRecon, an expert in Digital Asset Discovery and Supply Chain Attack Surface Management (EASM), announced the launch of its new supply chain product and a significantly expanded strategic partnership programme. This initiative is designed to empower Managed Security Service Providers (MSSPs), Application Cybersecurity Partners, and cybersecurity consultancies to deliver comprehensive, next-generation security solutions to global enterprise organisations and governments. Intelligence...
After several years of hosting the Partner Connections event in the USA and, most recently, Latin America, Alarm.com, the pioneering platform for the intelligently connected property, is pleased to announce its upcoming popular and highly respected European Partner Connections event, taking place on May 6–8, 2025, in the idyllic setting of Ibiza, Spain. This exclusive three-day gathering will bring together a selection of Alarm.com’s key partners from across Europe for strategic di...
Asian IR Summit officially kicks off, May 6, at the Galaxy International Convention Centre in Macau, bringing together top executives from both local and international travel and integrated resort sectors. Over the next three days, industry pioneers will engage in high-level discussions, addressing the challenges shaping the future of the industry. The Asian IR Expo exhibition, co-located with G2E Asia, opens at May 7-9, at The Venetian Macao, with complimentary shuttle service to ens...
Artificial Intelligence Technology Solutions, Inc., through its subsidiary Robotic Assistance Devices, Inc. (RAD-I), announced the expansion of RADCam™, its innovative AI-powered security device, into two additional distinct product lines to supplement the current residential solution positioning. Specifically, the Company is building RADCam software versions to specifically cater to high-frequency small-to-medium business (SMB) needs. Furthermore, RADCam will have software modi...
With its worldwide online “Eplan L!VE” event on 14 May, this time around solutions provider Eplan is guest at Eaton in Hengelo. Enquiring minds can gain first-hand experience about how Eaton's facility in the Netherlands has optimised all its processes in engineering and manufacturing for maximum efficiency. In just two-and-a-half hours, online attendees will get a compact overview how new ideas and tried-and-tested solutions for greater productivity look on the ground. News on Epla...
Camden Door Controls has introduced the industry's first 1/2" RIM Strike with 15 lbs. preload. Camden 1299 Series strikes are Grade 1 rated, with UL 1034/294 and ANSI/BHMA listings. Available in brushed stainless steel or black finish, these 1299 strikes offer 'Universal' performance with selectable 12/24V, AC/DC voltage, and fail-secure/fail-safe operation. Latch monitor included. 1299 Series Preload RIM strikes 1299 Series strikes are packaged with 1/8" and 1/4" spacer plates to accommodat...
News
Intercede, a pioneering digital identity management company, announced the launch of its latest version of MyID CMS that enables the management of Passkeys with Microsoft Entra ID. Administrators can now use the credentials management system to seamlessly manage FIDO Passkeys on devices including the Yubico YubiKey family of products, that can then be used to securely authenticate to Entra ID protected resources. Integrating Entra ID’s robust FIDO2 The solution enables corps to use seamless, secure authentication methods by combining the strengths The solution enables organisations to use seamless, secure authentication processes by combining the strengths of the Intercede, Yubico, and Microsoft technology platforms. By integrating Entra ID’s robust FIDO2 provisioning API’s with MyID CMS and YubiKeys, enterprises can now implement an end-to-end secure issuance and life cycle management solution for FIDO Passkeys, whether in Cloud or Hybrid Entra ID solutions, manage PKI and FIDO credentials on a single YubiKey, as well as support for using a Passkey as a Derived Credential. Key highlights of MyID 12.14 Entra ID Capabilities Compliance with NIST SP800-63B digital identity guidelines Simplified FIDO passkey issuance and lifecycle management Manage passkeys alongside other credential types such as certificates Applying expiry dates to passkeys – automatically revoke the credential for fixed term workers, or for temporary passkey usage Support for passkeys as a derived credential, compliant with NIST SP800-157 Compliance with NIST standards "This collaboration represents a significant step forward in enterprise credential management," said Allen Storey, Chief Product Officer at Intercede. "Our integrated solution enables customers to issue and manage passkeys at the highest level of security in compliance with NIST standards, making the use of passkeys in high-assurance environments a reality." Implementation of passkey technology with Entra ID Natee Pretikul, Principal Product Management Lead at Microsoft Security, commented: "At Microsoft, we are committed to transforming enterprise security through the implementation of passkey technology with Entra ID." "Our newly developed FIDO2 provisioning APIs, coupled with collaborations with industry partners such as Intercede and Yubico, enable us to deliver comprehensive authentication solutions that can be deployed and managed at scale.” Yubico’s trusted hardware-based authentication The combined solution addresses growing enterprise needs for robust, flexible, and user-friendly Jeff Wallace - SVP Product at Yubico, stated: “By integrating Yubico’s trusted hardware-based authentication in the YubiKey with Intercede’s MyID CMS and Microsoft Entra ID, we are empowering organisations to securely manage the lifecycle of FIDO passkeys with a streamlined, end-to-end solution, that also includes previously available authentication protocols.” Wallace added: “This collaboration ensures enterprises can uphold the highest security standards while simplifying credential management for both cloud and hybrid environments.” Identity verification strategies The combined solution addresses growing enterprise needs for robust, flexible, and user-friendly phishing-resistant authentication systems. By eliminating traditional complexity in credential management, the collaboration empowers organisations to implement more agile and secure identity verification strategies.
Richter, a consulting firm specialising in civil, structural and geotechnical engineering, has selected Red Helix, a market pioneer in cyber security and network performance, to strengthen its cyber security. The collaboration has empowered Richter to better manage IT risks, streamline compliance processes and successfully secure major infrastructure projects, including work on the UK’s high-speed rail project, HS2. Cybersecurity and risk management Operating within a globally interconnected supply chain, Richter turned to Red Helix to improve its cybersecurity and risk management in an age of greater threats, heightened regulation and increased expectations among supply chain partners and customers. Being a lean SME, Richter did not have limitless resources and was spending excessive time manually addressing security alerts. Red Helix’s cybersecurity services Richter is now able to safeguard its projects and provide the strongest possible reassurance By implementing Red Helix’s managed cyber security services - including Endpoint Detection and Response (EDR), Network Detection and Response (NDR), 24/7 Security Operations Centre (SOC) monitoring, Security Information and Event Management (SIEM), and Zero Trust Network Access (ZTNA), Richter is now able to safeguard its projects and provide the strongest possible reassurance to its broader networks of suppliers, contractors and stakeholders. Jordan Lance, Director of IT, Richter, said: “Our collaboration with Red Helix has transformed our security posture and given partners, clients and stakeholders the reassurance they need to do business with us. Their support has allowed us to win some large construction frameworks and provided us with an incredible pool of cyber security professionals we would not otherwise have had access to.” Richter’s infrastructure The partnership began with a comprehensive audit of Richter’s infrastructure, leading to tailored solutions that have dramatically improved visibility of cyber threats and reduced response times. Red Helix’s 24/7 SOC proactively monitors Richter’s environment, resolving most issues before they require intervention from the internal IT team - a shift that has saved valuable time and boosted operational efficiency. Enhanced key security metrics Richter has also benefitted from enhanced key security metrics, enabling the company to fulfil more data Richter has also benefitted from enhanced key security metrics, enabling the company to fulfil more advanced reporting and data sovereignty requirements that are essential for operating in the UK’s Critical National Infrastructure (CNI) sector now. It has streamlined compliance with critical frameworks such as ISO, Cyber Essentials, and NIST, generating automated weekly reports that help Richter maintain its certifications. Richter’s specific needs Tom Exelby, Head of Cyber Security, Red Helix said: “It's a privilege to work so closely with Richter, supporting the strengthening of their cyber security posture by providing the skills and experience of our team alongside our advanced security platform." "As always, we have built our provision around Richter’s specific needs and will continue to keep pace with the company’s evolving requirements, ensuring it remains protected by the most effective security available.”
HID, pioneer in trusted identity and access management solutions, announced the launch of HID Integration Service, a platform that integrates physical security, cybersecurity and digital identity management. This integration platform-as-a-service (IPaaS) was designed to empower application developers, solution integrators and software vendors to seamlessly and rapidly integrate essential physical security solutions, streamlining processes and enhancing system interoperability. Integrations between physical and cybersecurity systems The platform aims to ease the burden of care and upgrades associated with managing physical security By doing so, the platform aims to ease the burden of maintenance and upgrades associated with managing and implementing integrations between physical security and cybersecurity systems, thereby lowering costs, streamlining operations and significantly reducing implementation time. "Organisations have long struggled with brittle, complex integrations and the costs to maintain them," said Martin Ladstaetter, senior vice president and head of Identity and Access Management Solutions at HID. Top benefits of HID Integration Service Ladstaetter added: "HID Integration Service eliminates these pain points by providing an integration platform that connects physical and digital security products, reducing time to market for development partners who are building the next generation of security solutions with greater speed, quality, resilience and value." HID Integration Service directly addresses the top benefits security pioneers seek from unified management solutions—improved efficiencies, simplified management and enhanced visibility—helping them: Reduce operational complexities and maintenance costs. Deliver new security capabilities faster into tailored industry solutions. Simplify security touchpoints through streamlined user experiences. Key features include: A comprehensive integration layer that scales from point-to-point connections into multi-party integrations Pre-built integrations that accelerate deployment and reduce development costs Scalability and security to support rapidly evolving business needs HID's new integration platform capabilities Each brings deep expertise and robust capabilities across various security domains HID is privileged to have a few early adopters on the platform. Each brings deep expertise and robust capabilities across various technologies, verticals and security domains. "We are excited about HID's new integration platform capabilities, which we believe can only add to SwiftConnect's ability to meet our customers' expectations and broader needs in the commercial real estate and enterprise markets," according to Matt Kopel, co-founder and co-CEO of SwiftConnect. "The alignment of vision and direction between our companies will enhance and multiply the business changes our customers are pursuing," continued Kopel. RemotePhoto's AI workflow “We envision a world where ID photos magically arrive in their intended location without human intervention,” said Luke Rettstatt, chief executive officer of CloudCard. “To realise this vision, we must develop and maintain many integrations, which is daunting for a small team. HID Integration Service allows us to focus on RemotePhoto's AI workflow rather than building and maintaining certified integrations with third parties.” HID’s 2025 State of Security and Identity Report This growing demand for seamless integration and efficiency is reflected in HID’s 2025 State of Security and Identity Report. According to the report, 67% of security leaders are actively transitioning to software-driven security solutions, with nearly three-quarters of organisations considering unified data collection critical to their operations.
Kaseya, the pioneering provider of AI-powered cybersecurity and IT management software, began its Kaseya Connect 2025 conference in Las Vegas by celebrating its global customer community and unveiling a new set of technology and commercial innovations. Thousands of attendees are connecting and sharing best practices to grow faster, improve service quality, and operate more efficiently – all powered by the company’s flagship AI-powered platform, Kaseya 365. Latest Kaseya 365 platform enhancements The latest Kaseya 365 platform enhancements give IT professionals the tools and pricing With 81% of small businesses worried about IT security and efficiency, they are requiring enterprise-grade security with AI-driven automation to protect more users and devices. Backed by data from nearly 50,000 customers and millions of endpoints, the latest Kaseya 365 platform enhancements give IT professionals the tools and pricing they need to stay ahead in a rapidly evolving threat landscape. Highlights from Kaseya’s innovation announcements Kaseya 365 Ops – The newest edition to the Kaseya 365 platform applies practical AI to help customers scale efficiently, improve operations, and achieve top-tier service delivery and performance metrics. Early Kaseya 365 Ops customers save an average of 160 hours per month thanks to the platform’s AI capabilities and automation, which equates to the productivity of one additional technician. Kaseya SIEM (Security Information and Event Management) – The new Kaseya SIEM provides a streamlined, unified response system for customers with SaaS Alerts and MDR protection and without the expense of enterprise-grade alternatives. Kaseya SIEM correlates threat data from RocketCyber and SaaS Alerts, combining endpoint and cloud telemetry to deliver unified, faster, and more actionable threat detection. Free-to-Use Hardware – All models of Datto’s backup hardware will be free-to-use for all Kaseya customers, regardless of model or term. This allows Kaseya backup partners to provide a consistent level of service while eliminating upfront hardware costs. Datto ALTO 5 – The return of a 2TB ALTO model to the Datto lineup is being offered at the same monthly cost as the current 1TB model and now includes encryption to bolster security Improve businesses against cyberthreats “As we move forward, innovation is at the heart of everything we do at Kaseya. What we’re unveiling at Connect 2025 delivers on that vision,” says Jim Lippie, Chief Product Officer at Kaseya. “These innovations allow our customers to improve their businesses and fight against growing cyberthreats.”
Colt Technology Services (Colt), the digital infrastructure company, announced an expansion to its multi-award winning On Demand Network as a Service (NaaS) platform with the addition of new features designed to enhance businesses’ cloud services, boost resilience and provide greater autonomy for organisations needing flexibility, security and choice in the dynamic market environment. The three new features - available now - are On Demand Diversity, Dedicated Cloud Ports and new Multi-Vendor ‘Offnet’. Colt’s On Demand NaaS platform Colt’s On Demand NaaS platform gives businesses choice and flexibility, enabling them to consume Colt’s On Demand NaaS platform gives businesses choice and flexibility, enabling them to consume their network services on an agile, scalable, ‘per use’ basis, as they would their cloud services. Organisations can choose whether to connect via a portal or API; they can add or remove services and capacity, and benefit from real-time delivery for Colt’s on net services. They can also choose between fully flexible ‘by the hour’ billing, or longer subscription models. Colt’s continued commitment The new features are added as part of Colt’s continued commitment to expanding its On Demand NaaS platform to meet the evolving needs of its global customers. On Demand Diversity allows businesses to select different network routes for their Ethernet, Cloud and Internet services using a self-serve ordering system in the Colt NaaS platform. The ability to request access-level diversity ‘on demand’ improves network performance; bolsters resilience and disaster recovery; and supports deeper levels of compliance. Colt’s NaaS platform Cloud Ports are also open now via Colt’s NaaS platform, offering greater scalability for businesses Dedicated Cloud Ports are also available now via Colt’s NaaS platform, offering greater scalability for businesses’ cloud solutions and complementing the hosted cloud capability already live in the platform. Previously, access to cloud services from organisations including AWS, Microsoft and Google was available already in NaaS through shared ‘hosted’ cloud ports, which could be set up quickly via the portal or APIs. Dedicated Cloud Ports feature The new Dedicated Cloud Ports feature offers direct, private connections to the cloud and offering high capacity, reliability and security. Selecting Dedicated Cloud Ports through the Colt NaaS platform gives businesses an effortless service experience, cost transparency and unparalleled network reach as they can connect to the cloud from millions of locations worldwide. Colt’s own network infrastructure New Multi-Vendor Offnet feature enhances flexibility and efficiency for Colt’s customers The new Multi-Vendor Offnet feature enhances flexibility and efficiency for Colt’s customers, by enabling them to choose from hundreds of carrier partners when they connect a new ‘offnet’ location which is not directly part of Colt’s own network infrastructure. With many businesses choosing a multi-vendor strategy to best fit their global organisation, Colt’s NaaS platform offers a convenient, fast and cost-effective way to build this infrastructure. Colt cloud consumption model Peter Coppens, VP Infrastructure and Connectivity Solutions, Colt Technology Services said, “Dynamic businesses which adapt to changing macro conditions have a market advantage, so organisations are looking for new ways to build in flex. Colt has brought the “cloud consumption model” to the networking world, enabling customers to break away from the slow, static world of traditional networking." "Colt’s intuitive, self-serve NaaS platform provides this, with flexibility, choice and scale. We’ll continue to expand our fantastic NaaS platform and we’ll develop exciting new features to make life easier for our customers”. Colt digital infrastructure services Colt revolutionised the way businesses provision their digital infrastructure services. Its On Demand platform – launched more than seven years ago - was the earliest, first-to-market iteration of NaaS, providing a simplified, automated self-service platform which cut through complexity and reimagined the ordering and provisioning process. Now, organisations have access through the NaaS portal to: 32,000 Colt-connected buildings and over 275 cloud points of presence across Europe, Asia and North America 130,000 locations served by dedicated fibre (FTTX) Millions of locations delivered via carrier partners in over 180 locations with one SLA, one contract and one contact MEF Naas Excellence Awards 2024 Colt recently secured six wins for its NaaS platform at the global MEF Naas Excellence awards 2024. These are: NaaS Service Provider of the Year – Global NaaS Service Provider of the Year – Europe SD WAN Service Provider of the Year – Europe Best NaaS Vision - Service Provider Best Services Ecosystem Automation Platform Service Automation Leadership – Europe
Everon, LLC, a pioneering security integrator and premier provider of commercial security, video, fire and life safety solutions in the U.S., announced its award of a Sourcewell cooperative purchasing contract in the state and local government category. This contract allows Everon to expand its extensive portfolio of offerings and services to public agencies across the U.S. Cost-effective and efficient solutions Sourcewell serves government, education, and nonprofit corps across the U.S., including all 50 states Sourcewell serves government, education, and nonprofit organisations across the U.S., including all 50 states, Washington D.C., and U.S. territories. It operates as a national cooperative purchasing organisation, leveraging the collective buying power of over 50,000 participating public sector agencies to help them streamline procurement through pre-negotiated, competitively solicited contracts to secure cost-effective and efficient purchasing solutions. Security, video, fire and life safety “Our agreement with Sourcewell demonstrates the tangible value in working with Everon. We can help public agencies across the country optimise savings and avoid delays in the purchasing process,” said Scott Wulforst, Sr. Director, State and Local Government Programs for Everon. “We are excited to be a Sourcewell-approved vendor and look forward to working with K-12 schools, higher education institutions, and state and local municipalities as a critical resource and all-in-one provider to support their security, video, fire and life safety needs.” Local procurement requirements Everon secured the Sourcewell contract following a rigorous RFP process Everon secured the Sourcewell contract following a rigorous request for proposal (RFP) process, ensuring compliance with local procurement requirements and delivering exceptional value and service. The contract grants any public agency access to purchase from Everon through a ready-to-use, Sourcewell-vetted contract, streamlining the public purchasing process. Sourcewell-approved vendors “We’re excited to welcome Everon to our elite group of Sourcewell-approved vendors,” said John Caddy, Associate Director of Cooperative Contracts for Sourcewell. “Everon’s deep experience in the security, fire and life safety industry for the public sector as well as their ability to scale nationally made them a standout choice during our competitive solicitation process.” Range of solutions and services Under the contract, Everon can provide public agencies nationwide with streamlined, cost-effective access to a wide range of solutions and services tailored to their facilities’ needs, including: Access control systems Intrusion alarm systems Video systems, remote monitoring Fire alarm, sprinkler Gunshot detection Installation, service, and maintenance Advanced smoke, heat, and gas Mass notification and emergency Ancillary services, lights Visitor management Testing and inspections 24/7/365 UL-listed monitoring
Intercede, a pioneering digital identity management company, announced the launch of its latest version of MyID CMS that enables the management of Passkeys with Microsoft Entra ID. Administrators can now use the credentials management system to seamlessly manage FIDO Passkeys on devices including the Yubico YubiKey family of products, that can then be used to securely authenticate to Entra ID protected resources. Integrating Entra ID’s robust FIDO2 The solution enables corps to use seamless, secure authentication methods by combining the strengths The solution enables organisations to use seamless, secure authentication processes by combining the strengths of the Intercede, Yubico, and Microsoft technology platforms. By integrating Entra ID’s robust FIDO2 provisioning API’s with MyID CMS and YubiKeys, enterprises can now implement an end-to-end secure issuance and life cycle management solution for FIDO Passkeys, whether in Cloud or Hybrid Entra ID solutions, manage PKI and FIDO credentials on a single YubiKey, as well as support for using a Passkey as a Derived Credential. Key highlights of MyID 12.14 Entra ID Capabilities Compliance with NIST SP800-63B digital identity guidelines Simplified FIDO passkey issuance and lifecycle management Manage passkeys alongside other credential types such as certificates Applying expiry dates to passkeys – automatically revoke the credential for fixed term workers, or for temporary passkey usage Support for passkeys as a derived credential, compliant with NIST SP800-157 Compliance with NIST standards "This collaboration represents a significant step forward in enterprise credential management," said Allen Storey, Chief Product Officer at Intercede. "Our integrated solution enables customers to issue and manage passkeys at the highest level of security in compliance with NIST standards, making the use of passkeys in high-assurance environments a reality." Implementation of passkey technology with Entra ID Natee Pretikul, Principal Product Management Lead at Microsoft Security, commented: "At Microsoft, we are committed to transforming enterprise security through the implementation of passkey technology with Entra ID." "Our newly developed FIDO2 provisioning APIs, coupled with collaborations with industry partners such as Intercede and Yubico, enable us to deliver comprehensive authentication solutions that can be deployed and managed at scale.” Yubico’s trusted hardware-based authentication The combined solution addresses growing enterprise needs for robust, flexible, and user-friendly Jeff Wallace - SVP Product at Yubico, stated: “By integrating Yubico’s trusted hardware-based authentication in the YubiKey with Intercede’s MyID CMS and Microsoft Entra ID, we are empowering organisations to securely manage the lifecycle of FIDO passkeys with a streamlined, end-to-end solution, that also includes previously available authentication protocols.” Wallace added: “This collaboration ensures enterprises can uphold the highest security standards while simplifying credential management for both cloud and hybrid environments.” Identity verification strategies The combined solution addresses growing enterprise needs for robust, flexible, and user-friendly phishing-resistant authentication systems. By eliminating traditional complexity in credential management, the collaboration empowers organisations to implement more agile and secure identity verification strategies.
Richter, a consulting firm specialising in civil, structural and geotechnical engineering, has selected Red Helix, a market pioneer in cyber security and network performance, to strengthen its cyber security. The collaboration has empowered Richter to better manage IT risks, streamline compliance processes and successfully secure major infrastructure projects, including work on the UK’s high-speed rail project, HS2. Cybersecurity and risk management Operating within a globally interconnected supply chain, Richter turned to Red Helix to improve its cybersecurity and risk management in an age of greater threats, heightened regulation and increased expectations among supply chain partners and customers. Being a lean SME, Richter did not have limitless resources and was spending excessive time manually addressing security alerts. Red Helix’s cybersecurity services Richter is now able to safeguard its projects and provide the strongest possible reassurance By implementing Red Helix’s managed cyber security services - including Endpoint Detection and Response (EDR), Network Detection and Response (NDR), 24/7 Security Operations Centre (SOC) monitoring, Security Information and Event Management (SIEM), and Zero Trust Network Access (ZTNA), Richter is now able to safeguard its projects and provide the strongest possible reassurance to its broader networks of suppliers, contractors and stakeholders. Jordan Lance, Director of IT, Richter, said: “Our collaboration with Red Helix has transformed our security posture and given partners, clients and stakeholders the reassurance they need to do business with us. Their support has allowed us to win some large construction frameworks and provided us with an incredible pool of cyber security professionals we would not otherwise have had access to.” Richter’s infrastructure The partnership began with a comprehensive audit of Richter’s infrastructure, leading to tailored solutions that have dramatically improved visibility of cyber threats and reduced response times. Red Helix’s 24/7 SOC proactively monitors Richter’s environment, resolving most issues before they require intervention from the internal IT team - a shift that has saved valuable time and boosted operational efficiency. Enhanced key security metrics Richter has also benefitted from enhanced key security metrics, enabling the company to fulfil more data Richter has also benefitted from enhanced key security metrics, enabling the company to fulfil more advanced reporting and data sovereignty requirements that are essential for operating in the UK’s Critical National Infrastructure (CNI) sector now. It has streamlined compliance with critical frameworks such as ISO, Cyber Essentials, and NIST, generating automated weekly reports that help Richter maintain its certifications. Richter’s specific needs Tom Exelby, Head of Cyber Security, Red Helix said: “It's a privilege to work so closely with Richter, supporting the strengthening of their cyber security posture by providing the skills and experience of our team alongside our advanced security platform." "As always, we have built our provision around Richter’s specific needs and will continue to keep pace with the company’s evolving requirements, ensuring it remains protected by the most effective security available.”
HID, pioneer in trusted identity and access management solutions, announced the launch of HID Integration Service, a platform that integrates physical security, cybersecurity and digital identity management. This integration platform-as-a-service (IPaaS) was designed to empower application developers, solution integrators and software vendors to seamlessly and rapidly integrate essential physical security solutions, streamlining processes and enhancing system interoperability. Integrations between physical and cybersecurity systems The platform aims to ease the burden of care and upgrades associated with managing physical security By doing so, the platform aims to ease the burden of maintenance and upgrades associated with managing and implementing integrations between physical security and cybersecurity systems, thereby lowering costs, streamlining operations and significantly reducing implementation time. "Organisations have long struggled with brittle, complex integrations and the costs to maintain them," said Martin Ladstaetter, senior vice president and head of Identity and Access Management Solutions at HID. Top benefits of HID Integration Service Ladstaetter added: "HID Integration Service eliminates these pain points by providing an integration platform that connects physical and digital security products, reducing time to market for development partners who are building the next generation of security solutions with greater speed, quality, resilience and value." HID Integration Service directly addresses the top benefits security pioneers seek from unified management solutions—improved efficiencies, simplified management and enhanced visibility—helping them: Reduce operational complexities and maintenance costs. Deliver new security capabilities faster into tailored industry solutions. Simplify security touchpoints through streamlined user experiences. Key features include: A comprehensive integration layer that scales from point-to-point connections into multi-party integrations Pre-built integrations that accelerate deployment and reduce development costs Scalability and security to support rapidly evolving business needs HID's new integration platform capabilities Each brings deep expertise and robust capabilities across various security domains HID is privileged to have a few early adopters on the platform. Each brings deep expertise and robust capabilities across various technologies, verticals and security domains. "We are excited about HID's new integration platform capabilities, which we believe can only add to SwiftConnect's ability to meet our customers' expectations and broader needs in the commercial real estate and enterprise markets," according to Matt Kopel, co-founder and co-CEO of SwiftConnect. "The alignment of vision and direction between our companies will enhance and multiply the business changes our customers are pursuing," continued Kopel. RemotePhoto's AI workflow “We envision a world where ID photos magically arrive in their intended location without human intervention,” said Luke Rettstatt, chief executive officer of CloudCard. “To realise this vision, we must develop and maintain many integrations, which is daunting for a small team. HID Integration Service allows us to focus on RemotePhoto's AI workflow rather than building and maintaining certified integrations with third parties.” HID’s 2025 State of Security and Identity Report This growing demand for seamless integration and efficiency is reflected in HID’s 2025 State of Security and Identity Report. According to the report, 67% of security leaders are actively transitioning to software-driven security solutions, with nearly three-quarters of organisations considering unified data collection critical to their operations.
Kaseya, the pioneering provider of AI-powered cybersecurity and IT management software, began its Kaseya Connect 2025 conference in Las Vegas by celebrating its global customer community and unveiling a new set of technology and commercial innovations. Thousands of attendees are connecting and sharing best practices to grow faster, improve service quality, and operate more efficiently – all powered by the company’s flagship AI-powered platform, Kaseya 365. Latest Kaseya 365 platform enhancements The latest Kaseya 365 platform enhancements give IT professionals the tools and pricing With 81% of small businesses worried about IT security and efficiency, they are requiring enterprise-grade security with AI-driven automation to protect more users and devices. Backed by data from nearly 50,000 customers and millions of endpoints, the latest Kaseya 365 platform enhancements give IT professionals the tools and pricing they need to stay ahead in a rapidly evolving threat landscape. Highlights from Kaseya’s innovation announcements Kaseya 365 Ops – The newest edition to the Kaseya 365 platform applies practical AI to help customers scale efficiently, improve operations, and achieve top-tier service delivery and performance metrics. Early Kaseya 365 Ops customers save an average of 160 hours per month thanks to the platform’s AI capabilities and automation, which equates to the productivity of one additional technician. Kaseya SIEM (Security Information and Event Management) – The new Kaseya SIEM provides a streamlined, unified response system for customers with SaaS Alerts and MDR protection and without the expense of enterprise-grade alternatives. Kaseya SIEM correlates threat data from RocketCyber and SaaS Alerts, combining endpoint and cloud telemetry to deliver unified, faster, and more actionable threat detection. Free-to-Use Hardware – All models of Datto’s backup hardware will be free-to-use for all Kaseya customers, regardless of model or term. This allows Kaseya backup partners to provide a consistent level of service while eliminating upfront hardware costs. Datto ALTO 5 – The return of a 2TB ALTO model to the Datto lineup is being offered at the same monthly cost as the current 1TB model and now includes encryption to bolster security Improve businesses against cyberthreats “As we move forward, innovation is at the heart of everything we do at Kaseya. What we’re unveiling at Connect 2025 delivers on that vision,” says Jim Lippie, Chief Product Officer at Kaseya. “These innovations allow our customers to improve their businesses and fight against growing cyberthreats.”
Colt Technology Services (Colt), the digital infrastructure company, announced an expansion to its multi-award winning On Demand Network as a Service (NaaS) platform with the addition of new features designed to enhance businesses’ cloud services, boost resilience and provide greater autonomy for organisations needing flexibility, security and choice in the dynamic market environment. The three new features - available now - are On Demand Diversity, Dedicated Cloud Ports and new Multi-Vendor ‘Offnet’. Colt’s On Demand NaaS platform Colt’s On Demand NaaS platform gives businesses choice and flexibility, enabling them to consume Colt’s On Demand NaaS platform gives businesses choice and flexibility, enabling them to consume their network services on an agile, scalable, ‘per use’ basis, as they would their cloud services. Organisations can choose whether to connect via a portal or API; they can add or remove services and capacity, and benefit from real-time delivery for Colt’s on net services. They can also choose between fully flexible ‘by the hour’ billing, or longer subscription models. Colt’s continued commitment The new features are added as part of Colt’s continued commitment to expanding its On Demand NaaS platform to meet the evolving needs of its global customers. On Demand Diversity allows businesses to select different network routes for their Ethernet, Cloud and Internet services using a self-serve ordering system in the Colt NaaS platform. The ability to request access-level diversity ‘on demand’ improves network performance; bolsters resilience and disaster recovery; and supports deeper levels of compliance. Colt’s NaaS platform Cloud Ports are also open now via Colt’s NaaS platform, offering greater scalability for businesses Dedicated Cloud Ports are also available now via Colt’s NaaS platform, offering greater scalability for businesses’ cloud solutions and complementing the hosted cloud capability already live in the platform. Previously, access to cloud services from organisations including AWS, Microsoft and Google was available already in NaaS through shared ‘hosted’ cloud ports, which could be set up quickly via the portal or APIs. Dedicated Cloud Ports feature The new Dedicated Cloud Ports feature offers direct, private connections to the cloud and offering high capacity, reliability and security. Selecting Dedicated Cloud Ports through the Colt NaaS platform gives businesses an effortless service experience, cost transparency and unparalleled network reach as they can connect to the cloud from millions of locations worldwide. Colt’s own network infrastructure New Multi-Vendor Offnet feature enhances flexibility and efficiency for Colt’s customers The new Multi-Vendor Offnet feature enhances flexibility and efficiency for Colt’s customers, by enabling them to choose from hundreds of carrier partners when they connect a new ‘offnet’ location which is not directly part of Colt’s own network infrastructure. With many businesses choosing a multi-vendor strategy to best fit their global organisation, Colt’s NaaS platform offers a convenient, fast and cost-effective way to build this infrastructure. Colt cloud consumption model Peter Coppens, VP Infrastructure and Connectivity Solutions, Colt Technology Services said, “Dynamic businesses which adapt to changing macro conditions have a market advantage, so organisations are looking for new ways to build in flex. Colt has brought the “cloud consumption model” to the networking world, enabling customers to break away from the slow, static world of traditional networking." "Colt’s intuitive, self-serve NaaS platform provides this, with flexibility, choice and scale. We’ll continue to expand our fantastic NaaS platform and we’ll develop exciting new features to make life easier for our customers”. Colt digital infrastructure services Colt revolutionised the way businesses provision their digital infrastructure services. Its On Demand platform – launched more than seven years ago - was the earliest, first-to-market iteration of NaaS, providing a simplified, automated self-service platform which cut through complexity and reimagined the ordering and provisioning process. Now, organisations have access through the NaaS portal to: 32,000 Colt-connected buildings and over 275 cloud points of presence across Europe, Asia and North America 130,000 locations served by dedicated fibre (FTTX) Millions of locations delivered via carrier partners in over 180 locations with one SLA, one contract and one contact MEF Naas Excellence Awards 2024 Colt recently secured six wins for its NaaS platform at the global MEF Naas Excellence awards 2024. These are: NaaS Service Provider of the Year – Global NaaS Service Provider of the Year – Europe SD WAN Service Provider of the Year – Europe Best NaaS Vision - Service Provider Best Services Ecosystem Automation Platform Service Automation Leadership – Europe
Everon, LLC, a pioneering security integrator and premier provider of commercial security, video, fire and life safety solutions in the U.S., announced its award of a Sourcewell cooperative purchasing contract in the state and local government category. This contract allows Everon to expand its extensive portfolio of offerings and services to public agencies across the U.S. Cost-effective and efficient solutions Sourcewell serves government, education, and nonprofit corps across the U.S., including all 50 states Sourcewell serves government, education, and nonprofit organisations across the U.S., including all 50 states, Washington D.C., and U.S. territories. It operates as a national cooperative purchasing organisation, leveraging the collective buying power of over 50,000 participating public sector agencies to help them streamline procurement through pre-negotiated, competitively solicited contracts to secure cost-effective and efficient purchasing solutions. Security, video, fire and life safety “Our agreement with Sourcewell demonstrates the tangible value in working with Everon. We can help public agencies across the country optimise savings and avoid delays in the purchasing process,” said Scott Wulforst, Sr. Director, State and Local Government Programs for Everon. “We are excited to be a Sourcewell-approved vendor and look forward to working with K-12 schools, higher education institutions, and state and local municipalities as a critical resource and all-in-one provider to support their security, video, fire and life safety needs.” Local procurement requirements Everon secured the Sourcewell contract following a rigorous RFP process Everon secured the Sourcewell contract following a rigorous request for proposal (RFP) process, ensuring compliance with local procurement requirements and delivering exceptional value and service. The contract grants any public agency access to purchase from Everon through a ready-to-use, Sourcewell-vetted contract, streamlining the public purchasing process. Sourcewell-approved vendors “We’re excited to welcome Everon to our elite group of Sourcewell-approved vendors,” said John Caddy, Associate Director of Cooperative Contracts for Sourcewell. “Everon’s deep experience in the security, fire and life safety industry for the public sector as well as their ability to scale nationally made them a standout choice during our competitive solicitation process.” Range of solutions and services Under the contract, Everon can provide public agencies nationwide with streamlined, cost-effective access to a wide range of solutions and services tailored to their facilities’ needs, including: Access control systems Intrusion alarm systems Video systems, remote monitoring Fire alarm, sprinkler Gunshot detection Installation, service, and maintenance Advanced smoke, heat, and gas Mass notification and emergency Ancillary services, lights Visitor management Testing and inspections 24/7/365 UL-listed monitoring


Expert commentary
Technology advances in the security industry are transforming the way modern systems are designed and installed. Customers today are looking for greater scalability and flexibility, lower up-front costs, and operational efficiency. Cloud-based software as a service (SaaS) solutions, AI-enhanced tools, and IoT-enabled sensors and devices are increasingly in demand. The traditional role of the systems integrator is evolving as a result. While security integrators have always worked closely with end users, today’s pioneers go beyond installation and maintenance. They align security strategies with evolving business needs, integrating IT, cybersecurity, and data-driven insights into their offerings. A look at the past and present Integrators are often asked to help tailor solutions and provide expertise in IT and cybersecurity Traditionally, systems integrators specialised in installing and maintaining wired physical security systems like CCTV, access control, and alarms. The service model was built around large, up-front investments and project-based installations. However, today customers are seeking comprehensive solutions. They’re looking to wirelessly integrate security infrastructure with cloud-based SaaS systems and IoT devices. While modern systems are often faster to deploy, they’re most effective when supported by ongoing consulting and strategic planning. Integrators are often asked to help tailor solutions and provide expertise in IT and cybersecurity. Data requirements and modern systems Data requirements have also changed. Modern systems collect vast amounts of data. Advanced analytics, machine learning, and automation are now must-have tools for actionable insights. Security integrators can help end users set up custom dashboards, automations, and continuous system optimisation. Let’s look at some of the specific ways the role of systems integrators is evolving and how to adapt and succeed. Strengthen your IT expertise Integrators with IT expertise can ensure that hardware is optimised and maintained for peak performance The competitive landscape today includes not just security specialists but also IT-focused integrators and SaaS providers. Systems integrators with expertise in traditional physical security solutions plus IT experience offer unique value. They understand the real-world security challenges and opportunities, along with cybersecurity and network best practices. Integrators with IT expertise can also ensure that hardware is optimised and maintained for peak performance. Their experience with legacy systems allows them to offer practical recommendations on cost-effective approaches, such as upgrading or integrating older hardware with new digital solutions. Consider who’s making the purchase decisions Traditionally, security integrators primarily sold to security directors, facility managers, and operations teams. Now, multiple stakeholders may be involved in decision-making. IT teams, CIOs, and CTOs often weigh in on purchase decisions when cloud-based security and SaaS solutions are under consideration. Customers today aren’t just shopping for cameras, access control panels, alarms, and other hardware components. They’re looking for security ecosystems that can integrate with enterprise-wide IT infrastructure and business applications. When working with these different teams, consider outlining the system's return on investment (ROI). How can the solution reduce risk for various departments? Can it help improve operational efficiency or reduce the time required to onboard and train staff? Will it make regulatory compliance easier to manage? Focus on the long-term value for the entire organisation. Take a consultative approach Another way systems integrators are adding value is by offering vertical specialisation Installation fees remain important for many integrators, but there may be additional consultative opportunities to build long-term relationships with customers. Offer services such as roadmap planning, hardware and integration maintenance, training to certify end users on the manufacturer’s product, and cybersecurity services. While cloud-based solutions reduce on-premises maintenance, they don’t eliminate the need for ongoing support and training. Consider offering training opportunities. These can lead to other benefits as well. Better-educated and technically proficient customers are usually more willing to adopt new technologies. They understand the value of these investments and have more confidence that they’ll see results. Another way systems integrators are adding value is by offering vertical specialisation. Healthcare, sports venues, critical infrastructure, education, retail - each specialty has its own set of challenges, partner networks, regulatory restrictions, training needs, and business requirements. Integrators who specialise are uniquely positioned to offer key sector-specific insights that are invaluable to their clients. Embrace the cloud A key growth area for integrators is supporting customers in their shift to cloud deployments. Cloud solutions aren’t a one-size-fits-all solution. Each organisation is evaluating options and deciding whether cloud, hybrid, or fully on-prem solutions are the right fit for its unique needs. A key growth area for integrators is helping clients in their shift to cloud deployments Helping customers navigate and adopt cloud or hybrid solutions opens new opportunities to expand your business and deepen your relationship with your customers. Systems integrators who sell cloud solutions have the opportunity to add new layers to services for more value for customers. With a cloud solution that's easy and fast to deploy and managed and maintained by the provider, you can reduce overhead costs, staff training, and truck rolls via remote customer support. These benefits also allow you to spend time developing greater expertise in your customers’ processes. Using this knowledge, you can tailor your services towards potential productivity gains for your customers and turn them into additional sales. You ensure that your customers get the most out of the technology that’s available and that they have already purchased. Highlight your focus on cybersecurity Cybersecurity is no longer solely an IT department's responsibility. While dedicated IT security teams may still handle broader network defense, integrators play a crucial role in securing access control, surveillance, and IoT devices within a security framework. If unsecured, these devices can provide an entry point for cyber criminals to gain access to an organisation’s network. Cybersecurity is no longer solely an IT department's responsibility To best protect end users from cyberattacks, choose physical security systems with built-in security and privacy-by-design features. Help customers implement best practices to ensure their entire ecosystem is designed, built, and managed with end-to-end security in mind. Once implemented, work with your manufacturers, consultants, and end users to ensure that vulnerabilities are identified and mitigated. Every person on the network plays a role in keeping cyber threats at bay. Lean into the power of partnerships In today’s complex and dynamic security landscape, choosing the right technology partners is crucial. Ask potential partners to share their technology roadmap, and how you can offer feedback or participate in discussions about industry trends. Ideally, your partners will have a program in place to get input from integrators and end users, so they can develop products that are designed to address their most pressing issues and concerns. Your manufacturer partners should be working to help identify the evolving needs of customers and communicate these insights to systems integrators. Seek partners who actively support integrators to understand how security is evolving In addition to a good experience for the end user, strong manufacturer partners also offer solutions to streamline and automate workflows for integrators. It should be easy to order and check your shipping statuses online, for example. These are simple things that save you time and demonstrate your partner’s care for your business. Seek partners who actively support integrators to understand how security is evolving. While training is often offered on-site, some companies are now also offering blended learning models so integrators and their technicians can reduce classroom time and stay out in the field. Evolution is an opportunity Security integrators with traditional physical security expertise remain indispensable because they understand real-world risks and regulatory requirements. They can provide hands-on system deployment and optimisation. Now, there are new opportunities to build long term customer relationships. As the physical security industry undergoes this profound shift, adaptation is key. By embracing cloud and hybrid solutions, integrators can unlock new revenue streams, enhance customer relationships, and stay ahead of technological advancements. With the right partnerships and a forward-thinking mindset, systems integrators can navigate this transformation and take advantage of new opportunities being presented by evolving technology. Leverage your deep industry experience while upskilling in cloud, cybersecurity, and IT. The strongest approach is for end users, systems integrators, IT specialists, and manufacturers to work together to navigate industry changes.
In today’s world, almost any electronic security system holds the potential to become a gateway for cybercriminals. With physical security and cybersecurity increasingly entwined, security professionals aren’t doing their job unless they take all possible precautions to lock down unauthorised access to camera systems, access control platforms, intercoms, and other network-based security devices and solutions. Let’s explore the many steps companies should take throughout their security technologies’ lifecycle – from choosing a vendor all the way through device decommissioning – to avoid making the common mistakes that leave systems, and the networks they reside on, vulnerable to attack and sabotage. Prepurchase phase: Laying the groundwork for cybersecurity 1. Conduct a Vendor Risk Assessment IT departments often rely on the same Vendor Risk Assessment criteria they use for evaluating IT equipment manufacturers when considering the suitability of physical security vendors. While commonalities exist between how to assess these disparate solutions, there are also differences that require distinct scrutiny. For example, device endpoints within physical security systems run on custom Linux Kernels and therefore do not utilise standard Linux distributions like Red Hat, Ubuntu, or Debian. IT divisions often rely on the same Vendor Risk Assessment criteria they use for evaluating IT kit A comprehensive evaluation should examine how each security solutions manufacturer handles its software development life cycles. Ideally, vendors should adhere to a recognised framework when developing both their platform management and device-specific software. In 2021, Executive Order 14028 made it a bit easier for companies to evaluate vendors by providing guidelines for evaluating software security, the practices of the software developer, and methods to demonstrate conformance with secure practices, specifically referencing the NIST SP 800-218 Secure Software Development Framework. In short, a good vendor should have documentation that explains everything it’s doing to address cybersecurity from development, through releases and ongoing maintenance. 2. Obtain Software Update Schedules The frequency with which manufacturers update their software varies. Each company is different. If you’re their customer, it shouldn't matter whether the vendor schedules updates every six months, three months, or more often than that. What does matter is that you know what to expect and have a plan for how to deal with that reality. For example, if updates only occur every six months, under what conditions are patches released to address vulnerabilities that emerge between updates? Customers must understand how often they'll be updating the software on their devices and ensure they have the resources to make it happen. Make sure stakeholders agree, upfront, who will be performing the software updates. Will it be the integrator who installed the system, the physical security system staff, the IT team, or the end user? Keeping an entire system current is a huge challenge, but a non-negotiable responsibility. Manufacturers who don't issue frequent releases and patches put the onus on customers to handle mitigation efforts on their own. In these instances, IT departments must be prepared to employ network segmentation, firewalls, security whitelists/blacklists, and other methods to protect their systems until a patch is released. If a company's security team has typically updated firmware only when something breaks, these additional responsibilities most likely require greater collaboration with IT departments and a shift in how security systems are managed. 3. Know the Warranty Terms and Duration of Software Support Organisations should understand the warranty policies for the devices they purchase Organisations should understand the warranty policies for the devices they purchase. Even more important is knowing when a device's software support will expire. Software support should extend well beyond hardware coverage. For example, if a camera has a five-year hardware warranty, customers should reasonably expect an additional five years of software support. When that period ends, companies must plan on replacing the device – even if it still works well. Without software updates, the device lacks vulnerability support and becomes too risky to remain on the network. Manufacturers should be transparent about their warranty and software support policies, helping organisations plan for device replacements that align with cybersecurity needs. 4. Request a Software Bill of Materials (SBOM) During the pre-discovery process, customers should request a Software Bill of Materials (SBOM) that provides a detailed inventory of the software running on each device, including open-source components. By revealing what software is "under the hood," the SBOM allows IT departments to be vigilant in protecting the company's systems from exposed vulnerabilities. For example, a customer should understand how Transport Layer Security (TLS) is being handled to secure a security solution's web server if it’s an open-source component like OpenSSL. 5. Assess Vulnerability Disclosure Practices CNA manufacturers represent the gold standard in cybersecurity practices Understanding how a manufacturer handles vulnerabilities is essential. Ideally, they should be a Certified Naming Authority (CAN) and report common vulnerabilities and exposures (CVEs) to national vulnerability databases such as NIST and MITRE. Doing so automatically includes any disclosed vulnerabilities associated with their devices in vulnerability scanners' databases. CNA manufacturers represent the gold standard in cybersecurity practices, but most security manufacturers do not reach this level. At a minimum, the vendors you choose to work with should have an email notification system in place to alert customers to new vulnerabilities. Remember – email notifications are only as reliable as the employees managing them, so investigate whether the manufacturer has a strong track record of keeping up with such communications. Ask to speak with customer references who have been using the solution for an extended period to ensure the vendor is diligent in its communications. Configuration phase: Ensuring a secure setup 1. Use Hardening Guides Once a device is purchased, configuring it securely is the next critical step. Manufacturers should publish hardening guides that detail the security controls available for their products and recommended practices for implementation. Between the features offered by the vendor and your company's own cybersecurity policies, make sure all possible encryption options are activated. Using HTTPS is vital for ensuring secure communication with devices. Many physical security devices default to HTTP to accommodate customer-specific network topologies and certificate management. Failing to implement HTTPS can leave sensitive metadata unencrypted and vulnerable to interception. 2. Consider Advanced Encryption Protocols Protocols are necessary to protect video data in transit from cameras to the VMS Some solutions offer built-in encryption protocols, like MACsec, which makes it impossible for data to be compromised as it is transmitted over the network. HTTPS is still necessary to secure the connection to the devices’ webservice, but while customers set up and configure their devices, MACsec will keep network data safe. Additionally, if you want to encrypt video streams, consider protocols such as Secure Real-Time Transport Protocol (SRTP), which secures the transmission of audio and video data over the Internet, or tunnelling methods like Secure Socket Tunnelling Protocol (SSTP), which encapsulate data packets for safe transmission between two points, even if the network is insecure. Such protocols are necessary to protect video data in transit from cameras to the Video Management System (VMS). Encryption should also extend to the VMS hard drive where video is stored. There are different methodologies to do that, but ultimately the goal is to encrypt data in transit and in storage. 3. Implement Remote Syslog In the case of a breach, each device maintains a set of logs that are useful for forensic investigations. However, if a device gets hacked, its log may not be accessible. Best practices dictate that companies should set up a remote Syslog server that maintains a copy of all device logs within a central repository. In addition to providing redundant data for investigations, a Syslog offers IT systems an efficient way to look for anomalies. Cybersecurity teams will receive immediate notification for events like unsuccessful login attempts so they can quickly figure out what's happening. Who is trying to log in? Why on that particular device? 4. Practice Healthy Password Hygiene Ideally, organisations should move towards using Active Directory or Single Sign-On (SSO) solutions One of the most basic and yet overlooked aspects of cybersecurity is the failure to manage user accounts meticulously. Many organisations use the same username and password for all security devices because it's simply too cumbersome to manage a network of devices in which each requires a separate, unique login. It's assumed that the system's primary administrators are the only ones who know the universal password. However, the system becomes vulnerable if anyone within this select group leaves the company and the password isn't changed or deleted right away. Ideally, organisations should move towards using Active Directory or Single Sign-On (SSO) solutions. This approach ensures that employees throughout a company are each assigned a unique login credential that they use for any systems they use throughout the organisation. When they leave, their passwords and access are universally terminated along with their accounts. If SSO is not an option, regular password changes and prompt account deactivation are critical. Decommissioning phase: Securely retiring devices At some point, physical security devices will reach the end of their useful life. When that time comes, companies must take care in how they dispose of their devices. A good vendor will provide guidance on how to clear memory chipsets and restore factory defaults. Improper decommissioning can lead to severe risks. For example, if an improperly decommissioned device is sold on the secondary market or retrieved from a dumpster, an attacker could gain access to sensitive network configurations and use this information for malicious purposes. Conclusion Deploying physical security solutions involves more than just securing buildings and assets; it also requires robust measures to protect against cybersecurity threats. From assessing vendors and understanding update policies to configuring devices securely and managing decommissioning processes, each step presents potential pitfalls that, if overlooked, could expose organisations to significant risks. By incorporating the techniques discussed into their deployment protocols, organisations can ensure their physical security solutions provide comprehensive physical and digital protection.
Digital access control has well-known benefits over traditional security, of course, but also costs attached to each stage of its lifetime. However, these costs are not fixed. Many factors – including building size, shape, type, location, national regulations and more – impact affordability and efficiency calculations. Crucially, the type of access solution a business selects – wired or wireless – impacts total operating costs, including during installation, running and any potential expansion or reconfiguration stages. Wireless installation Wiring premises can be expensive. So, the potential cost savings from choosing wireless digital access begin at the very start. Installation stage is the largest contributor to potential cost savings when businesses go wireless. In calculations for one report, access experts at ASSA ABLOY examined projected costs for a fictional 100-door installation. Labour savings for those who chose wireless over wired locks were 82.5%. Why? Firstly, because wireless installation is much faster. It is also less intrusive. Most wireless locking devices require little or no drilling of the door, whereas wired security needs cabling through and partly around a door – which means not just door damage, but the contracting of specialist electrical installers who may require multiple site visits. These costs add up. Digital access technology Torus aims for the highest level of LEED certification for all its new properties In Poland, for example, developer Torus aims for the highest level of LEED certification for all their new properties around Gdansk. Where possible, they choose products with Environmental Product Declarations (EPDs) and Green Circle documentation, favouring access solutions which reduce their carbon footprint. Wireless digital access technology is a natural choice. “The lack of wiring significantly reduces materials use, reduces costs, and ensures quick installation,” confirms Torus’ Roman Sokolowski. There’s no cabling, which cuts power consumption. There’s less damage to the building fabric and fitters make fewer journeys to and from the site. Adaptable locking solution By choosing a wireless solution, organisations also upgrade building security with little disruption. A wireless system makes it easier to improve security at an existing building via a retrofit process which does not inconvenience staff or disturb work routines. This was one goal at Plexal, a £15 million flexible work environment for London enterprise and academia. Plexal chose battery powered wireless locks integrated with DoorFlow, NetNodes’ online platform for managing and auditing building access. “Plexal required an adaptable locking solution for a range of different doors and, with no wiring required, it was quick and easy to install ASSA ABLOY Aperio® devices with minimal disruption,” confirms Stewart Johnson, Director at NetNodes. Cost savings with improved energy efficiency Choosing wireless over wired locking can play a vital role in reducing ongoing energy use Choosing wireless over wired locking can play an important role in reducing ongoing energy use – and, therefore, expenditure. Wholesale electricity prices in Europe are approximately double what they were in 2019, according to the IEA’s “Electricity 2024” report. For a variable cost such as energy, where businesses have little control over unit prices, it is critical to control usage, especially if high and/or changeable energy prices become what analysts at ING called “the new normal for business”. Thus, the fact that battery-powered locks consume much less energy than traditional wired solutions is increasingly relevant and important. Additional saving on energy costs Traditional wired door access devices often work via magnets connected permanently to mains electricity. These doors draw power around the clock to remain locked. Wireless locks work differently. They only “wake up” when presented with a credential, to make the access decision. This translates to an additional saving on energy costs during operation: more than 70%, or thousands of euros over a typical access system’s lifetime. Wireless digital access Wireless locks only need a change of their standard battery, which may be rechargeable Related energy and materials costs during in-use stage are also lower. Wireless locks only need a change of their standard battery – which may be rechargeable – typically once every two years. No specialist maintenance is required, saving on specialists and their travel to and from the site(s). By choosing wireless digital access, businesses help protect themselves against these ongoing costs, notably energy price increases and volatility. Cost-efficient flexible working, for staff and facilities managers Perhaps harder to quantify, but equally easy to imagine, the financial benefits of choosing a wireless digital solution are felt in the increased convenience and efficiency of daily operations. In the co-working sector, for example, flexible access to offices is a priority. As “fixed” office space rented by corporations continues to fall, co-working spaces are expected to keep growing, with one estimate suggesting almost 18% CAGR to 2030. To stand out from the competition, the founders of ULab in Alicante sought the latest innovations in access and design to create their 21st-century business centre. Part of the suite of digital access solutions from ASSA ABLOY, a SMARTair® system gave ULab real-time access management via battery-powered locks and Openowä, the Mobile Key solution for SMARTair, without any need to wire doors and other openings. SMARTair TS1000 Web interface With SMARTair and Openow, workspace residents can carry virtual keys on their smartphone With SMARTair and Openow, workspace residents can carry virtual keys on their smartphone; ULab’s security team update their rights over the air. An office manager can perform any operation remotely from the SMARTair TS1000 Web interface. In case of an emergency, they could lock-down the site or open doors remotely, for example. It’s convenient, efficient and boosts ULab’s security, benefiting users and managers. And because of SMARTair’s flexibility, they can comfortably welcome many more than their usual 100 daily users. “In addition to regular daily traffic, weekly traffic can almost multiply by 10 if an event is held,” says Enrique Burgos Pérez, Director at ULab. “We needed an access control system as flexible and convenient as SMARTair.” ASSA ABLOY benchmarking report Choosing wireless locks also adds flexibility – and can reduce costs – when an organisation reconfigures or expands their commercial space. High-quality wireless devices like SMARTair can typically be reinstalled at another opening without impacting reliability. They move to wherever is convenient. If a business is rethinking workspace to encourage flexible or hybrid work patterns, for example, cost efficiencies could be significant. Typical savings on office relocation or expansion are estimated at around 30% with wireless over wired locking, according to the same ASSA ABLOY benchmarking report. Cost efficiency and more control with ASSA ABLOY digital access To refit and improve their student accommodation, managers at the University of St Andrews sought energy- and cost-efficient access control. They chose Aperio, another innovative digital access solution from ASSA ABLOY. Approximately 1,600 doors so far are equipped with battery-powered Aperio escutcheons – without cabling. Aperio devices integrate fully with both the university’s existing central security system and their student ID card. University security managers continue to enjoy the efficiency benefits of monitoring and controlling access from a single point and in real-time, including for doors across multiple buildings. Aperio, another innovative digital access solution from ASSA ABLOY. Benefits of cost-efficiency In comparison to a wired solution, Aperio offers significant cost-efficiency benefits. Devices are wireless, so can be installed with little energy use and no need for wiring to the mains. They consume near-zero energy when idle and run on standard batteries, consuming little power during operation. Through the entire product life-cycle, Aperio combines reliability with cost effectiveness. “Aperio gives us central management and control,” says Pauline Brown, Associate Chief Information Officer at the University of St Andrews, “and contributes to our award-winning track record in energy efficiency.”
Security beat
For all the emphasis on cloud systems and centralised servers at ISC West, a lot of innovation in security video systems is happening at the edge. New advancements inside video cameras are boosting capabilities at the edge, from advancements in processing power to artificial intelligence (AI) and machine learning (ML) algorithms that can now be deployed directly on the cameras or edge devices. Advancements in AI algorithms The progress of video systems becoming smarter at the edge is driven by the need for real-time insights, lower latency, bandwidth efficiency, enhanced privacy, and improved reliability. Advancements in edge computing hardware and AI algorithms are enabling a range of intelligent video applications across various industries, including physical security. Smarter functionality at the edge is a benefit of new computer systems-on-chips (SoCs) that are driving new heights of performance for today’s cameras. Axis Communications’ ARTPEC-9 Axis Communications’ new ARTPEC-9 SoC offers advanced video compression to reduce bandwidth Axis Communication’s new ARTPEC-9 system-on-chip (SoC) offers advanced video compression to reduce bandwidth and storage needs. With a low bitrate, the SoC helps deliver high-quality imaging with outstanding forensic detail. ARTPEC-9 also offers enhanced deep learning capabilities to allow users to leverage the latest video analytics and accelerate the implementation of AI technology. Axis maintains control over all aspects of the chip’s development to ensure high quality and cybersecurity. Among the benefits of ARTPEC-9 are better AI and deep learning, better image quality, better cybersecurity, and AV1 license-free video compression (see below). Hanwha Vision’s Wisenet 9 Hanwha Vision has launched Wisenet 9, its most advanced AI-powered System on Chip (SoC). Wisenet 9’s enhanced edge AI capabilities increase performance as the volume and complexity of security threats demand real-time, accurate analysis. By elevating edge-device performance, AI empowers systems to quickly analyse vast amounts of video data and discern crucial patterns and anomalies. A key differentiator driving Wisenet 9 is deployment of two Neural Processing Units (NPUs), which improve performance three-fold compared to Wisenet 7, the previous SoC generation. While one NPU handles image processing, the other focuses on object detection and advanced analytics. This dual NPU concept was introduced to ensure video quality and analytics have independent resources, thus preventing one function from impacting the performance of the other. The latest from Ambarella Ambarella is a supplier of edge AI systems-on-chips to multiple video camera manufacturers Off the ISC West trade show floor in a nearby meeting room, semiconductor company Ambarella demonstrated how it will continue to push the envelope of what is possible with generative AI at the edge. Ambarella is a supplier of edge AI systems-on-chips to multiple video camera manufacturers and recently achieved the milestone of 30 million cumulative units shipped. The demonstrations highlight Ambarella’s ability to enable scalable, high-performance reasoning and vision AI applications across its ultra-efficient, edge-inference CVflow 3.0 AI SoC portfolio. The company’s DeepSeek GenAI models run on three different price/performance levels of its SoC portfolio. In addition to advancements in GenAI processing at the edge, Ambarella integrates image processing, encoding and system-level functions into all its AI SoCs. New standard for video encoding: AV1 AV1 compression is a next-generation video coding technology that offers significant improvements in compression efficiency and video quality, especially at lower bitrates. Its royalty-free nature positions it as a crucial codec for the future of internet video. AV1 compression is a next-generation video coding technology. Axis Communication’s ARTPEC-9 chip now supports the AV1 video encoding standard. By embracing this standard, which is new to the physical security market although it was introduced in 2018, Axis sets the stage for AV1 compression to eventually become the industry standard, replacing H.264 and H.265. Network video transmission AV1 is an open-source, license-free coding format designed mainly for efficient network video transmission AV1 is an open-source, license-free coding format designed specifically for efficient network video transmission. It delivers high-quality video at low bitrates, reducing bandwidth consumption and storage costs. The codec was developed by the Alliance for Open Media (AOM), a nonprofit organisation founded in 2015 by Google, Intel, Amazon, Microsoft, Netflix, and Mozilla (among others), to provide open-standard, next-gen video coding technology. AV1 is ideal for cloud solutions—making streaming applications more robust, scalable, and capable of delivering real-time insights. Now the ARTPEC-9 chipset brings these benefits to the surveillance industry, and AV1 is currently supported by AXIS Camera Station. Providers of major video management solutions (VMS) such as Genetec and Milestone will be adding support for AV1, with further developments already underway. More intelligence at the edge Intelligence inside video cameras comes from the processing power and algorithms that enable them to perform tasks beyond simply capturing and recording images. This "intelligence" allows cameras to analyse the video stream in real-time, identify objects, detect events, and make decisions or provide alerts based on what they "see." New and improved SoCs are driving performance improvements at the edge. The increasing power of embedded processors and advancements in AI are continuously expanding the capabilities of intelligent video cameras.
AI has the potential to enhance the usability of traditionally complex access control and physical security systems. The application of AI (artificial intelligence) within access control is still relatively new, but rapid advancements in generative AI are already transforming how security systems operate. acre security is driving the deployment of generative AI in access control through its acquisition of REKS earlier this year. REKS is a purpose-built generative AI solution designed specifically for acre’s access control platform. Unlike generic AI tools, REKS understands both system and security-specific terminology, allowing users to ask natural-language questions like, “Show me all access denied events at a specific location,” and receive instant results. AI workflows and AI agents “We're starting to see how AI workflows and AI agents, that leverage language models, can potentially be used in conjunction with access control to create new, automated processes around false alarm reduction, system configuration, report generation, data analysis, threat detection, and in-system customer support,” says Adam Groom, Director of Business Development, AI Development Team, acre security. “We expect AI-driven capabilities to evolve rapidly, but the full range of benefits will depend on continued development and real-world application,” he adds. Integrate AI-driven capabilities acre’s ability to integrate AI-driven capabilities across the company’s product portfolio positions The best way to think of REKS is as an acre access control expert you can talk to, says Groom. “As AI adoption grows in security, REKS will expand its capabilities, making access control more usable and more efficient.” Groom says acre’s ability to integrate AI-driven capabilities across the company’s product portfolio positions the company as a pioneer in next-generation physical security. “These features will add long-term value by enhancing usability and operational insights across various segments,” says Groom. “Work is already under way to incorporate REKS into acre access control, and we’ll evaluate other integration opportunities in the future.” REKS' AI capabilities According to acre, REKS simplifies daily operations, automating routine tasks, and delivering real-time, actionable intelligence. With REKS' AI capabilities, users can interact with the system to retrieve more detailed insights and actionable information from their acre access control system. “This eliminates the need for complex reports, navigating drop-down menus, or manually reviewing logs,” says Groom. “It significantly enhances efficiency and usability for security professionals.” Enhancing productivity and customer satisfaction Key concern is ensuring that system configuration, enactment, and servicing remain within their scope For integrators, the key concern is ensuring that system configuration, implementation, and servicing remain within their scope of expertise. With REKS, that doesn’t change — but the process becomes significantly faster and more efficient. Instead of manually configuring every panel, input, and output — a traditionally time-consuming task — REKS enables integrators to use natural language commands to streamline setup and adjustments, says Groom. This eliminates tedious steps and dramatically improves operational efficiency, allowing integrators to deploy and fine-tune systems with greater speed and accuracy, ultimately enhancing both productivity and customer satisfaction, he adds. Cloud-enabled ecosystems “We are committed to helping organisations modernise their security infrastructure by transitioning from legacy systems to cloud-enabled ecosystems at their own pace — ensuring minimal disruption while maximising value,” says Groom. “By integrating AI-driven capabilities, we enhance usability and deliver deeper operational insights across all segments.” “Security’s future isn’t about forcing change — it’s about empowering choice,” adds Groom. “Whether staying on-prem, migrating to the cloud, or adopting a hybrid model, we plan to provide a seamless, zero-disruption transition, prioritising interoperability, automation, and security at every stage.” Generic AI tools AI must be purpose-built for security applications because security demands precision, reliability, and context-aware decision-making, which only focused AI offerings like REKS bring to the table, says Groom. In contrast, generic AI tools, like ChatGPT, are designed to perform a wide variety of tasks, like how humans can learn and do many different things. Instead, purpose-built AI is built to do just one specific function. “REKS adds specially designed artificial intelligence to our access control solutions to enhance both intelligence gathering and the user experience,” says Groom. New applications in access control The integration of generative AI into acre's access control platforms and their broader portfolio A new AI development team will lead AI initiatives at acre, driving the integration of generative AI into acre's access control platforms and their broader portfolio. This team will seek to push boundaries in applying AI to new applications in access control, intrusion detection, and beyond, empowering security professionals to interact with their systems in a smarter, more intuitive way. But don’t worry, AI will not take the human element out of security entirely. AI human capabilities “The reality is that AI will improve upon human capabilities because it is a versatile tool that supports and strengthens security operations, not a replacement for human decision-making,” comments Groom. “It helps operators process large amounts of data quickly and detect patterns that might be missed otherwise.” Rather than removing the human element, AI allows security teams to work more efficiently by automating repetitive tasks and providing actionable data, enabling professionals to focus on critical responsibilities. {##Poll1743085396 - What is the biggest challenge you face with your current access control system?##}
Casinos face multiple security issues caused by potential bad actors, everything from cheating to vandalism, from theft to vagrancy. A new intelligent technology can monitor for specific keywords and behaviours. The technology scans the entire casino premises constantly for potential threats and notifies key personnel when they happen. Casinos are among the environments deploying the OpticSense system by Huvr Inc., which uses special fibre optic technology called an interferometer to secure large areas. Imagine a very sensitive loop made of fibre-optic cables placed around the perimeter of a facility. System’s artificial intelligence Basically, it converts the entire facility into a highly sensitive microphone, detecting any slight disturbances, such as an unusual movement or sound. When the system senses something out of the ordinary, it immediately triggers cameras to look at the disturbance and record a short video. The system’s artificial intelligence (AI) then analyses both the sound and video to determine what's happening. It compiles a detailed report and immediately sends the information to security teams. OpticSense OpticSense can hear, see, and analyse potential threats automatically before they get out of control. “This makes it possible for fewer people to do more,” says Herman C. DeBoard III, CEO and Founder of Huvr Inc, adding “When you don’t need as many personnel to monitor video feeds and analyse data, you can drastically reduce your labour costs. Best of all, when you optimise your resource allocation, your security teams can respond more effectively to each threat.” The system’s AI analyses sound and video to define what's happening. Combining fibre optics and AI Huvr was originally designed as a platform to provide immersive virtual travel experiences Huvr was originally designed as a platform to provide immersive virtual travel experiences. However, with the acquisition of OpticSense and Grip Places, the company pivoted to integrate advanced fibre-optic technology and AI-driven analytics into a comprehensive security system. The system’s artificial intelligence and fibre-optic interferometer technology work together to detect and analyse real-time threats. When the Fibre Optic Ring Interferometer (FoRi) detects even minute audio abnormalities, it triggers AI analysis. In split seconds, the AI directs cameras to record 60 seconds of video, compiles a detailed report, and then texts the real-time intelligence to security teams and authorities. Intelligent security solutions The growing need for intelligent security solutions can help to drive Huvr's entry into the security marketplace. Advanced technology enables the company to meet the increasing concerns surrounding public safety and the growing need for real-time threat analysis. The AI system classifies each detected anomaly according to its severity and stores data from various incidents to improve its risk assessment abilities over time. This continuous learning enables the AI to become more adept at accurately identifying and responding to threats specific to the casino environment. AI system classifies each detected anomaly according to its severity. Simple and discreet installation The system involves installing fibre optic cables around the casino’s perimeter The system involves installing fibre optic cables around the casino’s perimeter. It’s a simple job that typically requires less than a day. “These cables allow the casino to establish a smart perimeter detection system without significant infrastructure alterations,” says DeBoard Casinos typically employ upwards of 6,000 cameras, but human security teams cannot feasibly monitor all the incoming data at once. Huvr's OpticSense product becomes like the brain of the casino, constantly monitoring disturbances and responding in real time. Huvr’s fibre optic cables Huvr’s advanced detection algorithms work in tandem with a casino’s existing camera infrastructure, simply adding a layer of security that converts traditional security measures into an intelligent system that continuously monitors and analyses video footage. With Huvr’s fibre optic cables easily hidden or buried and the server roughly the size of a shoe box, the system is designed to be extremely discreet. It can be operated by a single person using a small handheld device. The security system is simple to scale and manage without disrupting casino operations. Security system is simple to work without disrupting casino operations. Autonomy boosts productivity Huvr automates surveillance and anomaly detection to decrease the load on security teams Autonomy is an important aspect of this new technology. Traditional security systems have required constant human monitoring, but Huvr automates surveillance and anomaly detection to decrease the load on security teams. “Without any human direction, Huvr detects minute disturbances, triggering the AI system to direct cameras and analyse video footage instantaneously,” says DeBoard. He adds, “The intelligent system rapidly monitors every anomaly and accurately decides which present potential threats. When it detects an issue, it compiles a detailed report that includes the number of individuals involved, their appearances, direction of movement, and licence plates. It takes only seconds to text this report to security teams and authorities.” Applications beyond casinos Beyond casinos, Huvr already provides proactive security in a wide variety of settings. In banks, the system monitors parking lots and ATM machines for suspicious activity. In large stadiums, it proactively detects target words such as “help” or “gun.” In schools, Huvr’s fibre optic ring interferometer secures campuses against unauthorised intrusions. In hospitals, it alerts medical staff when patients need immediate care. In airport terminals, it monitors for suspicious behaviour. In restaurants or construction sites, the system learns to monitor for safety violations and health hazards. Smart perimeters around critical infrastructure The fibre optic cables also form smart perimeters around critical infrastructure like power grids, cell towers, and bridges to watch for physical disturbances or tampering. “Because the system can be customised to each new environment and can learn quickly, the applications are virtually limitless,” says DeBoard. {##Poll1728555696 - Do you believe AI-driven perimeter detection systems will significantly reduce security labour costs?##}
Case studies
Encore Atlantic Shores is a residential complex of 240 luxurious townhomes for ages 55 and over in Eastport, New York. Completed in 2011, the site boasts an 11,800 square foot clubhouse, with amenities such as a fitness centre, heated indoor pool, whirlpool spa, multi-purpose ballroom, cardroom and clubroom with billiards, tennis courts and an outdoor putting green. The complex required an update to their legacy security system, so they reached out to CWC Security to specify a new and modern solution for their site. Paxton’s Net2 access control system Paxton’s Net2 access control system due to its flexibility to integrate with multiple other systems CWC Security, based in Melville, New York, specialises in designing, installing, and monitoring state-of-the-art security systems that offer comprehensive protection for residential and commercial spaces. They chose Paxton’s Net2 access control system due to its flexibility to integrate with multiple other systems that were already on Encore’s network. Paxton, the security technology manufacturer, designs and develops access control systems, video intercom products, IP cameras, and wireless door handles that are installed and used globally. Requirement Encore Atlantic Shores needed to update all internal and external entry and exit points on the premises, including their access-controlled gates to allow flexible access permissions. Additionally, multiple areas of the site were on different internet networks, which needed to be managed from one central location. There is a clubhouse that also required permission-based access for summer residents who are not members of the clubhouse but need access to the pool. The property manager utilises Net2 software to provide temporary access rights during these times for different members. The site’s pool management personnel also require separate access to the basement for equipment storage. Solution Net2 is Paxton’s networked access control system that can be administered using one or more PCs Michael Pittakas, owner of CWC Security, presented Encore Atlantic Shores with Net2 as a solution. Net2 is Paxton’s networked access control system that can be administered using one or more PCs and can be monitored and managed from a central location. The software is designed to easily integrate with other security systems. This made it straightforward to run alongside the sites existing systems and further streamline security for their staff and residents alike. Net2 now secures all primary entry points to the complex, with keyfobs provided to residents to access the front gate. For deliveries and garbage collection, the rear gate is also controlled via the Net2 software. This enables Erin Stewart, the Property Manager, to open the gate for these vehicles when needed. Video intercom system Michael said: “The front and rear gates are relay controlled, so we utilised triggers and actions within Net2 to provide access.” “We also integrated Net2 with the existing video intercom system at the front gate so that non-residents call the security booth before they can enter the premises. This is then recorded as an event in the Net2 software.” Result Erin at Encore Atlantic Shores has been very pleased with the Net2 system and CWC’s service Since the installation took place, Erin at Encore Atlantic Shores has been very pleased with the Net2 system and CWC’s assistance and support. Michael explained “I showed Erin how to create schedules, control the property via the Net2 software, and setup the correct access permissions.” Erin said: “We find Net2 to be the perfect fit for our needs at Encore Atlantic Shores. The software is user-friendly, reliable, and customisable. Having the ability to program keyfobs with different access levels has been a tremendous help with vendors who may need access during hours with limited staff. The reporting ability gives you a record of who and when someone uses a keyfob to enter the Clubhouse.” Setup of a Net2 system CWC, a Silver Paxton Partner, commissioned the site via the Paxton Installer app’s commissioning feature. This makes the setup of a Net2 system simpler and faster than ever before, as it saves installers from having to write down the products’ serial numbers to add them into the Net2 software afterwards.
ZeroEyes, the creators of the first AI-based gun detection video analytics platform to earn the US Department of Homeland Security SAFETY Act Designation, announced that its proactive gun detection and intelligent situational awareness solution has been deployed at Scott County R-IV School District in Benton, Missouri, to mitigate gun-related violence. The deployment was facilitated by Freedom Security, a local security provider serving the greater Missouri Area. Robust security upgrades Located in a rural community near the borders of Illinois and Kentucky, Scott County R-IV School District consists of a single campus with three interconnected buildings serving students from pre-K through 12th grade. The district educates approximately 800 students annually and employs around 125 teachers and administrators. ZeroEyes is the newest addition to the district's robust security upgrades, which include window tints, HAVEN locks, integrations with CrisisGo, and more. Digital security cameras ZeroEyes’ AI gun detection and intelligent situational awareness software layer onto existing cameras ZeroEyes’ AI gun detection and intelligent situational awareness software layer onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Centre (ZOC), the industry’s only U.S.-based, fully in-house operation centre, which is staffed 24/7/365 by specially trained U.S. military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and school administration as quickly as 3 to 5 seconds from detection. ZeroEyes safety strategy “ZeroEyes is not intrusive or invasive, and it does more than just detect; it alerts, responds, and continues to do so throughout any situation involving a potential threat,” said Dr. Bradley Kolwyck, Superintendent of Scott County R-IV School District. “This technology is the final piece we needed to ensure every layer of our safety strategy is connected, enabling us to provide the safest environment possible.” ZeroEyes deployment ZeroEyes and the district are hosting a Lunch & Learn session at 11:00 am at the Scott County ZeroEyes and the district are hosting a Lunch & Learn session at 11:00 am at the Scott County R-IV District Office (4035 State Highway 77, Benton, MO). It will feature demonstrations and discussion sessions, including reflections from school pioneers on the district’s successful ZeroEyes deployment. The event is open to local schools, law enforcement, and media. ZeroEyes’ innovation and protection “I commend Scott County R-IV School District for taking the initiative to lean into innovation and proactively protect its students from gun-related violence,” said Mike Lahiff, CEO and cofounder of ZeroEyes. “ZeroEyes’ ability to provide first responders and law enforcement with advance warning and situational awareness empowers them to act quickly and save lives.”
Richard Thorp has been fascinated with aviation since childhood. A self-described “aviation geek,” Thorp is now the Chief Technology Officer at Swissport International AG, where he leads IT infrastructure strategy for the world’s largest ground-handling company, ensuring seamless operations across 276 airports in 45 countries, handling approximately 247 million airline passengers per year, as of the end of 2024. “If we were an airline, we’d actually be the biggest airline in the world in terms of a number of passengers we support and handle,” he says. Security challenges Swissport’s goal is to make a tangible impact on people’s lives by enabling smooth air travel Swissport’s goal is to make a tangible impact on people’s lives by enabling smooth air travel. “If the things we do get people to their destinations safely and on time, then magically, we become more successful and profitable as an organisation,” he says. But casting that spell had been challenging for Swissport. Three years ago, legacy IT leadership at Swissport had overcome network challenges with Cato, but more work was needed to address their security challenges, particularly in securing endpoints. Thorp and Swissport CISO, Giles Ashton-Roberts, joined Swissport in the middle of the Cato deployment. Having deep experience with a legacy zero trust provider, they were skeptical that Cato could meet Swissport’s requirements. Cato platform Over the next 10 months of meetings, investigation, and testing Thorp and Ashton-Roberts challenged Cato, ultimately changing their perspective. “IT is no longer seen as a blocker; it just works,” says Thorp. “I relax a bit more with the Cato platform around. It’s given us holistic way of protecting ourselves today, and a secure foundation for everything we want to do in the future.” The challenges of a global, always-on operation Swissport’s network helps millions of passengers, cargo shipments, and lounges worldwide Swissport’s network supports millions of passengers, cargo shipments, and lounges worldwide. Three years ago, scale was an enormous challenge—ensuring reliable connectivity for operations spanning locations and time zones. The company relied on a mix of MPLS and regional SD-WAN solutions across its now 320+ sites and airport locations. But bandwidth limitations and performance variability impacted many applications, including cloud-based, mission-critical applications. As a result of that complicated network, expanding to new locations was resource-intensive, requiring manual setup and multiple vendor dependencies. Differences between networking tools made troubleshooting inconsistent and time-consuming. The IT team in turn had to maintain expertise in multiple networking technologies, increasing operational overhead. What security inspection existed for unencrypted traffic Visibility was an enormous challenge. With multiple network platforms in place, Swissport’s IT team lacked a centralised view of network performance and security threats. “In the past, working with multiple systems meant inconsistency,” says Thorp. “Different platforms required different configurations, which complicated troubleshooting and made security enforcement a challenge.” Swissport relied on a patchwork of security appliances, including firewalls and web gateways. Remote users are connected through different VPN servers deployed across different regions. The complex appliance stack required manual maintenance and lacked centralised visibility and control. Security patching was manual and error-prone and implementing consistent security policies was practically impossible, weakening Swissport’s security posture. What security inspection existed was relegated to unencrypted traffic due to the well-founded concern that inspecting encrypted traffic could break the application experience that in this case were airline partners’ systems. Finally, the lack of consistent, advanced threat detection worldwide limited Swissport’s ability to detect and stop threats. Visibility differentiates the Cato SASE cloud platform Thorp and the IT team had initially leaned away towards deploying that architecture Recognising these inefficiencies, Swissport’s legacy IT team initiated the Cato relationship, connecting many of the now 320+ sites and instances in AWS and Azure to the Cato SASE Cloud Platform. When Thorp and the new IT leadership joined Swissport, about two-thirds of the connections had been deployed. Having been familiar with a legacy cybersecurity provider, Thorp and the IT team had initially leaned away towards deploying that architecture. Hearing about the value of Cato they decided to have a closer look. “What really drew me to Cato is the visibility the platform provides. It’s incredibly easy to pinpoint connectivity issues, analyse traffic patterns, and secure our network from a single interface,” says Thorp. Cato uniquely stores the metadata of all enterprise traffic crossing the Cato SASE Cloud Platform — whether to the Internet or another location — from all endpoints — in the office and outside of it — in a single data store. This incredible resource provides Cato customers with deep, end-to-end insight into their complete network. Much improved security and a better network With a platform that is resilient, secure, and easy to manage, Swissport has been able to take a more proactive approach to security, streamline IT processes, and ensure a seamless digital experience for employees across the globe. Advanced threat prevention now operates globally and protects against malware and ransomware even in encrypted traffic. “Cato’s TLS Inspection gives us the ability to inspect encrypted traffic while avoiding unintended service disruptions,” says Ashton-Roberts. “It’s been a major improvement to our security posture.” Fine-grained access control through the always-on Cato Client connects remote users to Cato, granting access only to permitted resources. The Cato Client fully implements zero trust principles and operates outside and inside the office under one common policy set. “With Cato, every device—whether in a Swissport office or in an airport lounge—operates under the same set of security policies. That level of consistency wasn’t possible before,” says Ashton-Roberts. Deploying new network sites Cato not only delivers optimised network version worldwide but also makes deploying new networks Access is across the Cato Global Private Backbone built into the Cato SASE Cloud Platform, delivering an exceptional, secure user experience anywhere in the world. Cato not only delivers optimised network performance worldwide but also makes deploying new network sites effortless. “Connecting new airlines or contracts now takes just a few clicks,” says Thorp. Thorp’s team has also dramatically reduced network resolution times. “We recently identified and solved a performance issue in a South African location that would have taken us days before Cato,” says Thorp. “Within 15 minutes, our team identified excessive database traffic, blocked the device, and restored normal operations.” Transforming IT by transforming the infrastructure The transformative impact of the Cato SASE Cloud Platform on the IT team has been profound. Previously, managing multiple networking platforms required maintaining expertise in diverse technologies, creating an operational burden. The IT staff was constantly troubleshooting connectivity issues, manually configuring security appliances, and dealing with inconsistent policies across different locations. The shift to Cato not only simplified management but also allowed the IT team to focus on higher-value strategic initiatives. “Before Cato, we had to maintain different skill sets for different platforms, which spread the team thin. Now, we have one standardised system that allows us to be much more efficient,” Thorp says. Newfound network visibility Swissport has been able to optimise resource allocation and improve overall productivity By consolidating security and networking into a single platform, Swissport has been able to optimise resource allocation and improve overall productivity. The newfound network visibility has also brought a shift from reactive to a proactive IT strategy that has helped the company ensure consistent service delivery across its global operations. “For me, Cato future proofs Swissport’s IT infrastructure,” says Thorp. “The platform constantly evolves, adapts to new technologies, and provides the visibility and security we need to support our business today and tomorrow.” Partnership with Cato proved unique The success of Swissport’s IT transformation was built on more than just technology—it was about forming a strong, collaborative relationship with Cato Networks. From the start, Cato worked closely with Swissport to understand its unique challenges and deliver tailored solutions that addressed its global security and networking needs. “We worked directly with Cato’s product team to enhance capabilities—not just for us, but for all customers,” says Thorp. The success of Swissport’s IT transformation was built on more than just technology Features requested by Swissport were implemented on schedule, unlike other vendors who provided only lip service. Thorp says, “Many vendors say they listen, but Cato actually delivers on what they promise.” This close partnership has given Swissport confidence that its evolving needs will continue to be met as Cato refines its platform. “With Cato, we’re not just another customer; we’re part of a continuous innovation cycle that ensures our IT infrastructure remains future-ready,” says Thorp. “It’s rare to find a vendor so responsive and committed to delivering what they promise.” Looking ahead to the future Swissport IT requirements continue to evolve with Cato remaining a key pillar. “With Cato in place, we know that our network is not the limiting factor in our growth,” Thorp explains. The ongoing partnership between Swissport and Cato ensures that as technology continues to evolve, Swissport’s IT infrastructure remains secure, scalable, and adaptable to the demands of a fast-paced aviation industry. On a personal level, Cato has given Thorp peace of mind. “I relax a bit more with the Cato platform around. It’s given us a holistic way of protecting ourselves today and a secure foundation for everything we want to do in the future. Swissport’s IT leadership now can focus on innovation rather than crisis management.”
Omnilert, a pioneer in AI-driven safety solutions and AT&I Systems, announced that Amerant Bank has chosen Omnilert’s AI technology to help bolster the security at all of its locations in Florida. AT&I Systems, a longtime security partner of Amerant Bank, was chosen as the security integrator. Omnilert’s software, which recently received the full SAFETY Act Designation by the U.S. Department of Homeland Security (DHS), will be integrated into more than 160 existing Amerant Bank cameras to provide advanced 24/7 surveillance with automated response capabilities. Key layer of security “Omnilert technology has become a key layer of security that can transform traditional surveillance capabilities and ensure a fast, robust and automatic response in an emergency,” said Dave Fraser, CEO of Omnilert. “With our software running non-stop in the background, Amerant can focus on carrying out their daily business knowing their workers and patrons are being kept safe from harm.” New and innovative ways to enhance the safety “At Amerant Bank, we are always looking for new and innovative ways to enhance the safety of our bank locations, and Omnilert’s AI technology will be an important part of our overall security infrastructure,” said Orlando Gonzalez, Head of Corporate Security at Amerant Bank. “Integrating the software into our existing cameras made the installation quick and seamless, and once installed, it transformed these cameras into powerful, intelligent surveillance devices that are constantly detecting potential threats.”
Gunnebo Entrance Control has successfully installed its BoardSec intelligent airport boarding gate system at Chongqing Jiangbei International Airport’s Terminal 3, as part of a major smart renovation and upgrade program. As the primary international gateway for Chongqing - one of the world's most populous cities - Jiangbei International Airport handled over 40 million passengers in 2024, ranking among the top ten busiest airports in mainland China. Gunnebo’s top visual recognition technology To enhance security and streamline airport operations, Gunnebo Entrance Control has supplied over 150 BoardSec systems, integrating advanced biometric face recognition and cutting-edge visual behaviour identification technology to revolutionise self-boarding. Traditional boarding gates often struggle to detect complex passenger behaviours. Gunnebo’s Top Visual Recognition Technology leverages high-precision camera arrays and deep-learning algorithms to identify over 20 types of risky behaviours, including tailgating, reversing, and unattended luggage. If an item is left unattended beyond a set time, the system automatically alerts staff—reducing manual checks and improving efficiency by 90%. Gunnebo Entrance Control’s intelligent boarding solution Implementation of Gunnebo Entrance Control’s intelligent boarding key has enhanced active efficiency Chongqing Jiangbei International Airport has praised the system’s ability to optimise passenger experience while enabling data-driven operational management. The implementation of Gunnebo Entrance Control’s intelligent boarding solution has significantly enhanced operational efficiency while ensuring a smoother, more secure journey for passengers. This innovation supports the vision of Chongqing International Airport becoming a pioneering intelligent aviation hub in China. Advancements in 5G and edge computing Says Davis Zhang, Vice-President China for Gunnebo Entrance Control: “As a trusted intelligent solution provider for nearly 100 international airports worldwide, Gunnebo Entrance Control is proud to support Chongqing’s digital transformation." "With advancements in 5G and edge computing, we remain committed to driving innovation in China’s civil aviation industry. This project is a testament to our global capability to transform large transport hubs - delivering security, efficiency, and an enhanced passenger experience without compromise.” BoardSec’s next-generation The system uses truly even in hard conditions like strong backlighting or mask-wearing BoardSec’s next-generation multi-spectrum face recognition system enables seamless identity verification - passengers simply walk through the gate as dual-mode imaging (near-infrared and visible light) confirms identity in just 0.3 seconds with 99.98% accuracy. The system operates effectively even in challenging conditions such as strong backlighting or mask-wearing. By eliminating manual code scanning, BoardSec cuts queue times by 70%, increasing single-gate capacity from 180 to 320 passengers per hour. Real-time monitoring of gate operations Gunnebo Entrance Control has also equipped the airport with an intelligent equipment management platform, providing real-time monitoring of gate operations, passenger flow, and system health. Powered by AI, the platform automatically opens additional gates during peak demand, initiates remote diagnostics for maintenance issues, and boosts overall operational efficiency by 60%.
RGB Spectrum™, a pioneer in mission-critical video solutions for real-time decision support, announced that the City of Norman, Oklahoma, has selected the company to deliver a video processing and control system for its new Traffic Management Centre (TMC). This innovative display approach will replace the traditional front-of-room screen with personal console-based video walls, setting a new standard for operational efficiency. RGB Spectrum’s Zio® 4000 series New system redefines what’s possible in compact, efficient traffic management environments Designed in partnership with global engineering and design firm Stantec, the new system redefines what’s possible in compact, efficient traffic management environments. At the core of the deployment is RGB Spectrum’s Zio® 4000 series video processor, XtendPoint® KVM-over-IP, and RGB Rack PCs, enabling seamless, customised workflows to operators. Norman’s commitment “Norman’s commitment to cutting-edge technology ensures we can effectively monitor traffic patterns and enhance safety for all who live, work, and travel through our city,” said David R. Riesland, City Transportation Engineer, City of Norman. “This project has been over 15 years in the making, and it’s incredibly rewarding to see that long-time vision finally become reality. We’re excited to partner with RGB Spectrum to implement a best-in-class solution that supports our mission.” Five discrete networks The new 2,300 square-foot facility will be transformed from a shell space into a highly functional centre, including three offices, an operations room, and an IT room. Within the operations space, four operators oversee five discrete networks—ranging from ATMS/ITS and enterprise to public safety, security, and web administration—through a fully distributed architecture. Each operator will have access to five dedicated Rack PCs located remotely in the IT room, allowing for quiet, clutter-free workstations and centralised maintenance. RGB Spectrum’s XtendPoint KVM The upper displays at the station serve as “videowalls,” dynamically combining a mix of sources Using RGB Spectrum’s XtendPoint KVM-over-IP with multiviewing capability, operators control and interact with any PC across any network from their consoles. The upper displays at each station serve as personalised “videowalls,” dynamically combining a mix of sources. Each operator can mirror a common display layout or configure their own unique, task-specific view. RGB Spectrum performance and adaptability In total, any operator can control and view any or all of the 20 Rack PCs, providing a flexible and resilient operations environment. Whether deploying a centralised videowall or a decentralised, operator-specific layout, RGB Spectrum delivers the mission-critical performance and adaptability that modern traffic management centres demand.
Encore Atlantic Shores is a residential complex of 240 luxurious townhomes for ages 55 and over in Eastport, New York. Completed in 2011, the site boasts an 11,800 square foot clubhouse, with amenities such as a fitness centre, heated indoor pool, whirlpool spa, multi-purpose ballroom, cardroom and clubroom with billiards, tennis courts and an outdoor putting green. The complex required an update to their legacy security system, so they reached out to CWC Security to specify a new and modern solution for their site. Paxton’s Net2 access control system Paxton’s Net2 access control system due to its flexibility to integrate with multiple other systems CWC Security, based in Melville, New York, specialises in designing, installing, and monitoring state-of-the-art security systems that offer comprehensive protection for residential and commercial spaces. They chose Paxton’s Net2 access control system due to its flexibility to integrate with multiple other systems that were already on Encore’s network. Paxton, the security technology manufacturer, designs and develops access control systems, video intercom products, IP cameras, and wireless door handles that are installed and used globally. Requirement Encore Atlantic Shores needed to update all internal and external entry and exit points on the premises, including their access-controlled gates to allow flexible access permissions. Additionally, multiple areas of the site were on different internet networks, which needed to be managed from one central location. There is a clubhouse that also required permission-based access for summer residents who are not members of the clubhouse but need access to the pool. The property manager utilises Net2 software to provide temporary access rights during these times for different members. The site’s pool management personnel also require separate access to the basement for equipment storage. Solution Net2 is Paxton’s networked access control system that can be administered using one or more PCs Michael Pittakas, owner of CWC Security, presented Encore Atlantic Shores with Net2 as a solution. Net2 is Paxton’s networked access control system that can be administered using one or more PCs and can be monitored and managed from a central location. The software is designed to easily integrate with other security systems. This made it straightforward to run alongside the sites existing systems and further streamline security for their staff and residents alike. Net2 now secures all primary entry points to the complex, with keyfobs provided to residents to access the front gate. For deliveries and garbage collection, the rear gate is also controlled via the Net2 software. This enables Erin Stewart, the Property Manager, to open the gate for these vehicles when needed. Video intercom system Michael said: “The front and rear gates are relay controlled, so we utilised triggers and actions within Net2 to provide access.” “We also integrated Net2 with the existing video intercom system at the front gate so that non-residents call the security booth before they can enter the premises. This is then recorded as an event in the Net2 software.” Result Erin at Encore Atlantic Shores has been very pleased with the Net2 system and CWC’s service Since the installation took place, Erin at Encore Atlantic Shores has been very pleased with the Net2 system and CWC’s assistance and support. Michael explained “I showed Erin how to create schedules, control the property via the Net2 software, and setup the correct access permissions.” Erin said: “We find Net2 to be the perfect fit for our needs at Encore Atlantic Shores. The software is user-friendly, reliable, and customisable. Having the ability to program keyfobs with different access levels has been a tremendous help with vendors who may need access during hours with limited staff. The reporting ability gives you a record of who and when someone uses a keyfob to enter the Clubhouse.” Setup of a Net2 system CWC, a Silver Paxton Partner, commissioned the site via the Paxton Installer app’s commissioning feature. This makes the setup of a Net2 system simpler and faster than ever before, as it saves installers from having to write down the products’ serial numbers to add them into the Net2 software afterwards.
ZeroEyes, the creators of the first AI-based gun detection video analytics platform to earn the US Department of Homeland Security SAFETY Act Designation, announced that its proactive gun detection and intelligent situational awareness solution has been deployed at Scott County R-IV School District in Benton, Missouri, to mitigate gun-related violence. The deployment was facilitated by Freedom Security, a local security provider serving the greater Missouri Area. Robust security upgrades Located in a rural community near the borders of Illinois and Kentucky, Scott County R-IV School District consists of a single campus with three interconnected buildings serving students from pre-K through 12th grade. The district educates approximately 800 students annually and employs around 125 teachers and administrators. ZeroEyes is the newest addition to the district's robust security upgrades, which include window tints, HAVEN locks, integrations with CrisisGo, and more. Digital security cameras ZeroEyes’ AI gun detection and intelligent situational awareness software layer onto existing cameras ZeroEyes’ AI gun detection and intelligent situational awareness software layer onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Centre (ZOC), the industry’s only U.S.-based, fully in-house operation centre, which is staffed 24/7/365 by specially trained U.S. military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and school administration as quickly as 3 to 5 seconds from detection. ZeroEyes safety strategy “ZeroEyes is not intrusive or invasive, and it does more than just detect; it alerts, responds, and continues to do so throughout any situation involving a potential threat,” said Dr. Bradley Kolwyck, Superintendent of Scott County R-IV School District. “This technology is the final piece we needed to ensure every layer of our safety strategy is connected, enabling us to provide the safest environment possible.” ZeroEyes deployment ZeroEyes and the district are hosting a Lunch & Learn session at 11:00 am at the Scott County ZeroEyes and the district are hosting a Lunch & Learn session at 11:00 am at the Scott County R-IV District Office (4035 State Highway 77, Benton, MO). It will feature demonstrations and discussion sessions, including reflections from school pioneers on the district’s successful ZeroEyes deployment. The event is open to local schools, law enforcement, and media. ZeroEyes’ innovation and protection “I commend Scott County R-IV School District for taking the initiative to lean into innovation and proactively protect its students from gun-related violence,” said Mike Lahiff, CEO and cofounder of ZeroEyes. “ZeroEyes’ ability to provide first responders and law enforcement with advance warning and situational awareness empowers them to act quickly and save lives.”
Richard Thorp has been fascinated with aviation since childhood. A self-described “aviation geek,” Thorp is now the Chief Technology Officer at Swissport International AG, where he leads IT infrastructure strategy for the world’s largest ground-handling company, ensuring seamless operations across 276 airports in 45 countries, handling approximately 247 million airline passengers per year, as of the end of 2024. “If we were an airline, we’d actually be the biggest airline in the world in terms of a number of passengers we support and handle,” he says. Security challenges Swissport’s goal is to make a tangible impact on people’s lives by enabling smooth air travel Swissport’s goal is to make a tangible impact on people’s lives by enabling smooth air travel. “If the things we do get people to their destinations safely and on time, then magically, we become more successful and profitable as an organisation,” he says. But casting that spell had been challenging for Swissport. Three years ago, legacy IT leadership at Swissport had overcome network challenges with Cato, but more work was needed to address their security challenges, particularly in securing endpoints. Thorp and Swissport CISO, Giles Ashton-Roberts, joined Swissport in the middle of the Cato deployment. Having deep experience with a legacy zero trust provider, they were skeptical that Cato could meet Swissport’s requirements. Cato platform Over the next 10 months of meetings, investigation, and testing Thorp and Ashton-Roberts challenged Cato, ultimately changing their perspective. “IT is no longer seen as a blocker; it just works,” says Thorp. “I relax a bit more with the Cato platform around. It’s given us holistic way of protecting ourselves today, and a secure foundation for everything we want to do in the future.” The challenges of a global, always-on operation Swissport’s network helps millions of passengers, cargo shipments, and lounges worldwide Swissport’s network supports millions of passengers, cargo shipments, and lounges worldwide. Three years ago, scale was an enormous challenge—ensuring reliable connectivity for operations spanning locations and time zones. The company relied on a mix of MPLS and regional SD-WAN solutions across its now 320+ sites and airport locations. But bandwidth limitations and performance variability impacted many applications, including cloud-based, mission-critical applications. As a result of that complicated network, expanding to new locations was resource-intensive, requiring manual setup and multiple vendor dependencies. Differences between networking tools made troubleshooting inconsistent and time-consuming. The IT team in turn had to maintain expertise in multiple networking technologies, increasing operational overhead. What security inspection existed for unencrypted traffic Visibility was an enormous challenge. With multiple network platforms in place, Swissport’s IT team lacked a centralised view of network performance and security threats. “In the past, working with multiple systems meant inconsistency,” says Thorp. “Different platforms required different configurations, which complicated troubleshooting and made security enforcement a challenge.” Swissport relied on a patchwork of security appliances, including firewalls and web gateways. Remote users are connected through different VPN servers deployed across different regions. The complex appliance stack required manual maintenance and lacked centralised visibility and control. Security patching was manual and error-prone and implementing consistent security policies was practically impossible, weakening Swissport’s security posture. What security inspection existed was relegated to unencrypted traffic due to the well-founded concern that inspecting encrypted traffic could break the application experience that in this case were airline partners’ systems. Finally, the lack of consistent, advanced threat detection worldwide limited Swissport’s ability to detect and stop threats. Visibility differentiates the Cato SASE cloud platform Thorp and the IT team had initially leaned away towards deploying that architecture Recognising these inefficiencies, Swissport’s legacy IT team initiated the Cato relationship, connecting many of the now 320+ sites and instances in AWS and Azure to the Cato SASE Cloud Platform. When Thorp and the new IT leadership joined Swissport, about two-thirds of the connections had been deployed. Having been familiar with a legacy cybersecurity provider, Thorp and the IT team had initially leaned away towards deploying that architecture. Hearing about the value of Cato they decided to have a closer look. “What really drew me to Cato is the visibility the platform provides. It’s incredibly easy to pinpoint connectivity issues, analyse traffic patterns, and secure our network from a single interface,” says Thorp. Cato uniquely stores the metadata of all enterprise traffic crossing the Cato SASE Cloud Platform — whether to the Internet or another location — from all endpoints — in the office and outside of it — in a single data store. This incredible resource provides Cato customers with deep, end-to-end insight into their complete network. Much improved security and a better network With a platform that is resilient, secure, and easy to manage, Swissport has been able to take a more proactive approach to security, streamline IT processes, and ensure a seamless digital experience for employees across the globe. Advanced threat prevention now operates globally and protects against malware and ransomware even in encrypted traffic. “Cato’s TLS Inspection gives us the ability to inspect encrypted traffic while avoiding unintended service disruptions,” says Ashton-Roberts. “It’s been a major improvement to our security posture.” Fine-grained access control through the always-on Cato Client connects remote users to Cato, granting access only to permitted resources. The Cato Client fully implements zero trust principles and operates outside and inside the office under one common policy set. “With Cato, every device—whether in a Swissport office or in an airport lounge—operates under the same set of security policies. That level of consistency wasn’t possible before,” says Ashton-Roberts. Deploying new network sites Cato not only delivers optimised network version worldwide but also makes deploying new networks Access is across the Cato Global Private Backbone built into the Cato SASE Cloud Platform, delivering an exceptional, secure user experience anywhere in the world. Cato not only delivers optimised network performance worldwide but also makes deploying new network sites effortless. “Connecting new airlines or contracts now takes just a few clicks,” says Thorp. Thorp’s team has also dramatically reduced network resolution times. “We recently identified and solved a performance issue in a South African location that would have taken us days before Cato,” says Thorp. “Within 15 minutes, our team identified excessive database traffic, blocked the device, and restored normal operations.” Transforming IT by transforming the infrastructure The transformative impact of the Cato SASE Cloud Platform on the IT team has been profound. Previously, managing multiple networking platforms required maintaining expertise in diverse technologies, creating an operational burden. The IT staff was constantly troubleshooting connectivity issues, manually configuring security appliances, and dealing with inconsistent policies across different locations. The shift to Cato not only simplified management but also allowed the IT team to focus on higher-value strategic initiatives. “Before Cato, we had to maintain different skill sets for different platforms, which spread the team thin. Now, we have one standardised system that allows us to be much more efficient,” Thorp says. Newfound network visibility Swissport has been able to optimise resource allocation and improve overall productivity By consolidating security and networking into a single platform, Swissport has been able to optimise resource allocation and improve overall productivity. The newfound network visibility has also brought a shift from reactive to a proactive IT strategy that has helped the company ensure consistent service delivery across its global operations. “For me, Cato future proofs Swissport’s IT infrastructure,” says Thorp. “The platform constantly evolves, adapts to new technologies, and provides the visibility and security we need to support our business today and tomorrow.” Partnership with Cato proved unique The success of Swissport’s IT transformation was built on more than just technology—it was about forming a strong, collaborative relationship with Cato Networks. From the start, Cato worked closely with Swissport to understand its unique challenges and deliver tailored solutions that addressed its global security and networking needs. “We worked directly with Cato’s product team to enhance capabilities—not just for us, but for all customers,” says Thorp. The success of Swissport’s IT transformation was built on more than just technology Features requested by Swissport were implemented on schedule, unlike other vendors who provided only lip service. Thorp says, “Many vendors say they listen, but Cato actually delivers on what they promise.” This close partnership has given Swissport confidence that its evolving needs will continue to be met as Cato refines its platform. “With Cato, we’re not just another customer; we’re part of a continuous innovation cycle that ensures our IT infrastructure remains future-ready,” says Thorp. “It’s rare to find a vendor so responsive and committed to delivering what they promise.” Looking ahead to the future Swissport IT requirements continue to evolve with Cato remaining a key pillar. “With Cato in place, we know that our network is not the limiting factor in our growth,” Thorp explains. The ongoing partnership between Swissport and Cato ensures that as technology continues to evolve, Swissport’s IT infrastructure remains secure, scalable, and adaptable to the demands of a fast-paced aviation industry. On a personal level, Cato has given Thorp peace of mind. “I relax a bit more with the Cato platform around. It’s given us a holistic way of protecting ourselves today and a secure foundation for everything we want to do in the future. Swissport’s IT leadership now can focus on innovation rather than crisis management.”
Omnilert, a pioneer in AI-driven safety solutions and AT&I Systems, announced that Amerant Bank has chosen Omnilert’s AI technology to help bolster the security at all of its locations in Florida. AT&I Systems, a longtime security partner of Amerant Bank, was chosen as the security integrator. Omnilert’s software, which recently received the full SAFETY Act Designation by the U.S. Department of Homeland Security (DHS), will be integrated into more than 160 existing Amerant Bank cameras to provide advanced 24/7 surveillance with automated response capabilities. Key layer of security “Omnilert technology has become a key layer of security that can transform traditional surveillance capabilities and ensure a fast, robust and automatic response in an emergency,” said Dave Fraser, CEO of Omnilert. “With our software running non-stop in the background, Amerant can focus on carrying out their daily business knowing their workers and patrons are being kept safe from harm.” New and innovative ways to enhance the safety “At Amerant Bank, we are always looking for new and innovative ways to enhance the safety of our bank locations, and Omnilert’s AI technology will be an important part of our overall security infrastructure,” said Orlando Gonzalez, Head of Corporate Security at Amerant Bank. “Integrating the software into our existing cameras made the installation quick and seamless, and once installed, it transformed these cameras into powerful, intelligent surveillance devices that are constantly detecting potential threats.”
Gunnebo Entrance Control has successfully installed its BoardSec intelligent airport boarding gate system at Chongqing Jiangbei International Airport’s Terminal 3, as part of a major smart renovation and upgrade program. As the primary international gateway for Chongqing - one of the world's most populous cities - Jiangbei International Airport handled over 40 million passengers in 2024, ranking among the top ten busiest airports in mainland China. Gunnebo’s top visual recognition technology To enhance security and streamline airport operations, Gunnebo Entrance Control has supplied over 150 BoardSec systems, integrating advanced biometric face recognition and cutting-edge visual behaviour identification technology to revolutionise self-boarding. Traditional boarding gates often struggle to detect complex passenger behaviours. Gunnebo’s Top Visual Recognition Technology leverages high-precision camera arrays and deep-learning algorithms to identify over 20 types of risky behaviours, including tailgating, reversing, and unattended luggage. If an item is left unattended beyond a set time, the system automatically alerts staff—reducing manual checks and improving efficiency by 90%. Gunnebo Entrance Control’s intelligent boarding solution Implementation of Gunnebo Entrance Control’s intelligent boarding key has enhanced active efficiency Chongqing Jiangbei International Airport has praised the system’s ability to optimise passenger experience while enabling data-driven operational management. The implementation of Gunnebo Entrance Control’s intelligent boarding solution has significantly enhanced operational efficiency while ensuring a smoother, more secure journey for passengers. This innovation supports the vision of Chongqing International Airport becoming a pioneering intelligent aviation hub in China. Advancements in 5G and edge computing Says Davis Zhang, Vice-President China for Gunnebo Entrance Control: “As a trusted intelligent solution provider for nearly 100 international airports worldwide, Gunnebo Entrance Control is proud to support Chongqing’s digital transformation." "With advancements in 5G and edge computing, we remain committed to driving innovation in China’s civil aviation industry. This project is a testament to our global capability to transform large transport hubs - delivering security, efficiency, and an enhanced passenger experience without compromise.” BoardSec’s next-generation The system uses truly even in hard conditions like strong backlighting or mask-wearing BoardSec’s next-generation multi-spectrum face recognition system enables seamless identity verification - passengers simply walk through the gate as dual-mode imaging (near-infrared and visible light) confirms identity in just 0.3 seconds with 99.98% accuracy. The system operates effectively even in challenging conditions such as strong backlighting or mask-wearing. By eliminating manual code scanning, BoardSec cuts queue times by 70%, increasing single-gate capacity from 180 to 320 passengers per hour. Real-time monitoring of gate operations Gunnebo Entrance Control has also equipped the airport with an intelligent equipment management platform, providing real-time monitoring of gate operations, passenger flow, and system health. Powered by AI, the platform automatically opens additional gates during peak demand, initiates remote diagnostics for maintenance issues, and boosts overall operational efficiency by 60%.
RGB Spectrum™, a pioneer in mission-critical video solutions for real-time decision support, announced that the City of Norman, Oklahoma, has selected the company to deliver a video processing and control system for its new Traffic Management Centre (TMC). This innovative display approach will replace the traditional front-of-room screen with personal console-based video walls, setting a new standard for operational efficiency. RGB Spectrum’s Zio® 4000 series New system redefines what’s possible in compact, efficient traffic management environments Designed in partnership with global engineering and design firm Stantec, the new system redefines what’s possible in compact, efficient traffic management environments. At the core of the deployment is RGB Spectrum’s Zio® 4000 series video processor, XtendPoint® KVM-over-IP, and RGB Rack PCs, enabling seamless, customised workflows to operators. Norman’s commitment “Norman’s commitment to cutting-edge technology ensures we can effectively monitor traffic patterns and enhance safety for all who live, work, and travel through our city,” said David R. Riesland, City Transportation Engineer, City of Norman. “This project has been over 15 years in the making, and it’s incredibly rewarding to see that long-time vision finally become reality. We’re excited to partner with RGB Spectrum to implement a best-in-class solution that supports our mission.” Five discrete networks The new 2,300 square-foot facility will be transformed from a shell space into a highly functional centre, including three offices, an operations room, and an IT room. Within the operations space, four operators oversee five discrete networks—ranging from ATMS/ITS and enterprise to public safety, security, and web administration—through a fully distributed architecture. Each operator will have access to five dedicated Rack PCs located remotely in the IT room, allowing for quiet, clutter-free workstations and centralised maintenance. RGB Spectrum’s XtendPoint KVM The upper displays at the station serve as “videowalls,” dynamically combining a mix of sources Using RGB Spectrum’s XtendPoint KVM-over-IP with multiviewing capability, operators control and interact with any PC across any network from their consoles. The upper displays at each station serve as personalised “videowalls,” dynamically combining a mix of sources. Each operator can mirror a common display layout or configure their own unique, task-specific view. RGB Spectrum performance and adaptability In total, any operator can control and view any or all of the 20 Rack PCs, providing a flexible and resilient operations environment. Whether deploying a centralised videowall or a decentralised, operator-specific layout, RGB Spectrum delivers the mission-critical performance and adaptability that modern traffic management centres demand.


Products


Round table discussion
In the physical security marketplace, artificial intelligence (AI) has evolved beyond the novelty phase. The emphasis has now shifted to the more practical aspects of implementing AI technology. That a system implements AI is no longer impressive in and of itself. The question becomes: What can this AI system do for me? How can it improve my physical security stance? We asked our Expert Panel Roundtable: How is artificial intelligence (AI) transforming physical security?
Physical security technologies are a prominent tool used by correctional facilities to provide a safe, secure, and controlled environment for staff, inmates, and the wider community. Among several functions, security technologies are used to prevent unauthorised access, to detect contraband, to monitor inmate movements and activities, and to protect staff. For security technology manufacturers, integrators and consultants, the corrections market presents distinctive challenges. We asked our Expert Panel Roundtable: What are the unique aspects of the corrections market, and how should the physical security industry adapt?
As cutting-edge trends go, convergence has been around for at least two decades. The meaning has shifted over the years, and if anything, the idea of convergence has gotten even more aspirational. Unfortunately, the widespread use of the term has also paradoxically undermined its meaning and power. However, today's concept of convergence has matured to provide new levels of benefit for security professionals. We asked our Expert Panel Roundtable: How has the meaning of “convergence” evolved in the security market? How are systems today more converged than ever?
White papers

Integrated access control: reap the benefits of connected security
Download
Getting the most value from Software Subscription Agreements
Download
Combining systems intelligence and human insight for superior security
Download
Why outdated access control systems are a big problem
Download
Preparing your organisation with quality situational awareness
Download
Three Reasons to Upgrade Your Access Control Technology
Download
House Of Smart Cards - How assumptions can open dangerous security gaps
Download
Integrating IT & physical security teams
Download
Top 7 trends to watch in the physical security industry
Download
Boost efficiency and streamline security with integrated access control
Download
Video technology strategies for hospitals are moving beyond security
Download
IoT connectivity
Download
Creating a secure and positive healthcare experience
Download
Unified physical security
Download
Integrated access control: reap the benefits of connected security
Download
Getting the most value from Software Subscription Agreements
Download
Combining systems intelligence and human insight for superior security
Download
Why outdated access control systems are a big problem
Download
Preparing your organisation with quality situational awareness
Download
Three Reasons to Upgrade Your Access Control Technology
Download
House Of Smart Cards - How assumptions can open dangerous security gaps
Download
Integrating IT & physical security teams
Download
Top 7 trends to watch in the physical security industry
Download
Boost efficiency and streamline security with integrated access control
Download
Video technology strategies for hospitals are moving beyond security
Download
IoT connectivity
Download
Creating a secure and positive healthcare experience
Download
Unified physical security
Download

Videos
Integration software: Manufacturers & Suppliers

Using artificial intelligence (AI) to automate physical security systems
Download
A modern guide to data loss prevention
Download
7 proven solutions for law enforcement key control and asset management
Download
The truth behind 9 mobile access myths
Download
Access control system planning phase 2
Download