Covert Surveillance
Genetec Inc., the pioneer in enterprise physical security software, announced the AutoVu™ ANPR Analysis Reports plugin, an advanced investigation tool that expands ANPR-based forensic search capabilities within Genetec™ Security Centre. The new plugin empowers law enforcement officers and investigators to quickly narrow down a pool of suspects using vehicle behaviour patterns—specifically driving speed and travel cohorts. By eliminating manual data sorting and enabling ta...
The role of audio in physical security is multifaceted and increasingly vital, offering a layer of intelligence and interaction that access control and/or video surveillance alone cannot provide. Sounds provide crucial context to visual events. For instance, someone running might appear suspicious on video, but audio could reveal they are shouting for help, changing the interpretation entirely. Even so, historically speaking, audio has been an underused component in physical security. How is the...
Artificial Intelligence isn’t just a buzzword anymore. It has become part of our lives, and its uses and applications are growing every other day. Even the public sector, which usually is a late adopter of new technologies, has come onboard this new train. Law enforcement, in particular, has seen the advantages different AI technologies can offer to their work and has started to integrate them into their workflow and daily routines. But there is much more to come. Task automation: AI as...
Hanwha Vision, the global vision solution provider, has added AI capabilities to its compact range of mobile cameras. The range, including models TNV-C8014RM and TNV-C8034RM, showcases powerful AI analytics, alongside colour detection of clothing and vehicles, and dynamic privacy masking. At only 55mm in height, the solution is discreet and well suited to spaces with low ceilings, such as buses and trains. Dynamic Privacy Masking Dynamic Privacy Masking is a standout feature of the AI mobil...
Elite Interactive Solutions, a remote video guarding pioneer using proprietary intelligence and integration to achieve proven crime and catastrophe prevention, announces that the company was selected this month as one of three finalists for The Monitoring Association’s (TMA) 2025 Excellence Awards. The prestigious program nominated Elite for its highest honour, Monitoring Centre of the Year. The TMA Excellence Awards recognise any FM-Approved, Intertek/ETL or UL‐Listed monitoring centre a...
Check Point Software Technologies Ltd., a pioneer in cybersecurity solutions, and Illumio, the breach containment company, announced a strategic partnership to help organisations strengthen security and advance their Zero Trust posture. Illumio Segmentation and Insights The integration between the Check Point Infinity Platform and the Illumio Platform delivers rapid identification and mitigation of lateral movement risks across hybrid and multi-cloud environments using advanced microsegmentati...
News
Dallmeier electronic, one of the pioneering manufacturers of video technology “Made in Germany”, presents innovative solutions for more security and efficiency in logistics at the Transport Logistic 2025 in Munich. At the joint stand of the Mobility & Logistics Cluster (Hall B1, Stand 433/534) from 2 to 5 June 2025, the Dallmeier experts will demonstrate state-of-the-art camera systems and video analytics for the effective monitoring and protection of indoor/outdoor areas and perimeters. Securing large areas–total cost of ownership In addition to the flexible Domera® camera systems, the focus is on Panomera® multifocal sensor technology In addition to the flexible Domera® camera systems, the focus is on Panomera® multifocal sensor technology. This patented technology enables logistics companies to monitor large areas, such as warehouses or loading zones, with a minimum of hardware. Up to eight lenses and sensors ensure consistently high resolution, even in distant areas. With significantly fewer cameras required, infrastructure and personnel requirements are reduced. Operators benefit not only from an improved overview, but also from significantly lower total cost of ownership compared to conventional video technology. Efficient claims management and TAPA-compliant security By combining an overall view with any number of detailed images, Panomera® technology significantly improves claims management. Damage or loss of goods in transit can be reliably documented and subsequently traced. In addition, any part of the premises to be monitored can be easily covered in accordance with the international standard DIN EN 62676-4 for video surveillance systems, helping those responsible to meet TAPA requirements. AI-based perimeter protection Panomera® S4 Perimeter offers a powerful solution for perimeter protection, with minimal false alarm rates For superior perimeter protection, Dallmeier presents the Panomera® S4 Perimeter. This system combines a specially developed perimeter AI for the reliable detection of intruders with the extended AI Tamper Detection for the detection of even advanced tampering attempts. The neural network detects people wearing camouflage as well as tampering attempts such as twisting, defocusing, spraying or blinding the camera. Even fogging of the detection area by pyrotechnics is reliably detected. With a range of up to 200 metres at a resolution density above 125 pixels per metre, the Panomera® S4 Perimeter offers a powerful solution for perimeter protection – with minimal false alarm rates. Comprehensive security solutions for logistics companies “Logistics companies today are faced with the challenge of increasing their security standards and at the same time improving the efficiency of their processes”, explains Christian Linthaler, CSO of Dallmeier electronic. “Our solutions not only provide protection against theft and vandalism but also offer real added value by optimising logistics processes – from damage management to improving process security.”
A new report jointly issued by the Rutgers University Miller Center on Policing and Community Resilience, the Global Consortium of Law Enforcement Training Executives (GCLETE), and the Life Safety Alliance (LSA) addresses rising concerns from civil liberties groups over the use of drones by law enforcement. The comprehensive white paper presents evidence that unmanned aerial systems (UAS)—commonly referred to as drones—are saving lives, improving officer safety, and increasing police efficiency at a time when departments nationwide face severe staffing shortages. Severe staffing shortages However, the report’s authors conclude that such fears are largely speculative or anecdotal The report responds directly to recent claims by organizations such as the American Civil Liberties Union (ACLU), which has warned that police drone programs may usher in an era of mass aerial surveillance. However, the report’s authors conclude that such fears are largely speculative or anecdotal. “Civil liberties are a precious cornerstone of democratic societies,” said Michael Gips, co-author and President of the Life Safety Alliance. “We need to respect and preserve them. But our analysis shows that drones are being used responsibly and transparently, with policies and oversight already in place in many jurisdictions.” Law enforcement drone The 32-page report: Cites dozens of examples of drones aiding search-and-rescue, criminal apprehension, and public safety. Highlights a 150% increase in law enforcement drone use since 2018, driven by proven effectiveness. Details model policies, such as the “Five Cs” framework by DRONERESPONDERS, which emphasize privacy, transparency, accountability, and community engagement. Explores case law demonstrating that the U.S. legal system effectively balances competing interests in law enforcement drone use. Presents a sample department policy ensuring strict compliance with FAA regulations, data retention rules, and privacy safeguards. Documents the most significant relevant literature on law enforcement drone use. Outweigh theoretical risks Paul Goldenberg, Chief Advisor to the Miller Center and former DHS Senior Advisor, added: “Now is the time to inform—not inflame—the public about how drones can serve communities while upholding civil rights. This report does just that.” The authors argue against halting Drone as First Responder (DFR) programs, as recommended by the ACLU, stating that the benefits of drone deployment far outweigh theoretical risks. In fact, the report cites hundreds of successful missions, including the rescue of missing persons, apprehension of violent offenders, and disaster response. “Let’s not use fear to undermine a tool that protects our communities,” said Dr. David Grantham, national security expert and co-author. “We need thoughtful policy, not paralysis.”
Hexagon AB announced an agreement to acquire the Unified Communications Radio Suite (UCRS) software assets of CONET Communications GmbH (CCOM), part of CONET Group, to complement its public safety platform. UCRS is a high-performance communication solution for control centres capable of integrating diverse channels such as Private Branch Exchange (PBX) and mobile phone networks, digital radio, business information systems, public address systems, video surveillance (CCTV), video conferencing, and satellite communication infrastructures. Hexagon's public safety platform Successful customers such as the Kassel Fire Brigade already benefit from the combined Hexagon Combining UCRS with Hexagon's public safety platform will provide agencies with a fully integrated command-and-control solution from one vendor. Successful customers such as the Kassel Fire Brigade already benefit from the combined Hexagon and CONET offering. “Seamless communication is an essential part of emergency response. Public safety agencies must be able to communicate with responders in a variety of ways, making the addition of CCOM’s product suite a natural extension of Hexagon’s technology stack,” said Norbert Hanke, interim President and CEO, Hexagon. “This acquisition strengthens our ability to serve public safety customers today while accelerating innovation for the future.” CCOM’s UCRS solution CCOM’s UCRS solution, supported by around 50 employees, will be reported within Hexagon's Safety, Infrastructure & Geospatial division and is expected to generate revenues of around ~10 MEUR in 2025 with margins similar to SIG averages. Completion of the transaction is subject to regulatory approvals and other customary conditions and is expected to be finalised by the end of Q2 2025.
ISS (Intelligent Security Systems), a pioneering provider of video intelligence and data awareness solutions, is proud to announce that our SecurOS® UVSS (Under Vehicle Surveillance System) is now listed on GSA Advantage, an online purchasing platform for U.S. General Services Administration (GSA) Schedule contracts. This milestone simplifies procurement for federal agencies, and it also underscores the commitment to providing advanced video intelligence solutions to the government sector. Advanced security solutions The inclusion of UVSS in the GSA Schedule offers several key advantages, including enhanced accessibility for federal buyers, a streamlined purchasing process, and further affirmation of ISS' dedication to compliance with federal procurement standards. “The listing of the UVSS on GSA Advantage simplifies access to our video intelligence offerings for government agencies, reinforcing our commitment to national security and operational excellence,” said Matt Powell, Managing Director for North America, ISS. “This achievement reflects ISS’ unwavering dedication to delivering advanced security solutions while meeting the highest standards of compliance.” Vehicle threat detection and public safety Inclusion of UVSS in the GSA Schedule offers several key advantages, including enhanced accessibility Phil Jensen, Director of Sales for Under Vehicle Surveillance Systems, ISS, added: “Achieving GSA Schedule status is a major milestone." "It underscores the trust ISS has earned within the government sector and further validates the UVSS as a critical tool for vehicle threat detection and public safety.” About the UVSS The UVSS is a compact, purpose-built system designed to enhance facility security by visually inspecting vehicle undercarriages in as little as three seconds. Leveraging AI-driven analytics, it enables security operators to identify explosives, prohibited items, damage, and various other anomalies across various vehicle types. Key capabilities include high-resolution imaging, integrated licence plate recognition, and compatibility with third-party systems, ensuring adaptability for diverse operational needs. The system is ideal for securing high-risk facilities, including critical infrastructure, military installations, border checkpoints, logistics hubs, and much more.
Deep Sentinel, a pioneer in proactive AI-powered security, has announced the launch of their Gen V Hub. The new product delivers stronger, faster and more affordable security by supporting up to 20 cameras for commercial deployments. Intended users include businesses that use multiple cameras for on-premise security, including multifamily residences, businesses prone to break-ins, auto dealerships and hotel properties. Gen V Hub updates The Gen V has a smaller, sleeker design for easy installation and seamless integration Updates to the Gen V Hub include edge-AI computing, full local video processing for faster performance and enhanced privacy, quieter, more power-efficient operation and enhanced thermal management. The Gen V has a smaller, sleeker design for easy installation and seamless integration across commercial environments. For channel partners and enterprise customers, the Gen V Hub delivers superior performance, long-term supply chain stability and room for future AI enhancements in a smaller, power-efficient device. Enhanced security and scalability "With the Gen V Hub, Deep Sentinel took everything that worked about previous generations and leveled it up," said Jack Azbill, President at Varitec Systems, a current Deep Sentinel partner, adding "We can now offer faster response times, smoother installs, and more robust AI coverage — without passing higher costs to our clients." The Gen V Hub boasts features for channel customers that allow scaling without sacrificing performance or price. 10 active streams at launch, improved network configuration and plug-and-play installation make it easy and cost-effective for businesses to protect their properties. "We’ve already started testing the Gen V Hub with our customers, and the results are outstanding," said Mark Reynoso, Managing Partner at Left Coast Electric, Deep Sentinel partner, adding "It’s faster, more efficient, and makes it easier than ever to deliver top-tier protection across larger sites." Gen V Hub with AI integration Deep Sentinel pairs AI cameras with human guards who can actively intervene to prevent crimes "The Gen V Hub amazed us in the development stages, showing we can run 20 cameras at high quality and still have room to release more AI features as technology evolves," said David Selinger, CEO of Deep Sentinel, adding "This extra capacity is especially important as we continue to advance our use and development of cutting-edge AI models, delivering the most effective and cost-effective security available to both business and home owners anywhere." Deep Sentinel pairs AI cameras with human guards who can actively intervene to prevent crimes. When the systems detect suspicious activity, their proprietary AI verifies the threat and instantly alerts a remote guard. The guard issues a warning and takes further action when necessary. Scalable, next-gen protection Across the country, police departments won’t investigate calls from self-monitoring security systems. Deep Sentinel incorporates human monitoring into its process making its alerts credible to emergency responders. Whether securing a multifamily development, hotel or resort, car dealership or high-risk business, the Gen V Hub provides a stable foundation for scalable, next-gen protection and keeps businesses safe.
The Security Industry Association has sent a letter to U.S. Trade Representative - Jamieson Greer and U.S. Secretary of Commerce - Howard Lutnick requesting relief from tariffs for security industry products and asking that the Trump administration formulate a process that allows companies to apply for product-specific exemptions. Security industry – key segment of the U.S. economy The security industry is an important segment of the U.S. economy, contributing over $430 billion The security industry is an important segment of the U.S. economy, contributing over $430 billion in total economic impact and supporting over 2.1 million jobs. Manufacturers and integrators that provide essential life safety and security products to American consumers are being put under enormous strain, as they struggle to adapt to an uncertain and volatile trading environment. Requests made by SIA Not only do these tariffs hurt manufacturers by increasing the cost of key components as they compete globally, but the additional applicability to finished goods will directly increase the cost of essential security products, potentially pricing out integrators and reducing the availability of key products in the United States. SIA is requesting exemptions for imported components of security systems, security cameras, locks and other door hardware and equipment to include: Alarm systems Access control Camera systems Communications equipment and systems Identity management solutions Security-related uncrewed systems Robotics A range of other cutting-edge security solutions SIA’s agenda It is vitally important that the administration provide this relief to the security industry, and SIA will continue to advocate for this exemption to preserve some stability in the current international trading environment for the industry at large. SIA will continue to anonymously survey the industry and measure how tariffs are affecting their manufacturers and integrators, and they encourage them to reach out to their government relations team with any impact statements that they would like to share.
Dallmeier electronic, one of the pioneering manufacturers of video technology “Made in Germany”, presents innovative solutions for more security and efficiency in logistics at the Transport Logistic 2025 in Munich. At the joint stand of the Mobility & Logistics Cluster (Hall B1, Stand 433/534) from 2 to 5 June 2025, the Dallmeier experts will demonstrate state-of-the-art camera systems and video analytics for the effective monitoring and protection of indoor/outdoor areas and perimeters. Securing large areas–total cost of ownership In addition to the flexible Domera® camera systems, the focus is on Panomera® multifocal sensor technology In addition to the flexible Domera® camera systems, the focus is on Panomera® multifocal sensor technology. This patented technology enables logistics companies to monitor large areas, such as warehouses or loading zones, with a minimum of hardware. Up to eight lenses and sensors ensure consistently high resolution, even in distant areas. With significantly fewer cameras required, infrastructure and personnel requirements are reduced. Operators benefit not only from an improved overview, but also from significantly lower total cost of ownership compared to conventional video technology. Efficient claims management and TAPA-compliant security By combining an overall view with any number of detailed images, Panomera® technology significantly improves claims management. Damage or loss of goods in transit can be reliably documented and subsequently traced. In addition, any part of the premises to be monitored can be easily covered in accordance with the international standard DIN EN 62676-4 for video surveillance systems, helping those responsible to meet TAPA requirements. AI-based perimeter protection Panomera® S4 Perimeter offers a powerful solution for perimeter protection, with minimal false alarm rates For superior perimeter protection, Dallmeier presents the Panomera® S4 Perimeter. This system combines a specially developed perimeter AI for the reliable detection of intruders with the extended AI Tamper Detection for the detection of even advanced tampering attempts. The neural network detects people wearing camouflage as well as tampering attempts such as twisting, defocusing, spraying or blinding the camera. Even fogging of the detection area by pyrotechnics is reliably detected. With a range of up to 200 metres at a resolution density above 125 pixels per metre, the Panomera® S4 Perimeter offers a powerful solution for perimeter protection – with minimal false alarm rates. Comprehensive security solutions for logistics companies “Logistics companies today are faced with the challenge of increasing their security standards and at the same time improving the efficiency of their processes”, explains Christian Linthaler, CSO of Dallmeier electronic. “Our solutions not only provide protection against theft and vandalism but also offer real added value by optimising logistics processes – from damage management to improving process security.”
A new report jointly issued by the Rutgers University Miller Center on Policing and Community Resilience, the Global Consortium of Law Enforcement Training Executives (GCLETE), and the Life Safety Alliance (LSA) addresses rising concerns from civil liberties groups over the use of drones by law enforcement. The comprehensive white paper presents evidence that unmanned aerial systems (UAS)—commonly referred to as drones—are saving lives, improving officer safety, and increasing police efficiency at a time when departments nationwide face severe staffing shortages. Severe staffing shortages However, the report’s authors conclude that such fears are largely speculative or anecdotal The report responds directly to recent claims by organizations such as the American Civil Liberties Union (ACLU), which has warned that police drone programs may usher in an era of mass aerial surveillance. However, the report’s authors conclude that such fears are largely speculative or anecdotal. “Civil liberties are a precious cornerstone of democratic societies,” said Michael Gips, co-author and President of the Life Safety Alliance. “We need to respect and preserve them. But our analysis shows that drones are being used responsibly and transparently, with policies and oversight already in place in many jurisdictions.” Law enforcement drone The 32-page report: Cites dozens of examples of drones aiding search-and-rescue, criminal apprehension, and public safety. Highlights a 150% increase in law enforcement drone use since 2018, driven by proven effectiveness. Details model policies, such as the “Five Cs” framework by DRONERESPONDERS, which emphasize privacy, transparency, accountability, and community engagement. Explores case law demonstrating that the U.S. legal system effectively balances competing interests in law enforcement drone use. Presents a sample department policy ensuring strict compliance with FAA regulations, data retention rules, and privacy safeguards. Documents the most significant relevant literature on law enforcement drone use. Outweigh theoretical risks Paul Goldenberg, Chief Advisor to the Miller Center and former DHS Senior Advisor, added: “Now is the time to inform—not inflame—the public about how drones can serve communities while upholding civil rights. This report does just that.” The authors argue against halting Drone as First Responder (DFR) programs, as recommended by the ACLU, stating that the benefits of drone deployment far outweigh theoretical risks. In fact, the report cites hundreds of successful missions, including the rescue of missing persons, apprehension of violent offenders, and disaster response. “Let’s not use fear to undermine a tool that protects our communities,” said Dr. David Grantham, national security expert and co-author. “We need thoughtful policy, not paralysis.”
Hexagon AB announced an agreement to acquire the Unified Communications Radio Suite (UCRS) software assets of CONET Communications GmbH (CCOM), part of CONET Group, to complement its public safety platform. UCRS is a high-performance communication solution for control centres capable of integrating diverse channels such as Private Branch Exchange (PBX) and mobile phone networks, digital radio, business information systems, public address systems, video surveillance (CCTV), video conferencing, and satellite communication infrastructures. Hexagon's public safety platform Successful customers such as the Kassel Fire Brigade already benefit from the combined Hexagon Combining UCRS with Hexagon's public safety platform will provide agencies with a fully integrated command-and-control solution from one vendor. Successful customers such as the Kassel Fire Brigade already benefit from the combined Hexagon and CONET offering. “Seamless communication is an essential part of emergency response. Public safety agencies must be able to communicate with responders in a variety of ways, making the addition of CCOM’s product suite a natural extension of Hexagon’s technology stack,” said Norbert Hanke, interim President and CEO, Hexagon. “This acquisition strengthens our ability to serve public safety customers today while accelerating innovation for the future.” CCOM’s UCRS solution CCOM’s UCRS solution, supported by around 50 employees, will be reported within Hexagon's Safety, Infrastructure & Geospatial division and is expected to generate revenues of around ~10 MEUR in 2025 with margins similar to SIG averages. Completion of the transaction is subject to regulatory approvals and other customary conditions and is expected to be finalised by the end of Q2 2025.
ISS (Intelligent Security Systems), a pioneering provider of video intelligence and data awareness solutions, is proud to announce that our SecurOS® UVSS (Under Vehicle Surveillance System) is now listed on GSA Advantage, an online purchasing platform for U.S. General Services Administration (GSA) Schedule contracts. This milestone simplifies procurement for federal agencies, and it also underscores the commitment to providing advanced video intelligence solutions to the government sector. Advanced security solutions The inclusion of UVSS in the GSA Schedule offers several key advantages, including enhanced accessibility for federal buyers, a streamlined purchasing process, and further affirmation of ISS' dedication to compliance with federal procurement standards. “The listing of the UVSS on GSA Advantage simplifies access to our video intelligence offerings for government agencies, reinforcing our commitment to national security and operational excellence,” said Matt Powell, Managing Director for North America, ISS. “This achievement reflects ISS’ unwavering dedication to delivering advanced security solutions while meeting the highest standards of compliance.” Vehicle threat detection and public safety Inclusion of UVSS in the GSA Schedule offers several key advantages, including enhanced accessibility Phil Jensen, Director of Sales for Under Vehicle Surveillance Systems, ISS, added: “Achieving GSA Schedule status is a major milestone." "It underscores the trust ISS has earned within the government sector and further validates the UVSS as a critical tool for vehicle threat detection and public safety.” About the UVSS The UVSS is a compact, purpose-built system designed to enhance facility security by visually inspecting vehicle undercarriages in as little as three seconds. Leveraging AI-driven analytics, it enables security operators to identify explosives, prohibited items, damage, and various other anomalies across various vehicle types. Key capabilities include high-resolution imaging, integrated licence plate recognition, and compatibility with third-party systems, ensuring adaptability for diverse operational needs. The system is ideal for securing high-risk facilities, including critical infrastructure, military installations, border checkpoints, logistics hubs, and much more.
Deep Sentinel, a pioneer in proactive AI-powered security, has announced the launch of their Gen V Hub. The new product delivers stronger, faster and more affordable security by supporting up to 20 cameras for commercial deployments. Intended users include businesses that use multiple cameras for on-premise security, including multifamily residences, businesses prone to break-ins, auto dealerships and hotel properties. Gen V Hub updates The Gen V has a smaller, sleeker design for easy installation and seamless integration Updates to the Gen V Hub include edge-AI computing, full local video processing for faster performance and enhanced privacy, quieter, more power-efficient operation and enhanced thermal management. The Gen V has a smaller, sleeker design for easy installation and seamless integration across commercial environments. For channel partners and enterprise customers, the Gen V Hub delivers superior performance, long-term supply chain stability and room for future AI enhancements in a smaller, power-efficient device. Enhanced security and scalability "With the Gen V Hub, Deep Sentinel took everything that worked about previous generations and leveled it up," said Jack Azbill, President at Varitec Systems, a current Deep Sentinel partner, adding "We can now offer faster response times, smoother installs, and more robust AI coverage — without passing higher costs to our clients." The Gen V Hub boasts features for channel customers that allow scaling without sacrificing performance or price. 10 active streams at launch, improved network configuration and plug-and-play installation make it easy and cost-effective for businesses to protect their properties. "We’ve already started testing the Gen V Hub with our customers, and the results are outstanding," said Mark Reynoso, Managing Partner at Left Coast Electric, Deep Sentinel partner, adding "It’s faster, more efficient, and makes it easier than ever to deliver top-tier protection across larger sites." Gen V Hub with AI integration Deep Sentinel pairs AI cameras with human guards who can actively intervene to prevent crimes "The Gen V Hub amazed us in the development stages, showing we can run 20 cameras at high quality and still have room to release more AI features as technology evolves," said David Selinger, CEO of Deep Sentinel, adding "This extra capacity is especially important as we continue to advance our use and development of cutting-edge AI models, delivering the most effective and cost-effective security available to both business and home owners anywhere." Deep Sentinel pairs AI cameras with human guards who can actively intervene to prevent crimes. When the systems detect suspicious activity, their proprietary AI verifies the threat and instantly alerts a remote guard. The guard issues a warning and takes further action when necessary. Scalable, next-gen protection Across the country, police departments won’t investigate calls from self-monitoring security systems. Deep Sentinel incorporates human monitoring into its process making its alerts credible to emergency responders. Whether securing a multifamily development, hotel or resort, car dealership or high-risk business, the Gen V Hub provides a stable foundation for scalable, next-gen protection and keeps businesses safe.
The Security Industry Association has sent a letter to U.S. Trade Representative - Jamieson Greer and U.S. Secretary of Commerce - Howard Lutnick requesting relief from tariffs for security industry products and asking that the Trump administration formulate a process that allows companies to apply for product-specific exemptions. Security industry – key segment of the U.S. economy The security industry is an important segment of the U.S. economy, contributing over $430 billion The security industry is an important segment of the U.S. economy, contributing over $430 billion in total economic impact and supporting over 2.1 million jobs. Manufacturers and integrators that provide essential life safety and security products to American consumers are being put under enormous strain, as they struggle to adapt to an uncertain and volatile trading environment. Requests made by SIA Not only do these tariffs hurt manufacturers by increasing the cost of key components as they compete globally, but the additional applicability to finished goods will directly increase the cost of essential security products, potentially pricing out integrators and reducing the availability of key products in the United States. SIA is requesting exemptions for imported components of security systems, security cameras, locks and other door hardware and equipment to include: Alarm systems Access control Camera systems Communications equipment and systems Identity management solutions Security-related uncrewed systems Robotics A range of other cutting-edge security solutions SIA’s agenda It is vitally important that the administration provide this relief to the security industry, and SIA will continue to advocate for this exemption to preserve some stability in the current international trading environment for the industry at large. SIA will continue to anonymously survey the industry and measure how tariffs are affecting their manufacturers and integrators, and they encourage them to reach out to their government relations team with any impact statements that they would like to share.


Expert commentary
Retailers now often find themself in a precarious situation. Profit margins are being squeezed by widespread shoplifting: The Council on Criminal Justice reports that between the first half of 2023 and the first half of 2024, shoplifting reports increased by 24%. Meanwhile, the strategies used by shops to deal with this situation are alienating consumers and affecting total sales. Andy Jassy, the CEO of Amazon, stated during an earnings call that customers are now purchasing more pharmaceuticals from Amazon in response to other retailers locking their cabinets. Media reports This crisis impacts not only the large chains—more than 7,100 retail stores were closed in the U.S. in 2024, a 69% increase from the previous year—but also small, local businesses, whose profit margins are even narrower. Media reports out of Los Angeles show that small businesses in regions with greater shoplifting rates are more likely to close, and small business owners' job satisfaction and general well-being are negatively impacted by the fear of crime. How to safeguard staff and inventory Unchecked retail theft demoralises staff and makes the store less attractive to customers This is obviously not a sustainable situation. In addition to lowering revenue, unchecked retail theft demoralises staff and makes the store less attractive to customers. Unfortunately, making customers wait in line to enter a store or locking up toothpaste and deodorant only makes the customer relationship worse. Retailers need to figure out how to safeguard staff and inventory without alienating their customer base—and they need to figure it out fast. Advanced video security A new tool has come to the forefront of this fight: advanced video security. Of course, video surveillance has been used in stores for many years. However, the technology currently being used to reduce retail theft is very different from the outdated analog video systems of the past. With features like cloud-based flexibility and AI-enhanced analytics, this new generation of video surveillance systems has all the advantages of modern technological advancements, while also providing businesses with a competitive edge in the fight against retail theft. Security's new AI video standard Workers are constantly rushing from aisle to aisle in an effort to satisfy eager consumers Although the typical chain pharmacy may appear straightforward to the customer, retailers are aware of how intricate these spaces are. Hundreds or even thousands of shoppers may come and go on any given day, with a larger volume during busy seasons like holidays or special promotional events. It's common for shoppers to pick up merchandise and put it down in another part of the store, often far away from its original location. Meanwhile, workers are constantly rushing from aisle to aisle in an effort to satisfy eager consumers, particularly during these busy seasons. How much can recorded videos reveal in a busy Using traditional CCTV, managers and security teams can monitor some of this activity, but their viewpoint of events will always be incomplete. There is a limit to how much recorded videos can reveal in busy, fast-paced customer situations, and even the largest chain stores lack the staff and resources to continuously sort and evaluate all of the data they collect. When more customers are in the store for a special event, there’s also naturally a higher risk of theft. New generation of video security Using machine learning algorithms trained on large amounts of retail-specific data The new generation of video security aims to provide retailers with comprehensive intelligence that covers all aspects of their operations. Using machine learning algorithms trained on large amounts of retail-specific data, they are focused on predictive actions and can recognise problematic behaviour in real time from raw video footage. AI-powered surveillance For example, if someone entered a store with empty bags but bypassed the cashier and started heading to the exit with a full bag, AI could predict a potential theft before it happens. Instead of just recording the theft, security action could be triggered in the moment. AI-powered surveillance is like an all-seeing security officer, quickly analysing the thousands of variables at play and spotting the warning signs of a possible crime before it happens. This is especially crucial during the holidays and busy shopping periods. Security personnel required to monitor cameras Imagine a chain store with 500 locations and 32 cameras each: that’s 1,600 cameras Cameras with AI can also alert human security personnel of events that would have otherwise been missed. Imagine a chain store with 500 locations and 32 cameras each: that’s 1,600 cameras. Now just imagine the number of security personnel required to monitor all of those cameras – when it comes down to it, traditional security is a numbers game. AI is the differentiator here that will allow retailers to win this game. VSaaS: A new tool to Deter Theft The emergence of Video Surveillance as a Service (VSaaS), a surprisingly under-discussed aspect of the broader SaaS revolution, is an important part of video security’s evolution. VSaaS solutions are especially helpful for chains that require a high level of centralisation and coordination across hundreds or even thousands of locations. In addition to offering action alerts at the shop level, VSaaS offers comprehensive security systems accessible from any location. This gives corporate headquarters access to complete, aggregated insights on all aspects of business operations. Identify the best ways to deploy staff Retail operators are constantly in a state of triage, rushing to identify the best ways to deploy staff This is significant in part because of the importance that social engineering and store layout have in preventing theft. Stores are frequently more busy during specific hours than others, and consumers may congregate in particular areas of the store while others are comparatively empty. Retail operators are constantly in a state of triage, rushing to identify the best ways to deploy staff and organise inventory while accounting for all of these variables. Cloud-based VSaaS solutions Cloud-based VSaaS solutions help streamline this process by eliminating uncertainty, highlighting blind spots and bottlenecks, and informing retailers of what truly works. Another regrettable reality is that employees frequently steal from businesses they work at. Here, too, VSaaS solutions—when combined with sophisticated, integrated access controls—are essential. AI analytics technology Implementation and deployment of VSaaS is also easier and less costly than CCTV Implementation and deployment of VSaaS is also easier and less costly than CCTV. When new AI analytic updates become available, the client software and hardware don’t need to be upgraded, and the onsite technology and cameras also don’t need to be replaced. The AI analytics technology is upgraded in the cloud, enabling faster deployment and implementation of new technology. New VSaaS solutions Theft will always occur at some level; it's just a part of doing business. However, the growth in shoplifting that retailers have experienced in recent years is unacceptable, and if these figures keep rising, the consequences will be disastrous. In a time of dire need for retail, new VSaaS solutions have come to the forefront and are already turning the tide.
In today's rapidly evolving security landscape, facial recognition has become a buzzword that often triggers privacy and data protection concerns. However, many security professionals may not realise that "facial recognition" is an umbrella term encompassing various technologies, each with distinct applications and privacy implications. Let's dive into what these technologies really mean for security system resellers, integrators, and end-users. Facial recognition tech At its core, facial recognition technology re-identifies or verifies individuals based on their facial features, which are used as biometrics. However, not all biometric systems are based on unique identifying features. Some analyse general characteristics like facial hair style or other distinctive marks. Such traits, known as soft biometrics, can aid in identification but aren't unique enough to verify someone's identity uniquely. Personally identifiable information Modern systems incorporate robust safeguards, including data encryption and strict retention policies While facial recognition technology has applications ranging from access control to crime prevention to investigation, its implementation varies widely depending on specific needs. Modern systems incorporate robust safeguards, including data encryption and strict retention policies, to ensure the responsible handling of any personally identifiable information (PII). Understanding key technologies and applications Facial recognition encompasses several distinct technologies, each serving specific purposes. Here's a comprehensive breakdown of these technologies and their real-world applications. Key technologies: Face Verification (1:1): A one-to-one comparison where a person claims an identity (e.g., by showing an ID card), and the system verifies whether the face matches the provided identity. Example: In airports, face verification is used for automated passport control. When a traveler approaches a gate, their face is scanned and compared to the photo stored in the government database. If the face matches, the traveler is allowed through the gate without manual checks. Face Identification (1 to many): A one-to-many comparison, where a face captured by a system is compared to a database of multiple faces and facial features to identify the person. This process is often used in security or surveillance contexts. Example: In the case of a missing child at an airport, a system could scan the faces of all passengers passing through checkpoints and compare them to a photo of the child in a database. If a match is found, it triggers an alert. Face Re-identification (Many to Many): Many-to-many comparisons where multiple faces are compared to multiple other faces. This is typically used to track a person’s movement anonymously across different areas by matching their facial images at different checkpoints, without knowing their identity. Example: In a retail environment, facial re-identification might be used to track how long an anonymous person spends moving from one section of a store to another by re-identifying their face as they enter and leave different camera views. Facial recognition can be used both for real-time and offline applications. Real-Time Facial Recognition: Real-time facial recognition refers to the immediate processing of a live video feed, comparing faces to a database to generate instant alerts when a match is found. Example: At large public events like sports stadiums, real-time facial recognition might be used to detect banned individuals (e.g., known hooligans) as they attempt to enter. Post-Event (Recorded) Facial Recognition: This refers to analysing video recordings after the event has occurred, rather than in real-time. Facial recognition is applied to recorded data to identify or track individuals. Example: After a crime, investigators could use facial recognition software on recorded video from security cameras to identify suspects by matching their faces to known databases. These definitions cover various aspects of facial recognition technology, its different applications, and how biometrics are used for identification and tracking purposes. Biometrics: Biometric technologies use a person’s distinguishing physical characteristics, such as their face, fingerprint, or iris, to identify them. Example: Fingerprint or face scanning for unlocking a phone or using iris recognition for secure entry at high-security buildings like data centers. Hard Biometrics: Hard biometrics refer to physical characteristics that are sufficiently unique enough to be used for identifying a specific individual, such as a face, fingerprint, or iris. Example: Using iris recognition at airport security checkpoints to confirm the identity of a traveler. Soft Biometrics: Soft biometrics (personal features) include general attributes like height or body shape, which are not unique enough to identify a person on their own but can help narrow down re-identification when combined with other information. Example: Using height and body shape to help identify a suspect in a camera scene when facial features alone are unreliable. Appearance Similarity: This refers to distinguishing between people based on their appearance (e.g., clothing, accessories) rather than biometric features. It’s often used for accelerated investigation and statistical analysis rather than identification. Example: A retail store may track customers based on the clothes they are wearing to monitor how long they stay in the store, without tracking their faces or personal details. Liveness Detection: A method used to determine whether the subject in front of a facial recognition system is a live human being and not a photo or a video recording. Example: In some mobile payment systems, facial recognition requires users to blink or move their head slightly to ensure they are a live person and not someone trying to use a photo for authentication. Mathematical Representation: Non-reversible mathematical representations are lists of numbers based on a person's facial image or appearance based on clothing. These numbers represent characteristics but cannot be easily used to recreate the face. Example: When an organisation stores only the mathematical representations from a face rather than an actual image, even if the data is stolen, it is nearly impossible to recreate the person’s face or use the data with another system. Privacy and security considerations Modern facial recognition systems prioritise privacy through various protective measures, moving far beyond the basic security protocols of the past. Solutions integrate multiple layers of protection designed to safeguard personal data while maintaining system effectiveness. These sophisticated privacy controls work in concert to ensure responsible data handling and comply with evolving security standards. Key protective measures include: Biometric template isolation that keeps facial recognition templates separate from other personal data, with dedicated secure storage environments. Template encryption frameworks specifically designed for biometric data, using industry-standard protocols that protect facial features during both processing and storage. Biometric data anonymisation that converts facial features into non-reversible mathematical representations – into numbers - prevents the reconstruction of original face images. Cascading deletion protocols automatically remove both raw facial data and derived biometric templates after their authorised use period. Segmented access controls that separate facial recognition administrative functions (like enrollment and template management) from regular system operation. Privacy standards The key is selecting the right tool for each application and ensuring that personal data is collected The security industry continues to evolve, finding innovative ways to balance effective surveillance with privacy protection. By understanding this comprehensive range of technologies, security professionals can better serve their clients with solutions that address specific needs while maintaining appropriate privacy standards. The key is selecting the right tool for each application and ensuring that personal data is collected only when necessary and protected when it is not. Statistical analysis and pattern recognition The variety of facial recognition applications demonstrates that not all systems require storing personal information. Many modern solutions focus on statistical analysis and pattern recognition rather than individual identification, offering powerful security benefits while respecting privacy concerns. This balance of capability and responsibility represents the future of video security technology.
The artificial intelligence revolution in physical security has arrived, transforming how we protect people, assets, and infrastructure. From smart buildings that automatically adjust access protocols based on real-time threat assessments to healthcare facilities using AI-enhanced video analytics for patient safety, these technologies are reshaping the industry landscape. But with this transformation comes a new era of regulatory oversight that security professionals must navigate carefully. Convergence of AI The convergence of powerful AI capabilities with traditional security systems has created unprecedented opportunities for enhanced protections while simultaneously raising important questions about privacy, transparency, and responsible deployment. As these technologies become more sophisticated, security professionals face the dual challenge of maximising their potential while ensuring compliance with evolving regulatory frameworks. The current state of AI in security systems By combining multiple data streams, AI creates a more comprehensive and intelligent security ecosystem Today's AI-driven security solutions extend far beyond traditional security capabilities. Modern systems can understand complex human behaviours, analyse crowd patterns in transportation hubs, detect early signs of trouble in retail environments, and even predict potential security breaches before they occur. By combining multiple data streams — video feeds, access control systems, audio detection, and various sensors — AI creates a more comprehensive and intelligent security ecosystem. Industrial applications The impact is particularly evident in integrated security operations. In healthcare settings, AI systems can simultaneously monitor patient safety, manage access control, and detect unauthorised entries, all while maintaining strict privacy protocols. In education environments, these technologies help safeguard campuses by identifying unusual behaviour patterns while respecting student privacy rights. Retail operations benefit from AI's ability to not only detect potential theft but also analyse customer flow patterns and identify operational inefficiencies. The technology's capabilities continue to expand through: Advanced anomaly detection that establishes normal activity patterns and flags deviations. Predictive analytics that forecast potential security risks before incidents occur. Natural language interfaces that allow security teams to query video data using voice or text commands. Multimodal analysis combining data from thermal cameras, LIDAR, IoT sensors, and other sources. Integration of multiple data sources Security systems are evolving into predictive platforms that can anticipate and prevent incidents These innovations represent just the beginning of AI's potential impact on security applications. As algorithms become more sophisticated and computing power increases, security systems are evolving into predictive platforms that can anticipate and prevent incidents rather than simply respond to them. The integration of multiple data sources allows for a more nuanced understanding of security situations, enabling more precise and effective responses to potential threats. Emerging regulatory frameworks The rapid advancement of AI capabilities has prompted governments worldwide to develop comprehensive regulatory frameworks. The European Union has taken the lead with its AI Act, categorising AI systems based on their potential risks and establishing strict guidelines for high-risk applications. Focus on safe, secure AI The United States is following suit, with recent executive orders focusing on safe, secure, and trustworthy AI development. These initiatives reflect growing global awareness of the need to balance technological advancement with ethical considerations and human rights protection. These regulations are reshaping how security technology providers approach development and implementation. Responsibility-by-design approach Companies must consider the entire lifecycle of their AI solutions, from initial development The focus has shifted toward a "responsibility-by-design" approach, where privacy protection, data security, and ethical considerations are built into systems from the ground up. This includes robust testing protocols, responsible data practices, and continuous monitoring of AI systems post-deployment. Companies must consider the entire lifecycle of their AI solutions, from initial development through deployment and ongoing operation. Transparency, accountability For security professionals, this regulatory evolution means adapting to new requirements around transparency, accountability, and human oversight. Security teams must document how AI systems make decisions, implement safeguards against bias, and ensure human operators maintain final authority over critical security decisions. The regulations also emphasise the importance of data protection, requiring organisations to implement strict controls over how information is collected, stored, and used within AI-powered security systems. Address challenges of AI The regulatory landscape continues to evolve, with new frameworks emerging that specifically address the unique challenges of AI in security applications. These include requirements for regular system audits, mandatory impact assessments for high-risk deployments, and specific guidelines for handling sensitive personal data in security contexts. Organisations must also develop clear procedures for addressing potential AI system errors or biases, ensuring that corrective measures can be implemented quickly when needed. Preparing for the future The challenge lies in maximising security effectiveness while maintaining transparency and public trust The security industry stands at a crucial junction where innovation meets responsibility. As AI capabilities grow more sophisticated, security professionals must balance the use of these powerful tools while adhering to evolving regulatory requirements. This balance becomes particularly critical in smart city applications, where AI systems might monitor public spaces for safety while respecting individual privacy rights. The challenge lies in maximising security effectiveness while maintaining transparency and public trust. Proactive approach Success in this new landscape requires a proactive approach. Security teams should invest in understanding both the technical capabilities and regulatory implications of their AI systems. This includes developing clear protocols for data handling, establishing robust testing procedures, and implementing continuous monitoring systems that can detect and address potential issues before they become problems. Organisations must also create comprehensive training programs to ensure security personnel understand both the capabilities and limitations of AI-powered systems. Human-in-the-loop approach The human element remains crucial. While AI can process vast amounts of data and identify patterns beyond human capability, security professionals must maintain oversight and final decision-making authority. This "human-in-the-loop" approach ensures that AI serves as a powerful tool for augmenting human judgment rather than replacing it. Training and education become increasingly important as security teams must understand not only how to operate AI-enhanced systems but also how to interpret their outputs and make informed decisions based on AI-generated insights. An ever-evolving environment The integration of emerging technologies like large language models and computer vision will create new opportunities Looking ahead, the security industry will likely see continued evolution in both AI capabilities and regulatory requirements. Future systems may incorporate more advanced predictive capabilities, enhanced natural language processing, and improved ability to understand complex human behaviours. However, these advancements will need to develop within an increasingly structured regulatory framework that prioritises privacy, transparency, and ethical use. The integration of emerging technologies like large language models and computer vision will create new opportunities while also introducing novel regulatory challenges. Physical security transformation The transformation of physical security through AI represents both an opportunity and a responsibility. By embracing responsible innovation practices while maintaining strong ethical standards, security professionals can help shape a future where advanced AI capabilities and regulatory compliance work together to create safer, more secure environments for everyone. Need for security guidelines The key to success lies in viewing regulatory requirements not as obstacles but as guidelines for developing more trustworthy and effective security solutions. As the industry continues to evolve, organisations that prioritise both innovation and compliance will be best positioned to leverage AI's full potential while maintaining public trust and regulatory compliance.
Security beat
For all the emphasis on cloud systems and centralised servers at ISC West, a lot of innovation in security video systems is happening at the edge. New advancements inside video cameras are boosting capabilities at the edge, from advancements in processing power to artificial intelligence (AI) and machine learning (ML) algorithms that can now be deployed directly on the cameras or edge devices. Advancements in AI algorithms The progress of video systems becoming smarter at the edge is driven by the need for real-time insights, lower latency, bandwidth efficiency, enhanced privacy, and improved reliability. Advancements in edge computing hardware and AI algorithms are enabling a range of intelligent video applications across various industries, including physical security. Smarter functionality at the edge is a benefit of new computer systems-on-chips (SoCs) that are driving new heights of performance for today’s cameras. Axis Communications’ ARTPEC-9 Axis Communications’ new ARTPEC-9 SoC offers advanced video compression to reduce bandwidth Axis Communication’s new ARTPEC-9 system-on-chip (SoC) offers advanced video compression to reduce bandwidth and storage needs. With a low bitrate, the SoC helps deliver high-quality imaging with outstanding forensic detail. ARTPEC-9 also offers enhanced deep learning capabilities to allow users to leverage the latest video analytics and accelerate the implementation of AI technology. Axis maintains control over all aspects of the chip’s development to ensure high quality and cybersecurity. Among the benefits of ARTPEC-9 are better AI and deep learning, better image quality, better cybersecurity, and AV1 license-free video compression (see below). Hanwha Vision’s Wisenet 9 Hanwha Vision has launched Wisenet 9, its most advanced AI-powered System on Chip (SoC). Wisenet 9’s enhanced edge AI capabilities increase performance as the volume and complexity of security threats demand real-time, accurate analysis. By elevating edge-device performance, AI empowers systems to quickly analyse vast amounts of video data and discern crucial patterns and anomalies. A key differentiator driving Wisenet 9 is deployment of two Neural Processing Units (NPUs), which improve performance three-fold compared to Wisenet 7, the previous SoC generation. While one NPU handles image processing, the other focuses on object detection and advanced analytics. This dual NPU concept was introduced to ensure video quality and analytics have independent resources, thus preventing one function from impacting the performance of the other. The latest from Ambarella Ambarella is a supplier of edge AI systems-on-chips to multiple video camera manufacturers Off the ISC West trade show floor in a nearby meeting room, semiconductor company Ambarella demonstrated how it will continue to push the envelope of what is possible with generative AI at the edge. Ambarella is a supplier of edge AI systems-on-chips to multiple video camera manufacturers and recently achieved the milestone of 30 million cumulative units shipped. The demonstrations highlight Ambarella’s ability to enable scalable, high-performance reasoning and vision AI applications across its ultra-efficient, edge-inference CVflow 3.0 AI SoC portfolio. The company’s DeepSeek GenAI models run on three different price/performance levels of its SoC portfolio. In addition to advancements in GenAI processing at the edge, Ambarella integrates image processing, encoding and system-level functions into all its AI SoCs. New standard for video encoding: AV1 AV1 compression is a next-generation video coding technology that offers significant improvements in compression efficiency and video quality, especially at lower bitrates. Its royalty-free nature positions it as a crucial codec for the future of internet video. AV1 compression is a next-generation video coding technology. Axis Communication’s ARTPEC-9 chip now supports the AV1 video encoding standard. By embracing this standard, which is new to the physical security market although it was introduced in 2018, Axis sets the stage for AV1 compression to eventually become the industry standard, replacing H.264 and H.265. Network video transmission AV1 is an open-source, license-free coding format designed mainly for efficient network video transmission AV1 is an open-source, license-free coding format designed specifically for efficient network video transmission. It delivers high-quality video at low bitrates, reducing bandwidth consumption and storage costs. The codec was developed by the Alliance for Open Media (AOM), a nonprofit organisation founded in 2015 by Google, Intel, Amazon, Microsoft, Netflix, and Mozilla (among others), to provide open-standard, next-gen video coding technology. AV1 is ideal for cloud solutions—making streaming applications more robust, scalable, and capable of delivering real-time insights. Now the ARTPEC-9 chipset brings these benefits to the surveillance industry, and AV1 is currently supported by AXIS Camera Station. Providers of major video management solutions (VMS) such as Genetec and Milestone will be adding support for AV1, with further developments already underway. More intelligence at the edge Intelligence inside video cameras comes from the processing power and algorithms that enable them to perform tasks beyond simply capturing and recording images. This "intelligence" allows cameras to analyse the video stream in real-time, identify objects, detect events, and make decisions or provide alerts based on what they "see." New and improved SoCs are driving performance improvements at the edge. The increasing power of embedded processors and advancements in AI are continuously expanding the capabilities of intelligent video cameras.
ISC West 2025 in Las Vegas showcased the latest advancements in security technology, offering security professionals a glimpse into the future of the industry. This year's expo highlighted the growing influence of artificial intelligence (AI), cloud computing, and enhanced integration. The pioneering comprehensive and converged security event attracted nearly 29,000 industry professionals to the Venetian Convention Centre. Integration into unified platforms Several companies emphasised the importance of cloud-based solutions and the integration of diverse security components into unified platforms. For example, Brivo's Security Suite provides “everything in one platform” – not just access control. Customers only pay for what they use because the system is flexible and scalable from a single door to enterprise level applications. Brivo’s suite includes video, but the system can also tie in with third-party “partners.” Genetec's Security Centre allows for more frequent updates through the cloud. Milestone is undergoing a two-year transition to bring its Xprotect system into the future by incorporating Arcules and Briefcam into a video-as-a service product. Suprema introduced BioStar X, which integrates access control and video analytics into a single platform. AI and mobile credentials Axis Communications’ Cloud Connect product announced three new partnerships at ISC West 2025 Axis Communications’ Cloud Connect product announced three new partnerships at ISC West – Eagle Eye Networks, SecuriThings, and Wesco. They join the three partners announced during the first year of Axis Cloud Connect – Genetec, Kone (elevators) and Milestone. AI and mobile credentials were still hot topics at ISC West 2025, but the conversation has evolved beyond amazement at the technologies’ capabilities and now centres on more practical aspects. From the theoretical to the practical “AI and mobility are still the ‘flavors de jour,’ but messages are evolving to manifest AI for better outcomes,” says Heather Torrey, General Manager, Commercial Security, Americas, for Honeywell Building Automation. The company has reframed its security portfolio to be very building- and business-focused, continuing to grow and evolve after the recent acquisition of LenelS2. “From the theoretical to the practical, we want customers to be part of the conversation so we can deliver AI that is meaningful to them, focusing on what’s most important,” says Torrey. Under Honeywell’s new ownership structure, “each part of the business can be more focused on customers’ needs,” she says. Honeywell continues its journey around mobile access and credentialing and migrating to cloud solutions. Innovations in Access Control Gallagher’s new Quickswitch access control board simplifies the migration from legacy systems Access control remains a critical component of security systems, and ISC West 2025 showcased several innovations in this area. Acre is releasing “Gallery,” its version of the App Store for access control. DormaKaba is launching the Keyscan KC Series door controller with TCP/IP connectivity and enhanced features. Gallagher’s new Quickswitch access control board simplifies the migration from legacy systems. Johnson Controls highlighted its C-Cure command centre and C-Cure IQ web client, offering a unified approach to access control and video. Hardware integrations for security panels For service provider Alarm.com, hardware products prepare a path to greater customer experiences, says Abe Kinney, Alarm.com’s Director, Product Management, who oversees hardware integrations for security panels, sensors, video, etc., and drives new product development. “We are looking to bridge the physical world to digital world,” he says. “We want to bring an advantage to our dealers that they can bring to customers.” Because Alarm.com’s customers pay a monthly fee, the products must be durable and economical, says Kinney. “It should work with no need for truck rolls.” The importance of longevity and flexibility Products are evaluated based on features, price, and ease of installation Products are evaluated based on features, price, and ease of installation. In particular, longevity is important for the Alarm.com’s pro channel. There is also a growing emphasis on deterrence industrywide. Says Kinney: “We recognise that detection is part of it, but we need to prevent problems from happening in the first place. And the industry is re-evaluating.” When it comes to cloud intelligence, Eagle Eye Networks puts the emphasis on flexibility. They offer AI that can perform anywhere on the system infrastructure, on the camera, on their on-site bridge device, or in the cloud. They support their own AI and also any AI product from a third party. “We focus on what customers want from the data AI detects,” says Hans Kahler, Eagle Eye Networks’ Chief Operating Officer. Integration with other systems A timely alert from gun detection could save a life, but AI can also generate information that might be used and analysed later, such as point-of-sale information, dwell time, foot traffic, etc. “What people want is the ability to work with the data for business intelligence,” says Kahler. Integration with other systems provides new opportunities for customers: For example, a licence plate reader at a restaurant drive-thru could trigger customisation of the menu board digital signage based on the customer’s previous buying pattern. Relentless Innovation Assa Abloy handles more than 40 million SKUs for all its various brands, faked in 28 factories in the US Assa Abloy handles more than 40 million stock keeping units (SKUs) for all its various brands manufactured in 28 factories in the United States. Merely complying with regulations such as the “Buy American Act” is a monumental effort considering the massive product line, attendees heard at Assa Abloy’s Annual ISC West Breakfast focusing on compliance challenges in the security market. Meanwhile, back at the trade show booth, Assa Abloy focused on “relentless innovation” in every corner of its product line. Assa Abloy’s message: Innovation in security does not have to be about AI or automation. In fact, inventive approaches to products come in all shapes and sizes and at every level of the product portfolio, and innovation is happening faster than ever. For example, the Safebolt product from Securitech, a brand recently acquired by Assa Abloy, can quickly lock down existing doors with the press of a red button on a cylindrical or mortise lock. Temporary Systems to Secure Events Securing events is the focus of Allied Universal's Unified Command Solutions, which specialises in setting up temporary security systems for conventions, trade shows, festivals, construction sites, parades, and other events. They can add technology to situations where previously mostly security officers were used, providing safety/security and enabling more efficient event operation. “We can put cameras anywhere, whether they need power or not, use cell service or WiFi, a localised network or the internet, or whatever,” says Andrew LaMadrid, VP, Sales for Allied Universal's Unified Command Solutions. Event operation and management IDIS came to ISC West looking to leverage new products that they did not promote in the past The focus is on easy implementation, flexibility, and fast setup and removal. “We look for a solution to solve each customer’s pain points,” says LaMadrid. They specialise in setting up and deploying surveillance cameras for safety/security and for event operation and management. Mobile surveillance is a relatively new “piece of our puzzle” when it comes to protecting high-profile events. “People are excited about what we can offer that’s new,” says LaMadrid. Unified Command Solutions has been around for about 12 years and was acquired by Allied Universal last summer. IDIS came to ISC West looking to leverage new products that they did not promote in the past, and visitors were very interested in those solutions, says Scott Switzer, IDIS CEO. “The progression of our product line has been tremendous,” he says. Last year, the IDIS booth offered only basic analytics, but this year they had 30 different advanced analytics including gun and aggression detection using the advanced solution “IDIS Vaidio AI.” What Makes You Different? The most common question IDIS hears at their trade show booth is: “What makes you different?” The answer: They offer an end-to-end solution, including cameras; they manage, control, design from end-to-end; and there is no need for multiple integrations. The time needed to install an IDIS system is significantly less because of the simplicity. “We have customers we have supported and grown together for over 20 years,” says Switzer. The company previously deployed IDIS cameras under the Costar brand before the Korean IDIS brand was introduced into the U.S. (IDIS purchased Costar and changed the name to IDIS America.) “This has been a tremendous show for us; we are looking to build our momentum and let more people know about IDIS,” says Switzer. Managing real AI at the edge The depth of their metadata enables new applications, whether for security or business operations Based in Prague, Czech Republic, and with U.S. offices in Pennsylvania, FF Group provides licence plate recognition for harsh environments. Using Axis cameras, they offer “managed real AI at the edge,” selling through a nationwide distributed network, says Alex Osypov, CEO and Founder of FF Group. Markets include parking lots, cities/municipalities, police, government, water systems, etc. The depth of their metadata enables new applications, whether for security or business operations. They are looking to combine and correlate data including LIDAR, RADAR, etc. to exploit the advantages of “data fusion.” Osypov says: “The market is growing because we are involving other adjacent markets.” Unified platforms and advanced tools Several companies are focusing on enhancing security operations centres (SOCs) by providing unified platforms and advanced tools. Axon’s Fusus system “layers” onto existing infrastructure, tying together various sensors into a single interface for real-time monitoring and information sharing. Increasingly, enterprises have invested in a lot of technologies – ac, video, asset trackers – but none of it talks together. Fusus ties all the systems together so that operators no longer have to look at 10 different screens. Rather, there is a “single pane of glass” that shows everything and facilitates sharing of information with law enforcement. Motorola also showcased its Security Operations Centre, which integrates hardware, software, smart sensors, communication radios, and broadband devices to streamline incident management.
Big news on the mergers and acquisitions (M&A) front is closing out 2024, a year in which several shifts changed the face of the physical security manufacturer community. Announced in December, German giant Bosch Group is selling its Building Technologies division’s product business for security and communications technology to the European investment firm Triton. Bosch division selling to Triton The transaction encompasses three business units – Video, Access and Intrusion, and Communication – and thus the entire product business of Bosch Building Technologies that was offered for sale. All 4,300 associates employed in these units at more than 90 locations worldwide will be taken over. The transaction reflects a growing confidence in the security market among private equity companies such as Triton, Becklar, and Volaris. Sharing best practices Acre Security and Bosch will remain independent, standalone companies under Triton’s ownership Acre Security, previously acquired by Triton, has benefited from Triton’s strategic guidance and expertise, according to the company, which is confident Bosch will experience the same level of support and opportunity to thrive. Acre Security and Bosch will remain independent, standalone companies under Triton’s ownership, but will benefit from the potential to collaborate and share best practices as part of the broader Triton portfolio. Resideo acquires Snap One Earlier in 2024, there were other large M&A transactions. In the spring, Resideo Technologies, Inc., a manufacturer and distributor of technology-driven products and solutions, agreed to acquire Snap One Holdings Corp., a provider of smart-living products, services, and software to professional integrators. The transaction is valued at $1.4 billion, inclusive of net debt. Upon closing, Snap One becomes part of Resideo's ADI Global Distribution business. Honeywell buys Carrier’s Access Solutions In late 2023, Honeywell announced plans to enhance and strengthen its building automation capabilities with the acquisition of Carrier Global Corporation’s Global Access Solutions business for $4.95 billion, in an all-cash transaction. The acquisition, which played out through 2024, includes both hardware and software solutions, adding three respected brands to Honeywell’s portfolio with a focus on life safety and digital access solutions. Acquired brands include LenelS2, commercial and enterprise access solutions; Onity electronic locks; and Supra cloud-based electronic real estate lock boxes. Hirsch reemerges as an iconic brand The Identiv sale was originally announced in April, subject to regulatory approval Identiv announced plans to sell its physical security business and assets to Vitaprotech, the security solutions provider that also acquired British manufacturer, TDSI, in 2019. The Identiv sale was originally announced in April, subject to regulatory approval. As a result of the sale, Hirsch, a global security technology pioneer advancing physical security, video intelligence, cybersecurity, and digital identification solutions, announces the relaunch of its iconic brand and strengthened focus on the industry’s most complete high-security, end-to-end platform. Ease of use security solutions The move seeks to reposition Hirsch as the global pioneer in physical security, video intelligence, and identity solutions, protecting everything from small enterprises to critical national infrastructure. With a 43-year-strong foundation in the industry, Hirsch’s mission has always been empowering a secure, connected world, combining government-grade high security with ease of use. Milestone and Arcules unite Effective July 1, 2024, global video technology company Milestone Systems announced its merger with the cloud-based video surveillance solutions provider, Arcules. Both companies are owned by Japanese multinational Canon Inc. Based in Irvine, Calif., Arcules was spun off from Milestone in 2017. The merger brings together Milestone and Arcules’ best-in-class capabilities within video management software (VMS), video analytics, and video surveillance as a service (VSaaS), providing a complete video technology offering. More M&A stories in 2024 In other M&A moves in 2024, cloud-based workforce management software provider Synerion USA Inc. acquired cloud-based video surveillance and access control solutions platform Qumulex Inc. Also, the global pioneer in airspace awareness and security, Dedrone, became part of the public safety and technology company Axon. The acquisition unites two companies with a shared mission to improve public safety and national security by staying ahead of persistent and escalating threats, enabling faster, more effective responses and ultimately protecting more lives in more places.
Case studies
ZeroEyes, the creators of the first AI-based gun detection video analytics platform to earn the full US Department of Homeland Security SAFETY Act Designation, announced that its technology has been deployed at East Hill Synagogue in Englewood, New Jersey, to proactively address gun-related threats. East Hill Synagogue is a 20+ year-old house of worship serving a diverse community of Modern Orthodox Jews, offering Shabbat and holiday prayer services, adult education and family activities. Proactive security measures ZeroEyes is one of multiple solutions in East Hill’s multi-layered security approach ZeroEyes is one of multiple solutions in East Hill’s multi-layered security approach, enabling members to participate in religious activities without fear or distraction. Anti-Semitic attacks have reached new levels in the past 18 months, with the Anti-Defamation League reporting that the U.S. has seen a 200% increase in hate crimes. This concerning fact highlights the need for increased proactive security measures to protect congregants during worship services and other events. Overall security initiative “Jewish law dictates that preserving (saving) life is a top priority, and we take that quite literally at East Hill Synagogue; safety is our top priority,” said Jonathan Blinken, Directory of Security, East Hill Synagogue. “ZeroEyes is one of the most important layers that we have in our overall security initiative. It is an extremely powerful tool to help us protect those that we love, our institutions and everyone that comes to visit them.” Digital security cameras ZeroEyes' AI gun detection and awareness software layers onto existing digital security cameras ZeroEyes' AI gun detection and intelligent situational awareness software layers onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Centre (ZOC), the industry’s only U.S.-based, fully in-house operation centre, which is staffed 24/7/365 by specially trained military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and synagogue staff as quickly as 3 to 5 seconds from detection. ZeroEyes to safeguard from gun-related threats "Every individual has the right to safety in their place of worship, and it’s deeply troubling when violence threatens that sense of peace," said Mike Lahiff, CEO and co-founder of ZeroEyes. "We thank East Hill Synagogue for trusting ZeroEyes to safeguard their congregation from gun-related threats, ensuring their community remains secure and welcoming."
Texas A&M University opened its doors in 1876 as the state's first public institution of higher learning. Now, it’s well known as a research-intensive flagship university dedicated to preparing Aggie pioneers to take on the challenges of the future. Located in the heart of the Houston-Dallas-Austin triangle, Texas A&M's main campus in College Station, Texas, is home to more than 69,000 students. Another 5,200 are at branch campuses. The challenge Staff would write tickets when they saw cars without valid parking receipts or hang tags The growing student and staff population at Texas A&M University led to more cars, bicycles, foot traffic, and bus passengers to manage. Manual processes couldn’t keep up. Issuing and managing physical permits required significant administrative work, and the parking enforcement team relied on foot patrols to walk each parking lot. Staff would write tickets when they saw cars without valid parking receipts or hang tags. It was a slow and cumbersome process, making it difficult to monitor parking lot occupancy to ensure the number of permit holders matches the number of available spots. The solution Efficient parking enforcement: Patrollers use vehicles equipped with AutoVu SharpZ3 cameras to enforce parking and track real-time data on parking lot usage — even during large events. Improved parking permit distribution: Vehicle information is in the system almost immediately after the customer purchases the permit, reducing overhead costs since hang tags don’t have to be printed and distributed. Increased customer satisfaction: Students, faculty, staff, and guests don’t need a hang tag or paper permit. Users can go online and change the plate on their account, and it’s in the system within minutes. “The reduction in time and resources required to enforce parking is notable. A patrol that used to take an hour now takes around 10 minutes. We’re able to reallocate resources in a more efficient way,” said Dell Hamilton, Parking Systems Manager at Texas A&M Results Now, parking enforcement is based on license plate registrations, and the university has eliminated physical permits for the majority of customers. Patrollers use vehicles equipped with AutoVu SharpZ3 cameras to enforce parking and track real-time data on parking lot usage — even during large events. Getting data more quickly also makes it easier to manage the variety of parking restrictions that exist on campus. This includes spaces reserved for specific groups of people, time of day restrictions, and timed parking limits in areas such as the student recreation center. “Going away from paper permits and hang tags was a huge success,” Hamilton said. “Today, the vast majority of permits issued can be validated with ALPR. Users can go online and change the plate on their account, and it’s in the system within minutes. We not only save on printing and shipping costs but also make it easier for the customer to exchange or return their permit.”
ZeroEyes, the creators of the only AI-based gun detection video analytics platform that holds the full U.S. Department of Homeland Security SAFETY Act Designation, announces that its proactive gun detection and intelligent situational awareness solution has been deployed by Berrien Springs Public Schools (BSPS) in Michigan to mitigate gun-related violence. The company and district are also partnering to present ‘Lunch & Learn: Protecting Schools from Active Shooter Events,’ an in-depth safety and security seminar, ZeroEyes demo for surrounding schools, and Q&A to take place May 12th at 11:30 am in the STEM Central Building. Safe learning environment Located in the southwestern corner of the state, BSPS’ main campus sits in the heart of Berrien County and includes six schools: Mars Elementary, Sylvester Elementary, Berrien Springs Middle School, Berrien Springs High School, Virtual Academy, and Discovery Academy. Additionally, beyond its main campus, the district supports 28 additional learning centers statewide through an alternative learning program that helps students earn their high school diploma under the Michigan Merit Curriculum guidelines. The district has implemented ZeroEyes to further strengthen its multilayered security approach Serving approximately 7,000 students and employing 600 staff members in total, BSPS prioritises safety across all its campuses. Each school features secure vestibules and locked entry points, while the main campus is staffed with a dedicated school resource officer (SRO). The district has implemented ZeroEyes to further strengthen its multilayered security approach and ensure a safe learning environment for students and staff statewide. Engaging educational environment “At Berrien Springs Public Schools, student and staff safety are a priority as we continuously improve attendance, achievement, and engagement,” said Superintendent Dr. Thomas Bruce. “Implementing ZeroEyes allows us to take a proactive approach to security, ensuring that students and staff can focus on teaching and learning without distraction. This technology aligns with our commitment to creating an outstanding safe and engaging educational environment.” If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence ZeroEyes' AI gun detection and intelligent situational awareness software layers onto BSPS’ existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Center (ZOC), the industry's only U.S.-based, fully in-house operation center, which is staffed 24/7/365 by military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to first responders and local staff as quickly as 3 to 5 seconds from detection. Secure learning environment According to the incidents analysed by the ZeroEyes Gun Violence Research Center, Michigan has seen more gun-related incidents than the national average in the past 365 days. “We are extremely proud to work with Berrien Springs Public Schools to further protect students and teachers throughout the state of Michigan,” said Mike Lahiff, CEO and co-founder of ZeroEyes. “The district’s dedication to student success is showcased by its unwavering commitment to safety. I applaud their decision to implement proactive measures to create a secure learning environment.”
Omnilert, a pioneer in AI-driven safety solutions and AT&I Systems, announced that Amerant Bank has chosen Omnilert’s AI technology to help bolster the security at all of its locations in Florida. AT&I Systems, a longtime security partner of Amerant Bank, was chosen as the security integrator. Omnilert’s software, which recently received the full SAFETY Act Designation by the U.S. Department of Homeland Security (DHS), will be integrated into more than 160 existing Amerant Bank cameras to provide advanced 24/7 surveillance with automated response capabilities. Key layer of security “Omnilert technology has become a key layer of security that can transform traditional surveillance capabilities and ensure a fast, robust and automatic response in an emergency,” said Dave Fraser, CEO of Omnilert. “With our software running non-stop in the background, Amerant can focus on carrying out their daily business knowing their workers and patrons are being kept safe from harm.” New and innovative ways to enhance the safety “At Amerant Bank, we are always looking for new and innovative ways to enhance the safety of our bank locations, and Omnilert’s AI technology will be an important part of our overall security infrastructure,” said Orlando Gonzalez, Head of Corporate Security at Amerant Bank. “Integrating the software into our existing cameras made the installation quick and seamless, and once installed, it transformed these cameras into powerful, intelligent surveillance devices that are constantly detecting potential threats.”
ZeroEyes, the creators of the first AI-based gun detection video analytics platform to earn the US Department of Homeland Security SAFETY Act Designation, announced that its proactive gun detection and intelligent situational awareness solution has been deployed at Scott County R-IV School District in Benton, Missouri, to mitigate gun-related violence. The deployment was facilitated by Freedom Security, a local security provider serving the greater Missouri Area. Robust security upgrades Located in a rural community near the borders of Illinois and Kentucky, Scott County R-IV School District consists of a single campus with three interconnected buildings serving students from pre-K through 12th grade. The district educates approximately 800 students annually and employs around 125 teachers and administrators. ZeroEyes is the newest addition to the district's robust security upgrades, which include window tints, HAVEN locks, integrations with CrisisGo, and more. Digital security cameras ZeroEyes’ AI gun detection and intelligent situational awareness software layer onto existing cameras ZeroEyes’ AI gun detection and intelligent situational awareness software layer onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Centre (ZOC), the industry’s only U.S.-based, fully in-house operation centre, which is staffed 24/7/365 by specially trained U.S. military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and school administration as quickly as 3 to 5 seconds from detection. ZeroEyes safety strategy “ZeroEyes is not intrusive or invasive, and it does more than just detect; it alerts, responds, and continues to do so throughout any situation involving a potential threat,” said Dr. Bradley Kolwyck, Superintendent of Scott County R-IV School District. “This technology is the final piece we needed to ensure every layer of our safety strategy is connected, enabling us to provide the safest environment possible.” ZeroEyes deployment ZeroEyes and the district are hosting a Lunch & Learn session at 11:00 am at the Scott County ZeroEyes and the district are hosting a Lunch & Learn session at 11:00 am at the Scott County R-IV District Office (4035 State Highway 77, Benton, MO). It will feature demonstrations and discussion sessions, including reflections from school pioneers on the district’s successful ZeroEyes deployment. The event is open to local schools, law enforcement, and media. ZeroEyes’ innovation and protection “I commend Scott County R-IV School District for taking the initiative to lean into innovation and proactively protect its students from gun-related violence,” said Mike Lahiff, CEO and cofounder of ZeroEyes. “ZeroEyes’ ability to provide first responders and law enforcement with advance warning and situational awareness empowers them to act quickly and save lives.”
The Torrance Unified School District is a cornerstone of the Torrance community, dedicated to providing a high-quality education that prepares students for success in college, career, and life. Serving a diverse student population, Torrance USD delivers a comprehensive and enriching educational experience from kindergarten through high school. The school district comprises 17 elementary, eight middle, and five high schools, one continuation high school, and one alternative high school. Vendor solutions Torrance USD had a mashup of different technologies and vendor solutions across its schools Like many school districts, Torrance USD had a mashup of different technologies and vendor solutions across its schools regarding the ability to broadcast announcements and alerts. Each school had separate systems for bells, clocks, and loudspeakers. There was no central management of these systems, and the school district couldn't create pre-recorded messages for emergencies. Many system components were also end-of-life, and maintaining everything was cumbersome at best. Focusing on consolidation for reliability and consistency Torrance USD began planning district-wide communication improvements in 2020, with the overarching goal of deploying one uniform system through all 32 campuses, with one dashboard to manage communications. The school district achieved its goal by deploying Cisco Call Manager coupled with Singlewire’s InformaCast communications software and hundreds of IPX endpoints from AtlasIED. Vetted integration technology partners like Cisco, Singlewire, and AtlasIED ensure that interoperability, reliability, and usability have all been verified and validated through extensive testing. Surveillance cameras for emergency alerting Torrance USD began planning district-wide communication improvements in 2020 “This project was part of a larger strategic plan to secure each campus — improve perimeter security, add surveillance cameras, allow for emergency alerting, consolidate the speaker systems, and standardise the bells,” said Gil Mara, Chief EdTech and Information Services Officer at Torrance USD. “For example, when you went from one campus to another, campuses had different bell sequences for scenarios like lockdowns. So, there was no consistency of the alerting mechanisms, and we wanted to ensure it was consistent across all the schools.” Digital and physical security of K-12 schools District staff contacted Nilkanth Radadia, Senior Account Manager at NIC Partners, to design the desired district-wide communications solution. NIC Partners has over two decades of experience enhancing the digital and physical security of K-12 schools and was well-suited to take on a project of Torrance USD’s scale. Focusing on what’s most important “Many stakeholders were involved in this project,” said Radadia. ”Given the project’s scope and requirements, there were a lot of conversations beforehand to get the district comfortable with understanding how the system would work." "Some key elements were customisability, two-way talk, multicolour visual message capabilities, and ADA compliance for the visual and hearing impaired. When AtlasIED came out with their full LCD screen speaker, that was a game changer.” Feature set and industrial design NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages AtlasIED was chosen as the vendor for the system upgrades after a thorough evaluation of various vendors. Their feature set and industrial design, particularly the full LCD screen speaker, stood out. NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages were audible, visible, and intelligible. WAN or LAN network architecture Leveraging standard WAN or LAN network architecture, each speaker is equipped with an integrated talkback microphone, LCD, and LED flasher, supporting both visual text and audio broadcast to enhance physical security while improving day-to-day communications through advanced alerting, bell schedules, and pre-recorded and scheduled announcements. For example, at 8:30 each morning, the Pledge of Allegiance is broadcast to all schools with a patriotic colour palette appearing on the IPX endpoints. LED blinker “We needed to implement a solution that would serve the needs of all the students, including those with visual or audio impairments,” said Mara. “That's why having the LED blinker and the message crawler was essential. That solved the issues regarding accessibility for our students and staff to ensure they got the message(s) every time.” Network-wide communication For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED. The IP-HVP is a vandal-proof, IP45 weather-resistant, wall-mount IP speaker well-suited for environments where network-wide communication is desired, and high output is required to overcome excessive ambient noise or large spaces. Almost 600 IP-HVP speakers were installed district-wide. Additionally, the Power over Ethernet (PoE+)-enabled IPX endpoints connect through the same IT network the school uses to deliver Internet access. InformaCast mass communications software The platform simplifies the installation process for integrators and reduces the need to introduce multiple cable types to a project. The IPX platform also offers scalability benefits, allowing schools the flexibility to expand their systems as the district’s communications evolve. The IPX Series also helped Torrance USD incorporate new and expanded campus safety capabilities with the help of InformaCast mass communications software. IPX LCD screens Torrance USD is trying out various colour combinations on the IPX LCD screens to indicate alerts Using InformaCast, designated school personnel can initiate an alert from a mobile device wherever they are. The software then sends text messages to faculty, students, and parents' mobile devices, alerts law enforcement, and activates attention-grabbing audio alarms and LCD text messages on the installed IPX devices throughout the school or district. Currently, Torrance USD is trying out various colour combinations on the IPX LCD screens to indicate different kinds of alerts, including earthquakes, shelter-in-place, and all-clear messages. Intentional and phased deployment leads to consistent use NIC Partners started with the smallest school to establish best practices for implementation. Once the first school was completed and future implementation methods documented, NIC Partners went full-on with the remaining schools, working second shift during the school year and completing all the upgrades district-wide in less than five months. The communication system is in the final phase of upgrading all the schools to InformaCast Fusion servers and upgrading Cisco Call Manager to Webex calling. These updates will allow select school and district staff members to make emergency announcements or push out notifications directly from their cell phones. NIC Partners and AtlasIED Staff and students appreciate the audio upgrades, albeit for different reasons. Teachers are relieved by the improved audio clarity, as they can finally hear things “loud and clear,” and emergency alerts include visual messaging. Students love the music played at the end of each period to indicate a class transition. “Before the upgrades, you couldn't make a good page,” said Mara. “Now, the audio clarity is way better. We’re delighted with the IPX products and even happier to have NIC Partners and AtlasIED as our partners for such a huge undertaking. We wouldn't have been successful without their help.”
ZeroEyes, the creators of the first AI-based gun detection video analytics platform to earn the full US Department of Homeland Security SAFETY Act Designation, announced that its technology has been deployed at East Hill Synagogue in Englewood, New Jersey, to proactively address gun-related threats. East Hill Synagogue is a 20+ year-old house of worship serving a diverse community of Modern Orthodox Jews, offering Shabbat and holiday prayer services, adult education and family activities. Proactive security measures ZeroEyes is one of multiple solutions in East Hill’s multi-layered security approach ZeroEyes is one of multiple solutions in East Hill’s multi-layered security approach, enabling members to participate in religious activities without fear or distraction. Anti-Semitic attacks have reached new levels in the past 18 months, with the Anti-Defamation League reporting that the U.S. has seen a 200% increase in hate crimes. This concerning fact highlights the need for increased proactive security measures to protect congregants during worship services and other events. Overall security initiative “Jewish law dictates that preserving (saving) life is a top priority, and we take that quite literally at East Hill Synagogue; safety is our top priority,” said Jonathan Blinken, Directory of Security, East Hill Synagogue. “ZeroEyes is one of the most important layers that we have in our overall security initiative. It is an extremely powerful tool to help us protect those that we love, our institutions and everyone that comes to visit them.” Digital security cameras ZeroEyes' AI gun detection and awareness software layers onto existing digital security cameras ZeroEyes' AI gun detection and intelligent situational awareness software layers onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Centre (ZOC), the industry’s only U.S.-based, fully in-house operation centre, which is staffed 24/7/365 by specially trained military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and synagogue staff as quickly as 3 to 5 seconds from detection. ZeroEyes to safeguard from gun-related threats "Every individual has the right to safety in their place of worship, and it’s deeply troubling when violence threatens that sense of peace," said Mike Lahiff, CEO and co-founder of ZeroEyes. "We thank East Hill Synagogue for trusting ZeroEyes to safeguard their congregation from gun-related threats, ensuring their community remains secure and welcoming."
Texas A&M University opened its doors in 1876 as the state's first public institution of higher learning. Now, it’s well known as a research-intensive flagship university dedicated to preparing Aggie pioneers to take on the challenges of the future. Located in the heart of the Houston-Dallas-Austin triangle, Texas A&M's main campus in College Station, Texas, is home to more than 69,000 students. Another 5,200 are at branch campuses. The challenge Staff would write tickets when they saw cars without valid parking receipts or hang tags The growing student and staff population at Texas A&M University led to more cars, bicycles, foot traffic, and bus passengers to manage. Manual processes couldn’t keep up. Issuing and managing physical permits required significant administrative work, and the parking enforcement team relied on foot patrols to walk each parking lot. Staff would write tickets when they saw cars without valid parking receipts or hang tags. It was a slow and cumbersome process, making it difficult to monitor parking lot occupancy to ensure the number of permit holders matches the number of available spots. The solution Efficient parking enforcement: Patrollers use vehicles equipped with AutoVu SharpZ3 cameras to enforce parking and track real-time data on parking lot usage — even during large events. Improved parking permit distribution: Vehicle information is in the system almost immediately after the customer purchases the permit, reducing overhead costs since hang tags don’t have to be printed and distributed. Increased customer satisfaction: Students, faculty, staff, and guests don’t need a hang tag or paper permit. Users can go online and change the plate on their account, and it’s in the system within minutes. “The reduction in time and resources required to enforce parking is notable. A patrol that used to take an hour now takes around 10 minutes. We’re able to reallocate resources in a more efficient way,” said Dell Hamilton, Parking Systems Manager at Texas A&M Results Now, parking enforcement is based on license plate registrations, and the university has eliminated physical permits for the majority of customers. Patrollers use vehicles equipped with AutoVu SharpZ3 cameras to enforce parking and track real-time data on parking lot usage — even during large events. Getting data more quickly also makes it easier to manage the variety of parking restrictions that exist on campus. This includes spaces reserved for specific groups of people, time of day restrictions, and timed parking limits in areas such as the student recreation center. “Going away from paper permits and hang tags was a huge success,” Hamilton said. “Today, the vast majority of permits issued can be validated with ALPR. Users can go online and change the plate on their account, and it’s in the system within minutes. We not only save on printing and shipping costs but also make it easier for the customer to exchange or return their permit.”
ZeroEyes, the creators of the only AI-based gun detection video analytics platform that holds the full U.S. Department of Homeland Security SAFETY Act Designation, announces that its proactive gun detection and intelligent situational awareness solution has been deployed by Berrien Springs Public Schools (BSPS) in Michigan to mitigate gun-related violence. The company and district are also partnering to present ‘Lunch & Learn: Protecting Schools from Active Shooter Events,’ an in-depth safety and security seminar, ZeroEyes demo for surrounding schools, and Q&A to take place May 12th at 11:30 am in the STEM Central Building. Safe learning environment Located in the southwestern corner of the state, BSPS’ main campus sits in the heart of Berrien County and includes six schools: Mars Elementary, Sylvester Elementary, Berrien Springs Middle School, Berrien Springs High School, Virtual Academy, and Discovery Academy. Additionally, beyond its main campus, the district supports 28 additional learning centers statewide through an alternative learning program that helps students earn their high school diploma under the Michigan Merit Curriculum guidelines. The district has implemented ZeroEyes to further strengthen its multilayered security approach Serving approximately 7,000 students and employing 600 staff members in total, BSPS prioritises safety across all its campuses. Each school features secure vestibules and locked entry points, while the main campus is staffed with a dedicated school resource officer (SRO). The district has implemented ZeroEyes to further strengthen its multilayered security approach and ensure a safe learning environment for students and staff statewide. Engaging educational environment “At Berrien Springs Public Schools, student and staff safety are a priority as we continuously improve attendance, achievement, and engagement,” said Superintendent Dr. Thomas Bruce. “Implementing ZeroEyes allows us to take a proactive approach to security, ensuring that students and staff can focus on teaching and learning without distraction. This technology aligns with our commitment to creating an outstanding safe and engaging educational environment.” If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence ZeroEyes' AI gun detection and intelligent situational awareness software layers onto BSPS’ existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Center (ZOC), the industry's only U.S.-based, fully in-house operation center, which is staffed 24/7/365 by military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to first responders and local staff as quickly as 3 to 5 seconds from detection. Secure learning environment According to the incidents analysed by the ZeroEyes Gun Violence Research Center, Michigan has seen more gun-related incidents than the national average in the past 365 days. “We are extremely proud to work with Berrien Springs Public Schools to further protect students and teachers throughout the state of Michigan,” said Mike Lahiff, CEO and co-founder of ZeroEyes. “The district’s dedication to student success is showcased by its unwavering commitment to safety. I applaud their decision to implement proactive measures to create a secure learning environment.”
Omnilert, a pioneer in AI-driven safety solutions and AT&I Systems, announced that Amerant Bank has chosen Omnilert’s AI technology to help bolster the security at all of its locations in Florida. AT&I Systems, a longtime security partner of Amerant Bank, was chosen as the security integrator. Omnilert’s software, which recently received the full SAFETY Act Designation by the U.S. Department of Homeland Security (DHS), will be integrated into more than 160 existing Amerant Bank cameras to provide advanced 24/7 surveillance with automated response capabilities. Key layer of security “Omnilert technology has become a key layer of security that can transform traditional surveillance capabilities and ensure a fast, robust and automatic response in an emergency,” said Dave Fraser, CEO of Omnilert. “With our software running non-stop in the background, Amerant can focus on carrying out their daily business knowing their workers and patrons are being kept safe from harm.” New and innovative ways to enhance the safety “At Amerant Bank, we are always looking for new and innovative ways to enhance the safety of our bank locations, and Omnilert’s AI technology will be an important part of our overall security infrastructure,” said Orlando Gonzalez, Head of Corporate Security at Amerant Bank. “Integrating the software into our existing cameras made the installation quick and seamless, and once installed, it transformed these cameras into powerful, intelligent surveillance devices that are constantly detecting potential threats.”
ZeroEyes, the creators of the first AI-based gun detection video analytics platform to earn the US Department of Homeland Security SAFETY Act Designation, announced that its proactive gun detection and intelligent situational awareness solution has been deployed at Scott County R-IV School District in Benton, Missouri, to mitigate gun-related violence. The deployment was facilitated by Freedom Security, a local security provider serving the greater Missouri Area. Robust security upgrades Located in a rural community near the borders of Illinois and Kentucky, Scott County R-IV School District consists of a single campus with three interconnected buildings serving students from pre-K through 12th grade. The district educates approximately 800 students annually and employs around 125 teachers and administrators. ZeroEyes is the newest addition to the district's robust security upgrades, which include window tints, HAVEN locks, integrations with CrisisGo, and more. Digital security cameras ZeroEyes’ AI gun detection and intelligent situational awareness software layer onto existing cameras ZeroEyes’ AI gun detection and intelligent situational awareness software layer onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Centre (ZOC), the industry’s only U.S.-based, fully in-house operation centre, which is staffed 24/7/365 by specially trained U.S. military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and school administration as quickly as 3 to 5 seconds from detection. ZeroEyes safety strategy “ZeroEyes is not intrusive or invasive, and it does more than just detect; it alerts, responds, and continues to do so throughout any situation involving a potential threat,” said Dr. Bradley Kolwyck, Superintendent of Scott County R-IV School District. “This technology is the final piece we needed to ensure every layer of our safety strategy is connected, enabling us to provide the safest environment possible.” ZeroEyes deployment ZeroEyes and the district are hosting a Lunch & Learn session at 11:00 am at the Scott County ZeroEyes and the district are hosting a Lunch & Learn session at 11:00 am at the Scott County R-IV District Office (4035 State Highway 77, Benton, MO). It will feature demonstrations and discussion sessions, including reflections from school pioneers on the district’s successful ZeroEyes deployment. The event is open to local schools, law enforcement, and media. ZeroEyes’ innovation and protection “I commend Scott County R-IV School District for taking the initiative to lean into innovation and proactively protect its students from gun-related violence,” said Mike Lahiff, CEO and cofounder of ZeroEyes. “ZeroEyes’ ability to provide first responders and law enforcement with advance warning and situational awareness empowers them to act quickly and save lives.”
The Torrance Unified School District is a cornerstone of the Torrance community, dedicated to providing a high-quality education that prepares students for success in college, career, and life. Serving a diverse student population, Torrance USD delivers a comprehensive and enriching educational experience from kindergarten through high school. The school district comprises 17 elementary, eight middle, and five high schools, one continuation high school, and one alternative high school. Vendor solutions Torrance USD had a mashup of different technologies and vendor solutions across its schools Like many school districts, Torrance USD had a mashup of different technologies and vendor solutions across its schools regarding the ability to broadcast announcements and alerts. Each school had separate systems for bells, clocks, and loudspeakers. There was no central management of these systems, and the school district couldn't create pre-recorded messages for emergencies. Many system components were also end-of-life, and maintaining everything was cumbersome at best. Focusing on consolidation for reliability and consistency Torrance USD began planning district-wide communication improvements in 2020, with the overarching goal of deploying one uniform system through all 32 campuses, with one dashboard to manage communications. The school district achieved its goal by deploying Cisco Call Manager coupled with Singlewire’s InformaCast communications software and hundreds of IPX endpoints from AtlasIED. Vetted integration technology partners like Cisco, Singlewire, and AtlasIED ensure that interoperability, reliability, and usability have all been verified and validated through extensive testing. Surveillance cameras for emergency alerting Torrance USD began planning district-wide communication improvements in 2020 “This project was part of a larger strategic plan to secure each campus — improve perimeter security, add surveillance cameras, allow for emergency alerting, consolidate the speaker systems, and standardise the bells,” said Gil Mara, Chief EdTech and Information Services Officer at Torrance USD. “For example, when you went from one campus to another, campuses had different bell sequences for scenarios like lockdowns. So, there was no consistency of the alerting mechanisms, and we wanted to ensure it was consistent across all the schools.” Digital and physical security of K-12 schools District staff contacted Nilkanth Radadia, Senior Account Manager at NIC Partners, to design the desired district-wide communications solution. NIC Partners has over two decades of experience enhancing the digital and physical security of K-12 schools and was well-suited to take on a project of Torrance USD’s scale. Focusing on what’s most important “Many stakeholders were involved in this project,” said Radadia. ”Given the project’s scope and requirements, there were a lot of conversations beforehand to get the district comfortable with understanding how the system would work." "Some key elements were customisability, two-way talk, multicolour visual message capabilities, and ADA compliance for the visual and hearing impaired. When AtlasIED came out with their full LCD screen speaker, that was a game changer.” Feature set and industrial design NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages AtlasIED was chosen as the vendor for the system upgrades after a thorough evaluation of various vendors. Their feature set and industrial design, particularly the full LCD screen speaker, stood out. NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages were audible, visible, and intelligible. WAN or LAN network architecture Leveraging standard WAN or LAN network architecture, each speaker is equipped with an integrated talkback microphone, LCD, and LED flasher, supporting both visual text and audio broadcast to enhance physical security while improving day-to-day communications through advanced alerting, bell schedules, and pre-recorded and scheduled announcements. For example, at 8:30 each morning, the Pledge of Allegiance is broadcast to all schools with a patriotic colour palette appearing on the IPX endpoints. LED blinker “We needed to implement a solution that would serve the needs of all the students, including those with visual or audio impairments,” said Mara. “That's why having the LED blinker and the message crawler was essential. That solved the issues regarding accessibility for our students and staff to ensure they got the message(s) every time.” Network-wide communication For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED. The IP-HVP is a vandal-proof, IP45 weather-resistant, wall-mount IP speaker well-suited for environments where network-wide communication is desired, and high output is required to overcome excessive ambient noise or large spaces. Almost 600 IP-HVP speakers were installed district-wide. Additionally, the Power over Ethernet (PoE+)-enabled IPX endpoints connect through the same IT network the school uses to deliver Internet access. InformaCast mass communications software The platform simplifies the installation process for integrators and reduces the need to introduce multiple cable types to a project. The IPX platform also offers scalability benefits, allowing schools the flexibility to expand their systems as the district’s communications evolve. The IPX Series also helped Torrance USD incorporate new and expanded campus safety capabilities with the help of InformaCast mass communications software. IPX LCD screens Torrance USD is trying out various colour combinations on the IPX LCD screens to indicate alerts Using InformaCast, designated school personnel can initiate an alert from a mobile device wherever they are. The software then sends text messages to faculty, students, and parents' mobile devices, alerts law enforcement, and activates attention-grabbing audio alarms and LCD text messages on the installed IPX devices throughout the school or district. Currently, Torrance USD is trying out various colour combinations on the IPX LCD screens to indicate different kinds of alerts, including earthquakes, shelter-in-place, and all-clear messages. Intentional and phased deployment leads to consistent use NIC Partners started with the smallest school to establish best practices for implementation. Once the first school was completed and future implementation methods documented, NIC Partners went full-on with the remaining schools, working second shift during the school year and completing all the upgrades district-wide in less than five months. The communication system is in the final phase of upgrading all the schools to InformaCast Fusion servers and upgrading Cisco Call Manager to Webex calling. These updates will allow select school and district staff members to make emergency announcements or push out notifications directly from their cell phones. NIC Partners and AtlasIED Staff and students appreciate the audio upgrades, albeit for different reasons. Teachers are relieved by the improved audio clarity, as they can finally hear things “loud and clear,” and emergency alerts include visual messaging. Students love the music played at the end of each period to indicate a class transition. “Before the upgrades, you couldn't make a good page,” said Mara. “Now, the audio clarity is way better. We’re delighted with the IPX products and even happier to have NIC Partners and AtlasIED as our partners for such a huge undertaking. We wouldn't have been successful without their help.”


Round table discussion
Direct costs such as purchase price and maintenance are important elements in the total cost of ownership (TCO). However, there are others. Elements such as opportunity costs of lost revenue or hidden costs of energy consumption and environmental consequences can also impact the measure of TCO. Costs of training, integration, support, and scalability can also be examined. Considering the security industry impact of TCO, we asked this week's Expert Panel Roundtable: How does/should total cost of ownership (TCO) impact the decision-making process when choosing technologies for security?
When it comes to preventing theft and ensuring overall safety, technology offers a robust toolkit for retail stores to enhance security in several ways. From intelligent surveillance systems to RFID tags used to avoid shoplifting, today’s retail and loss prevention strategies are more effective than ever. Beyond security, the newer technologies can also provide benefits related to merchandising, inventory control, customer service, and the list goes on. The combination of abundant data and artificial intelligence (AI) is a powerful one-two punch that is on the verge of reshaping the retail industry. We asked this week's Expert Panel Roundtable: How are new technologies transforming the retail and loss prevention markets?
Video surveillance has been a dominant factor in the casino market since the 1950s when video replaced the use of elevated walkways that allowed casino security personnel to monitor the gaming floor from above. As technology continues to evolve, we can expect to see more innovative uses of video in the casino market. Beyond video, other technologies are also transforming the casino experience. We asked this week’s Expert Panel Roundtable: How are new technologies impacting the casino surveillance and security market?
Products


White papers

Video surveillance as a service: Why are video management systems migrating to the Cloud?
Download
11 reasons video surveillance is moving to the cloud
Download
How security systems ensure healthy workplaces during COVID and after
Download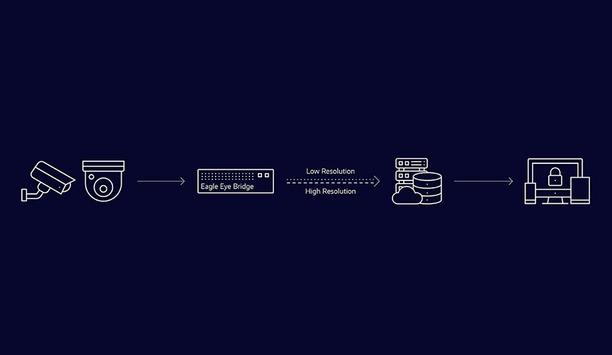
Best practices guide: analogue video to cloud
Download
The inevitability of The Cloud
Download
5 ways to strengthen physical security with an integrated system
Download
Video technology: making cities safer & improving lives
Download
Empowering cameras with AI
Download
Protecting dormitory residents and assets
Download
Choosing the right storage technology for video surveillance
Download
Video surveillance as a service: Why are video management systems migrating to the Cloud?
Download
11 reasons video surveillance is moving to the cloud
Download
How security systems ensure healthy workplaces during COVID and after
Download
Best practices guide: analogue video to cloud
Download
The inevitability of The Cloud
Download
5 ways to strengthen physical security with an integrated system
Download
Video technology: making cities safer & improving lives
Download
Empowering cameras with AI
Download
Protecting dormitory residents and assets
Download
Choosing the right storage technology for video surveillance
Download

Videos
Covert Surveillance: Manufacturers & Suppliers
- Hikvision Covert Surveillance
- Dahua Technology Covert Surveillance
- Hanwha Vision Covert Surveillance
- Verkada Covert Surveillance
- Milesight Covert Surveillance
- Axis Communications Covert Surveillance
- Avigilon Covert Surveillance
- LILIN Covert Surveillance
- Illustra Covert Surveillance
- MOBOTIX Covert Surveillance
- Speco Technologies Covert Surveillance
- Raytec Covert Surveillance
- Honeywell Security Covert Surveillance
- AV Costar Covert Surveillance
- Videotec Covert Surveillance
- Milestone Covert Surveillance
- DNAKE Covert Surveillance
- exacqVision Covert Surveillance
- Anviz Covert Surveillance

The ultimate guide to mastering key control
Download
Using artificial intelligence (AI) to automate physical security systems
Download
A modern guide to data loss prevention
Download
7 proven solutions for law enforcement key control and asset management
Download
The truth behind 9 mobile access myths
Download

















































