Covert cameras
AlarMax Distributors, Inc., a national pioneer in security and surveillance distribution, announces the appointment of Barbara Ann Perkes as Sales Manager – Strategic Accounts. With over a decade of expertise in low voltage and autonomous security technologies, Perkes brings a powerful mix of business insight, customer-first thinking, and transformational leadership to the AlarMax team. Barbara leadership roles A visionary sales and marketing executive, Barbara has built her career on...
Smiths Detection, a pioneer in threat detection and security screening technologies, and a business of Smiths Group plc, announces it is to supply SDX 6040 X-ray inspection systems to a number of major cruise lines. With thousands of people and large quantities of cargo coming onboard, screening systems are vital in helping detect weapons, explosives, drugs, and other prohibited items hidden in luggage or supplies. SDX 6040’s portable and flexible design SDX 6040’s portable and fl...
MOBOTIX consolidates its position as a pioneering provider of innovative fire protection technologies: MOBOTIX thermographic cameras have again received the “Technical Evaluation of Suitability” (Evaluación Técnica de Idoneidad). The certification according to the strict requirements of the Spanish Fire Protection Systems Regulation (Reglamento de Instalaciones de Protección Contra Incendios/RIPCI) was issued by Applus, a certification body recognised by the Sp...
LOOKOUT, a pioneering provider of marine AI systems for safety, announced the expansion of its product line by introducing a new camera featuring an integrated navigation light. This new camera system offers enhanced safety and greater installation flexibility and is available in LOOKOUT's classic blue and white, matte black with carbon accents and custom colours by request, to complement a wider range of vessel designs. Advanced AI vision cameras LOOKOUT has solved a common installation dile...
ADI | Snap One is demonstrating its expansive portfolio at ISC West 2025 from April 2 – 4, at The Venetian Expo in Las Vegas, Nevada, USA. In Booth #12043, visitors can explore an assortment of technologies and solutions across multiple product categories, including security, video surveillance, automation, power, networking, remote management, data communications, fire and life safety, smart living, and more. ADI | Snap One exhibits at ISC West 2025 “As a combined business,...
ZeroEyes, the creators of the first AI-based gun detection video analytics platform to earn the full U.S. Department of Homeland Security SAFETY Act Designation. Has announced that its gun detection and intelligent situational awareness platform has been deployed at Calhan School District (CSD) in Calhan, Colorado. The proactive security technology has been integrated to protect students, staff and visitors at all of the district’s schools. Proactive threat detection The ZeroEyes Gun Vi...
News
FLIR, a Teledyne Technologies company, is set to showcase its maintenance portfolio at Maintenance NEXT from April 8 to 10 in Rotterdam. FLIR Si1-LD acoustic camera FLIR’s main highlight at Maintenance NEXT will be the new Si1-LD industrial acoustic imaging camera, which brings faster and more accurate compressed air leak detection to those operating on a limited condition monitoring budget. Si1-LD offers improved detection and quantification capabilities in comparison with the existing FLIR Si124-LD Plus, along with a higher upper limit frequency range. Leveraging the advantages of ultrasonic technology, the new FLIR Si1-LD pinpoints leaks with enhanced imaging sensitivity at an affordable price. FLIR products In addition to the Si1-LD, FLIR will also showcase the following products: FLIR E8 Pro: The FLIR E8 Pro is the must-have tool for locating and diagnosing electrical, mechanical, and building problems. FLIR T530-14°: The FLIR T530 thermal camera has the features professionals need to accurately troubleshoot hot spots and potential faults. With the 180° rotating lens platform and a bright 4" LCD, the FLIR T530 is engineered to help users diagnose hard-to-reach components in any environment. 80° Wide-Angle Thermal Lens: The FLIR 80° lens is designed to enable maintenance managers, engineers, and mechanical technicians to keep an eye on assets in a large target area for continuous monitoring, condition monitoring, and early intervention of developing faults. FlexView® Dual FOV IR Lens (42°/24°): The FlexView 42°/24° lens is ideal for inspecting large targets, while providing excellent image understanding without sacrificing standard target image quality. FLIR IRP-1: The FLIR IRP-1 port helps to improve worker safety and electrical inspection efficiency—all while reducing the installation costs associated with using thermal cameras to inspect indoor electrical cabinets. FLIR ONE® Edge Pro: This thermal camera for smartphones allows them to take crisp thermal images from any angle. Improved battery time and ruggedness makes sure the camera is ready to use in more industrial environments. FLIR C5: With the FLIR C5 in the pocket they’ll be ready anytime to find hot fuses, air leaks, plumbing issues, and more. FLIR Cx5: The FLIR Cx5 is certified for use in many explosive environments, eliminating the need to acquire hot work permits due to gas, vapour, and dust, while making T-Class surveys quick and easy. FLIR Si2-Pro: The FLIR Si2-Pro helps to significantly lower costs associated with mechanical bearing issues and partial discharge on electrical equipment. Visit FLIR at Maintenance NEXT, booth number 5.005, from April 8 to 10 in Rotterdam.
FLIR, pioneer in high-performance marine thermal-imaging systems, announced the launch of the new FLIR JCU-4 remote control, offering precision camera control and an elevated, yet simplified user experience. Providing confident control of FLIR marine thermal and visible cameras, the FLIR JCU-4 remote control is designed for FLIR marine cameras and is compatible with the M232, M300, M400/M400XR and M500 series, as well as legacy models. It offers pan, tilt, and zoom capabilities, and control of all additional camera functions with an ergonomic keypad and responsive joystick control. Camera operation and easy access The JCU-4 is a meaningful upgrade for those who actively navigate using thermal technology Designed by mariners, for mariners, the JCU-4 is a meaningful upgrade for those who actively navigate using thermal technology and require dependable and intuitive control of their FLIR camera. The rugged, low-profile three-axis joystick is mounted with a 2.9-inch colour LCD and keypad, to simplify camera operation and offer easy access to the joystick setup menus. A dimmable colour LCD and back-lit keypad preserves the operator’s vision during nighttime operations. User-defined camera functions The JCU-4 can be easily configured with intuitive pairing between FLIR marine cameras and marine monitors or chartplotters. Three custom keys can be pre-programmed for quick access to the most used user-defined camera functions. The FLIR JCU-4 is available for $1,699 USD.
Zenitel, a global pioneer in Unified Critical Communication solutions, is launching two new innovations for mixed-use building communication solutions: the Zenitel Display Door intercom (ZDD-1) and the Zenitel Slim Door intercom (ZSD-1). This launch further strengthens Zenitel’s position as a market leader in audio communication solutions. Amazing sound, effortlessly integrated New door entry intercoms are engineered from the ground up, offering a premium audio experience With 125 years of experience in sound design, these new door entry intercoms are engineered from the ground up, offering a premium audio experience in a sleek design that seamlessly blends into any building. With ONVIF compatibility, they seamlessly integrate with surveillance systems, providing an additional layer of security for effective identification and entry control. “Door entry intercoms are an essential part of overall building security, and there are plenty of options available on the market. However, we had a different vision for ours – to uniquely enhance our customer experience and continue elevating audio quality, which is the cornerstone for Zenitel,” said Lars Paulsson, EVP for Safety and Security at Zenitel. "The combination of high-quality hardware, advanced software-driven audio processing, and precision engineering makes our new door entry intercoms the most realistic-sounding intercom on the market.” Zenitel display door Built on Zenitel’s industry-leading sound technology, the Zenitel Display Door intercom features a speaker and microphone array to deliver an immersive sound experience, while high sound pressure levels make it ideal even for high-noise environments. The bi-directional video communication enables face-to-face interaction, fostering a sense of connection, while also supporting the needs of sign language users. The Zenitel Display Door (ZDD-1) features an intuitive touch display with an easy-to-use UI/UX, making navigation simple and efficient for all users. Zenitel slim door The Zenitel Slim Door (ZSD-1) is a compact yet powerful, outdoor-ready intercom that delivers premium sound in a sleek design, with easy installation in tight spaces, including door frames. The intuitive design of this intercom offers visual and aural feedback to ensure ease of use for all users. Unified communication As organizations seek to secure assets and streamline operations through technology, Zenitel’s latest innovations in door entry communications, combined with Zenitel Connect Pro — the industry's first Unified Critical Communication Platform — pave the way for unifying communication needs under a single platform for building owners. Additionally, built-in cybersecurity features of these intercoms ensure secure and encrypted communication at the door.
The future of security requires smarter, more efficient and secure solutions, and Hanwha Vision is helping to drive this transformation with the launch of its most advanced AI-powered System on a Chip (SoC), Wisenet 9. After nearly four years of extensive research and testing, Wisenet 9’s advanced features help elevate our cameras into an AI-driven era, setting a new standard for performance, accuracy, and security. Unmatched clarity “With Wisenet 9, you can count on the superior image quality that delivers the best possible video in the toughest environments, as well as the accuracy of the AI-generated data, whether statistical or event-driven,” states John Lutz Boorman, Head of Product and Marketing at Hanwha Vision Europe. AI revolution at the Edge Wisenet 9’s enhanced edge AI capabilities are essential in this innovation era, where the volume and complexity of security threats demand real-time, accurate analysis. By elevating edge-device performance, AI empowers systems to quickly analyse vast amounts of video data and discern crucial patterns and anomalies. A key differentiator driving this transformation is the two Neural Processing Units (NPUs), which have improved inference performance three-fold compared to Wisenet 7, the previous SoC generation. While one NPU handles image processing, the other focuses on object detection and advanced analytics. This dual NPU concept was introduced to ensure video quality and analytics have independent resources, preventing one function from impacting the performance of the other. Unveiling hidden details Wisenet 9 uses AI to analyse visual data with greater precision. By leveraging a powerful NPU, the system moves past traditional image processing to extract critical information, unlocking previously unseen details with remarkable clarity in tough environments. This enhanced visual intelligence is achieved through a suite of sophisticated AI features, including AI-based extreme Wide Dynamic Range, AI-powered noise reduction, alongside image enhancements. Combined, these technologies deliver exceptional clarity, even under the most challenging conditions. The AI-driven image enhancement, powered by an independent NPU, ensures that every detail, no matter how subtle, is captured and analysed. AI efficiency redefined The H.265 codec provides high video quality with optimised bandwidth AI is powerful, but it can also be resource-intensive. Wisenet 9 flips that script. It’s not just smart, it’s efficient - optimising every aspect of its operation.By intelligently reducing noise, Wisenet 9 achieves a remarkable level of efficiency in data volume reduction, resulting in significantly reduced bandwidth consumption and storage requirements. This core efficiency is further bolstered by the latest H.265 compression technology. The H.265 codec provides high video quality with optimised bandwidth, ensuring reliable, real-time video processing and transmission - critical for uninterrupted 24/7 security. Furthermore, this optimised H.265 support enables consistently high performance in demanding environments, essential for system stability, and streamlines data management in cloud environments, efficiently controlling storage and transfer costs. Seamless integration Wisenet 9’s H.265 codec, aligned with current industry standards and ONVIF profiles, ensures broad hardware compatibility and seamless integration with your existing security infrastructure and provides a dependable foundation for long-term system reliability. Beyond this, Wisenet 9 leverages AI for advanced analytics. Its enhanced AI technology provides detailed attribute analysis, including colour, bag, face mask, glasses, age, and gender, along with other key analytics like people and vehicle counting, slip and fall detection, crowd detection, heatmap, queue management, and more, enabling faster and more informed decision-making. Smart surveillance tech To further amplify its capabilities, Wisenet 9 incorporates several key technologies that power the next generation of efficiency, including: Re-Identification RE-ID technology is a deep learning-based approach to matching visual identities across non-overlapping camera views. RE-ID extracts feature vectors representing unique visual attributes, enabling video management systems to recognise and track individuals even with changes in appearance or conditions. For example, it can identify a person entering a building with an orange jacket and later recognise the same person leaving with the jacket unzipped and a hat, across different cameras. Dynamic Privacy Masking This AI-based feature efficiently safeguards biometric personal data, ensuring compliance with privacy regulations. Wisenet 9 offers flexible masking options, including both opaque and mosaic masking, allowing users to tailor privacy protection to their specific needs and preferences. Widening horizons with expandable AI Wisenet 9 has been engineered with unparalleled AI capabilities to recognise security demands Recognising that security demands are as diverse as the industries they serve, Wisenet 9 has been engineered with unparalleled AI capabilities. This empowers users to tailor their security systems. § AI Packs: Wisenet 9 is compatible with AI Packs (Traffic, Retail, Factory), designed to deliver actionable insights specific to various sectors. AI Sound Classification AI-based sound classification enables rapid detection and directional awareness of critical events like gunshots, glass breaks, and screaming, to enhance situational awareness. Hanwha vision open platform Wisenet 9 empowers users to create customised security solutions by providing the flexibility to tailor their systems with custom applications for video analytics, storage, and other functionalities. Improved end-to-end protection Wisenet 9 significantly enhances end-to-end protection by building upon the robust security foundation of Wisenet 7. It inherits essential features like Secure Storage, OS, and Boot, which protect critical chipset data and prevent unauthorised software execution. Moreover, the inclusion of a FIPS 140-3 Level 3 elevates security to an exceptional standard. This certification guarantees that the chipset adheres to rigorous security protocols, assuring users of comprehensive data protection.
Modern measurement technologies enable high-precision detection of the movement of liquids and gases - and thus provide valuable data for numerous applications. How does the air flow around an aeroplane? How does the blood move through our veins? And how can pollutant emissions in combustion processes be minimised? For this purpose, speed, direction, pressure and turbulence within a flow are analysed in order to increase efficiency, ensure safety and drive innovation in a wide variety of areas. Flow visualisation techniques A range of methods are available to measure these flows, such as particle image velocimetry A range of methods are available to measure these flows, including visual ones such as particle image velocimetry (PIV). High-resolution cameras are used to track marked particles within a flow and analyse their movement. iLA_5150 GmbH from Aachen (Germany) now also relies on EBIV. The abbreviation stands for Event Based Particle Image Velocimetry and is a new optical method for the qualitative and quantitative visualisation of flows and flow velocities. It combines PIV with event based cameras, here with a uEye EVS from IDS Imaging Development Systems GmbH. The innovative sensor technology of the industrial camera enables highly dynamic and energy-efficient detection, especially of fast and turbulent movements. Dynamic light capture In the EBIV method, tiny particles are added to a flowing fluid and illuminated in a plane, the so-called light section plane. They generate individual light pulses as they enter and exit the LED light section. This change in local brightness is recorded independently by the camera pixels and transmitted to the PC as a data stream of "change events". In contrast to conventional cameras, event-based models therefore only react to the changes in brightness registered in the image field. Stationary scattered light, such as background or a non-changing illuminated surface, does not generate a measurement signal. This reduces the amount of data considerably. Enhanced frame rates The data stream essentially contains information about what happens, when and where. In detail, these are the pixel coordinates on the sensor, microsecond time stamps of the pixel events and the information about the events: ON or OFF. This allows a distinction to be made between increasing intensity (ON event) and decreasing intensity (OFF event). Using suitable software, the stream can be converted into an image matrix in which both the spatial information and the linear time base of the stream are available. The result is comparable to the extremely high frame rate of a high-speed camera. Efficient frame capture "The EBIV measurement method differs fundamentally from conventional imaging methods. They usually generate very large amounts of data and require powerful peripherals that can process them.” “For exceptional frame rates of 1000 Hertz and more, the image-based cameras required are themselves very complex and expensive. With the help of event-based camera technology, comparable frame rates of 10,000 frames per second are possible, whereby only standard PC interfaces such as USB with a few gigabits per second are required.” “The price of the event-based models themselves is significantly lower than that of corresponding high-speed cameras and is therefore also very interesting for smaller teaching and research institutions," explains Dr André Brunn - Head of Development at iLA_5150 GmbH. Further processing The data stream is converted into image data and displayed in a front end - the so-called EBIV viewer – for direct online flow visualisation. The user can also select the integration time, which corresponds to the exposure time of an image camera, as well as the time increments of the sequence, i.e. the period between two consecutive shots. Classic image filters can also be used. With the help of these settings, the user can optimise the display of the movement paths and adapt them to individual examination objectives. Both fine flow details and large-scale patterns can be made more clearly recognisable. This ability to readjust the measurement results is another advantage of the event-based approach. Qualitative visualisation For a precise analysis of the flow properties, individual particles are illuminated for a moment using short In the qualitative visualisation of the flow in the EBIV-View, particles are continuously illuminated so that they are visible as luminous traces. The method is therefore very well suited to visualising the flow. However, it does not provide exact measurements of its speed or direction. For a precise, numerical analysis of the flow properties, individual particles are illuminated for a moment using short, time-defined light pulses. This allows their exact position to be recorded and their movement quantified. By comparing the particle positions in successive images, the speed and direction of the flow can be precisely calculated using PIV, for example. The result is a transient 2D vector field that changes over time - in other words, the vectors do not remain constant. As with classic PIV, the image sequences of the event-based camera can also be statistically analysed, for example to determine mean values and fluctuations in the flow velocity. Camera and software On the camera side, iLA relies on a uEye XCP-E from IDS. The small, lightweight industrial camera offers event-based sensor technology in a robust die-cast zinc housing (29 × 29 × 17 mm) with screw-on USB Micro-B connection. It is compatible with all standard C-mount lens sizes. This makes it ideal for both industrial and non-industrial areas. The integrated event-based vision sensor (EVS) was developed by Sony and Prophesee. It is supported by the Metavision SDK, a seamlessly integrated suite of software tools and models, APIs and other training and development resources from Prophesee for efficient analysis, visualisation and customisation. Building on this, the EBIV viewer from iLA_5150/PIVTec is specially tailored to flow visualisation applications. Outlook The optimisation of fluidic systems and processes requires detailed knowledge of the flow conditions. A qualitative flow visualisation is often sufficient to understand effects and develop suitable control mechanisms. Until now, however, imaging fast flows with high temporal resolution was usually only possible with expensive high-speed cameras. Event-based camera technology offers a cost-effective alternative that requires significantly less technical effort. These “simple” methods have been lacking in teaching and research in particular. Thanks to the extreme data reduction, this technology also allows the use of several cameras or large camera arrays without the periphery becoming a limitation for data transfer. The compact design of the uEye EVS models also makes them ideal for mobile applications. This means that real application environments can be analysed directly for the first time - without having to rely on artificial flow models or channels.
Omada by TP-Link and VIGI by TP-Link, TP-Link Systems Inc.’s exclusive business solutions brands, are set to make waves at ISC West 2025 with the debut of their groundbreaking unified networking and surveillance solutions. At the event, the brands will showcase a seamless integration of VIGI’s cutting-edge surveillance solutions, Omada’s comprehensive networking systems, and the Omada Central platform—a revolutionary cloud-based solution that unifies the management of networking and surveillance under one roof. Secure & scalable Focused exclusively on the B2B market, Omada and VIGI deliver reliable, secure, and intuitive networking and surveillance products tailored to the unique needs of SMBs and enterprises. Designed to address diverse scenarios—including retail, hospitality, offices, MDUs, and outdoor environments—Omada and VIGI empower businesses to enhance security, streamline operations, and drive efficiency. Unified networking and surveillance solutions Integrating networking and surveillance into a single platform, TP-Link eliminates the system managment complecity By integrating networking and surveillance into a single platform, TP-Link eliminates the complexity of managing multiple systems. This unified approach enables unified management; easy deployment and setup; and remote troubleshooting, reducing operational overhead while enhancing efficiency, scalability, and security for businesses across industries. Omada Central is the cornerstone of TP-Link’s unified approach, offering a single platform to manage both Omada networking devices and VIGI surveillance systems. This next-generation solution enables businesses to seamlessly manage gateways, switches, access points, and security surveillance equipment across multiple locations. Simplified Management It simplifies setup with intelligent device recognition, auto surveillance VLAN, and Zero-Touch Provisioning while reducing total cost of ownership with a single-vendor solution. The platform also offers a free version, Omada Central Essentials, making it accessible for businesses of all sizes. VIGI: professional surveillance solutions VIGI provides professional, reliable, and comprehensive surveillance solutions tailored for businesses. Offering a diverse product range—including bullet, turret, dome, and fisheye cameras, 4/8/16/32/64-channel NVRs, 90W/180W solar power systems, cloud and local VMS, and user-friendly apps—VIGI ensures robust security while enhancing operational efficiency and profitability. VIGI offers a comprehensive range of durable cameras designed to deliver guaranteed high-quality images. The product lineup includes: 180° Panoramic 4K Cameras with Red-Blue Warning Lights Dual-Lens Stitching 4K Cameras 4G Outdoor Cameras with 3 LAN Ports AI ISP-Powered ColorPro 2.0 Cameras 5X Optical Zoom Cameras Complementing these cameras are 64-Channel H.265+ NVRs featuring 4 SATAs with a up to 64TB storage capability and 320Mbps incoming/outgoing bandwidth. Additionally, VIGI’s easy-to-install and stable solar power solution ensures long standby performance, making it ideal for off-grid locations. VIGI CVM System VIGI’s Cloud Video Management System (VMS) provides free, centralised management for multiple sites, leveraging AWS-based reliability and zero-touch maintenance to reduce on-site troubleshooting costs and ensure seamless surveillance. Complementing this is VIGI’s NPU-powered AI technology, offering advanced detection and analysis capabilities such as Behavior and Object Detection; People and Vehicle Attributes Analysis; and Precise People Counting. Together, these innovations deliver smarter, more efficient security solutions that enhance operational efficiency and drive business success. Omada: Comprehensive Networking Solutions Omada delivers a complete set of SDN solutions, designed to meet the needs of businesses With a full portfolio that includes access points, gateways, hardware controllers, cloud controllers, and a diverse range of switches, Omada provides end-to-end networking solutions tailored for scalability, performance, and ease of management. Omada’s full lineup of Wi-Fi 7 access points redefine wireless connectivity, offering unparalleled speed and reliability for both indoor and outdoor environments. Complementing these are Outdoor 4G Wi-Fi Gateways and connectivity solutions, such as the Outdoor PoE Switch and Wireless Long-Range PtMP/PtP Bridge, which ensure reliable networking even in remote or challenging locations. The switch portfolio spans from unmanaged switches for plug-and-play simplicity to easy-managed switches and advanced L3/L2 + switches, catering to businesses of all sizes and complexities. Effortless surveillance connectivity The Agile Series of Easy Managed PoE Switches with Free Cloud, designed specifically for surveillance systems. Paired with Omada Central Essentials for free cloud access, the Agile Series features Auto IP Camera/NVR Recognition, Extend Mode for PoE up to 250m, enhanced PoE Auto Recovery, and Remote Troubleshooting Tools with Cable Test, Reboot PoE Port Management, and SSH to minimise downtime, making it an ideal choice for businesses seeking efficient and scalable networking solutions tailored to surveillance needs. Seamless connectivity Omada & VIGI unified networking and surveillance solutions are tailored to meet the needs of diverse industries, including retail, hospitality, offices, residential, and outdoor environments. By combining Omada’s networking expertise, VIGI’s surveillance solutions, and the Omada Central platform, TP-Link delivers agile, secure, and scalable ecosystems that simplify infrastructure and enhance operational efficiency across the board.
FLIR, a Teledyne Technologies company, is set to showcase its maintenance portfolio at Maintenance NEXT from April 8 to 10 in Rotterdam. FLIR Si1-LD acoustic camera FLIR’s main highlight at Maintenance NEXT will be the new Si1-LD industrial acoustic imaging camera, which brings faster and more accurate compressed air leak detection to those operating on a limited condition monitoring budget. Si1-LD offers improved detection and quantification capabilities in comparison with the existing FLIR Si124-LD Plus, along with a higher upper limit frequency range. Leveraging the advantages of ultrasonic technology, the new FLIR Si1-LD pinpoints leaks with enhanced imaging sensitivity at an affordable price. FLIR products In addition to the Si1-LD, FLIR will also showcase the following products: FLIR E8 Pro: The FLIR E8 Pro is the must-have tool for locating and diagnosing electrical, mechanical, and building problems. FLIR T530-14°: The FLIR T530 thermal camera has the features professionals need to accurately troubleshoot hot spots and potential faults. With the 180° rotating lens platform and a bright 4" LCD, the FLIR T530 is engineered to help users diagnose hard-to-reach components in any environment. 80° Wide-Angle Thermal Lens: The FLIR 80° lens is designed to enable maintenance managers, engineers, and mechanical technicians to keep an eye on assets in a large target area for continuous monitoring, condition monitoring, and early intervention of developing faults. FlexView® Dual FOV IR Lens (42°/24°): The FlexView 42°/24° lens is ideal for inspecting large targets, while providing excellent image understanding without sacrificing standard target image quality. FLIR IRP-1: The FLIR IRP-1 port helps to improve worker safety and electrical inspection efficiency—all while reducing the installation costs associated with using thermal cameras to inspect indoor electrical cabinets. FLIR ONE® Edge Pro: This thermal camera for smartphones allows them to take crisp thermal images from any angle. Improved battery time and ruggedness makes sure the camera is ready to use in more industrial environments. FLIR C5: With the FLIR C5 in the pocket they’ll be ready anytime to find hot fuses, air leaks, plumbing issues, and more. FLIR Cx5: The FLIR Cx5 is certified for use in many explosive environments, eliminating the need to acquire hot work permits due to gas, vapour, and dust, while making T-Class surveys quick and easy. FLIR Si2-Pro: The FLIR Si2-Pro helps to significantly lower costs associated with mechanical bearing issues and partial discharge on electrical equipment. Visit FLIR at Maintenance NEXT, booth number 5.005, from April 8 to 10 in Rotterdam.
FLIR, pioneer in high-performance marine thermal-imaging systems, announced the launch of the new FLIR JCU-4 remote control, offering precision camera control and an elevated, yet simplified user experience. Providing confident control of FLIR marine thermal and visible cameras, the FLIR JCU-4 remote control is designed for FLIR marine cameras and is compatible with the M232, M300, M400/M400XR and M500 series, as well as legacy models. It offers pan, tilt, and zoom capabilities, and control of all additional camera functions with an ergonomic keypad and responsive joystick control. Camera operation and easy access The JCU-4 is a meaningful upgrade for those who actively navigate using thermal technology Designed by mariners, for mariners, the JCU-4 is a meaningful upgrade for those who actively navigate using thermal technology and require dependable and intuitive control of their FLIR camera. The rugged, low-profile three-axis joystick is mounted with a 2.9-inch colour LCD and keypad, to simplify camera operation and offer easy access to the joystick setup menus. A dimmable colour LCD and back-lit keypad preserves the operator’s vision during nighttime operations. User-defined camera functions The JCU-4 can be easily configured with intuitive pairing between FLIR marine cameras and marine monitors or chartplotters. Three custom keys can be pre-programmed for quick access to the most used user-defined camera functions. The FLIR JCU-4 is available for $1,699 USD.
Zenitel, a global pioneer in Unified Critical Communication solutions, is launching two new innovations for mixed-use building communication solutions: the Zenitel Display Door intercom (ZDD-1) and the Zenitel Slim Door intercom (ZSD-1). This launch further strengthens Zenitel’s position as a market leader in audio communication solutions. Amazing sound, effortlessly integrated New door entry intercoms are engineered from the ground up, offering a premium audio experience With 125 years of experience in sound design, these new door entry intercoms are engineered from the ground up, offering a premium audio experience in a sleek design that seamlessly blends into any building. With ONVIF compatibility, they seamlessly integrate with surveillance systems, providing an additional layer of security for effective identification and entry control. “Door entry intercoms are an essential part of overall building security, and there are plenty of options available on the market. However, we had a different vision for ours – to uniquely enhance our customer experience and continue elevating audio quality, which is the cornerstone for Zenitel,” said Lars Paulsson, EVP for Safety and Security at Zenitel. "The combination of high-quality hardware, advanced software-driven audio processing, and precision engineering makes our new door entry intercoms the most realistic-sounding intercom on the market.” Zenitel display door Built on Zenitel’s industry-leading sound technology, the Zenitel Display Door intercom features a speaker and microphone array to deliver an immersive sound experience, while high sound pressure levels make it ideal even for high-noise environments. The bi-directional video communication enables face-to-face interaction, fostering a sense of connection, while also supporting the needs of sign language users. The Zenitel Display Door (ZDD-1) features an intuitive touch display with an easy-to-use UI/UX, making navigation simple and efficient for all users. Zenitel slim door The Zenitel Slim Door (ZSD-1) is a compact yet powerful, outdoor-ready intercom that delivers premium sound in a sleek design, with easy installation in tight spaces, including door frames. The intuitive design of this intercom offers visual and aural feedback to ensure ease of use for all users. Unified communication As organizations seek to secure assets and streamline operations through technology, Zenitel’s latest innovations in door entry communications, combined with Zenitel Connect Pro — the industry's first Unified Critical Communication Platform — pave the way for unifying communication needs under a single platform for building owners. Additionally, built-in cybersecurity features of these intercoms ensure secure and encrypted communication at the door.
The future of security requires smarter, more efficient and secure solutions, and Hanwha Vision is helping to drive this transformation with the launch of its most advanced AI-powered System on a Chip (SoC), Wisenet 9. After nearly four years of extensive research and testing, Wisenet 9’s advanced features help elevate our cameras into an AI-driven era, setting a new standard for performance, accuracy, and security. Unmatched clarity “With Wisenet 9, you can count on the superior image quality that delivers the best possible video in the toughest environments, as well as the accuracy of the AI-generated data, whether statistical or event-driven,” states John Lutz Boorman, Head of Product and Marketing at Hanwha Vision Europe. AI revolution at the Edge Wisenet 9’s enhanced edge AI capabilities are essential in this innovation era, where the volume and complexity of security threats demand real-time, accurate analysis. By elevating edge-device performance, AI empowers systems to quickly analyse vast amounts of video data and discern crucial patterns and anomalies. A key differentiator driving this transformation is the two Neural Processing Units (NPUs), which have improved inference performance three-fold compared to Wisenet 7, the previous SoC generation. While one NPU handles image processing, the other focuses on object detection and advanced analytics. This dual NPU concept was introduced to ensure video quality and analytics have independent resources, preventing one function from impacting the performance of the other. Unveiling hidden details Wisenet 9 uses AI to analyse visual data with greater precision. By leveraging a powerful NPU, the system moves past traditional image processing to extract critical information, unlocking previously unseen details with remarkable clarity in tough environments. This enhanced visual intelligence is achieved through a suite of sophisticated AI features, including AI-based extreme Wide Dynamic Range, AI-powered noise reduction, alongside image enhancements. Combined, these technologies deliver exceptional clarity, even under the most challenging conditions. The AI-driven image enhancement, powered by an independent NPU, ensures that every detail, no matter how subtle, is captured and analysed. AI efficiency redefined The H.265 codec provides high video quality with optimised bandwidth AI is powerful, but it can also be resource-intensive. Wisenet 9 flips that script. It’s not just smart, it’s efficient - optimising every aspect of its operation.By intelligently reducing noise, Wisenet 9 achieves a remarkable level of efficiency in data volume reduction, resulting in significantly reduced bandwidth consumption and storage requirements. This core efficiency is further bolstered by the latest H.265 compression technology. The H.265 codec provides high video quality with optimised bandwidth, ensuring reliable, real-time video processing and transmission - critical for uninterrupted 24/7 security. Furthermore, this optimised H.265 support enables consistently high performance in demanding environments, essential for system stability, and streamlines data management in cloud environments, efficiently controlling storage and transfer costs. Seamless integration Wisenet 9’s H.265 codec, aligned with current industry standards and ONVIF profiles, ensures broad hardware compatibility and seamless integration with your existing security infrastructure and provides a dependable foundation for long-term system reliability. Beyond this, Wisenet 9 leverages AI for advanced analytics. Its enhanced AI technology provides detailed attribute analysis, including colour, bag, face mask, glasses, age, and gender, along with other key analytics like people and vehicle counting, slip and fall detection, crowd detection, heatmap, queue management, and more, enabling faster and more informed decision-making. Smart surveillance tech To further amplify its capabilities, Wisenet 9 incorporates several key technologies that power the next generation of efficiency, including: Re-Identification RE-ID technology is a deep learning-based approach to matching visual identities across non-overlapping camera views. RE-ID extracts feature vectors representing unique visual attributes, enabling video management systems to recognise and track individuals even with changes in appearance or conditions. For example, it can identify a person entering a building with an orange jacket and later recognise the same person leaving with the jacket unzipped and a hat, across different cameras. Dynamic Privacy Masking This AI-based feature efficiently safeguards biometric personal data, ensuring compliance with privacy regulations. Wisenet 9 offers flexible masking options, including both opaque and mosaic masking, allowing users to tailor privacy protection to their specific needs and preferences. Widening horizons with expandable AI Wisenet 9 has been engineered with unparalleled AI capabilities to recognise security demands Recognising that security demands are as diverse as the industries they serve, Wisenet 9 has been engineered with unparalleled AI capabilities. This empowers users to tailor their security systems. § AI Packs: Wisenet 9 is compatible with AI Packs (Traffic, Retail, Factory), designed to deliver actionable insights specific to various sectors. AI Sound Classification AI-based sound classification enables rapid detection and directional awareness of critical events like gunshots, glass breaks, and screaming, to enhance situational awareness. Hanwha vision open platform Wisenet 9 empowers users to create customised security solutions by providing the flexibility to tailor their systems with custom applications for video analytics, storage, and other functionalities. Improved end-to-end protection Wisenet 9 significantly enhances end-to-end protection by building upon the robust security foundation of Wisenet 7. It inherits essential features like Secure Storage, OS, and Boot, which protect critical chipset data and prevent unauthorised software execution. Moreover, the inclusion of a FIPS 140-3 Level 3 elevates security to an exceptional standard. This certification guarantees that the chipset adheres to rigorous security protocols, assuring users of comprehensive data protection.
Modern measurement technologies enable high-precision detection of the movement of liquids and gases - and thus provide valuable data for numerous applications. How does the air flow around an aeroplane? How does the blood move through our veins? And how can pollutant emissions in combustion processes be minimised? For this purpose, speed, direction, pressure and turbulence within a flow are analysed in order to increase efficiency, ensure safety and drive innovation in a wide variety of areas. Flow visualisation techniques A range of methods are available to measure these flows, such as particle image velocimetry A range of methods are available to measure these flows, including visual ones such as particle image velocimetry (PIV). High-resolution cameras are used to track marked particles within a flow and analyse their movement. iLA_5150 GmbH from Aachen (Germany) now also relies on EBIV. The abbreviation stands for Event Based Particle Image Velocimetry and is a new optical method for the qualitative and quantitative visualisation of flows and flow velocities. It combines PIV with event based cameras, here with a uEye EVS from IDS Imaging Development Systems GmbH. The innovative sensor technology of the industrial camera enables highly dynamic and energy-efficient detection, especially of fast and turbulent movements. Dynamic light capture In the EBIV method, tiny particles are added to a flowing fluid and illuminated in a plane, the so-called light section plane. They generate individual light pulses as they enter and exit the LED light section. This change in local brightness is recorded independently by the camera pixels and transmitted to the PC as a data stream of "change events". In contrast to conventional cameras, event-based models therefore only react to the changes in brightness registered in the image field. Stationary scattered light, such as background or a non-changing illuminated surface, does not generate a measurement signal. This reduces the amount of data considerably. Enhanced frame rates The data stream essentially contains information about what happens, when and where. In detail, these are the pixel coordinates on the sensor, microsecond time stamps of the pixel events and the information about the events: ON or OFF. This allows a distinction to be made between increasing intensity (ON event) and decreasing intensity (OFF event). Using suitable software, the stream can be converted into an image matrix in which both the spatial information and the linear time base of the stream are available. The result is comparable to the extremely high frame rate of a high-speed camera. Efficient frame capture "The EBIV measurement method differs fundamentally from conventional imaging methods. They usually generate very large amounts of data and require powerful peripherals that can process them.” “For exceptional frame rates of 1000 Hertz and more, the image-based cameras required are themselves very complex and expensive. With the help of event-based camera technology, comparable frame rates of 10,000 frames per second are possible, whereby only standard PC interfaces such as USB with a few gigabits per second are required.” “The price of the event-based models themselves is significantly lower than that of corresponding high-speed cameras and is therefore also very interesting for smaller teaching and research institutions," explains Dr André Brunn - Head of Development at iLA_5150 GmbH. Further processing The data stream is converted into image data and displayed in a front end - the so-called EBIV viewer – for direct online flow visualisation. The user can also select the integration time, which corresponds to the exposure time of an image camera, as well as the time increments of the sequence, i.e. the period between two consecutive shots. Classic image filters can also be used. With the help of these settings, the user can optimise the display of the movement paths and adapt them to individual examination objectives. Both fine flow details and large-scale patterns can be made more clearly recognisable. This ability to readjust the measurement results is another advantage of the event-based approach. Qualitative visualisation For a precise analysis of the flow properties, individual particles are illuminated for a moment using short In the qualitative visualisation of the flow in the EBIV-View, particles are continuously illuminated so that they are visible as luminous traces. The method is therefore very well suited to visualising the flow. However, it does not provide exact measurements of its speed or direction. For a precise, numerical analysis of the flow properties, individual particles are illuminated for a moment using short, time-defined light pulses. This allows their exact position to be recorded and their movement quantified. By comparing the particle positions in successive images, the speed and direction of the flow can be precisely calculated using PIV, for example. The result is a transient 2D vector field that changes over time - in other words, the vectors do not remain constant. As with classic PIV, the image sequences of the event-based camera can also be statistically analysed, for example to determine mean values and fluctuations in the flow velocity. Camera and software On the camera side, iLA relies on a uEye XCP-E from IDS. The small, lightweight industrial camera offers event-based sensor technology in a robust die-cast zinc housing (29 × 29 × 17 mm) with screw-on USB Micro-B connection. It is compatible with all standard C-mount lens sizes. This makes it ideal for both industrial and non-industrial areas. The integrated event-based vision sensor (EVS) was developed by Sony and Prophesee. It is supported by the Metavision SDK, a seamlessly integrated suite of software tools and models, APIs and other training and development resources from Prophesee for efficient analysis, visualisation and customisation. Building on this, the EBIV viewer from iLA_5150/PIVTec is specially tailored to flow visualisation applications. Outlook The optimisation of fluidic systems and processes requires detailed knowledge of the flow conditions. A qualitative flow visualisation is often sufficient to understand effects and develop suitable control mechanisms. Until now, however, imaging fast flows with high temporal resolution was usually only possible with expensive high-speed cameras. Event-based camera technology offers a cost-effective alternative that requires significantly less technical effort. These “simple” methods have been lacking in teaching and research in particular. Thanks to the extreme data reduction, this technology also allows the use of several cameras or large camera arrays without the periphery becoming a limitation for data transfer. The compact design of the uEye EVS models also makes them ideal for mobile applications. This means that real application environments can be analysed directly for the first time - without having to rely on artificial flow models or channels.
Omada by TP-Link and VIGI by TP-Link, TP-Link Systems Inc.’s exclusive business solutions brands, are set to make waves at ISC West 2025 with the debut of their groundbreaking unified networking and surveillance solutions. At the event, the brands will showcase a seamless integration of VIGI’s cutting-edge surveillance solutions, Omada’s comprehensive networking systems, and the Omada Central platform—a revolutionary cloud-based solution that unifies the management of networking and surveillance under one roof. Secure & scalable Focused exclusively on the B2B market, Omada and VIGI deliver reliable, secure, and intuitive networking and surveillance products tailored to the unique needs of SMBs and enterprises. Designed to address diverse scenarios—including retail, hospitality, offices, MDUs, and outdoor environments—Omada and VIGI empower businesses to enhance security, streamline operations, and drive efficiency. Unified networking and surveillance solutions Integrating networking and surveillance into a single platform, TP-Link eliminates the system managment complecity By integrating networking and surveillance into a single platform, TP-Link eliminates the complexity of managing multiple systems. This unified approach enables unified management; easy deployment and setup; and remote troubleshooting, reducing operational overhead while enhancing efficiency, scalability, and security for businesses across industries. Omada Central is the cornerstone of TP-Link’s unified approach, offering a single platform to manage both Omada networking devices and VIGI surveillance systems. This next-generation solution enables businesses to seamlessly manage gateways, switches, access points, and security surveillance equipment across multiple locations. Simplified Management It simplifies setup with intelligent device recognition, auto surveillance VLAN, and Zero-Touch Provisioning while reducing total cost of ownership with a single-vendor solution. The platform also offers a free version, Omada Central Essentials, making it accessible for businesses of all sizes. VIGI: professional surveillance solutions VIGI provides professional, reliable, and comprehensive surveillance solutions tailored for businesses. Offering a diverse product range—including bullet, turret, dome, and fisheye cameras, 4/8/16/32/64-channel NVRs, 90W/180W solar power systems, cloud and local VMS, and user-friendly apps—VIGI ensures robust security while enhancing operational efficiency and profitability. VIGI offers a comprehensive range of durable cameras designed to deliver guaranteed high-quality images. The product lineup includes: 180° Panoramic 4K Cameras with Red-Blue Warning Lights Dual-Lens Stitching 4K Cameras 4G Outdoor Cameras with 3 LAN Ports AI ISP-Powered ColorPro 2.0 Cameras 5X Optical Zoom Cameras Complementing these cameras are 64-Channel H.265+ NVRs featuring 4 SATAs with a up to 64TB storage capability and 320Mbps incoming/outgoing bandwidth. Additionally, VIGI’s easy-to-install and stable solar power solution ensures long standby performance, making it ideal for off-grid locations. VIGI CVM System VIGI’s Cloud Video Management System (VMS) provides free, centralised management for multiple sites, leveraging AWS-based reliability and zero-touch maintenance to reduce on-site troubleshooting costs and ensure seamless surveillance. Complementing this is VIGI’s NPU-powered AI technology, offering advanced detection and analysis capabilities such as Behavior and Object Detection; People and Vehicle Attributes Analysis; and Precise People Counting. Together, these innovations deliver smarter, more efficient security solutions that enhance operational efficiency and drive business success. Omada: Comprehensive Networking Solutions Omada delivers a complete set of SDN solutions, designed to meet the needs of businesses With a full portfolio that includes access points, gateways, hardware controllers, cloud controllers, and a diverse range of switches, Omada provides end-to-end networking solutions tailored for scalability, performance, and ease of management. Omada’s full lineup of Wi-Fi 7 access points redefine wireless connectivity, offering unparalleled speed and reliability for both indoor and outdoor environments. Complementing these are Outdoor 4G Wi-Fi Gateways and connectivity solutions, such as the Outdoor PoE Switch and Wireless Long-Range PtMP/PtP Bridge, which ensure reliable networking even in remote or challenging locations. The switch portfolio spans from unmanaged switches for plug-and-play simplicity to easy-managed switches and advanced L3/L2 + switches, catering to businesses of all sizes and complexities. Effortless surveillance connectivity The Agile Series of Easy Managed PoE Switches with Free Cloud, designed specifically for surveillance systems. Paired with Omada Central Essentials for free cloud access, the Agile Series features Auto IP Camera/NVR Recognition, Extend Mode for PoE up to 250m, enhanced PoE Auto Recovery, and Remote Troubleshooting Tools with Cable Test, Reboot PoE Port Management, and SSH to minimise downtime, making it an ideal choice for businesses seeking efficient and scalable networking solutions tailored to surveillance needs. Seamless connectivity Omada & VIGI unified networking and surveillance solutions are tailored to meet the needs of diverse industries, including retail, hospitality, offices, residential, and outdoor environments. By combining Omada’s networking expertise, VIGI’s surveillance solutions, and the Omada Central platform, TP-Link delivers agile, secure, and scalable ecosystems that simplify infrastructure and enhance operational efficiency across the board.


Expert commentary
In today’s world, almost any electronic security system holds the potential to become a gateway for cybercriminals. With physical security and cybersecurity increasingly entwined, security professionals aren’t doing their job unless they take all possible precautions to lock down unauthorised access to camera systems, access control platforms, intercoms, and other network-based security devices and solutions. Let’s explore the many steps companies should take throughout their security technologies’ lifecycle – from choosing a vendor all the way through device decommissioning – to avoid making the common mistakes that leave systems, and the networks they reside on, vulnerable to attack and sabotage. Prepurchase phase: Laying the groundwork for cybersecurity 1. Conduct a Vendor Risk Assessment IT departments often rely on the same Vendor Risk Assessment criteria they use for evaluating IT equipment manufacturers when considering the suitability of physical security vendors. While commonalities exist between how to assess these disparate solutions, there are also differences that require distinct scrutiny. For example, device endpoints within physical security systems run on custom Linux Kernels and therefore do not utilise standard Linux distributions like Red Hat, Ubuntu, or Debian. IT divisions often rely on the same Vendor Risk Assessment criteria they use for evaluating IT kit A comprehensive evaluation should examine how each security solutions manufacturer handles its software development life cycles. Ideally, vendors should adhere to a recognised framework when developing both their platform management and device-specific software. In 2021, Executive Order 14028 made it a bit easier for companies to evaluate vendors by providing guidelines for evaluating software security, the practices of the software developer, and methods to demonstrate conformance with secure practices, specifically referencing the NIST SP 800-218 Secure Software Development Framework. In short, a good vendor should have documentation that explains everything it’s doing to address cybersecurity from development, through releases and ongoing maintenance. 2. Obtain Software Update Schedules The frequency with which manufacturers update their software varies. Each company is different. If you’re their customer, it shouldn't matter whether the vendor schedules updates every six months, three months, or more often than that. What does matter is that you know what to expect and have a plan for how to deal with that reality. For example, if updates only occur every six months, under what conditions are patches released to address vulnerabilities that emerge between updates? Customers must understand how often they'll be updating the software on their devices and ensure they have the resources to make it happen. Make sure stakeholders agree, upfront, who will be performing the software updates. Will it be the integrator who installed the system, the physical security system staff, the IT team, or the end user? Keeping an entire system current is a huge challenge, but a non-negotiable responsibility. Manufacturers who don't issue frequent releases and patches put the onus on customers to handle mitigation efforts on their own. In these instances, IT departments must be prepared to employ network segmentation, firewalls, security whitelists/blacklists, and other methods to protect their systems until a patch is released. If a company's security team has typically updated firmware only when something breaks, these additional responsibilities most likely require greater collaboration with IT departments and a shift in how security systems are managed. 3. Know the Warranty Terms and Duration of Software Support Organisations should understand the warranty policies for the devices they purchase Organisations should understand the warranty policies for the devices they purchase. Even more important is knowing when a device's software support will expire. Software support should extend well beyond hardware coverage. For example, if a camera has a five-year hardware warranty, customers should reasonably expect an additional five years of software support. When that period ends, companies must plan on replacing the device – even if it still works well. Without software updates, the device lacks vulnerability support and becomes too risky to remain on the network. Manufacturers should be transparent about their warranty and software support policies, helping organisations plan for device replacements that align with cybersecurity needs. 4. Request a Software Bill of Materials (SBOM) During the pre-discovery process, customers should request a Software Bill of Materials (SBOM) that provides a detailed inventory of the software running on each device, including open-source components. By revealing what software is "under the hood," the SBOM allows IT departments to be vigilant in protecting the company's systems from exposed vulnerabilities. For example, a customer should understand how Transport Layer Security (TLS) is being handled to secure a security solution's web server if it’s an open-source component like OpenSSL. 5. Assess Vulnerability Disclosure Practices CNA manufacturers represent the gold standard in cybersecurity practices Understanding how a manufacturer handles vulnerabilities is essential. Ideally, they should be a Certified Naming Authority (CAN) and report common vulnerabilities and exposures (CVEs) to national vulnerability databases such as NIST and MITRE. Doing so automatically includes any disclosed vulnerabilities associated with their devices in vulnerability scanners' databases. CNA manufacturers represent the gold standard in cybersecurity practices, but most security manufacturers do not reach this level. At a minimum, the vendors you choose to work with should have an email notification system in place to alert customers to new vulnerabilities. Remember – email notifications are only as reliable as the employees managing them, so investigate whether the manufacturer has a strong track record of keeping up with such communications. Ask to speak with customer references who have been using the solution for an extended period to ensure the vendor is diligent in its communications. Configuration phase: Ensuring a secure setup 1. Use Hardening Guides Once a device is purchased, configuring it securely is the next critical step. Manufacturers should publish hardening guides that detail the security controls available for their products and recommended practices for implementation. Between the features offered by the vendor and your company's own cybersecurity policies, make sure all possible encryption options are activated. Using HTTPS is vital for ensuring secure communication with devices. Many physical security devices default to HTTP to accommodate customer-specific network topologies and certificate management. Failing to implement HTTPS can leave sensitive metadata unencrypted and vulnerable to interception. 2. Consider Advanced Encryption Protocols Protocols are necessary to protect video data in transit from cameras to the VMS Some solutions offer built-in encryption protocols, like MACsec, which makes it impossible for data to be compromised as it is transmitted over the network. HTTPS is still necessary to secure the connection to the devices’ webservice, but while customers set up and configure their devices, MACsec will keep network data safe. Additionally, if you want to encrypt video streams, consider protocols such as Secure Real-Time Transport Protocol (SRTP), which secures the transmission of audio and video data over the Internet, or tunnelling methods like Secure Socket Tunnelling Protocol (SSTP), which encapsulate data packets for safe transmission between two points, even if the network is insecure. Such protocols are necessary to protect video data in transit from cameras to the Video Management System (VMS). Encryption should also extend to the VMS hard drive where video is stored. There are different methodologies to do that, but ultimately the goal is to encrypt data in transit and in storage. 3. Implement Remote Syslog In the case of a breach, each device maintains a set of logs that are useful for forensic investigations. However, if a device gets hacked, its log may not be accessible. Best practices dictate that companies should set up a remote Syslog server that maintains a copy of all device logs within a central repository. In addition to providing redundant data for investigations, a Syslog offers IT systems an efficient way to look for anomalies. Cybersecurity teams will receive immediate notification for events like unsuccessful login attempts so they can quickly figure out what's happening. Who is trying to log in? Why on that particular device? 4. Practice Healthy Password Hygiene Ideally, organisations should move towards using Active Directory or Single Sign-On (SSO) solutions One of the most basic and yet overlooked aspects of cybersecurity is the failure to manage user accounts meticulously. Many organisations use the same username and password for all security devices because it's simply too cumbersome to manage a network of devices in which each requires a separate, unique login. It's assumed that the system's primary administrators are the only ones who know the universal password. However, the system becomes vulnerable if anyone within this select group leaves the company and the password isn't changed or deleted right away. Ideally, organisations should move towards using Active Directory or Single Sign-On (SSO) solutions. This approach ensures that employees throughout a company are each assigned a unique login credential that they use for any systems they use throughout the organisation. When they leave, their passwords and access are universally terminated along with their accounts. If SSO is not an option, regular password changes and prompt account deactivation are critical. Decommissioning phase: Securely retiring devices At some point, physical security devices will reach the end of their useful life. When that time comes, companies must take care in how they dispose of their devices. A good vendor will provide guidance on how to clear memory chipsets and restore factory defaults. Improper decommissioning can lead to severe risks. For example, if an improperly decommissioned device is sold on the secondary market or retrieved from a dumpster, an attacker could gain access to sensitive network configurations and use this information for malicious purposes. Conclusion Deploying physical security solutions involves more than just securing buildings and assets; it also requires robust measures to protect against cybersecurity threats. From assessing vendors and understanding update policies to configuring devices securely and managing decommissioning processes, each step presents potential pitfalls that, if overlooked, could expose organisations to significant risks. By incorporating the techniques discussed into their deployment protocols, organisations can ensure their physical security solutions provide comprehensive physical and digital protection.
Rapid technological advancement, artificial intelligence (AI) and machine learning (ML) are revolutionising traditional on-premises video security systems. These next-level tools are not just enhancing video data capabilities; they're transforming how businesses approach security, operational efficiency, and information analysis. Video analytics have been a part of security systems for many years, but the arrival of deep learning in 2009 marked a turning point. By training neural networks, basic analytics tasks like motion detection, object detection, and tracking objects within scenes have become commonplace. This leap forward has paved the way for more sophisticated AI and ML applications in video security. Proactive security measures AI-powered systems can perform complex tasks such as pose estimation and anomaly detection Today's AI-powered systems can perform complex tasks such as pose estimation, anomaly detection, and behaviour analysis. These capabilities extend far beyond simple, passive monitoring, offering organisations rich insights and proactive security measures. For instance, analytics can now determine whether people are engaged in hostile or benign interactions, recognise unusual events that may signal safety hazards, and even predict potential security breaches before they occur — all based on analysing massive amounts of data that humans alone could never process. Enhancing on-premises infrastructure While the power of AI and ML in video security is clear, integrating these technologies into existing on-premises systems presents both opportunities and challenges. One of the primary considerations is the increased demand for processing power and storage capacity. As solution technology expands, hardware requirements will increase. This reality necessitates a strategic approach to system design and implementation. Organisations must carefully evaluate their current infrastructure and plan for future needs to ensure their on-premises systems can handle the computational demands of AI and ML tools. However, the benefits often outweigh the challenges. AI-enhanced on-premises systems offer several advantages: Real-time processing: On-premises AI can analyse video feeds in real time, allowing for immediate response to security threats. Data privacy: Keeping data processing on-site can help organisations meet strict data privacy regulations and protect sensitive information. Customisation: On-premises systems allow for greater customisation of AI models to meet specific security needs. Reduced latency: Processing data locally eliminates the need for constant cloud communication, reducing latency in critical security applications. The role of open platform video technology To fully leverage AI and ML capabilities in on-premises video security systems, open-platform video management software (VMS) plays a crucial role. An open platform VMS allows for seamless integration of various AI and ML tools, cameras, and other security devices, creating a highly flexible and scalable system. An open VMS can integrate thousands of cameras and sensors, allowing for centralised management and analysis of vast amounts of data. This approach enables security teams to quickly adapt to new threats and implement new and unplanned AI and ML solutions as they become available. Video system management The hybrid approach to video system management combines on-premises infrastructure with cloud services It's important to note that many organisations choose to deploy a hybrid approach to video system management that combines on-premises infrastructure with cloud services. This strategy can offer the best of both worlds: the control and low latency of on-premises systems with the scalability and advanced capabilities of cloud-based AI and ML tools. For example, some cities have implemented hybrid data storage models, hosting critical real-time data on local servers while leveraging cloud services for long-term storage and advanced analytics. This approach allows for efficient management of large amounts of high-resolution video data while reducing costs associated with on-premises storage expansion. Practical applications and benefits The integration of AI and ML into on-premises video security systems is transforming security practices across industries, offering benefits that extend beyond traditional surveillance. These advanced technologies enhance security measures while providing valuable insights for operational efficiency and strategic decision-making. By analysing video data in real time, AI and ML-powered systems can detect patterns and automate responses in unprecedented ways. Here are some key examples of sector-specific benefits: Retail: AI-powered analytics can optimise product placement, track shopping patterns, and enhance loss prevention efforts. Education: K-12 schools can use advanced video analysis to address issues like vaping and bullying, monitor traffic, ensure that proper procedures are followed, and provide enhanced safety and security. Manufacturing: AI can streamline quality control processes, detect safety violations, and optimise production line efficiency. Healthcare: Intelligent video systems can monitor patient safety, manage access control, and even assist in documenting and verifying that procedures and protocols are followed appropriately. Transportation: AI-enhanced video systems can improve traffic management, enhance security in transit hubs, and assist in incident response. Challenges and considerations Ensuring access to robust, diverse, and representative data sets is essential for training AI models effectively AI and ML hold great promise for on-premises video security, but organisations may encounter challenges during implementation. The considerable upfront costs could discourage smaller businesses or those with tight budgets. Nevertheless, this should be viewed as a long-term investment with significant returns in enhanced security and operational efficiency. Implementing AI-powered systems in video security can be complex, often requiring specialised skills, potentially creating a gap within existing IT or security teams. To bridge this skills gap, organisations may need to invest in training or partner with external experts to address this challenge. Additionally, the quality of data is crucial for effective AI and ML implementation; poor or insufficient data can result in inaccurate analyses and unreliable results. Ensuring access to robust, diverse, and representative data sets is essential for training AI models effectively. Benefits of integrating AI and ML Ethical considerations surrounding privacy, consent, and potential algorithmic bias are also critical. Organisations must strike a balance between enhancing security and safeguarding individual privacy rights to maintain public trust in these technologies. Despite these challenges, the benefits of integrating AI and ML into on-premises video security systems often outweigh the difficulties. Careful planning, resource investment, and a strong focus on ethical and regulatory compliance can lead to more effective, efficient, and intelligent security solutions. Future outlook Edge computing capabilities will enable sophisticated AI processing directly on cameras The future of AI and ML in on-premises video security promises significant advancements that will address current limitations and unlock new possibilities. Edge computing capabilities will enable sophisticated AI processing directly on cameras and other security devices, reducing strain on central servers and potentially lowering hardware requirements. This, combined with more efficient AI algorithms, will democratise access to advanced AI and ML capabilities for organisations of all sizes. AI-powered analytics Predictive analytics will become a cornerstone of future video security systems, marking a shift from reactive to proactive security measures. As AI models become more sophisticated, their ability to anticipate and prevent security incidents will improve dramatically, revolutionising risk management and incident response. The integration between video security and other business systems will deepen, with AI-powered analytics providing insights beyond security into business operations and strategic decision-making. Data for training AI models Explainable AI will become more overall, which is vital for building trust in automated systems Automation of security processes will reach new heights, freeing human operators to focus on high-level decision-making and complex situations. To support this evolution, we'll likely see increased use of synthetic data for training AI models, addressing privacy concerns, and improving model robustness. Explainable AI will become more prevalent, which is crucial for building trust in automated systems and meeting regulatory requirements. For security professionals, embracing these technologies is no longer optional but necessary to remain competitive and provide the best possible service to clients. By leveraging open platform VMS and carefully planning system architectures, organisations can create flexible, scalable, and powerful video security solutions that not only protect assets but also drive business value. Enhanced video security systems The key to success will be finding the right balance between on-premises control and cloud-based capabilities while addressing important considerations around privacy, ethics, and regulatory compliance. With thoughtful implementation and ongoing adaptation, AI and ML-enhanced video security systems will continue to play an increasingly central role in safeguarding our businesses, institutions, and communities.
As part of ever-evolving technological advancements and the increase in digitisation, home security systems remain a vital piece of equipment for at least 39 million households in the U.S., and as many as 13 million more households may install new security systems in the next 12 months. Global home security market In addition, a recent study found that 60% of burglars are deterred from attempting a burglary when a home has a security system, looking for alternative targets that are easier. Another similar study found homes without security systems are 300% more likely to experience a burglary. It’s estimated the global home security market is expected to grow to $84.4 billion as more and more people install home security systems as a way to ensure their safety. High-tech security devices Home security systems and the technology behind them will continue to expand and integrate further With the ongoing need for home security systems and the introduction of technology such as Artificial Intelligence (AI), home security companies are finding new and innovative ways to improve the home security experience by installing high-tech security devices. These devices are changing how we protect our homes, valuables, families, pets, and more. As we look ahead to the future, home security systems and the technology behind them will continue to expand and integrate further within the home as AI evolves and takes on a more meaningful and deeper role in the home security industry. Features of AI-based home security systems Most home security systems already use AI regularly for features like smart cameras, motion sensors, and alarms. These offerings incorporate AI to detect and respond to potential security threats, differentiating between everyday activities and potential suspicious behaviour and then alerting homeowners based on the activity. As AI expands the capabilities of critical security features such as facial recognition, voice control connectivity, and enhanced video capabilities, it will significantly improve the traditional security systems we use today, providing additional means of not only protecting homes but also streamlining the overall home security system. Future advancements in AI home security systems Increased integration of security devices through AI As AI continues to evolve, we can expect to see increased integration and connectivity of devices included in a home security system and home – all powered by AI. This includes hardware such as cameras, motion detectors, keypads, sensors, and smart locks, as well as software, such as digital apps. This increased connectivity will not only make it easier for homeowners to manage their security system but also to customise their home and home security to meet their evolving needs. Voice control connectivity The new hands-free approach to home security enhances the user experience and opens up new possibilities Voice control connectivity is yet another key feature that is gaining popularity in AI-powered home security systems. Security system users can control and monitor their security systems using voice commands similar to how Amazon’s Alexa works, making security systems more convenient and user-friendly. The new hands-free approach to home security not only enhances the user experience but also opens up new possibilities for seamless integration with other smart home devices and mobile devices. AI will help personalise and individualise security settings Relying more heavily on facial recognition technology, AI algorithms integrated into home security systems will become more personalised and tailored to individual users based on their preferences. Imagine a security system that recognises each member of your family and adjusts its settings and alerts based on each user’s unique preferences and habits. Thanks to facial recognition improvements in recent years, this new level of customisation will enhance security and improve the ease of use, making home security more intuitive and user-friendly. By incorporating personalisation via AI into home security systems, simple tasks like disarming the system when returning home or arming the system before going to bed at night will be much more efficient, and security settings will be saved based on each user’s preferences. AI will analyse threats before they become emergencies AI-powered automation will play a heightened role in the future of home security systems as it learns to proactively analyse and respond to potential threats, security breaches, and emergencies like fires or carbon monoxide leaks. Through real-time monitoring, AI will begin to predict and prevent security breaches before they occur, working efficiently with human counterparts for an effective approach to security monitoring. Security monitoring AI linked to a carbon monoxide detector may notice the levels rising before they reach a dangerous level For example, through camera monitoring, AI will learn how to tell the difference between normal and suspicious activities, automatically adjusting your security settings and alerting you of a potential risk. Similarly, AI linked to a carbon monoxide detector may notice the levels rising before they reach a dangerous level and alert the security system user and monitoring service in advance. The AI evolution of home security The traditional idea of home security systems, with physical locks, keypads, and alarms, is rapidly changing into a more intelligent system powered by AI. Just as the cell phone industry revolutionised communication by making phones constantly accessible to us all, AI is on the cusp of transforming our home security systems into a much safer and more user-friendly experience. Shortly, we’ll see a world where every aspect of home security systems is easily accessible on one or multiple devices within the home or even on mobile devices, boosted by the help of AI. From keyless entry systems that recognise our faces to AI assistants that communicate with us and adjust settings based on our preferences, the possibilities are truly endless. A safer, smarter, and more secure future As AI continues to advance and becomes more integrated into home security systems and life in general, the future will bring enhanced safety, security, convenience, and peace of mind for homeowners. As we move towards a future where AI plays a larger role in our daily lives, we can expect to see a shift in the way we think about and approach home security systems – in fact, it’s already happening. The traditional security setup of the past is being replaced by a new era of intelligent, interconnected, and proactive home security systems that work seamlessly. With AI as our ally and incorporated into our home security systems, we can look forward to a safer, smarter, and more secure future for our communities, homes, and loved ones.
Security beat
The information age is changing. Today, we are at the center of addressing one of the most critical issues in the digital age: the misinformation age. While most awareness of this problem has emerged in the consumer and political worlds, the issue cannot be ignored when it comes to the authenticity and protection of video and security data. Video surveillance data SWEAR is a company with the mission to ensure the integrity of video surveillance data by mapping video data and writing it into the blockchain, providing real-time, immutable proof of authenticity. Blockchain, which is the underlying technology that enables cryptocurrencies, is a decentralised digital ledger that securely stores records across a network of computers in a way that is transparent, immutable, and resistant to tampering. SWEAR solution The SWEAR solution is based on proactive, foundational protection that validates data at the source The SWEAR solution is based on proactive, foundational protection that validates data at the source before any opportunity for manipulation can occur. “Our technology is about proving what’s real and our goal is to ensure that security content and video surveillance data remain untampered with and reliable when needed,” says Jason Crawforth, Founder and CEO of SWEAR. Real-time authentication Security leaders need to ensure that the content they are relying on to make mission-critical decisions is authentic. Once verified, organisations can be sure that their investment in video can be trusted for critical use cases, including intelligence operations, legal investigations, and enterprise-scale security strategies. SWEAR seeks to embed trust and authenticity directly into video surveillance content at the point of creation. This ensures real-time authentication while proactively preventing tampering or manipulation before it can happen. AI-generated content The rise of AI-generated content, such as deepfakes, introduces significant challenges As AI transforms the landscape of video surveillance by enhancing threat detection and predictive analysis, it also introduces the very real risk of manipulation through AI-generated content. This presents a significant challenge in protecting critical security data, especially in mission-critical applications. The rise of AI-generated content, such as deepfakes, introduces significant challenges when it comes to ensuring the protection of digital media like video surveillance. Recent study findings It is a fact that digital media content is being questioned more regularly, which puts businesses, legal systems, and public trust at risk. A recent study from the Pew Research Center found that 63 percent of Americans believe altered videos and images create significant confusion about the facts of current issues. Last month, California Governor Gavin Newsom signed three bills aimed at curbing the use of AI to create fake images or videos in political ads ahead of the 2024 election. Footage authenticity “While most of the news cycle has centered on the use of fake content in politics, we need to think about how manipulated videos could affect security,” says Crawforth. “In video surveillance, ensuring the authenticity of footage is critical for keeping operations secure and safe around the world. That means verifying and protecting video data is a must.” Organisations must be capable of performing thorough digital investigations, which involve retrieving and analysing video and security data from devices and networks through a chain of evidence. Digital forensic capabilities Strong digital forensic capabilities also enhance incident response, risk management, and proactive security An in-depth understanding of who has handled video data, how it was handled, and where it has been is an important step in responding to security incidents, safeguarding assets, and protecting critical infrastructure. Strong digital forensic capabilities also enhance incident response, risk management, and proactive security measures, all essential for risk management, regulatory compliance, and cost control, says Crawforth. An unbroken chain of custody “By using tools to identify, preserve, and analyse digital evidence, organisations can ensure swift and accurate responses to security incidents,” he adds. “Using the latest tools and techniques is vital for maintaining a strong security posture." "But you must ensure your digital content isn’t manipulated.” SWEAR’s technology provides an unbroken chain of custody, ensuring that video evidence can be trusted and admissible in court and forensic applications. Authenticating content Authenticating content also strengthens accountability and trust, protecting organisations By verifying video content is protected from tampering, manipulation, or forgery, organisations can be sure that they have reliable evidence that produces actionable results. Authenticating content also strengthens accountability and trust, protecting organisations from legal disputes or compliance violations. Safeguarding digital content “With an increasing amount of disinformation in today’s world, we sought to develop an innovative solution to safeguard the integrity of digital content,” says Crawforth. SWEAR safeguards security content using real-time “digital DNA” encoding. It integrates directly at the video management system level, ensuring it is preserved with a secure chain of custody and maintains integrity for evidentiary purposes. Real-time “digital DNA” encoding The digital DNA is then stored on a blockchain, creating an immutable record The solution integrates with cameras and other recording devices to map this digital DNA of the video data, all in real-time. The digital DNA is then stored on a blockchain, creating an immutable record that tracks the content’s history and integrity. Any attempt to manipulate the media can be instantly detected by comparing the current state of the media to its original, authenticated version. SWEAR is actively collaborating with video management solution providers to integrate the technology into their platforms. Video and security data benefits “We’re still in the early stages of our collaboration in this space, but it is clear that the industry recognises that we have to work together to mitigate this risk proactively before it becomes a significant issue,” says Crawforth. “The feedback we have received from the industry to date has been beyond our expectations, and we expect to have more integration partners to highlight shortly.” “We should approach this as a collaborative effort across the industry, as ensuring the authenticity of video and security data benefits everyone involved,” says Crawforth.
Security applications for drones have evolved to provide benefits such as bird's-eye views of large areas, easy access to remote locations, and rapid deployment. However, to date, most drone applications have been outdoors. Not for long. Today, indoor drones are also finding unique opportunities for enhanced surveillance, security, and operational efficiency in indoor environments such as offices, warehouses, self-storage facilities, and malls. Indoor drones can navigate complex indoor spaces, providing real-time data and monitoring without the limitations of fixed cameras. New era of autonomous robotics A significant advantage of using drones indoors, as opposed to outdoors, is their ability to operate fully autonomously, circumventing U.S. Federal Aviation Administration (FAA) regulations that restrict such autonomy in outdoor environments. A new era of autonomous robotics enables drones to work seamlessly for users without the need for specialised flight training. A single security manager can oversee multiple indoor drones simultaneously with simple map clicks or prompts. A new era of autonomous robotics enables drones to work seamlessly for users Indoor monitoring and inspection Indoor Robotics is a company seeking to revolutionise indoor monitoring and inspection through its Control Bridge platform guiding indoor drones. Since its founding in 2018, Indoor Robotics has evolved through years of market engagement and product development. After initially recognising a demand for autonomous indoor monitoring, the company found that existing hardware fell short. “However, we understood the challenges of full autonomy and knew we would solve it using drones,” says Bar Biton, Marketing Manager of Indoor Robotics. Indoor Robotics has evolved through years of market engagement and product development Hardware challenges Seven years later, with the hardware challenges addressed, the company is shifting focus to continually increasing value for security managers, especially with generative AI (artificial intelligence). In 2018, the problem was charging methods, which has been solved with ceiling docking stations and five patents. “Today it’s about making indoor environments safer and even saving lives by identifying blocked emergency exits, missing safety gear, leaks, fire hazards and more,” says Biton. While indoor navigation presents challenges—such as the unreliability of GPS and the need for precision — Indoor Robotics has dedicated significant resources to achieve centimeter-level accuracy and ensure the utmost safety, maintaining a record of zero safety incidents to date, says Biton. Indoor navigation presents challenges—such as the unreliability of GPS and the need for precision Advanced AI-driven navigation systems Navigation challenges for indoor drones include manoeuvering through confined spaces, avoiding obstacles, and maintaining stable flight in varied lighting conditions. To address these, Indoor Robotics employs advanced AI-driven navigation systems, real-time 3D mapping, and robust obstacle avoidance technologies. These solutions enable drones to adapt to dynamic environments, ensuring precise and safe navigation. Additionally, the Control Bridge platform provides real-time data and monitoring, allowing drones to adjust their routes and respond to changing conditions effectively, thus enhancing their operational reliability. Highly versatile indoor drones find applications across numerous vertical markets such as retail, logistics, healthcare, and corporate settings. Key use cases encompass security surveillance, where drones monitor premises continuously; maintenance checks, especially in hard-to-reach areas; safety inspections to comply with regulations and company policies; and emergency response to provide real-time data during incidents. In warehouses, drones efficiently inspect high shelves. Healthcare facilities and data centres use them to oversee restricted zones. Additionally, corporate offices employ drones to automate after-hours security, safety and maintenance routines. Indoor Robotics employs advanced AI-driven navigation systems, real-time 3D mapping, and robust obstacle-avoidance technologies Alerts to the remote management team One Indoor Robotics client, a global tech company, deploys drones to enhance site surveillance and operational efficiency across six offices in three countries. The drones conduct regular security patrols after-hours, monitor facility activities, and ensure compliance with safety standards. This deployment has significantly improved the overall safety and security of their offices. The drones provide real-time alerts to the remote management team, enabling prompt responses to any anomalies, such as maintenance issues or unauthorised access. “The key advantage is the unified security standard provided by our Control Bridge operating system, allowing them to oversee all their sites from one centralised platform, ensuring consistent security management across all locations,” says Biton. When indoor drones co-exist with human workers, primary challenges include ensuring safety and preventing disruptions. Drones are equipped with advanced sensors and AI-driven obstacle avoidance systems to detect and navigate effectively around people. Strict operational protocols and designated flight paths are implemented to minimise interactions. Additionally, many drone operations are scheduled for after-hours to further reduce potential disruptions. “Safety is our top priority, and we invest significant resources to ensure it,” says Biton. “We are proud to report zero safety issues to date, reflecting our commitment to maintaining a secure environment for both drones and human workers.” Deploys drones to enhance site surveillance and operational efficiency across six offices in three countries Implementation of indoor drones Indoor drones are significantly more cost-effective and affordable when compared to traditional security methods like additional cameras, sensors, manpower, and even ground robots, says Biton. They cover larger areas and provide dynamic surveillance in less time, offering real-time data collection and enhanced flexibility. Unlike cameras or ground robots, drones eliminate blind spots and adapt to environmental changes autonomously. They also offer substantial indirect savings by optimising maintenance routines, according to Indoor Robotics. For instance, a drone can instantly identify issues in hard-to-reach areas, allowing for immediate, targeted responses, instead of requiring an inspector first and then a technician, thus streamlining maintenance processes. “The biggest obstacle to greater implementation of indoor drones is education and awareness,” says Biton. “Many people are not yet exposed to the concept of autonomous indoor drones and may find it hard to believe they really work.” To overcome this, Indoor Robotics focuses on creating awareness and educating customers about the reliability and benefits of the technology. Demonstrations, case studies, and clear communication about the capabilities and safety of drones are key. By showcasing successful implementations and providing hands-on experiences, Indoor Robotics seeks to build trust and drive wider adoption of indoor drone technology in security applications. Control Bridge operating system Drones are designed with strict privacy controls and advanced AI to ensure they respect privacy norms A common misconception is that indoor drones are intrusive and pose significant privacy risks. However, drones are designed with strict privacy controls and advanced AI to ensure they respect privacy norms. They operate primarily during off-hours and are programmed to avoid sensitive areas, focusing solely on enhancing security and operational efficiency. The solution also includes rigorous data protection measures to safeguard any collected information, ensuring compliance with privacy regulations and addressing concerns effectively. Soon, automation will become integral to tasks across all facility types, from manufacturing and logistics to retail and office spaces. Using Indoor Robotics’ Control Bridge operating system, facility managers will deploy fleets of robots to identify issues, collect data, and gain insights to enhance operations, maintenance, and safety. Facilities will benefit from 24/7 AI-driven monitoring, eliminating the need for occasional surveys. Managers will receive immediate alerts for any anomalies, with preventive maintenance tasks seamlessly integrated into building management platforms, ensuring optimal performance and safety. New standards in the industry The Indoor Robotics platform-agnostic approach provides flexibility and scalability. “As we continue to evolve, we support more and more platforms, enabling our clients to tailor their indoor monitoring solutions to their specific needs,” says Biton. “We believe that the future of security lies in intelligent, automated systems that can adapt to dynamic environments and provide real-time insights,” says Biton. Indoor Robotics seeks to be at the forefront of this transformation, setting new standards in the industry and paving the way for a safer, more efficient future.
In an emergency, information is pivotal. More information provides better understanding of an emergency and empowers potentially life-saving decision-making. Emergency response teams depend on information to guide their efforts and to deliver targeted assistance. On the front lines of emergency response are 911 and field responder agencies, which must direct reaction to life-or-death situations rapidly and efficiently. Historically, 911 operators had to respond based on very little information, perhaps just a voice on the phone or a location on their screen. Providing critical information Today, there are literally millions of information sources available, ranging from connected buildings to vehicle telematics to live video streams to health information from wearable devices. In fact, there are 540 million connected devices, any one of which could provide critical information in an emergency. But how can those information sources be leveraged to improve emergency response? That’s the mission and value proposition of RapidSOS, an ‘intelligent safety platform’ company that connects 911 operators with the vast universe of information available to promote better and faster emergency response. Highly sophisticated operation The platform is integrated into every major public safety software system and first responder agency “RapidSOS fuses human and artificial intelligence to put critical information from any connected device directly into the existing systems and operating procedures of first responders across the United States,” says Michael Martin, CEO of RapidSOS. RapidSOS is widely used by first responders. The platform is integrated into every major public safety software system and first responder agency. There are more than 4,600 software integrations that serve more than 21,000 first responders and 911 agencies. In 2023, RapidSOS supported the lifesaving work of public safety across 171 million emergencies with 3.3 billion data payloads. The system is adaptable and configurable to support any agency, from a highly sophisticated operation in New York City to a local sheriff running their own 911 center. Intelligent analytics and reporting RapidSOS Unite is the latest evolution of the product, a single solution that includes AI automation, rich content pathways, redundant connection to caller phones, and access to millions of connected devices. In an emergency, Unite intelligently fuses data from among millions of sensor feeds into a unified picture of an incident, allowing public safety officials to view real-time location, health profile, telematics, alarm data, and more. RapidSOS Unite is the latest evolution of the product, a single solution that includes AI automation RapidSOS offers core modules that handle call, text, video, sensor, mapping, and administration tools, and that provide partner data from connected devices. Additional modules provide enhanced geographic information system (GIS) data, and automated translation and transcription. There is also a single sign-on (SSO) upgrade, intelligent analytics and reporting, and seamless integration into field responder applications. Field responder applications Consider how an emergency might unfold and how RapidSOS can help. In a car accident, data from a modern automobile telematics system can alert a 911 operator of the accident as it happens. Data from a passenger’s wearable device might provide information about their health and condition. A nearby video or traffic camera could fill in details of how the accident occurred. Useful information in an emergency might come from any one of thousands of sources, including public safety data, sensor feeds, enterprise security systems, smart phones, etc. In a train derailment, electronic access to the cargo manifest can identify which train cars contain hazardous materials and how to manage the specific type of hazmat. This information could save valuable time when responding to incidents like the Feb. 3, 2023, Norfolk Southern train derailment involving 38 cars in East Palestine, Ohio. Consider how an emergency might unfold and how RapidSOS can help Institutional security partners Norfolk Southern is one of the companies that provides information to first responders using RapidSOS; in effect, the company provides a direct digital link from their rail security operations to any first responder in the United States. Amazon’s global operations centers also interface with RapidSOS to provide critical information to first responders. Partnering with corporate security helps to better support the flow of data from institutional security partners and their solutions. Information can transform and guide emergency responses. For example, in a structure fire, real-time sensor feeds throughout a building can help 911 and first responders understand how the fire is progressing. Real-time security camera footage Having access to live feeds can save lives as 911 provides pre-arrival instructions such as CPR Leading the way to providing video feeds from private camera systems to 911 operators is an agreement between Eagle Eye Networks and RapidSOS, which was announced in April 2024. The agreement allows an enterprise to opt-in to share real-time security camera footage from an Eagle Eye video stream during a live 911 call. Having access to live feeds can save lives as 911 provides pre-arrival instructions such as CPR. “Security cameras are crucial in many locations, including schools, but previously those cameras could not be accessed by 911 during an emergency but were only used for investigation after an incident,” says Martin. Improving fire and life safety systems RapidSOS is also integrated with Honeywell’s Connected Life Safety Services (CLSS) system, a cloud platform that combines software and hardware to improve fire and life safety systems. Technology integrations between the two companies further modernise and digitise the public safety communications process to provide faster, more accurate communications with emergency centers (i.e., 911 agencies). RapidSOS technology securely transmits detailed data about an emergency CLSS provides real-time visibility and connectivity to help systems integrators and facilities managers make informed decisions and manage fire systems more efficiently. When combined with Honeywell's solutions, RapidSOS technology securely transmits detailed data about an emergency, such as the type of hazard, severity, and location within the impacted building, to emergency response centers. Video object detection Rapid SOS’s emerging Harmony artificial intelligence (AI) product serves as a ‘co-pilot’ for 911 operators, helping them manage the high volume of emergencies by making their response more efficient. Harmony pulls all the sensor feeds in an emergency and works to make only the most important information available in the hands of 911 and first responders. Harmony can take key insights from text and video data, use ‘sentiment analysis’ to determine the emotion tone of a message, and help 911 professionals using language translation, keyword alerts and video object detection. Harmony can help local agencies as they address a 25% average staffing shortage by providing additional support to 911 professionals while lessening the workload. Harmony is also working to help RapidSOS expand the ecosystem, stitching more data together and quickly making it more actionable than ever. Emergency response system RapidSOS also interfaces with Iamresponding, a comprehensive end-to-end emergency response system for first responders in the fire and other emergency sectors. Iamresponding’s field responder application is used by RapidSOS to get information out to first responders in the field. More than 650,000 first responders use RapidSOS’s field application RapidSOS’s recent acquisition of Iamresponding helps the company improve the connection with the last mile “in-the-field” piece of the puzzle, ensuring partners across computer-aided dispatch (CAD), integrated applications, mobile data terminals, body cameras and other responders have access to critical data. More than 650,000 first responders use RapidSOS’s field application. Enhancing emergency response RapidSOS’s Safety Pioneer Program formalises the important partnership between RapidSOS and public safety agencies. Participants in the program receive early access to new platform features, contribute to the platform roadmap, and drive feedback to enhance emergency response. “911 and first responders do incredible lifesaving work,” says Martin. “Everything we have done and built at RapidSOS is a direct result of the engagement, partnerships, inside advice and insight we have gotten from public safety. We have learned from them, developed new technologies and tested them.” Martin adds: “Companies have data and we now know how to make that data actionable into the hands of 911 and first responders to save lives. This is an exciting moment for us continuing our mission in partnership with public safety, and for technology and security companies to have a major hand in that.” {##Poll1719488782 - What is the most valuable benefit of artificial intelligence (AI) in an emergency call center?##}
Case studies
ZeroEyes, the creators of the only AI-based gun detection video analytics platform that holds the full US Department of Homeland Security SAFETY Act Designation, announces that its solution has been deployed by Michigan’s Williamston Community Schools to protect students, staff and visitors from gun-related violence. Centered in Williamston, the district educates over 2,000 students from Williamstown, Locke, Leroy, Wheatfield, Alaiedon and Meridian townships. It comprises five schools: a preschool, two elementary schools, a middle school and a high school. Layered security measures ZeroEyes will complement the schools' existing layered security measures, which include secure vestibules, a school resource officer (SRO) and a full-time firearm detection dog team, alongside proactive mental health programs such as “Prevent to Protect”, which helps students who are at high risk of committing suicide or violent acts towards others. “ZeroEyes is an important layer of security that complements the efforts that have already been put in place in the district,” said Adam Spina, Superintendent of Williamston Community Schools. “Our security layers combine to create a significantly safer school day for our students and staff.” Intelligent situational awareness If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence ZeroEyes' AI gun detection and intelligent situational awareness software layers onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Center (ZOC), the industry’s only U.S.-based, fully in-house operation center, which is staffed 24/7/365 by specially trained military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and school staff as quickly as 3 to 5 seconds from detection. Improving student safety As a result of Michigan Public Act 103 (PA 103), Williamston Community Schools received a grant specifically dedicated to procuring AI gun detection software to improve student safety. "The extensive security protocols and systems of Williamston Community Schools reflects the districts’ commitment to keeping students and staff safe from gun-related violence," said Mike Lahiff, CEO and co-founder of ZeroEyes. "The support of Michigan’s legislative grant program enabled us to provide proactive gun detection to a number of districts throughout the state. We encourage policymakers to expand the program in 2025 to help protect more schools.”
The Buffalo and Erie County Naval & Military Park, in Buffalo, N.Y., has a clear mission based on four pillars: to honour all veterans, educate the public about the sacrifices made by those who serve, inspire a sense of patriotism and appreciation for those protecting Americans’ rights and freedoms, and preserve the artifacts entrusted to the Park’s care. Buffalo Park The Park regularly hosts events and takes visitors inside America’s military history with in-depth tours of decommissioned naval vessels, exhibits, and displays. The team’s goal is to highlight its monuments and artifacts while providing a welcoming and secure environment for visitors. A key challenge was the Park’s large open and unfenced grounds, allowing the public access to the facilities at any time of the day or night. Challenge Provide a welcoming and secure environment for visitors and deter criminal activity within the park. Achieve 360° coverage across all interior and exterior areas without using cables, which would have made the project cost-prohibitive. Design a wireless surveillance system to cover the park’s large areas of open ground. Surveillance system installation “We had begun to notice an increased rate of delinquent incidents happening during the day and off hours, including graffiti placed on the artifacts and monuments,” said Paul Marzello, Sr., President & CEO, Buffalo and Erie County Naval & Military Park. The Park engaged Mario Rodriguez, president of Forseti Protection Group, and Erik Schiefer, account executive at Seibold Security, to design and install a surveillance system based on Hanwha Vision’s multi-directional and AI-equipped cameras. “When we did our research, we found that Hanwha Vision certainly was a pioneer in the industry,” said Marzello. Factors to consider From a risk and public safety perspective, the goal from the start was to maintain an open and welcoming environment “We conducted a site survey, considering the line of sight, the cameras’ capabilities, the density of groups of visitors and where they tend to gravitate, and criminal history in the Park,” said Bill Abbott, Director of Operations, Buffalo and Erie County Naval & Military Park. “Those were all factors in how we determined the layout. We wanted to make sure that we had the right coverage.” From a risk and public safety perspective, the goal from the start was maintaining an open and welcoming environment while keeping public safety top-of-mind. Solution Install a Hanwha Vision surveillance system comprising multidirectional and AI cameras. 4K multi-sensor cameras Schiefer has extensive experience with Hanwha cameras from previous projects. “Their new 4K multi-sensor cameras are first class and as far as 360° coverage, with the ability to monitor several areas, Hanwha was the first choice,” he said. The ability to view 360° coverage from one camera that essentially is divided into multiple sectors was significant. “That gives us full visibility and lets us be open and welcoming while keeping out of the public’s way without being imposing or intimidating,” Rodriguez said. Ease of playback Schiefer added that one key benefit of using the Hanwha 360° cameras to cover such a large area Schiefer added that one key benefit of using the Hanwha 360° cameras to cover such a large area is the ease of playing back footage and monitoring activity after the fact. “They are broken out into four sensors, so you don’t necessarily have to go back and look through a large amount of footage,” he said. “You can pick the area you're looking for, go directly to that sensor within the camera that we have in that area, and you can pull footage much easier that way.” Cable cost and distance One challenge the team encountered during the design phase was running a cable for a project of this scale. “The cost to run buried cable at such long distances with switches would have rendered this project almost completely impossible,” Schiefer said. “We incorporated wireless network cards into the poles around the park and all the cameras feed directly back to the Hanwha NVR without using any sort of cabling.” NDAA compliant solutions The Park’s priorities included the use of National Defense Authorization Act (NDAA) compliant solutions and having more streamlined communication with law enforcement. “We wanted to make sure that the cameras themselves were secure,” said Abbott. “The cameras also needed to be used to positively identify someone who had done something, either damage or acts of violence. In the past, we could not effectively supply law enforcement with usable information to identify a suspect." Use of AI in cameras The Hanwha cameras’ use of AI plays a key role in delivering those capabilities "We've now changed that with the quality of cameras that we're using. We can share footage and data to produce an outcome that's satisfying to everybody as far as finding a culprit and holding them accountable." The Hanwha cameras’ use of AI plays a key role in delivering those capabilities. “You can use key identifiers, whether it's the colour of someone's shirt, if they're wearing a backpack, or there's some physical feature that we can then go through and locate that person through the system,” Abbott said. Sense of security “We absolutely would see an increase in the value and number of cameras that we use,” said Abbott. Marzello added, “From an operations standpoint, we feel a greater sense of security knowing the cameras are there and will help us identify activities that we can hopefully prevent. This system meets our needs today and will also be able to grow with us.” Results Ability to effectively monitor all park areas and more effective forensic searches. Reduction in on-premise incidents. Streamlined collaboration with law enforcement agencies.
Windsor Port Authority, one of just 17 national ports created by the 1999 Canada Marine Act, has enhanced waterway safety and security across its jurisdiction on the U.S.-Canada border with state-of-the-art cameras from Axis Communications. These cameras, combined with radar solutions from Accipiter Radar Technologies Inc., provide the port with the visibility needed to prevent collisions, better detect illegal activity, and save lives along the river. Windsor Port Located on the Detroit River, the Windsor Port serves as the passageway between Lake Huron and Lake Erie, navigating between 6,000 and 9,000 cargo vessels annually. In addition to commercial ships, over 10,000 small fishing boats and other recreational watercraft make their way through the port each year. Better visibility Windsor Port Authority realised that it needed better visibility into happenings along the river With so many vessels passing through, Windsor Port Authority realised that it needed better visibility into happenings along the river to be able to keep the waterway running safely and smoothly. “Axis’ cameras, along with Accipiter’s radar technology, have been vital to keeping the port safe for all who pass through it,” said Peter Berry, Harbour Master and Vice President of Operations for Windsor Port Authority. Real-time incident detection “Without detailed knowledge of the traffic in these waters, the risk of severe accidents increases significantly, so having the ability to both detect and visually confirm incidents in real-time is invaluable." "We’ve already been able to do some amazing things with the enhanced surveillance solution, like quickly rescuing drowning victims and helping to catch human smugglers, and we’re eager to see what the future holds as a result of this upgrade.” An effective, remote observation By integrating Axis’ bispectral cameras into Accipiter's platform, the port has a 360-degree surveillance system While radar coverage from Accipiter has monitored river activity for years, offering wide-area, real-time detection, and tracking to identify commercial vessels, small craft such as jet skiers, and even debris in the water, it lacked the visual detail needed to provide effective, remote observation. By integrating Axis’ bispectral cameras into Accipiter's platform, the port has a 360-degree surveillance system with both thermal detection and visual verification. System benefits With this enhanced system, the port can: Broadcast real-time warnings about obstructions in the channel: In one instance, the U.S. Coast Guard notified the port that they’d spotted a boat stopped in the middle of the river. The vessel had caught fire, dropped anchor, and was dead in the water. The thermal camera and radar technology allowed for continuous monitoring of the fire onboard the ship, helping them to determine that it was contained to the engine room while enabling the port to send out a navigational warning to other vessels on the river. While the darkness of the hour prevented them from seeing anything from shore, the technology also provided thermal visuals to monitor activity on the bridge and deck. Everyone was safely evacuated. Safely navigate craft through high-risk construction projects: During the construction of a new bridge, the port was concerned about potential disruptions to river traffic, but Axis cameras and integrated radars allowed them to effectively manage vessels passing underneath the site. Deliver precise coordinates for faster rescue operations: When the port got a call from the U.S. Coast Guard that they had spotted a person treading water by the Ambassador Bridge, they were able to quickly identify the location of the person using a combination of radar and camera technology and execute a life-saving rescue. Help to identify criminal activity: While using the camera-radar technology to view objects crossing from Canada to the U.S., the port identified suspicious activity from a boat that regularly sailed from Windsor to Detroit. The port turned the data and video over to the Canadian and U.S. authorities to investigate, which ultimately led to the arrest of two individuals running a human smuggling operation. Marine domain awareness “At Axis, we take pride in working with organisations like Windsor Port Authority to contribute to improved marine domain awareness and heightened safety along the border,” said Anthony Incorvati, Transportation Segment Development Manager for the Americas at Axis. “Combining advanced camera and radar technology ensures comprehensive visibility in maritime environments, providing essential detection and visual verification to resolve incidents quickly and effectively. Not only that, but powerful business intelligence capabilities contribute to improved operations across the organisation.”
Newport, a popular vacation destination, has partnered with Sorama to tackle growing noise pollution. By integrating AI technology and products from Axis Communications, Sorama, and FF Group, the city aims to reduce traffic noise and enhance road safety. FF Group’s CAMMRA AI software and DataFactory platform help generate accurate vehicle data in real-time, day or night, to support noise reduction efforts. The challenge How can they address the challenge of traffic noise? What actions can local municipalities take to effectively monitor noise pollution and improve road safety? The solution Newport, hosting 4 million annual visitors, faces traffic noise due to congestion. To address this, the city implemented an AI-based noise camera solution with the Axis Radar-Video Fusion Camera, powered by CAMMRA AI, Sorama Acoustic Monitors, and the DataFactory platform. This system helps adjust noise ordinances and improve traffic safety as part of Newport's smart city initiative. Solution architecture 1. Axis Radar Video Fusion Camera Monitors vehicle speeds up to 125 mph, integrates with CAMMRA AI for licence plate recognition and speed tracking. 2. CAMMRA AI Application Recognize vehicle details (make, model, plate) and merge data with speed from the Axis Radar. 3. Sorama L642 Acoustic Monitors Capture sound levels with 64 microphones and integrate with Axis cameras for detailed vehicle data. Offers integrations with Axis camera, Axis Camera Station and FF DataFactory. 4. DataFactory platform Collects data on all vehicles, including sound level, licence plate, make, model, colour, speed, vehicle type, GPS coordinates, and time, for analysis to help city officials identify emerging patterns. Aggregates real-time data for enforcement, identifying vehicles that exceed sound limits. 5. Axis Camera Station Connected to the City Monitoring Centre, providing ready-to-use data from DataFactory for efficient monitoring and response. Offers a single platform to access all data from loud vehicle events, including bookmarked entries for further analysis. AI-powered technologies FF Group is tackling traffic noise pollution and improving urban safety via AI-powered technologies The partnership between the City of Newport, Sorama, Axis Communications, and FF Group is tackling traffic noise pollution and enhancing urban safety through AI-powered technologies. By integrating tools like the Axis Radar-Video Fusion Camera, CAMMRA AI, and Sorama's acoustic monitoring systems, Newport is proactively managing noise in real-time. Traffic management and noise regulation This solution improves quality of life, supports smart city goals, and enables better traffic management and noise regulation enforcement. With real-time data on vehicle speed, licence plates, and sound levels, Newport can quickly address violations and detect emerging issues, creating a safer and more sustainable urban environment.
The Torrance Unified School District is a cornerstone of the Torrance community, dedicated to providing a high-quality education that prepares students for success in college, career, and life. Serving a diverse student population, Torrance USD delivers a comprehensive and enriching educational experience from kindergarten through high school. The school district comprises 17 elementary, eight middle, and five high schools, one continuation high school, and one alternative high school. Vendor solutions Torrance USD had a mashup of different technologies and vendor solutions across its schools Like many school districts, Torrance USD had a mashup of different technologies and vendor solutions across its schools regarding the ability to broadcast announcements and alerts. Each school had separate systems for bells, clocks, and loudspeakers. There was no central management of these systems, and the school district couldn't create pre-recorded messages for emergencies. Many system components were also end-of-life, and maintaining everything was cumbersome at best. Focusing on consolidation for reliability and consistency Torrance USD began planning district-wide communication improvements in 2020, with the overarching goal of deploying one uniform system through all 32 campuses, with one dashboard to manage communications. The school district achieved its goal by deploying Cisco Call Manager coupled with Singlewire’s InformaCast communications software and hundreds of IPX endpoints from AtlasIED. Vetted integration technology partners like Cisco, Singlewire, and AtlasIED ensure that interoperability, reliability, and usability have all been verified and validated through extensive testing. Surveillance cameras for emergency alerting Torrance USD began planning district-wide communication improvements in 2020 “This project was part of a larger strategic plan to secure each campus — improve perimeter security, add surveillance cameras, allow for emergency alerting, consolidate the speaker systems, and standardise the bells,” said Gil Mara, Chief EdTech and Information Services Officer at Torrance USD. “For example, when you went from one campus to another, campuses had different bell sequences for scenarios like lockdowns. So, there was no consistency of the alerting mechanisms, and we wanted to ensure it was consistent across all the schools.” Digital and physical security of K-12 schools District staff contacted Nilkanth Radadia, Senior Account Manager at NIC Partners, to design the desired district-wide communications solution. NIC Partners has over two decades of experience enhancing the digital and physical security of K-12 schools and was well-suited to take on a project of Torrance USD’s scale. Focusing on what’s most important “Many stakeholders were involved in this project,” said Radadia. ”Given the project’s scope and requirements, there were a lot of conversations beforehand to get the district comfortable with understanding how the system would work." "Some key elements were customisability, two-way talk, multicolour visual message capabilities, and ADA compliance for the visual and hearing impaired. When AtlasIED came out with their full LCD screen speaker, that was a game changer.” Feature set and industrial design NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages AtlasIED was chosen as the vendor for the system upgrades after a thorough evaluation of various vendors. Their feature set and industrial design, particularly the full LCD screen speaker, stood out. NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages were audible, visible, and intelligible. WAN or LAN network architecture Leveraging standard WAN or LAN network architecture, each speaker is equipped with an integrated talkback microphone, LCD, and LED flasher, supporting both visual text and audio broadcast to enhance physical security while improving day-to-day communications through advanced alerting, bell schedules, and pre-recorded and scheduled announcements. For example, at 8:30 each morning, the Pledge of Allegiance is broadcast to all schools with a patriotic colour palette appearing on the IPX endpoints. LED blinker “We needed to implement a solution that would serve the needs of all the students, including those with visual or audio impairments,” said Mara. “That's why having the LED blinker and the message crawler was essential. That solved the issues regarding accessibility for our students and staff to ensure they got the message(s) every time.” Network-wide communication For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED. The IP-HVP is a vandal-proof, IP45 weather-resistant, wall-mount IP speaker well-suited for environments where network-wide communication is desired, and high output is required to overcome excessive ambient noise or large spaces. Almost 600 IP-HVP speakers were installed district-wide. Additionally, the Power over Ethernet (PoE+)-enabled IPX endpoints connect through the same IT network the school uses to deliver Internet access. InformaCast mass communications software The platform simplifies the installation process for integrators and reduces the need to introduce multiple cable types to a project. The IPX platform also offers scalability benefits, allowing schools the flexibility to expand their systems as the district’s communications evolve. The IPX Series also helped Torrance USD incorporate new and expanded campus safety capabilities with the help of InformaCast mass communications software. IPX LCD screens Torrance USD is trying out various colour combinations on the IPX LCD screens to indicate alerts Using InformaCast, designated school personnel can initiate an alert from a mobile device wherever they are. The software then sends text messages to faculty, students, and parents' mobile devices, alerts law enforcement, and activates attention-grabbing audio alarms and LCD text messages on the installed IPX devices throughout the school or district. Currently, Torrance USD is trying out various colour combinations on the IPX LCD screens to indicate different kinds of alerts, including earthquakes, shelter-in-place, and all-clear messages. Intentional and phased deployment leads to consistent use NIC Partners started with the smallest school to establish best practices for implementation. Once the first school was completed and future implementation methods documented, NIC Partners went full-on with the remaining schools, working second shift during the school year and completing all the upgrades district-wide in less than five months. The communication system is in the final phase of upgrading all the schools to InformaCast Fusion servers and upgrading Cisco Call Manager to Webex calling. These updates will allow select school and district staff members to make emergency announcements or push out notifications directly from their cell phones. NIC Partners and AtlasIED Staff and students appreciate the audio upgrades, albeit for different reasons. Teachers are relieved by the improved audio clarity, as they can finally hear things “loud and clear,” and emergency alerts include visual messaging. Students love the music played at the end of each period to indicate a class transition. “Before the upgrades, you couldn't make a good page,” said Mara. “Now, the audio clarity is way better. We’re delighted with the IPX products and even happier to have NIC Partners and AtlasIED as our partners for such a huge undertaking. We wouldn't have been successful without their help.”
ZeroEyes, the creators of the only AI-based gun detection video analytics platform that holds the full U.S. Department of Homeland Security SAFETY Act Designation, announces that its proactive gun detection and intelligent situational awareness solution has been deployed by Berrien Springs Public Schools (BSPS) in Michigan to mitigate gun-related violence. The company and district are also partnering to present ‘Lunch & Learn: Protecting Schools from Active Shooter Events,’ an in-depth safety and security seminar, ZeroEyes demo for surrounding schools, and Q&A to take place May 12th at 11:30 am in the STEM Central Building. Safe learning environment Located in the southwestern corner of the state, BSPS’ main campus sits in the heart of Berrien County and includes six schools: Mars Elementary, Sylvester Elementary, Berrien Springs Middle School, Berrien Springs High School, Virtual Academy, and Discovery Academy. Additionally, beyond its main campus, the district supports 28 additional learning centers statewide through an alternative learning program that helps students earn their high school diploma under the Michigan Merit Curriculum guidelines. The district has implemented ZeroEyes to further strengthen its multilayered security approach Serving approximately 7,000 students and employing 600 staff members in total, BSPS prioritises safety across all its campuses. Each school features secure vestibules and locked entry points, while the main campus is staffed with a dedicated school resource officer (SRO). The district has implemented ZeroEyes to further strengthen its multilayered security approach and ensure a safe learning environment for students and staff statewide. Engaging educational environment “At Berrien Springs Public Schools, student and staff safety are a priority as we continuously improve attendance, achievement, and engagement,” said Superintendent Dr. Thomas Bruce. “Implementing ZeroEyes allows us to take a proactive approach to security, ensuring that students and staff can focus on teaching and learning without distraction. This technology aligns with our commitment to creating an outstanding safe and engaging educational environment.” If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence ZeroEyes' AI gun detection and intelligent situational awareness software layers onto BSPS’ existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Center (ZOC), the industry's only U.S.-based, fully in-house operation center, which is staffed 24/7/365 by military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to first responders and local staff as quickly as 3 to 5 seconds from detection. Secure learning environment According to the incidents analysed by the ZeroEyes Gun Violence Research Center, Michigan has seen more gun-related incidents than the national average in the past 365 days. “We are extremely proud to work with Berrien Springs Public Schools to further protect students and teachers throughout the state of Michigan,” said Mike Lahiff, CEO and co-founder of ZeroEyes. “The district’s dedication to student success is showcased by its unwavering commitment to safety. I applaud their decision to implement proactive measures to create a secure learning environment.”
ZeroEyes, the creators of the only AI-based gun detection video analytics platform that holds the full US Department of Homeland Security SAFETY Act Designation, announces that its solution has been deployed by Michigan’s Williamston Community Schools to protect students, staff and visitors from gun-related violence. Centered in Williamston, the district educates over 2,000 students from Williamstown, Locke, Leroy, Wheatfield, Alaiedon and Meridian townships. It comprises five schools: a preschool, two elementary schools, a middle school and a high school. Layered security measures ZeroEyes will complement the schools' existing layered security measures, which include secure vestibules, a school resource officer (SRO) and a full-time firearm detection dog team, alongside proactive mental health programs such as “Prevent to Protect”, which helps students who are at high risk of committing suicide or violent acts towards others. “ZeroEyes is an important layer of security that complements the efforts that have already been put in place in the district,” said Adam Spina, Superintendent of Williamston Community Schools. “Our security layers combine to create a significantly safer school day for our students and staff.” Intelligent situational awareness If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence ZeroEyes' AI gun detection and intelligent situational awareness software layers onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Center (ZOC), the industry’s only U.S.-based, fully in-house operation center, which is staffed 24/7/365 by specially trained military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and school staff as quickly as 3 to 5 seconds from detection. Improving student safety As a result of Michigan Public Act 103 (PA 103), Williamston Community Schools received a grant specifically dedicated to procuring AI gun detection software to improve student safety. "The extensive security protocols and systems of Williamston Community Schools reflects the districts’ commitment to keeping students and staff safe from gun-related violence," said Mike Lahiff, CEO and co-founder of ZeroEyes. "The support of Michigan’s legislative grant program enabled us to provide proactive gun detection to a number of districts throughout the state. We encourage policymakers to expand the program in 2025 to help protect more schools.”
The Buffalo and Erie County Naval & Military Park, in Buffalo, N.Y., has a clear mission based on four pillars: to honour all veterans, educate the public about the sacrifices made by those who serve, inspire a sense of patriotism and appreciation for those protecting Americans’ rights and freedoms, and preserve the artifacts entrusted to the Park’s care. Buffalo Park The Park regularly hosts events and takes visitors inside America’s military history with in-depth tours of decommissioned naval vessels, exhibits, and displays. The team’s goal is to highlight its monuments and artifacts while providing a welcoming and secure environment for visitors. A key challenge was the Park’s large open and unfenced grounds, allowing the public access to the facilities at any time of the day or night. Challenge Provide a welcoming and secure environment for visitors and deter criminal activity within the park. Achieve 360° coverage across all interior and exterior areas without using cables, which would have made the project cost-prohibitive. Design a wireless surveillance system to cover the park’s large areas of open ground. Surveillance system installation “We had begun to notice an increased rate of delinquent incidents happening during the day and off hours, including graffiti placed on the artifacts and monuments,” said Paul Marzello, Sr., President & CEO, Buffalo and Erie County Naval & Military Park. The Park engaged Mario Rodriguez, president of Forseti Protection Group, and Erik Schiefer, account executive at Seibold Security, to design and install a surveillance system based on Hanwha Vision’s multi-directional and AI-equipped cameras. “When we did our research, we found that Hanwha Vision certainly was a pioneer in the industry,” said Marzello. Factors to consider From a risk and public safety perspective, the goal from the start was to maintain an open and welcoming environment “We conducted a site survey, considering the line of sight, the cameras’ capabilities, the density of groups of visitors and where they tend to gravitate, and criminal history in the Park,” said Bill Abbott, Director of Operations, Buffalo and Erie County Naval & Military Park. “Those were all factors in how we determined the layout. We wanted to make sure that we had the right coverage.” From a risk and public safety perspective, the goal from the start was maintaining an open and welcoming environment while keeping public safety top-of-mind. Solution Install a Hanwha Vision surveillance system comprising multidirectional and AI cameras. 4K multi-sensor cameras Schiefer has extensive experience with Hanwha cameras from previous projects. “Their new 4K multi-sensor cameras are first class and as far as 360° coverage, with the ability to monitor several areas, Hanwha was the first choice,” he said. The ability to view 360° coverage from one camera that essentially is divided into multiple sectors was significant. “That gives us full visibility and lets us be open and welcoming while keeping out of the public’s way without being imposing or intimidating,” Rodriguez said. Ease of playback Schiefer added that one key benefit of using the Hanwha 360° cameras to cover such a large area Schiefer added that one key benefit of using the Hanwha 360° cameras to cover such a large area is the ease of playing back footage and monitoring activity after the fact. “They are broken out into four sensors, so you don’t necessarily have to go back and look through a large amount of footage,” he said. “You can pick the area you're looking for, go directly to that sensor within the camera that we have in that area, and you can pull footage much easier that way.” Cable cost and distance One challenge the team encountered during the design phase was running a cable for a project of this scale. “The cost to run buried cable at such long distances with switches would have rendered this project almost completely impossible,” Schiefer said. “We incorporated wireless network cards into the poles around the park and all the cameras feed directly back to the Hanwha NVR without using any sort of cabling.” NDAA compliant solutions The Park’s priorities included the use of National Defense Authorization Act (NDAA) compliant solutions and having more streamlined communication with law enforcement. “We wanted to make sure that the cameras themselves were secure,” said Abbott. “The cameras also needed to be used to positively identify someone who had done something, either damage or acts of violence. In the past, we could not effectively supply law enforcement with usable information to identify a suspect." Use of AI in cameras The Hanwha cameras’ use of AI plays a key role in delivering those capabilities "We've now changed that with the quality of cameras that we're using. We can share footage and data to produce an outcome that's satisfying to everybody as far as finding a culprit and holding them accountable." The Hanwha cameras’ use of AI plays a key role in delivering those capabilities. “You can use key identifiers, whether it's the colour of someone's shirt, if they're wearing a backpack, or there's some physical feature that we can then go through and locate that person through the system,” Abbott said. Sense of security “We absolutely would see an increase in the value and number of cameras that we use,” said Abbott. Marzello added, “From an operations standpoint, we feel a greater sense of security knowing the cameras are there and will help us identify activities that we can hopefully prevent. This system meets our needs today and will also be able to grow with us.” Results Ability to effectively monitor all park areas and more effective forensic searches. Reduction in on-premise incidents. Streamlined collaboration with law enforcement agencies.
Windsor Port Authority, one of just 17 national ports created by the 1999 Canada Marine Act, has enhanced waterway safety and security across its jurisdiction on the U.S.-Canada border with state-of-the-art cameras from Axis Communications. These cameras, combined with radar solutions from Accipiter Radar Technologies Inc., provide the port with the visibility needed to prevent collisions, better detect illegal activity, and save lives along the river. Windsor Port Located on the Detroit River, the Windsor Port serves as the passageway between Lake Huron and Lake Erie, navigating between 6,000 and 9,000 cargo vessels annually. In addition to commercial ships, over 10,000 small fishing boats and other recreational watercraft make their way through the port each year. Better visibility Windsor Port Authority realised that it needed better visibility into happenings along the river With so many vessels passing through, Windsor Port Authority realised that it needed better visibility into happenings along the river to be able to keep the waterway running safely and smoothly. “Axis’ cameras, along with Accipiter’s radar technology, have been vital to keeping the port safe for all who pass through it,” said Peter Berry, Harbour Master and Vice President of Operations for Windsor Port Authority. Real-time incident detection “Without detailed knowledge of the traffic in these waters, the risk of severe accidents increases significantly, so having the ability to both detect and visually confirm incidents in real-time is invaluable." "We’ve already been able to do some amazing things with the enhanced surveillance solution, like quickly rescuing drowning victims and helping to catch human smugglers, and we’re eager to see what the future holds as a result of this upgrade.” An effective, remote observation By integrating Axis’ bispectral cameras into Accipiter's platform, the port has a 360-degree surveillance system While radar coverage from Accipiter has monitored river activity for years, offering wide-area, real-time detection, and tracking to identify commercial vessels, small craft such as jet skiers, and even debris in the water, it lacked the visual detail needed to provide effective, remote observation. By integrating Axis’ bispectral cameras into Accipiter's platform, the port has a 360-degree surveillance system with both thermal detection and visual verification. System benefits With this enhanced system, the port can: Broadcast real-time warnings about obstructions in the channel: In one instance, the U.S. Coast Guard notified the port that they’d spotted a boat stopped in the middle of the river. The vessel had caught fire, dropped anchor, and was dead in the water. The thermal camera and radar technology allowed for continuous monitoring of the fire onboard the ship, helping them to determine that it was contained to the engine room while enabling the port to send out a navigational warning to other vessels on the river. While the darkness of the hour prevented them from seeing anything from shore, the technology also provided thermal visuals to monitor activity on the bridge and deck. Everyone was safely evacuated. Safely navigate craft through high-risk construction projects: During the construction of a new bridge, the port was concerned about potential disruptions to river traffic, but Axis cameras and integrated radars allowed them to effectively manage vessels passing underneath the site. Deliver precise coordinates for faster rescue operations: When the port got a call from the U.S. Coast Guard that they had spotted a person treading water by the Ambassador Bridge, they were able to quickly identify the location of the person using a combination of radar and camera technology and execute a life-saving rescue. Help to identify criminal activity: While using the camera-radar technology to view objects crossing from Canada to the U.S., the port identified suspicious activity from a boat that regularly sailed from Windsor to Detroit. The port turned the data and video over to the Canadian and U.S. authorities to investigate, which ultimately led to the arrest of two individuals running a human smuggling operation. Marine domain awareness “At Axis, we take pride in working with organisations like Windsor Port Authority to contribute to improved marine domain awareness and heightened safety along the border,” said Anthony Incorvati, Transportation Segment Development Manager for the Americas at Axis. “Combining advanced camera and radar technology ensures comprehensive visibility in maritime environments, providing essential detection and visual verification to resolve incidents quickly and effectively. Not only that, but powerful business intelligence capabilities contribute to improved operations across the organisation.”
Newport, a popular vacation destination, has partnered with Sorama to tackle growing noise pollution. By integrating AI technology and products from Axis Communications, Sorama, and FF Group, the city aims to reduce traffic noise and enhance road safety. FF Group’s CAMMRA AI software and DataFactory platform help generate accurate vehicle data in real-time, day or night, to support noise reduction efforts. The challenge How can they address the challenge of traffic noise? What actions can local municipalities take to effectively monitor noise pollution and improve road safety? The solution Newport, hosting 4 million annual visitors, faces traffic noise due to congestion. To address this, the city implemented an AI-based noise camera solution with the Axis Radar-Video Fusion Camera, powered by CAMMRA AI, Sorama Acoustic Monitors, and the DataFactory platform. This system helps adjust noise ordinances and improve traffic safety as part of Newport's smart city initiative. Solution architecture 1. Axis Radar Video Fusion Camera Monitors vehicle speeds up to 125 mph, integrates with CAMMRA AI for licence plate recognition and speed tracking. 2. CAMMRA AI Application Recognize vehicle details (make, model, plate) and merge data with speed from the Axis Radar. 3. Sorama L642 Acoustic Monitors Capture sound levels with 64 microphones and integrate with Axis cameras for detailed vehicle data. Offers integrations with Axis camera, Axis Camera Station and FF DataFactory. 4. DataFactory platform Collects data on all vehicles, including sound level, licence plate, make, model, colour, speed, vehicle type, GPS coordinates, and time, for analysis to help city officials identify emerging patterns. Aggregates real-time data for enforcement, identifying vehicles that exceed sound limits. 5. Axis Camera Station Connected to the City Monitoring Centre, providing ready-to-use data from DataFactory for efficient monitoring and response. Offers a single platform to access all data from loud vehicle events, including bookmarked entries for further analysis. AI-powered technologies FF Group is tackling traffic noise pollution and improving urban safety via AI-powered technologies The partnership between the City of Newport, Sorama, Axis Communications, and FF Group is tackling traffic noise pollution and enhancing urban safety through AI-powered technologies. By integrating tools like the Axis Radar-Video Fusion Camera, CAMMRA AI, and Sorama's acoustic monitoring systems, Newport is proactively managing noise in real-time. Traffic management and noise regulation This solution improves quality of life, supports smart city goals, and enables better traffic management and noise regulation enforcement. With real-time data on vehicle speed, licence plates, and sound levels, Newport can quickly address violations and detect emerging issues, creating a safer and more sustainable urban environment.
The Torrance Unified School District is a cornerstone of the Torrance community, dedicated to providing a high-quality education that prepares students for success in college, career, and life. Serving a diverse student population, Torrance USD delivers a comprehensive and enriching educational experience from kindergarten through high school. The school district comprises 17 elementary, eight middle, and five high schools, one continuation high school, and one alternative high school. Vendor solutions Torrance USD had a mashup of different technologies and vendor solutions across its schools Like many school districts, Torrance USD had a mashup of different technologies and vendor solutions across its schools regarding the ability to broadcast announcements and alerts. Each school had separate systems for bells, clocks, and loudspeakers. There was no central management of these systems, and the school district couldn't create pre-recorded messages for emergencies. Many system components were also end-of-life, and maintaining everything was cumbersome at best. Focusing on consolidation for reliability and consistency Torrance USD began planning district-wide communication improvements in 2020, with the overarching goal of deploying one uniform system through all 32 campuses, with one dashboard to manage communications. The school district achieved its goal by deploying Cisco Call Manager coupled with Singlewire’s InformaCast communications software and hundreds of IPX endpoints from AtlasIED. Vetted integration technology partners like Cisco, Singlewire, and AtlasIED ensure that interoperability, reliability, and usability have all been verified and validated through extensive testing. Surveillance cameras for emergency alerting Torrance USD began planning district-wide communication improvements in 2020 “This project was part of a larger strategic plan to secure each campus — improve perimeter security, add surveillance cameras, allow for emergency alerting, consolidate the speaker systems, and standardise the bells,” said Gil Mara, Chief EdTech and Information Services Officer at Torrance USD. “For example, when you went from one campus to another, campuses had different bell sequences for scenarios like lockdowns. So, there was no consistency of the alerting mechanisms, and we wanted to ensure it was consistent across all the schools.” Digital and physical security of K-12 schools District staff contacted Nilkanth Radadia, Senior Account Manager at NIC Partners, to design the desired district-wide communications solution. NIC Partners has over two decades of experience enhancing the digital and physical security of K-12 schools and was well-suited to take on a project of Torrance USD’s scale. Focusing on what’s most important “Many stakeholders were involved in this project,” said Radadia. ”Given the project’s scope and requirements, there were a lot of conversations beforehand to get the district comfortable with understanding how the system would work." "Some key elements were customisability, two-way talk, multicolour visual message capabilities, and ADA compliance for the visual and hearing impaired. When AtlasIED came out with their full LCD screen speaker, that was a game changer.” Feature set and industrial design NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages AtlasIED was chosen as the vendor for the system upgrades after a thorough evaluation of various vendors. Their feature set and industrial design, particularly the full LCD screen speaker, stood out. NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages were audible, visible, and intelligible. WAN or LAN network architecture Leveraging standard WAN or LAN network architecture, each speaker is equipped with an integrated talkback microphone, LCD, and LED flasher, supporting both visual text and audio broadcast to enhance physical security while improving day-to-day communications through advanced alerting, bell schedules, and pre-recorded and scheduled announcements. For example, at 8:30 each morning, the Pledge of Allegiance is broadcast to all schools with a patriotic colour palette appearing on the IPX endpoints. LED blinker “We needed to implement a solution that would serve the needs of all the students, including those with visual or audio impairments,” said Mara. “That's why having the LED blinker and the message crawler was essential. That solved the issues regarding accessibility for our students and staff to ensure they got the message(s) every time.” Network-wide communication For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED. The IP-HVP is a vandal-proof, IP45 weather-resistant, wall-mount IP speaker well-suited for environments where network-wide communication is desired, and high output is required to overcome excessive ambient noise or large spaces. Almost 600 IP-HVP speakers were installed district-wide. Additionally, the Power over Ethernet (PoE+)-enabled IPX endpoints connect through the same IT network the school uses to deliver Internet access. InformaCast mass communications software The platform simplifies the installation process for integrators and reduces the need to introduce multiple cable types to a project. The IPX platform also offers scalability benefits, allowing schools the flexibility to expand their systems as the district’s communications evolve. The IPX Series also helped Torrance USD incorporate new and expanded campus safety capabilities with the help of InformaCast mass communications software. IPX LCD screens Torrance USD is trying out various colour combinations on the IPX LCD screens to indicate alerts Using InformaCast, designated school personnel can initiate an alert from a mobile device wherever they are. The software then sends text messages to faculty, students, and parents' mobile devices, alerts law enforcement, and activates attention-grabbing audio alarms and LCD text messages on the installed IPX devices throughout the school or district. Currently, Torrance USD is trying out various colour combinations on the IPX LCD screens to indicate different kinds of alerts, including earthquakes, shelter-in-place, and all-clear messages. Intentional and phased deployment leads to consistent use NIC Partners started with the smallest school to establish best practices for implementation. Once the first school was completed and future implementation methods documented, NIC Partners went full-on with the remaining schools, working second shift during the school year and completing all the upgrades district-wide in less than five months. The communication system is in the final phase of upgrading all the schools to InformaCast Fusion servers and upgrading Cisco Call Manager to Webex calling. These updates will allow select school and district staff members to make emergency announcements or push out notifications directly from their cell phones. NIC Partners and AtlasIED Staff and students appreciate the audio upgrades, albeit for different reasons. Teachers are relieved by the improved audio clarity, as they can finally hear things “loud and clear,” and emergency alerts include visual messaging. Students love the music played at the end of each period to indicate a class transition. “Before the upgrades, you couldn't make a good page,” said Mara. “Now, the audio clarity is way better. We’re delighted with the IPX products and even happier to have NIC Partners and AtlasIED as our partners for such a huge undertaking. We wouldn't have been successful without their help.”
ZeroEyes, the creators of the only AI-based gun detection video analytics platform that holds the full U.S. Department of Homeland Security SAFETY Act Designation, announces that its proactive gun detection and intelligent situational awareness solution has been deployed by Berrien Springs Public Schools (BSPS) in Michigan to mitigate gun-related violence. The company and district are also partnering to present ‘Lunch & Learn: Protecting Schools from Active Shooter Events,’ an in-depth safety and security seminar, ZeroEyes demo for surrounding schools, and Q&A to take place May 12th at 11:30 am in the STEM Central Building. Safe learning environment Located in the southwestern corner of the state, BSPS’ main campus sits in the heart of Berrien County and includes six schools: Mars Elementary, Sylvester Elementary, Berrien Springs Middle School, Berrien Springs High School, Virtual Academy, and Discovery Academy. Additionally, beyond its main campus, the district supports 28 additional learning centers statewide through an alternative learning program that helps students earn their high school diploma under the Michigan Merit Curriculum guidelines. The district has implemented ZeroEyes to further strengthen its multilayered security approach Serving approximately 7,000 students and employing 600 staff members in total, BSPS prioritises safety across all its campuses. Each school features secure vestibules and locked entry points, while the main campus is staffed with a dedicated school resource officer (SRO). The district has implemented ZeroEyes to further strengthen its multilayered security approach and ensure a safe learning environment for students and staff statewide. Engaging educational environment “At Berrien Springs Public Schools, student and staff safety are a priority as we continuously improve attendance, achievement, and engagement,” said Superintendent Dr. Thomas Bruce. “Implementing ZeroEyes allows us to take a proactive approach to security, ensuring that students and staff can focus on teaching and learning without distraction. This technology aligns with our commitment to creating an outstanding safe and engaging educational environment.” If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence ZeroEyes' AI gun detection and intelligent situational awareness software layers onto BSPS’ existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Center (ZOC), the industry's only U.S.-based, fully in-house operation center, which is staffed 24/7/365 by military and law enforcement veterans. If these experts determine that the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to first responders and local staff as quickly as 3 to 5 seconds from detection. Secure learning environment According to the incidents analysed by the ZeroEyes Gun Violence Research Center, Michigan has seen more gun-related incidents than the national average in the past 365 days. “We are extremely proud to work with Berrien Springs Public Schools to further protect students and teachers throughout the state of Michigan,” said Mike Lahiff, CEO and co-founder of ZeroEyes. “The district’s dedication to student success is showcased by its unwavering commitment to safety. I applaud their decision to implement proactive measures to create a secure learning environment.”


Round table discussion
Direct costs such as purchase price and maintenance are important elements in the total cost of ownership (TCO). However, there are others. Elements such as opportunity costs of lost revenue or hidden costs of energy consumption and environmental consequences can also impact the measure of TCO. Costs of training, integration, support, and scalability can also be examined. Considering the security industry impact of TCO, we asked this week's Expert Panel Roundtable: How does/should total cost of ownership (TCO) impact the decision-making process when choosing technologies for security?
While technology like cameras, alarms, and access control systems are crucial components, they are only as effective as the people who use and manage them and the systems that deploy them. When installing physical security systems, the focus should be on the holistic operation of the system rather than the functioning of individual components. However, in the end, overlooking critical factors can undermine the totality of system performance. We asked this week's Expert Panel Roundtable: What is the most overlooked factor when installing physical security systems?
Video surveillance has been a dominant factor in the casino market since the 1950s when video replaced the use of elevated walkways that allowed casino security personnel to monitor the gaming floor from above. As technology continues to evolve, we can expect to see more innovative uses of video in the casino market. Beyond video, other technologies are also transforming the casino experience. We asked this week’s Expert Panel Roundtable: How are new technologies impacting the casino surveillance and security market?
Products


White papers

Video surveillance as a service: Why are video management systems migrating to the Cloud?
Download
11 reasons video surveillance is moving to the cloud
Download
How security systems ensure healthy workplaces during COVID and after
Download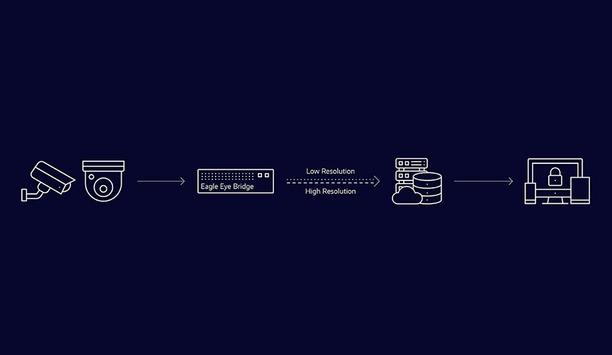
Best practices guide: analogue video to cloud
Download
The inevitability of The Cloud
DownloadMaking sense of today’s security camera options
Download
5 ways to strengthen physical security with an integrated system
Download
Video technology: making cities safer & improving lives
Download
Empowering cameras with AI
Download
Protecting dormitory residents and assets
Download
Choosing the right storage technology for video surveillance
Download
Video surveillance as a service: Why are video management systems migrating to the Cloud?
Download
11 reasons video surveillance is moving to the cloud
Download
How security systems ensure healthy workplaces during COVID and after
Download
Best practices guide: analogue video to cloud
Download
The inevitability of The Cloud
DownloadMaking sense of today’s security camera options
Download
5 ways to strengthen physical security with an integrated system
Download
Video technology: making cities safer & improving lives
Download
Empowering cameras with AI
Download
Protecting dormitory residents and assets
Download
Choosing the right storage technology for video surveillance
Download
Video surveillance as a service: Why are video management systems migrating to the Cloud?
Download

Videos
Covert cameras: Manufacturers & Suppliers
- Hikvision Covert cameras
- Dahua Technology Covert cameras
- Hanwha Vision Covert cameras
- Verkada Covert cameras
- Milesight Covert cameras
- Axis Communications Covert cameras
- LILIN Covert cameras
- Avigilon Covert cameras
- Illustra Covert cameras
- MOBOTIX Covert cameras
- Speco Technologies Covert cameras
- Honeywell Security Covert cameras
- AV Costar Covert cameras
- Videotec Covert cameras
- Milestone Covert cameras
- DNAKE Covert cameras
- Anviz Covert cameras
- exacqVision Covert cameras

Using artificial intelligence (AI) to automate physical security systems
Download
A modern guide to data loss prevention
Download
7 proven solutions for law enforcement key control and asset management
Download
The truth behind 9 mobile access myths
Download
Access control system planning phase 2
Download

















































