Asset tracking
Magenta Security Services, one of the UK’s pioneer security firms, has achieved an exceptional score of 87.5% in its most recent SIA Approved Contractor Scheme (ACS) audit - placing the company firmly within the top 5% of security companies nationwide. With only the top 10% of security firms scoring above 75%, Magenta’s remarkable result reflects the company’s consistent dedication to quality, compliance, and operational excellence across every area of its business. Exceeding...
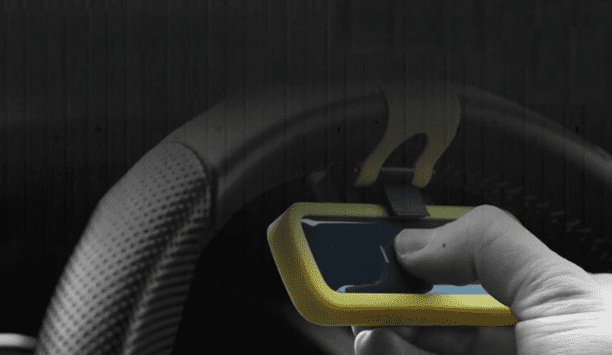
Pyronix announces new campaign offering a complimentary CarDefender inside every Enforcer Kit purchase, in promotion-labelled packs and while stocks last in distributors. This promotion will give installers immediate access to a free, award-winning peripheral when they buy one of our best-selling products. Next-gen auto safety The device’s inbuilt shock/tilt sensor offers three configurable detection modesThe CarDefender is an innovative wireless peripheral offering protection aga...
SAFR from RealNetworks, the world’s foremost AI computer vision platform for access control and security, invites ISC West 2025 attendees to experience its revolutionary suite of AI-powered solutions at booth #25089. SAFR's facial recognition technology delivers unparalleled certainty through industry-pioneer accuracy, enabling organisations to monitor and analyse visual data at speeds far beyond human capabilities—all while maintaining the highest standards of data privacy an...
Regula, a global developer of forensic devices and identity verification solutions, now has 15,000 templates in its identity document template database, the most comprehensive in the world. This significant update ensures that businesses and government agencies around the globe can verify the latest IDs, including the most advanced biometric documents, with the highest accuracy. Global ID verification simplified Incorporating ID templates from 251 countries and territories and capable o...
Data isn’t just the driver for project planning and design. The Eplan Data Portal offers users access to high-quality product catalogues from a continually growing pool of renowned component manufacturers. The portal has now passed the mark of more than two-million sets of static device data from around five hundred manufacturers! By using integrated configurators, users have far more than four million data sets at their fingertips. It’s a nearly limitless and ever-incr...
Colt Technology Services (Colt), the global digital infrastructure company, announced the successful completion of a groundbreaking quantum-secured encryption trial across its optical wave network. Colt collaborated with a number of technology partners for the trial including Adtran, Ciena, ID Quantique (IDQ), Nokia and Toshiba, with a view to Colt offering a suite of services for global businesses to prepare for a quantum-secured future. Secured encryption solutions Quantum-secured enc...
News
Nanodems, a pioneer in Physical Security Information Management (PSIM) announced a strategic partnership between TKH Security, a global pioneer in security and parking guidance technologies. TKH Security TKH Security, based in Zoetermeer, the Netherlands, with over 25 years of experience, provides innovative solutions for security, asset & site, and parking guidance management. Operating in over 80 countries with 12 offices worldwide, TKH Security is committed to delivering high-quality, cyber-secure technologies that are designed in-house and manufactured in Europe, with a strong focus on environmental responsibility. Nanodems Corporation Its seamless platform integrates and manages diverse security assets, including CCTV, access control systems Nanodems Corporation, based in Burlington, Massachusetts, specialises in PSIM solutions that enable organisations to streamline operations, mitigate risks, and centralise control of their security ecosystems. Its seamless platform integrates and manages diverse security assets, including CCTV, access control systems, and perimeter intrusion detection systems. Security management This partnership unites TKH Security’s expertise in VMS with Nanodems’ expertise in software solutions, providing a comprehensive and integrated approach to security management. Together, Nanodems aims to deliver innovative, efficient, and secure solutions that meet the evolving needs of organisations worldwide. This integration will provide innovative, efficient, and secure solutions to empower organisations globally.
ASSA ABLOY has acquired InVue, a US-based provider of precision-engineered connected asset protection and access control solutions. The company enables tailor-made security solutions to a broad spectrum of industries and retailers. Access control and asset protection "I am very pleased to welcome the InVue team to ASSA ABLOY. This acquisition delivers on our strategy to grow our business through adding complementary products and solutions to our core business,” says Nico Delvaux, President and CEO of ASSA ABLOY. “InVue is a global technology provider at the forefront of innovative security solutions for protecting assets in the retail business. InVue is an excellent addition to Global Solutions, the acquisition will expand our core capabilities across access control and asset protection globally. I look forward to working with InVue’s successful and experienced team,” says Stephanie Ordan, Executive Vice President and Head of Global Technologies business unit Global Solutions. InVue InVue was founded in 1986 and has some 260 employees. The main office is located in Charlotte, North Carolina, US. Sales for 2024 amounted to about MUSD 165 (approx. MSEK 1,850) with a strong EBIT margin. The acquisition will be accretive to EPS from the start.
Award-winning global security manufacturer, Gallagher Security is gearing up to showcase the latest in its innovative technology suite at Intersec Dubai from 14-16 January 2025. Together with their Technology Partners, DEA Security, COMMEND, Moro Hub, and Stratus Technologies, Gallagher will be showcasing their latest advanced perimeter protection, innovative access control, secure credentials, Apple Wallet integration, as well as the recently released, Controller 7000 (C7000) Enhanced, plus updates on some exciting new product releases earmarked for later in 2025. C7000 Enhanced Released in October 2024, the C7000 Enhanced, tipped as the controller designed with user confidence in mind offers increased reliability, redundancy, and resilience for customers. Jim Rayner, Value Owner at Gallagher who led production on the C7000 Enhanced says, ‘It has it all’. "We’re excited to bring the C7000 Enhanced to market and to continue building out this product range based on the feedback of our Channel Partners and End Users. The C7000 Enhanced is a future-proof solution, designed for those that want more.” C7000 Standard variant The Cyber Hub of the Year category celebrates pioneering products or services The award-winning C7000 Standard variant is also a finalist in the ‘Cyber Hub of the Year category at the Intersec Awards. The Cyber Hub of the Year category celebrates pioneering products or services that excel in protecting digital systems, networks, and data from cyber threats. Middle East CEO comments Gallagher Security Middle East CEO, Bilal Chehime says, “Intersec Dubai is a major event for both the Middle East and the global security industry, and we are thrilled to be exhibiting again this year." "Our commitment to innovation reflects our dedication to staying at the forefront of the ever-evolving security market and we take great pride in being part of such a dynamic and promising industry. We look forward to showcasing our latest solutions to meet the growing demands of security worldwide.” New appointment Nemer brings over a decade of leadership experience in business development, smart cities, IoT Visitors to the Gallagher stand will have the opportunity to meet with a strong contingent from the Middle East team, including newly appointed Regional Director – Middle East North Africa, Nemer Mdardas. Based in the company’s Dubai office, Nemer brings over a decade of leadership experience in business development, smart cities, IoT solutions, and physical security systems. Intersec Dubai 2025 Marking its 26th year, Intersec Dubai runs from 14 - 16 January at Dubai’s World Trade Centre. The 2024 event attracted a huge international audience, hosting more than 47,000 trade buyers from 141 countries, including key government pioneers, agencies, and organisational heads across various industries. Visit Gallagher Security at stand S1-C16.
Teledyne FLIR OEM, part of Teledyne Technologies Incorporated announced the release of Prism™ Supervisor, the latest addition to its Prism-embedded software ecosystem. Prism Supervisor integrates drone autopilot flight control systems with real-time, AI-based observations at the edge to improve mission safety, efficiency, and performance, enhancing the capabilities of unmanned aircraft systems (UAS). Prism Supervisor software Prism Supervisor software empowers mission planners with a flexible programming framework and software development kit (SDK) to facilitate custom, intricate mission scenarios. During flight, Prism Supervisor adapts its autopilot functionality in real-time, dynamically generating mission segments and flight plans on the fly, minimising operator impact while improving mission success. For example, a Prism Supervisor-controlled UAV flying a search mission pattern can autonomously circle and alert the operator upon the detection of a human or threat. Operational performance "From behaviour and mission planning to dynamically adjust in-flight operations, Prism Supervisor represents a significant advancement for drone autonomy through AI," said Dan Walker, Vice President of Product Management, at Teledyne FLIR. "It improves operational performance via single-click missions, opening up new possibilities for UAS operation from commercial to military use cases." User-friendly GUI It can facilitate collaborative behaviours and synchronised mission execution among multiple UAVs Prism Supervisor simplifies the operator experience with a user-friendly graphic user interface (GUI) for mission planning, real-time mission visualisation, and execution. Available for desktop or mobile deployment supporting Windows, Linux, macOS, iOS, and Android, the supervised mission management application streams and records detailed, full-frame-rate video, path visualisation, and metadata. It can facilitate collaborative behaviours and synchronised mission execution among multiple unmanned aerial vehicles (UAVs). Advanced AI and image processing Prism Supervisor expands Teledyne FLIR's Prism digital ecosystem of advanced AI and image processing. It provides a platform for deploying object detection, tracking, and computational imaging on low-power processors, enhancing UAS mission performance and reducing development costs.
Aesthetic options, in addition to robust security features, are increasingly important to architectural door openings. Adams Rite delivers, expanding its finish offerings for the 8800 Series Starwheel Rim Exit Devices to include Black Suede Powder (BSP). 8800 Rim Exit Devices Adams Rite 8800 Rim Exit Devices offers reliable security, durable construction, and streamlined design for narrow stile aluminum doors. Its unique Starwheel bolt interlocks door to frame to provide enhanced strength and prevent jamb spread, while a clean profile and fewer pinch points make it ideal for high-traffic storefronts. Life-safety and fire-rated exit devices The 8800 is part of a premium series of life-safety and fire-rated exit devices by Adams Rite, available with a range of mechanical and electrical options, multiple finishes, and compatible products for a seamless solution. Adams Rite offers the most complete line of exit devices and related hardware solutions in the industry to effectively secure single and pairs of doors with a unified look, standardized installation, and operation in any facility.
Cequence Security, a pioneer in API security and bot management announced significant momentum in the Middle East and Africa (MEA) region, driven by rapid customer adoption, strategic partnerships, and a strengthened leadership team. This expansion further solidifies Cequence’s position as the go-to API security and bot management provider in the region, addressing the growing demand for advanced threat protection and digital risk mitigation. Modern digital transformation “APIs are the backbone of modern digital transformation, but they are also the most exploited attack surface,” said Ameya Talwalkar, CEO of Cequence Security. “We are not just expanding—we are transforming how businesses defend their digital assets. As the only solution that provides data sovereignty in the region, we empower enterprises with AI-driven security tailored to their unique regulatory and threat landscapes. By combining innovative threat intelligence with proactive defence, we enable organisations to anticipate and mitigate attacks before they impact operations.” MEA expansion Cequence’s expansion in MEA has been marked by: 1) New customer acquisitions across financial services, telecommunications, oil and gas, and technology, securing organisations such as: A top Islamic bank in the UAE. One of the largest financial institutions in the Middle East and Africa. A major telecom provider in Turkey. A digital transformation pioneer in the energy sector. 2) A 193% increase in ARR in the MEA region year-over-year. 3) A 68% increase in partner deal registrations, demonstrating strong market demand for Cequence’s Unified API Protection (UAP) platform. 4) An 83% increase in reseller partnerships, spanning KSA, UAE, Qatar, Jordan, Kuwait, Bahrain, and Egypt. 5) The planned signing of a strategic Memorandum of Understanding (MOU) at LEAP 2025 with a strategic GTM partner, underscores Cequence’s commitment to regional cybersecurity initiatives. 6) Hiring for multiple positions across various departments in the region reinforces Cequence’s investment in local talent and its commitment to long-term growth in the MEA. Strategic leadership appointment Ismail brings a proven track record of driving business growth and forging strategic alliances To drive Cequence’s expansion in MEA, the company has appointed Mohammad Ismail as its new Head of Go-to-Market (GTM) & Sales for EMEA, strategically based in Dubai to accelerate regional growth and customer success. With over 25 years of experience in cybersecurity and enterprise IT across the Middle East, Africa, and Southeast Asia, Ismail brings a proven track record of driving business growth and forging strategic alliances. Reliance on APIs “My focus at Cequence is to strengthen our presence in the EMEA region by deepening relationships with customers and partners,” said Mohammad Ismail, Head of GTM & Sales for EMEA. “With the increasing adoption of the growing reliance on APIs to power digital services, organisations need robust API security and bot management solutions. I look forward to leveraging my experience to expand our footprint, provide strategic guidance, and help customers stay ahead of evolving cyber threats.” Customer success and industry validation Cequence’s platform has helped organisations across MEA overcome critical API security and bot management challenges. Customers have leveraged Cequence to: Secure APIs during open banking transitions, ensuring compliance and real-time protection for sensitive financial data. Enhance API governance and security testing, integrating seamlessly with CI/CD pipelines to enforce OWASP Top 10 protections. Detect and stop sophisticated API attacks with AI-driven threat detection and real-time behavioral analysis, mitigating risks from shadow APIs and automated threats. Improve visibility and response times with comprehensive API activity monitoring, automated security enforcement, and automated enforcement with no human intervention. Meet stringent data sovereignty requirements, ensuring security policies remain within customer-controlled environments. These capabilities combined with Cequence’s unified approach, continue to drive strong adoption among MEA enterprises seeking to protect their digital environments. Investor confidence and market leadership Cequence’s expansion in MEA has garnered continued support from investors Cequence’s expansion in MEA has garnered continued support from investors, including Prosperity7 Ventures and Sanabil Investments. “The Middle East presents a unique and fast-growing opportunity for cybersecurity innovation, and Cequence is pioneering the charge with its best-in-class API security solutions,” said Abhishek Shukla, managing director and head of North America at Prosperity7 Ventures. “With an experienced leadership team, strong regional partnerships, and a relentless focus on innovation, Cequence is well-positioned to drive continued success in the MEA market.” Commitment to innovation As part of its ongoing commitment to innovation, Cequence has introduced new capabilities tailored to the MEA market, including: Expanded cloud and on-premises deployment options, ensuring compliance with regional data sovereignty requirements. Enhanced partner enablement programs, equipping resellers and service providers with advanced API security expertise. Protecting digital assets “With API threats growing more sophisticated, we remain focused on delivering cutting-edge security solutions that empower organisations to stay ahead of attackers,” added Talwalkar. “Our investment in MEA reflects our dedication to supporting businesses with the tools they need to protect their digital assets and maintain trust with their customers.” LEAP 2025 Cequence will be at Stand H1.D30 during LEAP 2025. Stop by to meet the team and learn more about how the industry-pioneering API security and bot management solutions can help protect the digital ecosystem. Join Ameya Talwalkar, CEO of Cequence, as he discusses the evolving API security and bot management landscape. His session will cover emerging threats, regional trends, and strategies for mitigating cyber risks. When: 7:30 PM - 7:50 PM Where: Stand H1.D30
Nanodems, a pioneer in Physical Security Information Management (PSIM) announced a strategic partnership between TKH Security, a global pioneer in security and parking guidance technologies. TKH Security TKH Security, based in Zoetermeer, the Netherlands, with over 25 years of experience, provides innovative solutions for security, asset & site, and parking guidance management. Operating in over 80 countries with 12 offices worldwide, TKH Security is committed to delivering high-quality, cyber-secure technologies that are designed in-house and manufactured in Europe, with a strong focus on environmental responsibility. Nanodems Corporation Its seamless platform integrates and manages diverse security assets, including CCTV, access control systems Nanodems Corporation, based in Burlington, Massachusetts, specialises in PSIM solutions that enable organisations to streamline operations, mitigate risks, and centralise control of their security ecosystems. Its seamless platform integrates and manages diverse security assets, including CCTV, access control systems, and perimeter intrusion detection systems. Security management This partnership unites TKH Security’s expertise in VMS with Nanodems’ expertise in software solutions, providing a comprehensive and integrated approach to security management. Together, Nanodems aims to deliver innovative, efficient, and secure solutions that meet the evolving needs of organisations worldwide. This integration will provide innovative, efficient, and secure solutions to empower organisations globally.
ASSA ABLOY has acquired InVue, a US-based provider of precision-engineered connected asset protection and access control solutions. The company enables tailor-made security solutions to a broad spectrum of industries and retailers. Access control and asset protection "I am very pleased to welcome the InVue team to ASSA ABLOY. This acquisition delivers on our strategy to grow our business through adding complementary products and solutions to our core business,” says Nico Delvaux, President and CEO of ASSA ABLOY. “InVue is a global technology provider at the forefront of innovative security solutions for protecting assets in the retail business. InVue is an excellent addition to Global Solutions, the acquisition will expand our core capabilities across access control and asset protection globally. I look forward to working with InVue’s successful and experienced team,” says Stephanie Ordan, Executive Vice President and Head of Global Technologies business unit Global Solutions. InVue InVue was founded in 1986 and has some 260 employees. The main office is located in Charlotte, North Carolina, US. Sales for 2024 amounted to about MUSD 165 (approx. MSEK 1,850) with a strong EBIT margin. The acquisition will be accretive to EPS from the start.
Award-winning global security manufacturer, Gallagher Security is gearing up to showcase the latest in its innovative technology suite at Intersec Dubai from 14-16 January 2025. Together with their Technology Partners, DEA Security, COMMEND, Moro Hub, and Stratus Technologies, Gallagher will be showcasing their latest advanced perimeter protection, innovative access control, secure credentials, Apple Wallet integration, as well as the recently released, Controller 7000 (C7000) Enhanced, plus updates on some exciting new product releases earmarked for later in 2025. C7000 Enhanced Released in October 2024, the C7000 Enhanced, tipped as the controller designed with user confidence in mind offers increased reliability, redundancy, and resilience for customers. Jim Rayner, Value Owner at Gallagher who led production on the C7000 Enhanced says, ‘It has it all’. "We’re excited to bring the C7000 Enhanced to market and to continue building out this product range based on the feedback of our Channel Partners and End Users. The C7000 Enhanced is a future-proof solution, designed for those that want more.” C7000 Standard variant The Cyber Hub of the Year category celebrates pioneering products or services The award-winning C7000 Standard variant is also a finalist in the ‘Cyber Hub of the Year category at the Intersec Awards. The Cyber Hub of the Year category celebrates pioneering products or services that excel in protecting digital systems, networks, and data from cyber threats. Middle East CEO comments Gallagher Security Middle East CEO, Bilal Chehime says, “Intersec Dubai is a major event for both the Middle East and the global security industry, and we are thrilled to be exhibiting again this year." "Our commitment to innovation reflects our dedication to staying at the forefront of the ever-evolving security market and we take great pride in being part of such a dynamic and promising industry. We look forward to showcasing our latest solutions to meet the growing demands of security worldwide.” New appointment Nemer brings over a decade of leadership experience in business development, smart cities, IoT Visitors to the Gallagher stand will have the opportunity to meet with a strong contingent from the Middle East team, including newly appointed Regional Director – Middle East North Africa, Nemer Mdardas. Based in the company’s Dubai office, Nemer brings over a decade of leadership experience in business development, smart cities, IoT solutions, and physical security systems. Intersec Dubai 2025 Marking its 26th year, Intersec Dubai runs from 14 - 16 January at Dubai’s World Trade Centre. The 2024 event attracted a huge international audience, hosting more than 47,000 trade buyers from 141 countries, including key government pioneers, agencies, and organisational heads across various industries. Visit Gallagher Security at stand S1-C16.
Teledyne FLIR OEM, part of Teledyne Technologies Incorporated announced the release of Prism™ Supervisor, the latest addition to its Prism-embedded software ecosystem. Prism Supervisor integrates drone autopilot flight control systems with real-time, AI-based observations at the edge to improve mission safety, efficiency, and performance, enhancing the capabilities of unmanned aircraft systems (UAS). Prism Supervisor software Prism Supervisor software empowers mission planners with a flexible programming framework and software development kit (SDK) to facilitate custom, intricate mission scenarios. During flight, Prism Supervisor adapts its autopilot functionality in real-time, dynamically generating mission segments and flight plans on the fly, minimising operator impact while improving mission success. For example, a Prism Supervisor-controlled UAV flying a search mission pattern can autonomously circle and alert the operator upon the detection of a human or threat. Operational performance "From behaviour and mission planning to dynamically adjust in-flight operations, Prism Supervisor represents a significant advancement for drone autonomy through AI," said Dan Walker, Vice President of Product Management, at Teledyne FLIR. "It improves operational performance via single-click missions, opening up new possibilities for UAS operation from commercial to military use cases." User-friendly GUI It can facilitate collaborative behaviours and synchronised mission execution among multiple UAVs Prism Supervisor simplifies the operator experience with a user-friendly graphic user interface (GUI) for mission planning, real-time mission visualisation, and execution. Available for desktop or mobile deployment supporting Windows, Linux, macOS, iOS, and Android, the supervised mission management application streams and records detailed, full-frame-rate video, path visualisation, and metadata. It can facilitate collaborative behaviours and synchronised mission execution among multiple unmanned aerial vehicles (UAVs). Advanced AI and image processing Prism Supervisor expands Teledyne FLIR's Prism digital ecosystem of advanced AI and image processing. It provides a platform for deploying object detection, tracking, and computational imaging on low-power processors, enhancing UAS mission performance and reducing development costs.
Aesthetic options, in addition to robust security features, are increasingly important to architectural door openings. Adams Rite delivers, expanding its finish offerings for the 8800 Series Starwheel Rim Exit Devices to include Black Suede Powder (BSP). 8800 Rim Exit Devices Adams Rite 8800 Rim Exit Devices offers reliable security, durable construction, and streamlined design for narrow stile aluminum doors. Its unique Starwheel bolt interlocks door to frame to provide enhanced strength and prevent jamb spread, while a clean profile and fewer pinch points make it ideal for high-traffic storefronts. Life-safety and fire-rated exit devices The 8800 is part of a premium series of life-safety and fire-rated exit devices by Adams Rite, available with a range of mechanical and electrical options, multiple finishes, and compatible products for a seamless solution. Adams Rite offers the most complete line of exit devices and related hardware solutions in the industry to effectively secure single and pairs of doors with a unified look, standardized installation, and operation in any facility.
Cequence Security, a pioneer in API security and bot management announced significant momentum in the Middle East and Africa (MEA) region, driven by rapid customer adoption, strategic partnerships, and a strengthened leadership team. This expansion further solidifies Cequence’s position as the go-to API security and bot management provider in the region, addressing the growing demand for advanced threat protection and digital risk mitigation. Modern digital transformation “APIs are the backbone of modern digital transformation, but they are also the most exploited attack surface,” said Ameya Talwalkar, CEO of Cequence Security. “We are not just expanding—we are transforming how businesses defend their digital assets. As the only solution that provides data sovereignty in the region, we empower enterprises with AI-driven security tailored to their unique regulatory and threat landscapes. By combining innovative threat intelligence with proactive defence, we enable organisations to anticipate and mitigate attacks before they impact operations.” MEA expansion Cequence’s expansion in MEA has been marked by: 1) New customer acquisitions across financial services, telecommunications, oil and gas, and technology, securing organisations such as: A top Islamic bank in the UAE. One of the largest financial institutions in the Middle East and Africa. A major telecom provider in Turkey. A digital transformation pioneer in the energy sector. 2) A 193% increase in ARR in the MEA region year-over-year. 3) A 68% increase in partner deal registrations, demonstrating strong market demand for Cequence’s Unified API Protection (UAP) platform. 4) An 83% increase in reseller partnerships, spanning KSA, UAE, Qatar, Jordan, Kuwait, Bahrain, and Egypt. 5) The planned signing of a strategic Memorandum of Understanding (MOU) at LEAP 2025 with a strategic GTM partner, underscores Cequence’s commitment to regional cybersecurity initiatives. 6) Hiring for multiple positions across various departments in the region reinforces Cequence’s investment in local talent and its commitment to long-term growth in the MEA. Strategic leadership appointment Ismail brings a proven track record of driving business growth and forging strategic alliances To drive Cequence’s expansion in MEA, the company has appointed Mohammad Ismail as its new Head of Go-to-Market (GTM) & Sales for EMEA, strategically based in Dubai to accelerate regional growth and customer success. With over 25 years of experience in cybersecurity and enterprise IT across the Middle East, Africa, and Southeast Asia, Ismail brings a proven track record of driving business growth and forging strategic alliances. Reliance on APIs “My focus at Cequence is to strengthen our presence in the EMEA region by deepening relationships with customers and partners,” said Mohammad Ismail, Head of GTM & Sales for EMEA. “With the increasing adoption of the growing reliance on APIs to power digital services, organisations need robust API security and bot management solutions. I look forward to leveraging my experience to expand our footprint, provide strategic guidance, and help customers stay ahead of evolving cyber threats.” Customer success and industry validation Cequence’s platform has helped organisations across MEA overcome critical API security and bot management challenges. Customers have leveraged Cequence to: Secure APIs during open banking transitions, ensuring compliance and real-time protection for sensitive financial data. Enhance API governance and security testing, integrating seamlessly with CI/CD pipelines to enforce OWASP Top 10 protections. Detect and stop sophisticated API attacks with AI-driven threat detection and real-time behavioral analysis, mitigating risks from shadow APIs and automated threats. Improve visibility and response times with comprehensive API activity monitoring, automated security enforcement, and automated enforcement with no human intervention. Meet stringent data sovereignty requirements, ensuring security policies remain within customer-controlled environments. These capabilities combined with Cequence’s unified approach, continue to drive strong adoption among MEA enterprises seeking to protect their digital environments. Investor confidence and market leadership Cequence’s expansion in MEA has garnered continued support from investors Cequence’s expansion in MEA has garnered continued support from investors, including Prosperity7 Ventures and Sanabil Investments. “The Middle East presents a unique and fast-growing opportunity for cybersecurity innovation, and Cequence is pioneering the charge with its best-in-class API security solutions,” said Abhishek Shukla, managing director and head of North America at Prosperity7 Ventures. “With an experienced leadership team, strong regional partnerships, and a relentless focus on innovation, Cequence is well-positioned to drive continued success in the MEA market.” Commitment to innovation As part of its ongoing commitment to innovation, Cequence has introduced new capabilities tailored to the MEA market, including: Expanded cloud and on-premises deployment options, ensuring compliance with regional data sovereignty requirements. Enhanced partner enablement programs, equipping resellers and service providers with advanced API security expertise. Protecting digital assets “With API threats growing more sophisticated, we remain focused on delivering cutting-edge security solutions that empower organisations to stay ahead of attackers,” added Talwalkar. “Our investment in MEA reflects our dedication to supporting businesses with the tools they need to protect their digital assets and maintain trust with their customers.” LEAP 2025 Cequence will be at Stand H1.D30 during LEAP 2025. Stop by to meet the team and learn more about how the industry-pioneering API security and bot management solutions can help protect the digital ecosystem. Join Ameya Talwalkar, CEO of Cequence, as he discusses the evolving API security and bot management landscape. His session will cover emerging threats, regional trends, and strategies for mitigating cyber risks. When: 7:30 PM - 7:50 PM Where: Stand H1.D30


Expert commentary
GSX 2023 marks a poignant moment for the security industry as an increasingly complex risk landscape converges with the acceleration of technology innovation. Emerging from this environment are three key trends that will dominate the conference and the future of the security industry: (i) the adoption of AI, (ii) the use of predictive analytics, and (iii) a hybrid global and local risk management approach. As Chief Security Officer of Crisis24, a GardaWorld company, I regularly advise clients on how these trends are evolving and impacting their security and risk management approach. Here’s how we can expect to see them discussed at the show next month: Trend 1: Artificial intelligence is the new industry standard. AI is this year's buzzword. While AI is not new to the industry, this year it has become a standard to operate with AI being adopted or expanded more ubiquitously. Legacy AI-enhanced security offerings that have been years in the making are becoming more advanced and are being integrated into expert analyst teams to leverage the best of both man and machine. Limitations AI augments the data processing ability; however, human-led intelligence is still necessary AI can generate unparalleled levels of data and insights, but it also has its limitations. AI does not have the emotional intelligence that can influence decision-making. For instance, our Crisis24 analyst teams know that every one of the intelligence alerts they provide to leadership may save a life or protect a business. AI augments the data processing ability; however, human-led intelligence is still necessary to effectively elevate knowledge of those threats through an organisation to incite action. Trend 2: Predictive analytics powered by AI will transform security operations. Predictive analytics enabled by AI will allow for more precise planning and execution of true emergency management. Those living or operating in conflict zones must be ready to spring into action and predictive analytics can help better evaluate risks, threat levels, and the probability of certain events. When I served in Iraq in 2003, our greatest challenge was operating in an unpredictable environment and navigating the many unknown threats. With these large-scale threats, it was difficult to account for the vast array of variables involved and ensure that all parties were protected. Broad and instant visibility Predictive analytics provides broad and instant visibility into numerous potential outcomes, impacts, and mitigation strategies for a wide variety of threats. When dealing with risks that are constantly evolving and quickly accelerating, the insights from predictive analytics can have a direct impact on risk management, mitigation strategies, and preparedness levels. Predictive analytics can anticipate the ripple effect that threats can have on organisations, their people, and their assets and enable security teams to plan. Trend 3: Risk mitigation is increasingly both global and hyper-local. A company’s workforce is often scattered across the country or the world, working from home or on the go Remote work and a flood of 24/7 data sources have driven demand for timely, accurate, and hyper-local intelligence. Where before an organisation may have had a handful of facilities around the world where its employees gathered, now a company’s workforce is often scattered across the country or the world, working from home or on the go. Preventive mitigation steps To keep their people and assets safe, business pioneers need to know what’s happening in all corners of the globe, while also easily accessing details on what is happening at the street corner level. How a business takes care of its people, including anticipating risks and taking preventive mitigation steps as well as responding quickly in the face of threats, can directly affect its reputation. Every company is in the business of safety and security when it comes to looking after its people on a global, national, and increasingly hyper-local scale.
Physical security is essential for a modern production facility, users don’t want just anyone entering the building or accessing secure areas. But what about production machinery? Machine authentication is often a missing link in the security plan for manufacturers. Why machine authentication? Most manufacturers have made significant investments in physical access control (PAC) for production facilities. Few shops currently hand out physical keys to employees or leave the building unlocked during production hours. For all but the smallest shops, front-door access typically involves individual radio-frequency identification (RFID) badges that enable tracking of who is coming and going and at what times. Use of physical keys, password login It is simply assumed that anyone who has access to the factory floor has the knowledge, authority, and training But when it comes to production machinery, many manufacturers still rely on physical keys, password login on the human-machine interface (HMI), or a shared PIN to unlock machine access. In some shops, machines may not be secured at all, it is simply assumed that anyone who has access to the factory floor has the knowledge, authority, and training to use the machines responsibly. However, this is not necessarily a good assumption, especially in a larger manufacturing plant where many people can access the production floor. Valuable and sensitive equipment CNC machines, robotic welders, process equipment, and other production machinery can cost anywhere from $5,000 to half a million or more, depending on their size and function. They also have significant safety risks for untrained users and may hold valuable and sensitive IP (such as customer design specs or batch recipes). User authentication Authenticating users at the machine level closes an important security loophole and makes plants safer and more productive. Machine authentication prevents untrained or unauthorised users from accessing production machinery. The right authentication system also allows access levels to be tailored for different users based on training credentials, job roles, or even projects. Machine authentication benefits A strong machine authentication solution provides several benefits for manufacturers: Minimises unplanned downtime and expensive damage to machines caused by untrained operators. Enables tracking of production outcomes by machine operator for better quality control and troubleshooting. Protects company and client IP held on the machine by preventing unauthorised access to machine controls and memory. Enhances plant safety and compliance by limiting machine access to operators with the appropriate credentials. Reduces the risk of deliberate sabotage by unauthorised operators, including damage to machines and production facilities and data theft or corruption. Mark Merino, the Director of the Digital Factory Group for Polaris Automation, explains, “Machine authentication allows us to identify which people are logged into different pieces of equipment and make sure they are trained appropriately for the machine and have the right clearances for the data they are trying to access.” Choosing the right machine authentication solution Access control for production machinery can be accomplished by various means, including password and PIN systems, physical keys or fobs, RFID badges, or smartphone-based mobile credentialing systems. The best machine authentication system will: Be highly reliable and secure to protect the machine from unauthorised access. Enable identification of individual operators and tracking of who has used the machines, at what times, and for what projects. Allow access levels to be differentiated by the user. Be easy to implement and administer. Discourage sharing or cloning of credentials. RFID readers An RFID reader can be easily connected to or integrated with the HMI for the machine In most manufacturing environments, the simplest solution for machine authentication is the RFID badge employees already carry for building entry. An RFID reader can be easily connected to or integrated with the HMI for the machine. All users must do to authenticate themselves is swipe their badge over the reader to unlock machine controls. RFID benefits RFID provides multiple benefits for end users, IT, and managers: It leverages technology already widely used, so users do not have to carry a separate key or fob to access machine controls. It is more secure and easier to manage than a password system, as passwords are frequently forgotten, shared, or hacked. Unlike shared PINs, physical keys, or fobs, user authentication via an ID badge enables accurate identification of who is logging into the machine. Users are much less likely to share their picture ID badge (which is often also linked to HR functions such as time and attendance) than a machine password, PIN, or key. If an ID badge is lost or stolen, or an employee leaves the company, IT can easily disable access to the card. RFID credentials are very difficult to hack or clone. Transmission between the reader and card can be encrypted for added security. Unlike biometric options, RFID is highly reliable even in hot, dirty, or humid environments and does not require workers to remove gloves, safety goggles, or masks. Getting started with machine authentication Machine authentication starts with selecting the right RFID reader. A universal RFID reader supports easy implementation, integration with other building systems, and scaling. A universal reader also provides flexibility for the future in case companies want to change transponder technologies or allow for user authentication using mobile credentials on a smartphone. IIoT model User authentication must be designed within the context of the wider security ecosystem of the plant To ensure the security of production machinery, user authentication must be designed within the context of the wider security ecosystem of the plant. Modern production machines are increasingly networked and connected in an “Industrial Internet of Things” (IIoT) model. That means machines are not only vulnerable themselves but are also endpoints in the broader IT landscape of the plant. Machine authentication systems must incorporate best practices for endpoint security, such as those outlined by ISO (International Organisation for Standardisation), NIST (National Institute of Standards and Technology), and other industry organisations. Best practices: The reader installation should be tamper-proofed to prevent physical disruption of the authentication system. Use an encryption standard suitable for the security level of the application. Encryption prevents data interception or card cloning. If higher security is desired, RFID can be implemented as part of a multi-factor authentication system along with biometrics and/or a password or PIN. The authentication system should support different access levels for different users or classes of users. A role-based permission system allows for different levels of access for line operators, supervisors, IT, and maintenance, for example. For maximum safety and security, individual users should only have the minimum access required to do their jobs. With secure machine authentication, manufacturers can protect people, production equipment, and IP, while enabling smooth operations. It all starts with an authentication system that supports reliable and secure operator identification at the machine level.
Inadequate security measures on your essential infrastructure can have severe consequences. Consequences Consider the rail industry: If a vandal cuts the cables on a vital mechanism that controls train signals, train safety is jeopardised. To avoid train collisions or derailments and thus significant damage to property and potential loss of life, the operating company must shut down the service until the infrastructure is repaired and the network is up and running again. The disruption affects the rail ecosystem itself, but also the people using the trains, the transportation of cargo, and more. The financial cost of repairing the damage, restoring signal functionality, and compensating for delays can be substantial. For another example, consider electrical substations: A fire or targeted attack can damage the system and lead to devastating power outages. Traditional surveillance limitations Traditional video surveillance has its limits when it comes to protecting transformer stations Traditional video surveillance has its limits when it comes to protecting transformer stations. The facilities are often located in rural areas, where straying animals or flying leaves trigger false alarms. 3D Surveillance solutions overcome these challenges by volumetrically securing the area and immediately detecting intruders only raising the alarm in the event of a human intruder and even identifying drone attacks. Protecting critical infrastructure with 3D surveillance Critical infrastructure must be monitored. It remains at risk if operators do not have systems for monitoring entire areas rather than just the periphery if security personnel has limited information in case of an intrusion and if security response protocols are not automated. 3D Surveillance solutions 3D Surveillance is an important tool for protecting critical infrastructure and ensuring the safety of those who rely on it. Integrating LiDAR technology, 3D Surveillance solutions provide a comprehensive view of the area being monitored with real-time monitoring and response, protecting critical infrastructure from damage and providing a more comprehensive security system. Advanced analytics and artificial intelligence Security personnel can identify and verify threats more easily and track the movements of individuals or vehicles, as well as respond to incidents as they happen. 3D Surveillance systems can be equipped with advanced analytics and artificial intelligence (AI) capabilities to detect patterns and anomalies that may indicate a potential threat. This can help to prevent potential attacks or accidents before they occur, as well as enable more accurate responses to incidents. Talent challenge Turning to autonomy by implementing sensor- and software-based solutions requires fewer if any, in-person patrols 3D Surveillance can also help tackle the talent challenge in the industry: Recruiting security professionals involves extensive background checks, and jobs in the industry are notorious for their low salaries, which results in high staff turnover. Turning to autonomy by implementing sensor- and software-based solutions requires fewer if any, in-person patrols and ensure reliable infrastructure protection. Additional security measures In many countries, more stringent legislation now mandates the implementation of additional security measures to safeguard critical infrastructure, particularly at a country's points of entry, such as airports and harbours. Protecting the perimeter is no longer enough. For instance, airport management must ensure that critical areas, including the space around aircraft and near unauthorised access points, are secure. While multi-layered screening of individuals at the perimeter is a valuable security measure, it must be complemented by smooth and efficient surveillance of the entire area, which can only be achieved through advanced technology. Different adoption rates 3D Surveillance technology is only beginning to gain traction in most locations, and adoption rates differ significantly from one region to another. For instance, Scandinavia and Eastern Europe have embraced 3D Surveillance to a greater extent than Western Europe. Regions with lower adoption rates will likely catch up as they seek to reinforce the security of their critical infrastructure, especially given the conflict in Eastern Europe. Vandalism and damage protection 3D Surveillance enhances the security of critical infrastructure, reduces the risk of downtime and loss of revenue 3D Surveillance offers reliable protection against vandalism and damage - major concerns for companies that rely on critical infrastructure. LiDAR-based, software-enhanced 3D Surveillance solutions provide real-time insights and enable automatic processing of the information so that operators can autonomously and quickly detect and respond to potential threats. These solutions are scalable and customisable, allowing companies to adapt their security measures to their unique needs and changing environments. 3D Surveillance enhances the security of critical infrastructure, reduces the risk of downtime and loss of revenue, and ensures compliance with regulatory requirements. Asset management and maintenance planning Beyond its security benefits, 3D Surveillance can help with tasks such as asset management and maintenance planning. It can help identify potential problems or maintenance needs before they become more serious issues by providing a real-time view of the monitored infrastructure. This can help to reduce downtime and keep critical infrastructure running smoothly. Real-time management The same technology can also perform volume monitoring tasks and thus facilitate the management of valuable resources such as bulk material, grain, wood chips, or chemicals. By scanning the stock 24/7 and automatically calculating stock volume updating records in real-time, this technology supports lean production systems and automated processing.
Security beat
Collaboration among manufacturers in the physical security industry can result in systems that are easier to install for integrators and that provide a better customer experience for end users. Illustrating the point is the recent collaboration among a turnstile technology company, a supplier of short-range wireless readers/writers, and a biometric business focused on ‘frictionless’ access control. “The more manufacturers collaborate with each other, the more benefits for end users,” says Steve Caroselli, the Chief Executive Officer (CEO) of Orion Entrance Control. Better collaboration means a better user experience We look for opportunities to collaborate and make sure the experience is above and beyond" Steve Caroselli adds, “Better collaboration means a better user experience. We look for opportunities to collaborate and make sure the experience is above and beyond.” Orion’s collaboration with ELATEC RFID Systems and SAFR touchless biometrics by RealNetworks Inc. highlights the advantages of manufacturers working together to ensure technologies operate smoothly in the real world. Taking ownership of the customer experience When Orion Entrance Control provides a SpeedGate swing-glass optical turnstile, they take full ownership of the customer’s experience. That means ensuring the turnstile application operates as it should, regardless of which component of the broader system might be at fault. To the customer experience, a card reader that doesn’t work is the equivalent of a turnstile that doesn’t work. Which component is at fault is irrelevant, and in fact, invisible, to the overall customer experience. Importance of dependable operation of turnstiles As the most visible element in many access control systems, dependable operation of turnstiles reflects positively on the manufacturer and on the entire system. Orion tests various third-party components with their turnstiles To ensure an optimum customer experience, Orion tests various third-party components with their turnstiles, in order to ensure flawless operation before a turnstile is delivered to a customer. Customers buying an Orion turnstile send the card readers they want to use to Orion’s corporate headquarters in Laconia, New Hampshire, USA, where Orion engineers ensure seamless operation. Ensuring optimum customer experience All readers are designed to be bolted to the wall rather than installed inside a turnstile In addition to scenario-based testing, readers are placed inside the turnstile for a streamline appearance, which can be a challenge given the variety of sizes and types of readers a customer might choose. All readers are designed to be bolted to the wall rather than installed inside a turnstile, which complicates adaptation efforts. In short, historically for Orion, ensuring the optimum customer experience involved extra time and effort, although obviously it was worth it. Providing flexibility for any environment Seeking to simplify the process, Orion has found an alternative to using many different types and models of card readers for its turnstiles. Deploying an RFID reader/writer from ELATEC provides flexibility to operate in a variety of card and reader environments, including almost all 125 kHz and 13.56 MHz contactless technologies. The product is compatible with low-frequency (LF), high-frequency (HF), near field communication (NFC) or Bluetooth Low Energy (BLE) signals. An integrated BLE module supports mobile ID and authentication solutions. There is an integrated antenna for LF and HF to ensure excellent contactless performance. ‘Universal’ configuration of the ELATEC reader hardware Using applicable firmware, the ‘universal’ configuration of the ELATEC reader hardware is compatible with any card system. It works with all the access control protocols, including SEOS, OSDP and other open protocols. “We can stock an open SKU and flash the firmware as per the customer requirement,” says Steve Caroselli. The small form factor (around 1 1/2 inches square) of the ELATEC module lends itself to easy installation inside the turnstile housing. Easy availability of the ELATEC readers helps Orion continue to serve customers, despite recent disruptions in the supply chain. And, ELATEC’s reader hardware has earned global certifications that enable Orion to use their products for customers around the world. Testing to ensure smooth operation ELATEC was responsive at every stage as the relationship evolved, providing sample equipment for testing Before embracing the ELATEC reader module, Orion tested it for several months to ensure compatibility with its turnstiles. ELATEC was responsive at every stage as the relationship evolved, providing sample equipment for testing and working closely with the Orion team. Everyone in the ELATEC sales and engineering team, right up the company’s C-suite, worked to support Orion during the testing phase. In the end, in addition to other advantages, ELATEC’s detection speed and read range compares favorably to competing technologies. “We move really fast as an organisation, so we are looking for other organisations that move very fast,” says Steve Caroselli, adding “We met with ELATEC one week and had the equipment for testing the next week. We like to work with companies that move fast, and they are culturally aligned with how we do business.” Orion turnstiles with ELATEC TWN4 Palon Compact panel The Orion turnstiles incorporate an ELATEC TWN4 Palon Compact panel, a versatile panel-mount reader designed for integration into third-party products and devices. It supports enhanced interfaces, especially RS-485, and reflects the advantages and integrated tool support of the ELATEC TWN4 family. Orion is implementing SAFR SCAN biometric technology using hardware and software from RealNetworks Inc. “The selection of ELATEC products allows Orion to provide their customers and partners with a flexible RFID reader solution that supports numerous credential options and virtually all transponder technologies,” said Paul Massey, the Chief Executive Officer (CEO) of ELATEC, Inc., adding “This is especially valuable in multi-tenet, multi-credential environments.” Orion works with all the various stakeholders – architects, consultants, integrators, and end users – to ensure total satisfaction with an installation. Biometric technology for ‘frictionless’ access control Orion is also implementing SAFR SCAN biometric technology into their turnstiles using hardware and software from RealNetworks Inc. The facial recognition reader technology, designed for mainstream commercial access control, provides a ‘frictionless’ experience, and allows users to pass through turnstiles at a walk. The system can authenticate up to 30 individuals per minute with 99.9% accuracy, despite varied lighting conditions. SAFR’s system provides a good user experience Orion designed a mounting system to incorporate the biometric reader into their turnstile design Orion designed a mounting system to incorporate the biometric reader into their turnstile design. SAFR’s system provides a good user experience, when it comes to enrollment. On each turnstile, the SAFR technology can operate separate from the ELATEC reader or in conjunction with it for multi-factor authentication in higher-security applications. Innovation for new applications A broad approach to the customer experience reflects Orion’s positioning as a technology company, in addition to being a manufacturer of turnstiles. Their Infinity software is the ecosystem ‘nerve centre’ platform to ensure operation and connected through a single ‘pane of glass.’ The need to protect more entrances beyond the lobby led Orion to develop its recently patented DoorGuard, a LIDAR-based solution that detects each person who passes through a doorway and prevents tailgating (like a turnstile) for applications, such as stairway doors, perimeter doors, data centres, IDF closets, etc. The software mimics the advantages of a turnstile to monitor access control and occupancy. Removing friction during installation and beyond Orion’s Constellation is a presence detection system that uses UWB (ultra-wideband) radar to sense where people are in a building for emergency response and building utilisation applications. “One of our core values is to remove friction and make customers’ lives easier,” says Steve Caroselli, adding “Our people-first philosophy is: What can we do to make your life better? We want to be systematic, and everything must be repeatable in terms of how we react and interact with customers.”
The Global Security Exchange (GSX 2022) in Atlanta in September 2022 is the latest example of the energetic post-COVID resurgence of security trade shows. On the vibrant show flow, discussions centered on topics such as the security industry’s need for more employees and the lingering impact of a months-long supply chain crisis. Against a backdrop of continuing industry challenges, exhibitors and attendees were diverted by a wealth of new opportunities as the industry rebounded. Several major players had big product announcements at GSX 2022 in Atlanta. Manufacturers unveil the latest technology The big news at Genetec was “5.11.” That’s the newest version of Security Center, which is “all in,” i.e., providing everything Genetec offers in a single “unified” platform. The unified approach streamlines the process for systems integrators, makes quotes easier, and adds value for customers. Standard, Pro, and Enterprise versions provide video, access, and LPR “right out of the box.” Genetec is also launching a new web and mobile client for the “next generation operator.” Paid intern programme Kyle Hurt says the security industry’s biggest challenge is attracting personnel Kyle Hurt, Genetec’s Senior Sales Director, North America, says the security industry’s biggest challenge is attracting personnel (even more challenging that the supply chain.) Genetec’s response is a robust paid intern programme, welcoming 120 interns into various departments for a full semester. The programme helps to feed Genetec’s need for new talent. “You can’t coach passion,” said Hurt. WiseNet Edge Hanwha Techwin introduced a “serverless camera” at GSX 2022, named the WiseNet Edge. It is a video camera with a built-in solid-state hard drive for storage. The camera can store its own video and take in other camera feeds. In effect, it operates like an NVR but is less expensive and with an internal solid-state drive. Video can be viewed through a cloud browser, and Hanwha’s WAVE software, loaded on the camera, enables the management of several cameras at a site. High-res video is stored inside the camera, and any information can be shared with the cloud according to the needs of the application. i-PRO Mini i-PRO launches its own Video Insight video management system and MonitorCast access control i-PRO has fully transitioned away from Panasonic and is charting its own ambitious future path. Seeking to be “bold, trusted, and flexible,” the company is releasing a raft of new products, filling in previous gaps in the line, and bringing forward new innovations, including a full complement of AI. In addition to hardware, they have their own Video Insight video management system and MonitorCast access control, which was part of the Video Insight acquisition in 2015. An i-PRO Mini is a tiny camera, smaller than a smartphone. All cameras are NDAA compliant. People are coming together “The show has been phenomenal,” said Josh Letourneau, Chief Commercial Officer, Prosegur USA. “It’s very nice to see that people are coming back. After the pandemic, we are finally in a position of coming together. Lots of organisations are coming to see us.” Intelligence-led risk management Prosegur is a global company looking to expand aggressively in the United States, creating multiple “metropolitan service areas,” where the company’s fully integrated offerings are available. What makes the company unique is its “intelligence-led risk management,” says Josh Letourneau, adding “It’s more than AI, it’s about human intelligence, too." Prosegur sees evolution and growth opportunities in the U.S. market. “We are one of the largest companies no one has heard of,” adds Letourneau. “The show seems as back to normal as possible,” said Keith Bobrosky, President of Delta Scientific, who attended the show although his company did not exhibit, adding “There seems to be a generally positive spirit about the show this year.” Physical security protocols Bobrosky sees data centres as the next big market for his company’s vehicle barriers Bobrosky’s company has worked aggressively to avoid the impact of supply chain issues, ordering plenty of extra inventory to avoid the possibility of a part running out of stock. “We got ahead of it and are past the worst of it,” he said. Bobrosky sees data centres as the next big market for his company’s vehicle barriers. “The government will mandate physical security protocols for cybersecurity locations because they house data that affects national security,” he says. Robots and indoor drones ADT Commercial highlighted robots and indoor drones for security apps at their booth. The newest versions of the humanlike robots offer extra padding, more fluid movement, and 360-degree viewing for a better virtual reality (VR) experience, including better peripheral vision. Robots can operate for four hours without a charge and “know” when to return to the charger (to “top off” every hour). Fully autonomous indoor drones can also replace guards, flying near the ceiling and generally after business hours. The use of either robots or drones can lower costs when compared to hiring human guards. Varied uses for canines in security Glen Kucera, Chief Executive Officer, MSA Security, highlighted the capabilities of canines for explosives and firearms detection. “People don’t realise the flexibility of what they can do,” he said. Kucera says canines provide a sophisticated solution to address the escalating active shooter and criminal threat. MSA Security was acquired last year by Allied Universal, adding to the company’s varied offerings for threat detection and management. Rather than individual products, Allied Universal’s emphasis at the show was on bringing solutions together. Their message: Risk is multi-dimensional and different from one client to the next. Access control Access control needs to develop more modern interfaces to compete with new technology companies AMAG’s news at the show included a new president, David Sullivan, who highlighted AMAG’s role as one of the “last independent access control companies.” He said, “The beauty of AMAG is its installed base and loyal integrator channel.” Sullivan sees changing trends in how office space is managed in the wake of the pandemic. More workplace management applications will emerge, with one of the elements being access control. Access control also needs to develop more modern interfaces to compete with new technology companies entering the market. An encouraging sign is that AMAG had its best year ever in 2021. Orion Entrance Control Orion Entrance Control showed off one of its modern new turnstiles at the RealNetworks/SAFR booth at GSX 2022. The turnstile incorporates an access control module from Elatec to update and expand card reader functionality. Using the module streamlines Orion’s processes and avoids having to update a customer’s readers individually. The turnstile at GSX also incorporated a facial recognition system from SAFR, which could be used instead of, or in addition to, the access control reader. Balancing the cloud and on-premise systems Salient Systems is looking to balance the use of on-premise and cloud systems and emphasise data instead of video. Rather than a single market, Salient sees security as a variety of smaller markets, each focused on different needs. Salient’s customers are typically larger and have multi-site deployments with thousands of cameras. On-premise systems appeal here because they offer an element of control. Open-platform APIs Internal teams at customer sites are seeking out and finding new ways to leverage the data from video systems “People have a keen interest in control and ownership of their data,” says Sanjay Challa, Chief Product Officer, Salient Systems. Internal teams at customer sites are seeking out and finding new ways to leverage the data from video systems, and some of the uses fall outside the traditional “security” market. Open-platform application programming interfaces (APIs) enable more integration with various systems, and broader applications enable customers to leverage budgets from other stakeholders in an organisation. Add-on services “They’re unwilling to shift the entire solution to the cloud, but they want to leverage cloud technologies,” says Challa. For Salient, a cloud system provides remote access to monitor and service video installation remotely. “We enable the integrator to reach into your system to provide a higher level of service,” says Sanjay Challa. He concludes, “Our add-on services bring the best of the cloud to on-premise systems, and integrators don’t have to roll a truck to solve a problem with the system. We are focused on helping integrators succeed.”
As new technologies incorporate artificial intelligence (AI) and overall uses of AI continue to expand, what protections are in place to prevent its misuse? Artificial intelligence, like any technology or security measure, is not inherently bad. It can, however, be used for nefarious purposes and in ways that were never intended or thought of. ‘Responsible AI Policy’ to protect users Prosegur has created a ‘Responsible AI Policy’ to protect users from potential AI threats As an AI company, Prosegur has created a ‘Responsible AI Policy’ to protect users from potential AI threats, and to prevent employee and partner misuse of AI-enabled technology, with guard rails in place to hold them accountable, if artificial intelligence is being used nefariously. “Any security or similar company that utilises AI with its products should monitor for potential misuse and implement a similar policy for protection,” contends Mike Dunn, the Chief Technology Officer (CTO) at Prosegur USA. Requirements of Prosegur’s ‘Responsible AI Policy’ include: Human action and oversight - Prosegur heavily monitors their agents using an integrated international security operations centre (iSOC). Floor and shift supervisors ensure that everything is working properly and that incidents are handled. They also ensure employees are logging into AI-enabled cameras and other technologies for the right reason. Transparency - As with any new company-wide policy, Prosegur wants to ensure that every employee learns about the policy and their duties to uphold it. “In doing this, we are making sure that all processes involving AI development are transparent, so any employee can understand and implement the policy into these processes,” says Mike Dunn. Non-discrimination and equity - Prosegur seeks to make sure employees are using AI-enabled technology to look for known criminals, for example, and not profiling or singling people out. Having a policy in place ensures agents are aware. Accountability - The most important part of the policy is to hold people accountable, if AI-enabled technologies are misused. Violation of the policy will result in disciplinary actions, which can range from HR (Human Resources) intervention to possible suspension. For partners, Prosegur would cease and desist using their products immediately upon finding out about any misuse. Leading the charge for ethical AI practices Prosegur is proud to lead the charge for ethical AI practices, by creating this first policy of its kind" “Prosegur is proud to lead the charge for ethical AI practices, by creating this first policy of its kind, and we hope that other security organisations follow suit,” says Mike Dunn. Technology can do wonderful things. In security, technology can help to stop crimes and even to prevent them from happening with deterrents and alarms. Important to take action to stop ‘bad actors’ However, as with any industry or group of people, there will be ‘bad actors.’ Mike Dunn said “It is important to take actions to stop those people, but it is also important not to condemn all technology or practices when this happens.” Even proven, effective technologies can be used for bad (as well as good). An example is TSA Scanners at the airports. They were designed to provide safer air travel, picking up things that normal metal detectors could miss. Misuse of AI technology can cause lot of harm However, it came to light that a few ‘bad actors’ were using this technology and sharing silhouetted nude pictures of passengers. This has since been patched and fixed, but nonetheless, it’s a great example of how misuse can break people’s trust. As a whole, technology can be dangerous. If not used as intended, it can be used to hurt people. The U.S. government has found that China was using facial recognition and demographic analytics to classify and identify people, based on their ethnicity and that technology singled them out for tracking. Important to ensure analytics and AI used as intended As a society, I think it’s important for us to take that first step and self-police any use of these analytics" “As a society, I think it’s important for us to take that first step and self-police any use of these analytics,” said Mike Dunn, adding “At a minimum, (we should) set policies and procedures to make sure these analytics and AI are being used as intended.” As use of artificial intelligence (AI) continues to increase, an industry standard would ensure companies have protections in place for their employees, clients, and partners. Having a policy is the first proactive step in ensuring AI protections. However, companies need to enforce accountability too. Effectively handle security threats and vulnerabilities Mike Dunn continues, “By heavily monitoring for unethical AI practices and enforcing disciplinary actions when needed, companies will be better prepared to handle security threats and vulnerabilities.” At Prosegur, monitoring agents are heavily trained, taught procedures and then closely supervised by several methods. “This is something that should be common practice in the security industry,” says Mike Dunn, adding “We have employed a compliance officer to help us stay ahead of the curve. Fortunately, we have seen many manufacturers and end users adopt this practice as well.” Compliance officers can act faster than new laws enacted Compliance officers can act faster than new laws being enacted, and often will hold their company to higher standards than a minimum threshold. Mike Dunn concludes, “Putting a responsible AI procedure in place is Prosegur’s way of taking on this problem we see in our everyday work.”
Case studies
ISS (Intelligent Security Systems), a global provider of video intelligence and data awareness solutions and systems integrator Wireless Guardian, who develops its patented security technology, announced the successful deployment of the SecurOS® UVSS (Under Vehicle Surveillance System) for vehicle screening at EverBank Stadium in Jacksonville, Florida, USA. UVSS units Engineers from the two companies worked with local law enforcement authorities along with officials from the stadium management company, ASM Global, and security firm S.A.F.E. Management to deploy UVSS units at the stadium’s loading docks and athlete/performer entries to scan all vehicles entering the facility. C&M Consultants, a Wireless Guardian reseller based in Northern Virginia, coordinated this event between ASM Global, Wireless Guardian, and ISS. AI-powered system ISS’ SecurOS® Auto LPR/ANPR software was also used to create a complete profile for each vehicle During the Monday Night (4th Dec 2023) Football game, approximately 100 vehicle undercarriages ranging from large delivery trucks and commercial vehicles to police and civilian cars and even golf carts were scanned by the AI-powered system to detect a wide variety of threats. In conjunction with the UVSS, ISS’ SecurOS® Auto LPR/ANPR software was also used to create a complete profile for each vehicle, including their class, colour, make, and model. Benefits of UVSS “ISS has a long history of providing solutions that secure large events, from the Rio Olympics to the recent FIFA World Cup in Qatar. Now, we are bringing these lessons learned to North America by partnering with Wireless Guardian to help stadiums and other venues take advantage of the benefits of our patented UVSS solution,” said Matt Powell, Managing Director for North America at ISS. He adds, “Our teams worked together flawlessly to deliver the results that ASM Global and EverBank Stadium needed on an important night, and I look forward to continuing this success with Wireless Guardian, combining solutions to provide full awareness at events and venues around the U.S.” How it works The SecurOS® UVSS from ISS is a compact solution specially designed to screen the undercarriage of vehicles for explosives, illegal contraband, damages/anomalies, and other prohibited items. In addition to providing high-quality undercarriage scans, the UVSS can also be integrated with licence plate recognition (LPR) and access control systems to provide a comprehensive solution for vehicle ingress and egress in a wide variety of operating environments. De-warping technology The UVSS has been trusted by government and law enforcement agencies as well as private sector The system, which does not require heavy construction to deploy, also features patented de-warping technology to provide unmatched correction of distortions and composite image stitching. The UVSS has been trusted by government and law enforcement agencies as well as private sector organisations worldwide to protect several high-profile facilities and events. Safe, fast, and efficient screening In late 2022, for example, the UVSS was deployed to protect stadiums and other venues throughout Qatar that hosted matches and events for the 2022 FIFA World Cup. Specifically, 40 UVSS units were installed at vehicle checkpoints for the eight World Cup stadiums in and around Doha, along with three logistics areas and a fan zone, to safeguard visitors and make the screening process safer, faster, and more efficient.
HID, a worldwide pioneer in trusted identity solutions, has been awarded a contract to provide Finland with a new high-security driver’s licence cards and personalisation services solution, incorporating the European second-generation smart Tachograph solution. This collaboration reflects HID’s commitment to enhancing security and efficiency in Finland's transportation systems. Configurable solution Finland will benefit from a comprehensive, tailor-made, and configurable solution that integrates software, hardware, and equipment to align with the Traffic Authority's vision of a streamlined and efficient digital document issuance system. For the project, HID has joined forces with CardPlus Systems, a trusted partner that provides secure ID documents, services, and systems, to ensure an exceptional driver's licence solution with industry-pioneering features. Security, efficiency, and compliance We will be able to ensure that our card services continue to meet the highest level of security" Max Fogdell, Head of Services for Driving licences and Examinations at Finland’s Transport and Communications Agency, Traficom, stated, "The Finnish Transport and Communications Agency, Traficom, is pleased to enter into a partnership with HID." "We are convinced that with HID's broad experience in the field of trusted identity solutions, we will be able to ensure that our card services continue to meet the highest level of security, efficiency, and compliance with the European Union's safety regulations.” Enhance drivers licence Craig Sandness, Senior Vice President and Head of Citizen Identity and Secure Issuance expressed his enthusiasm for the project, stating, "We are proud to collaborate with the government of Finland and contribute to the enhancement of the country's driver's licence and tachograph systems." "Our commitment to security and innovation is unwavering, and this contract is a testament to our dedication to safeguarding citizens and infrastructure." Safety standards and tachograph regulations With the European Union’s new safety standards and tachograph regulations, commercial vehicles in the region are required to install second-generation tachographs by 2026. HID’s advanced solution fully complies with these stringent regulations and includes smartcards securing access to device data for drivers, law enforcement, companies, and workshops.
SeeTrue, a global AI software solution pioneer for security screening, disclosed its recent entry into the realm of urban security through a strategic partnership with Israel Railways. This collaborative effort has resulted in the seamless integration of SeeTrue's cutting-edge AI solution into security screening checkpoints at railway stations throughout Israel, including the country's largest stations, where more than 1,000 bags require screening every hour. Faster, smoother security process The integration of SeeTrue into train station security processes has proven to be transformative, maintaining a consistently high level of security and operating continuously around the clock. Passengers benefit from a faster, smoother security process minimising stress and ensuring that critical security checks do not result in bottlenecks that can negatively impact the journey. Security screening solution This incident offers concrete proof of SeeTrue's invaluable contribution to ensuring public safety In a recent incident at one of the busiest and most central train stations, SeeTrue's AI security screening solution identified a bag containing a concealed 30-centimetre knife, alerting security personnel in real-time. As a result, the potential threat was swiftly and effectively neutralised, resulting in the arrest of the individual carrying the concealed knife. This incident offers concrete proof of SeeTrue's invaluable contribution to ensuring public safety in high-traffic transportation hubs. AI technology Assaf Frenkel, Co-Founder and CEO of SeeTrue, "We take immense pride in deepening our expertise in AI technology to include urban security, an endeavour that complements our pioneering work in aviation, customs, and other urban security checkpoints." Assaf Frenkel adds, "Partnering with a high-quality, innovative mass-transit organisation like Israel Railways is a testament to our commitment to revolutionising safety and security across multiple domains, making our cities and transportation systems safer and more efficient." Innovation and intelligence in railway security Hagay Rozenfeld, Head of Innovation, Israel Railways, said "Innovation at Israel Railways is a key part of our strategy, and AI plays a pivotal role in strengthening our pledge to passenger safety, seamlessly infusing intelligence into our security strategies and enabling us to provide optimal security for our passengers and our employees." Shaked Bar, Head of Security, Israel Railways, said "Acknowledging our responsibility to top-tier security at Israel Railways, we harness the power of AI to provide the highest security standards, ensuring the best passenger experience and safety."
For years, the Civil Police of the State of São Paulo, Brazil’s largest state police force faced significant challenges with criminal bookings and identification, including: A Fragmented Identity System - Each of Brazil’s 27 states has its own siloed programme that does not interconnect. This not only hinders statewide criminal booking but also undermines the community’s confidence in the criminal justice system. Identity Fraud With Multiple IDs - Imagine having 43 identities. This was the case for one unlawful Brazilian. The prevalence of identity fraud is extremely high across the country. If a person wants to hide their identity, it’s common for them to simply move to another state and set up a new profile. Manual Ink-and-Paper Fingerprinting Techniques - Many law enforcement departments across Brazil administered manual fingerprinting techniques, resulting in inaccuracies and low matching rates. Slow, Inefficient Criminal Booking Processes - Inefficiency was another setback for justice. It took numerous steps to confirm one’s identity and, on average, a whole workweek to get matching results returned. Biometric National ID Compliance - The civil police must modernise systems to comply with the Brazilian government’s mandates for all citizens to tie biometrics to their IDs. The Civil Police of the State of São Paulo needed a more reliable and efficient solution to break down identification silos and put the agency on the path toward a unified, national system rooted in the power of biometrics. HID's solution The HID ten-print scanner is designed to quickly capture flat and rolled fingerprints for background checks Working through HID’s partner, Golden Distribuidora, one of Brazil’s largest distributors of IT products, the Civil Police of the State of São Paulo selected a comprehensive biometrics-based identification system called BioKit, featuring HID’s ten-print scanner. The HID ten-print scanner is designed to quickly capture flat and rolled fingerprints for background checks and identity validation programmes. It is also certified for FBI Appendix F (FAP 60) and offers an economical approach to fingerprint acquisition without sacrificing image quality. Automated Biometric Identification System The criminal booking process at São Paulo civil police stations is simplified and can be accomplished in minutes not days. First, agents use HID’s ten-print scanner to capture fingerprints and determine if the individual has a biometric file on record. The fingerprint images are compared against the state-run Automated Biometric Identification System (ABIS). If there is a match, the civil police move forward with their investigation. If there is no match, the officer then creates a new biographic/biometric profile for the individual in question and enrolls them into the ABIS. HID ten-print scanner HID ten-print scanners deliver superior performance and reliability at a competitive price point. Key advantages include: High-Quality Tenprint Capture - The scanner is FBI Appendix F (FAP 60) certified and can quickly capture high-resolution rolled and flat fingerprints. Ease of Use - User-friendly pictographs and LED indicators simplify the process for operators. Automatic Capture - Patented “Auto-Capture” offers fast and error-free image capture. Difficult Fingerprint Capability - An optional silicone membrane improves image quality for dry or damaged skin ensuring consistent results. ABIS Integration - The scanner seamlessly integrates with Brazil’s Automated Biometric Identification System (ABIS) to enable quick and accurate background checks. Results delivered Using the BioKit system, featuring the HID ten-print scanner significantly streamlines the criminal booking Using the BioKit system, featuring the HID ten-print scanner significantly streamlines the criminal booking process and improves matching accuracy for the State of São Paulo Civil Police. “Working with criminals can be difficult and dangerous, and the HID ten-print scanners help us identify and book criminals quickly and simply,” said Dr. Luiz Ortiz, Chief Delegate, Civil Police of the State of São Paulo. Easy to use Dr. Luiz Ortiz adds, “The HID ten-print scanner is easy to use and provides clear direction through pictographs, which is a big differentiator from other offerings.” To date, the BioKit system with HID’s print scanners is deployed in 500 civil police stations throughout São Paulo. This system has transformed criminal booking and identification processes, resulting in an increase in solved criminal cases and a steep reduction in identity fraud. HID fingerprint technology “What used to take 4 to 5 days is now done in minutes using the BioKit system and HID fingerprint technology,” said Dr. Ortiz. Dr. Ortiz adds, “Our agents can accurately identify or onboard suspects, and each new biometric enrollment into the centralised ABIS contributes to strengthening our country’s overall identity system and ability to bring about justice faster and smarter.” Biometric enrollment and verification “Each individual the Civil Police of the State of São Paulo onboards ties to a single set of fingerprints that verifies their true identity,” said Danilo Fernandes, Business Development Manager at Golden Distribuidora. Danilo Fernandes adds, “Utilising biometric enrollment and verification, our nation has the potential to streamline millions of records, while preventing countless cases of fraud. This establishes a fierce force to fight fraud here in Brazil.” A simple, fast, and trusted experience Additional use cases for the BioKit + HID ten-print scanner, beyond criminal bookings, include border control, background checks, correctional centres, courtrooms, voter registration, and national ID programmes. The team at Golden Distribuidora expects to continue distributing these biometric systems throughout the country to support Brazil in combating fraud and making biometric enrollment and identification a simple, fast, and trusted experience for all citizens and stakeholders.
As an Indian multinational public sector bank, this financial services entity plays a crucial role in bolstering India’s economy and addressing the diverse needs of its vast customer base. In the United Kingdom, this institution has been active since the early 1900s, gradually growing to become the largest Indian bank in the UK. Initially, its focus in the UK market was on wholesale banking, but it has since expanded its offerings to include a dedicated retail arm. Financial products and services Operating 11 branches across the UK, it provides a wide range of financial products and services tailored to both commercial and individual clients. These include commercial lending, buy-to-let mortgages, cash ISAs, safe deposit lockers, instant access savings accounts, business accounts, and fixed deposits. Overview The institution faced operational inefficiencies and security concerns due to maintaining separate software Confronted with the challenge of integrating attendance and payroll software, along with the inability to effectively restrict unauthorised access to its secured premises across 14 locations, a prominent financial institution sought a comprehensive multi-location solution. Additionally, the institution faced operational inefficiencies and security concerns due to maintaining separate software platforms for employee directories. Need for a cloud-based attendance system To address these issues, the institution sought an integrated cloud-based attendance system that seamlessly integrates with payroll, enhances access control measures, and consolidates employee directory management. This solution aimed to ensure streamlined operations and heightened security across its premises. Institution's challenge The challenges centered around implementing a cloud-based attendance system and access management processes, as detailed below: Need for Integrated Attendance and Payroll Software The financial institution faced difficulties managing attendance and payroll software separately, resulting in inefficiencies and potential discrepancies in salary processing. There was an urgent need to integrate these systems to ensure seamless data flow and improve payroll management. Inadequate Entry and Exit Security Measures The institution struggled to restrict unauthorised entry and exit into its secured premises, posing significant security risks. Strengthening access control measures was essential to mitigate the threat of unauthorised access and protect personnel and assets. Need for a Single Employee Directory Using different software for employee directories created complexity and inefficiency Using different software for employee directories created complexity and inefficiency in administrative processes. It was crucial to consolidate employee directory management into a single platform to ensure accurate, consistent, and easily accessible employee information. Need for a Dedicated Server to Safeguard Data Integrity and Compliance The client had stringent requirements regarding data usage, with a key stipulation being that their main servers could not be used to manage third-party applications. This necessitated the implementation of a separate server or a cloud-based attendance system to host third-party applications and services, ensuring strict data protection measures and compliance with relevant regulations. These challenges highlighted the need for comprehensive solutions to improve operational efficiency, security, and data management within the financial institution. Matrix solution To tackle the challenges faced by the financial institution, Matrix delivered comprehensive solutions, including a cloud-based attendance system that transformed its attendance management processes: Integration of Events and Payroll Software: Matrix seamlessly merged the institution's event logs and payroll software, Darwin Box, through API Integration, guaranteeing synchronised data flow. Through this consolidation, Matrix facilitated smooth payroll processing, lessening inefficiencies, and decreasing the likelihood of discrepancies in salary management. Enhancement of Entry and Exit Security Measures: Utilising advanced technology, Matrix enhanced security protocols, reducing potential risks Matrix deployed proactive access control measures to strengthen the institution's premises against unauthorised entry and exit. Utilising advanced technology, Matrix enhanced security protocols, reducing potential risks and effectively protecting personnel and assets. Unified Employee Directory Management: Matrix unified the institution's management of employee directories by offering a centralised platform. By consolidating employee data, Matrix optimised the system so that updates made in the payroll software would automatically synchronise with the COSEC software, ensuring precise, uniform, and easily accessible vital employee information. Implementation of Cloud-based Solution: Due to a strict restriction on using the COSEC application on their primary server, Matrix proposed and implemented COSEC VYOM, a cloud-based attendance system tailored to their requirements. Moreover, this system was seamlessly linked with their payroll system through API Integration. Results observed Matrix's comprehensive solutions brought significant enhancements across various facets of the financial institution's operations, yielding measurable improvements in efficiency, security, and compliance: Efficient Payroll Processing: By integrating event logs and payroll software, Matrix facilitated seamless data flow and streamlined payroll By integrating event logs and payroll software, Matrix facilitated seamless data flow and streamlined payroll processing. This consolidation minimised inefficiencies and reduced discrepancies in salary management, causing more accurate and efficient payroll operations. Improved Premises Security: Matrix's proactive implementation of access control technology, Matrix fortified entry and exit points, mitigating security risks, and effectively safeguarding personnel and assets. Centralised Employee Directory Management: Through a unified platform for employee directory management, Matrix streamlined administrative processes and ensured consistency and accuracy in employee data. Changes made in the COSEC application automatically updated the payroll software, reducing manual effort and error. Compliance with Data Protection Regulations via Cloud-Based Attendance System: Matrix's provision of COSEC VYOM, a cloud-based attendance system, helped ensure compliance with strict data protection requirements. By segregating data and applications, Matrix improved data integrity and ensured adherence to regulations, minimising the risk of data breaches and non-compliance penalties. Operational efficiency, security, compliance Matrix's solutions not only tackled the financial institution's challenges but also delivered tangible enhancements In summary, Matrix's solutions not only tackled the financial institution's challenges but also delivered tangible enhancements in operational efficiency, security, compliance, and data management. Matrix contributed to the institution's effectiveness and resilience in the financial sector through integrated systems and innovative solutions. Products offered COSEC ARGO CAM200: MiFare Classic Card-Based Ultra Fast Door Controller COSEC VYOM TENANT: Tenant User Licence COSEC VYOM PLATFORM UD10K: Cloud-based Platform User Licence for 10K User Days COSEC VYOM PLATFORM UD100K: Cloud-based Platform User Licence for 100K User Days
RecFaces, a facial recognition software company, has announced the successful deployment of its flagship product, Id-Guard at Jorge Chávez International Airport in Lima, Peru. This implementation marks a significant milestone in bolstering security measures at one of South America's busiest airports, underscoring the importance of maintaining a high level of safety at public transportation hubs. Jorge Chávez International Airport Jorge Chávez International Airport serves as a vital gateway for travellers and cargo, welcoming more than 20 million international and national passengers every year. With such a high flow of people, ensuring the safety and security of passengers and airport personnel becomes crucial. Recognising this need, RecFaces collaborated with airport authorities to implement their state-of-the-art Id-Guard solution and help ensure the safety of the facility. Enhanced security measures The solution's features enable airport authorities to prevent suspicious individuals from accessing the site The implementation of Id-Guard has significantly enhanced security measures, allowing for proactive monitoring and rapid response to potential security threats. The solution's features enable airport authorities to prevent suspicious individuals from accessing the site, thereby safeguarding the safety of passengers and staff. Highest level of security “Airport representatives felt the need for facial recognition to strengthen the security structure within the airport as a whole,” notes Maria Kazhuro, Business Development Director for the LATAM region, RecFaces. Maria Kazhuro adds, “Our goal was not only to provide the highest level of security but also to simplify work processes for security guards. We can confidently say that the installation of an ID guard has significantly improved security in the facility. Now both airport visitors and employees can be sure that they are under even greater protection than before.” Id-Guard facial recognition The deployment of Id-Guard at the Peruvian airport demonstrates RecFaces' dedication to excellence and innovation in the field of facial recognition technology. As airports worldwide continue to prioritise security and passenger experience, RecFaces remains at the forefront of delivering advanced biometric solutions tailored to the evolving needs of the aviation industry.
ISS (Intelligent Security Systems), a global provider of video intelligence and data awareness solutions and systems integrator Wireless Guardian, who develops its patented security technology, announced the successful deployment of the SecurOS® UVSS (Under Vehicle Surveillance System) for vehicle screening at EverBank Stadium in Jacksonville, Florida, USA. UVSS units Engineers from the two companies worked with local law enforcement authorities along with officials from the stadium management company, ASM Global, and security firm S.A.F.E. Management to deploy UVSS units at the stadium’s loading docks and athlete/performer entries to scan all vehicles entering the facility. C&M Consultants, a Wireless Guardian reseller based in Northern Virginia, coordinated this event between ASM Global, Wireless Guardian, and ISS. AI-powered system ISS’ SecurOS® Auto LPR/ANPR software was also used to create a complete profile for each vehicle During the Monday Night (4th Dec 2023) Football game, approximately 100 vehicle undercarriages ranging from large delivery trucks and commercial vehicles to police and civilian cars and even golf carts were scanned by the AI-powered system to detect a wide variety of threats. In conjunction with the UVSS, ISS’ SecurOS® Auto LPR/ANPR software was also used to create a complete profile for each vehicle, including their class, colour, make, and model. Benefits of UVSS “ISS has a long history of providing solutions that secure large events, from the Rio Olympics to the recent FIFA World Cup in Qatar. Now, we are bringing these lessons learned to North America by partnering with Wireless Guardian to help stadiums and other venues take advantage of the benefits of our patented UVSS solution,” said Matt Powell, Managing Director for North America at ISS. He adds, “Our teams worked together flawlessly to deliver the results that ASM Global and EverBank Stadium needed on an important night, and I look forward to continuing this success with Wireless Guardian, combining solutions to provide full awareness at events and venues around the U.S.” How it works The SecurOS® UVSS from ISS is a compact solution specially designed to screen the undercarriage of vehicles for explosives, illegal contraband, damages/anomalies, and other prohibited items. In addition to providing high-quality undercarriage scans, the UVSS can also be integrated with licence plate recognition (LPR) and access control systems to provide a comprehensive solution for vehicle ingress and egress in a wide variety of operating environments. De-warping technology The UVSS has been trusted by government and law enforcement agencies as well as private sector The system, which does not require heavy construction to deploy, also features patented de-warping technology to provide unmatched correction of distortions and composite image stitching. The UVSS has been trusted by government and law enforcement agencies as well as private sector organisations worldwide to protect several high-profile facilities and events. Safe, fast, and efficient screening In late 2022, for example, the UVSS was deployed to protect stadiums and other venues throughout Qatar that hosted matches and events for the 2022 FIFA World Cup. Specifically, 40 UVSS units were installed at vehicle checkpoints for the eight World Cup stadiums in and around Doha, along with three logistics areas and a fan zone, to safeguard visitors and make the screening process safer, faster, and more efficient.
HID, a worldwide pioneer in trusted identity solutions, has been awarded a contract to provide Finland with a new high-security driver’s licence cards and personalisation services solution, incorporating the European second-generation smart Tachograph solution. This collaboration reflects HID’s commitment to enhancing security and efficiency in Finland's transportation systems. Configurable solution Finland will benefit from a comprehensive, tailor-made, and configurable solution that integrates software, hardware, and equipment to align with the Traffic Authority's vision of a streamlined and efficient digital document issuance system. For the project, HID has joined forces with CardPlus Systems, a trusted partner that provides secure ID documents, services, and systems, to ensure an exceptional driver's licence solution with industry-pioneering features. Security, efficiency, and compliance We will be able to ensure that our card services continue to meet the highest level of security" Max Fogdell, Head of Services for Driving licences and Examinations at Finland’s Transport and Communications Agency, Traficom, stated, "The Finnish Transport and Communications Agency, Traficom, is pleased to enter into a partnership with HID." "We are convinced that with HID's broad experience in the field of trusted identity solutions, we will be able to ensure that our card services continue to meet the highest level of security, efficiency, and compliance with the European Union's safety regulations.” Enhance drivers licence Craig Sandness, Senior Vice President and Head of Citizen Identity and Secure Issuance expressed his enthusiasm for the project, stating, "We are proud to collaborate with the government of Finland and contribute to the enhancement of the country's driver's licence and tachograph systems." "Our commitment to security and innovation is unwavering, and this contract is a testament to our dedication to safeguarding citizens and infrastructure." Safety standards and tachograph regulations With the European Union’s new safety standards and tachograph regulations, commercial vehicles in the region are required to install second-generation tachographs by 2026. HID’s advanced solution fully complies with these stringent regulations and includes smartcards securing access to device data for drivers, law enforcement, companies, and workshops.
SeeTrue, a global AI software solution pioneer for security screening, disclosed its recent entry into the realm of urban security through a strategic partnership with Israel Railways. This collaborative effort has resulted in the seamless integration of SeeTrue's cutting-edge AI solution into security screening checkpoints at railway stations throughout Israel, including the country's largest stations, where more than 1,000 bags require screening every hour. Faster, smoother security process The integration of SeeTrue into train station security processes has proven to be transformative, maintaining a consistently high level of security and operating continuously around the clock. Passengers benefit from a faster, smoother security process minimising stress and ensuring that critical security checks do not result in bottlenecks that can negatively impact the journey. Security screening solution This incident offers concrete proof of SeeTrue's invaluable contribution to ensuring public safety In a recent incident at one of the busiest and most central train stations, SeeTrue's AI security screening solution identified a bag containing a concealed 30-centimetre knife, alerting security personnel in real-time. As a result, the potential threat was swiftly and effectively neutralised, resulting in the arrest of the individual carrying the concealed knife. This incident offers concrete proof of SeeTrue's invaluable contribution to ensuring public safety in high-traffic transportation hubs. AI technology Assaf Frenkel, Co-Founder and CEO of SeeTrue, "We take immense pride in deepening our expertise in AI technology to include urban security, an endeavour that complements our pioneering work in aviation, customs, and other urban security checkpoints." Assaf Frenkel adds, "Partnering with a high-quality, innovative mass-transit organisation like Israel Railways is a testament to our commitment to revolutionising safety and security across multiple domains, making our cities and transportation systems safer and more efficient." Innovation and intelligence in railway security Hagay Rozenfeld, Head of Innovation, Israel Railways, said "Innovation at Israel Railways is a key part of our strategy, and AI plays a pivotal role in strengthening our pledge to passenger safety, seamlessly infusing intelligence into our security strategies and enabling us to provide optimal security for our passengers and our employees." Shaked Bar, Head of Security, Israel Railways, said "Acknowledging our responsibility to top-tier security at Israel Railways, we harness the power of AI to provide the highest security standards, ensuring the best passenger experience and safety."
For years, the Civil Police of the State of São Paulo, Brazil’s largest state police force faced significant challenges with criminal bookings and identification, including: A Fragmented Identity System - Each of Brazil’s 27 states has its own siloed programme that does not interconnect. This not only hinders statewide criminal booking but also undermines the community’s confidence in the criminal justice system. Identity Fraud With Multiple IDs - Imagine having 43 identities. This was the case for one unlawful Brazilian. The prevalence of identity fraud is extremely high across the country. If a person wants to hide their identity, it’s common for them to simply move to another state and set up a new profile. Manual Ink-and-Paper Fingerprinting Techniques - Many law enforcement departments across Brazil administered manual fingerprinting techniques, resulting in inaccuracies and low matching rates. Slow, Inefficient Criminal Booking Processes - Inefficiency was another setback for justice. It took numerous steps to confirm one’s identity and, on average, a whole workweek to get matching results returned. Biometric National ID Compliance - The civil police must modernise systems to comply with the Brazilian government’s mandates for all citizens to tie biometrics to their IDs. The Civil Police of the State of São Paulo needed a more reliable and efficient solution to break down identification silos and put the agency on the path toward a unified, national system rooted in the power of biometrics. HID's solution The HID ten-print scanner is designed to quickly capture flat and rolled fingerprints for background checks Working through HID’s partner, Golden Distribuidora, one of Brazil’s largest distributors of IT products, the Civil Police of the State of São Paulo selected a comprehensive biometrics-based identification system called BioKit, featuring HID’s ten-print scanner. The HID ten-print scanner is designed to quickly capture flat and rolled fingerprints for background checks and identity validation programmes. It is also certified for FBI Appendix F (FAP 60) and offers an economical approach to fingerprint acquisition without sacrificing image quality. Automated Biometric Identification System The criminal booking process at São Paulo civil police stations is simplified and can be accomplished in minutes not days. First, agents use HID’s ten-print scanner to capture fingerprints and determine if the individual has a biometric file on record. The fingerprint images are compared against the state-run Automated Biometric Identification System (ABIS). If there is a match, the civil police move forward with their investigation. If there is no match, the officer then creates a new biographic/biometric profile for the individual in question and enrolls them into the ABIS. HID ten-print scanner HID ten-print scanners deliver superior performance and reliability at a competitive price point. Key advantages include: High-Quality Tenprint Capture - The scanner is FBI Appendix F (FAP 60) certified and can quickly capture high-resolution rolled and flat fingerprints. Ease of Use - User-friendly pictographs and LED indicators simplify the process for operators. Automatic Capture - Patented “Auto-Capture” offers fast and error-free image capture. Difficult Fingerprint Capability - An optional silicone membrane improves image quality for dry or damaged skin ensuring consistent results. ABIS Integration - The scanner seamlessly integrates with Brazil’s Automated Biometric Identification System (ABIS) to enable quick and accurate background checks. Results delivered Using the BioKit system, featuring the HID ten-print scanner significantly streamlines the criminal booking Using the BioKit system, featuring the HID ten-print scanner significantly streamlines the criminal booking process and improves matching accuracy for the State of São Paulo Civil Police. “Working with criminals can be difficult and dangerous, and the HID ten-print scanners help us identify and book criminals quickly and simply,” said Dr. Luiz Ortiz, Chief Delegate, Civil Police of the State of São Paulo. Easy to use Dr. Luiz Ortiz adds, “The HID ten-print scanner is easy to use and provides clear direction through pictographs, which is a big differentiator from other offerings.” To date, the BioKit system with HID’s print scanners is deployed in 500 civil police stations throughout São Paulo. This system has transformed criminal booking and identification processes, resulting in an increase in solved criminal cases and a steep reduction in identity fraud. HID fingerprint technology “What used to take 4 to 5 days is now done in minutes using the BioKit system and HID fingerprint technology,” said Dr. Ortiz. Dr. Ortiz adds, “Our agents can accurately identify or onboard suspects, and each new biometric enrollment into the centralised ABIS contributes to strengthening our country’s overall identity system and ability to bring about justice faster and smarter.” Biometric enrollment and verification “Each individual the Civil Police of the State of São Paulo onboards ties to a single set of fingerprints that verifies their true identity,” said Danilo Fernandes, Business Development Manager at Golden Distribuidora. Danilo Fernandes adds, “Utilising biometric enrollment and verification, our nation has the potential to streamline millions of records, while preventing countless cases of fraud. This establishes a fierce force to fight fraud here in Brazil.” A simple, fast, and trusted experience Additional use cases for the BioKit + HID ten-print scanner, beyond criminal bookings, include border control, background checks, correctional centres, courtrooms, voter registration, and national ID programmes. The team at Golden Distribuidora expects to continue distributing these biometric systems throughout the country to support Brazil in combating fraud and making biometric enrollment and identification a simple, fast, and trusted experience for all citizens and stakeholders.
As an Indian multinational public sector bank, this financial services entity plays a crucial role in bolstering India’s economy and addressing the diverse needs of its vast customer base. In the United Kingdom, this institution has been active since the early 1900s, gradually growing to become the largest Indian bank in the UK. Initially, its focus in the UK market was on wholesale banking, but it has since expanded its offerings to include a dedicated retail arm. Financial products and services Operating 11 branches across the UK, it provides a wide range of financial products and services tailored to both commercial and individual clients. These include commercial lending, buy-to-let mortgages, cash ISAs, safe deposit lockers, instant access savings accounts, business accounts, and fixed deposits. Overview The institution faced operational inefficiencies and security concerns due to maintaining separate software Confronted with the challenge of integrating attendance and payroll software, along with the inability to effectively restrict unauthorised access to its secured premises across 14 locations, a prominent financial institution sought a comprehensive multi-location solution. Additionally, the institution faced operational inefficiencies and security concerns due to maintaining separate software platforms for employee directories. Need for a cloud-based attendance system To address these issues, the institution sought an integrated cloud-based attendance system that seamlessly integrates with payroll, enhances access control measures, and consolidates employee directory management. This solution aimed to ensure streamlined operations and heightened security across its premises. Institution's challenge The challenges centered around implementing a cloud-based attendance system and access management processes, as detailed below: Need for Integrated Attendance and Payroll Software The financial institution faced difficulties managing attendance and payroll software separately, resulting in inefficiencies and potential discrepancies in salary processing. There was an urgent need to integrate these systems to ensure seamless data flow and improve payroll management. Inadequate Entry and Exit Security Measures The institution struggled to restrict unauthorised entry and exit into its secured premises, posing significant security risks. Strengthening access control measures was essential to mitigate the threat of unauthorised access and protect personnel and assets. Need for a Single Employee Directory Using different software for employee directories created complexity and inefficiency Using different software for employee directories created complexity and inefficiency in administrative processes. It was crucial to consolidate employee directory management into a single platform to ensure accurate, consistent, and easily accessible employee information. Need for a Dedicated Server to Safeguard Data Integrity and Compliance The client had stringent requirements regarding data usage, with a key stipulation being that their main servers could not be used to manage third-party applications. This necessitated the implementation of a separate server or a cloud-based attendance system to host third-party applications and services, ensuring strict data protection measures and compliance with relevant regulations. These challenges highlighted the need for comprehensive solutions to improve operational efficiency, security, and data management within the financial institution. Matrix solution To tackle the challenges faced by the financial institution, Matrix delivered comprehensive solutions, including a cloud-based attendance system that transformed its attendance management processes: Integration of Events and Payroll Software: Matrix seamlessly merged the institution's event logs and payroll software, Darwin Box, through API Integration, guaranteeing synchronised data flow. Through this consolidation, Matrix facilitated smooth payroll processing, lessening inefficiencies, and decreasing the likelihood of discrepancies in salary management. Enhancement of Entry and Exit Security Measures: Utilising advanced technology, Matrix enhanced security protocols, reducing potential risks Matrix deployed proactive access control measures to strengthen the institution's premises against unauthorised entry and exit. Utilising advanced technology, Matrix enhanced security protocols, reducing potential risks and effectively protecting personnel and assets. Unified Employee Directory Management: Matrix unified the institution's management of employee directories by offering a centralised platform. By consolidating employee data, Matrix optimised the system so that updates made in the payroll software would automatically synchronise with the COSEC software, ensuring precise, uniform, and easily accessible vital employee information. Implementation of Cloud-based Solution: Due to a strict restriction on using the COSEC application on their primary server, Matrix proposed and implemented COSEC VYOM, a cloud-based attendance system tailored to their requirements. Moreover, this system was seamlessly linked with their payroll system through API Integration. Results observed Matrix's comprehensive solutions brought significant enhancements across various facets of the financial institution's operations, yielding measurable improvements in efficiency, security, and compliance: Efficient Payroll Processing: By integrating event logs and payroll software, Matrix facilitated seamless data flow and streamlined payroll By integrating event logs and payroll software, Matrix facilitated seamless data flow and streamlined payroll processing. This consolidation minimised inefficiencies and reduced discrepancies in salary management, causing more accurate and efficient payroll operations. Improved Premises Security: Matrix's proactive implementation of access control technology, Matrix fortified entry and exit points, mitigating security risks, and effectively safeguarding personnel and assets. Centralised Employee Directory Management: Through a unified platform for employee directory management, Matrix streamlined administrative processes and ensured consistency and accuracy in employee data. Changes made in the COSEC application automatically updated the payroll software, reducing manual effort and error. Compliance with Data Protection Regulations via Cloud-Based Attendance System: Matrix's provision of COSEC VYOM, a cloud-based attendance system, helped ensure compliance with strict data protection requirements. By segregating data and applications, Matrix improved data integrity and ensured adherence to regulations, minimising the risk of data breaches and non-compliance penalties. Operational efficiency, security, compliance Matrix's solutions not only tackled the financial institution's challenges but also delivered tangible enhancements In summary, Matrix's solutions not only tackled the financial institution's challenges but also delivered tangible enhancements in operational efficiency, security, compliance, and data management. Matrix contributed to the institution's effectiveness and resilience in the financial sector through integrated systems and innovative solutions. Products offered COSEC ARGO CAM200: MiFare Classic Card-Based Ultra Fast Door Controller COSEC VYOM TENANT: Tenant User Licence COSEC VYOM PLATFORM UD10K: Cloud-based Platform User Licence for 10K User Days COSEC VYOM PLATFORM UD100K: Cloud-based Platform User Licence for 100K User Days
RecFaces, a facial recognition software company, has announced the successful deployment of its flagship product, Id-Guard at Jorge Chávez International Airport in Lima, Peru. This implementation marks a significant milestone in bolstering security measures at one of South America's busiest airports, underscoring the importance of maintaining a high level of safety at public transportation hubs. Jorge Chávez International Airport Jorge Chávez International Airport serves as a vital gateway for travellers and cargo, welcoming more than 20 million international and national passengers every year. With such a high flow of people, ensuring the safety and security of passengers and airport personnel becomes crucial. Recognising this need, RecFaces collaborated with airport authorities to implement their state-of-the-art Id-Guard solution and help ensure the safety of the facility. Enhanced security measures The solution's features enable airport authorities to prevent suspicious individuals from accessing the site The implementation of Id-Guard has significantly enhanced security measures, allowing for proactive monitoring and rapid response to potential security threats. The solution's features enable airport authorities to prevent suspicious individuals from accessing the site, thereby safeguarding the safety of passengers and staff. Highest level of security “Airport representatives felt the need for facial recognition to strengthen the security structure within the airport as a whole,” notes Maria Kazhuro, Business Development Director for the LATAM region, RecFaces. Maria Kazhuro adds, “Our goal was not only to provide the highest level of security but also to simplify work processes for security guards. We can confidently say that the installation of an ID guard has significantly improved security in the facility. Now both airport visitors and employees can be sure that they are under even greater protection than before.” Id-Guard facial recognition The deployment of Id-Guard at the Peruvian airport demonstrates RecFaces' dedication to excellence and innovation in the field of facial recognition technology. As airports worldwide continue to prioritise security and passenger experience, RecFaces remains at the forefront of delivering advanced biometric solutions tailored to the evolving needs of the aviation industry.


Round table discussion
2025 is likely to see further advancements in artificial intelligence, with potential impacts on various aspects of society, including the security industry. The new year will also require security professionals to adapt to changing market conditions and develop contingency plans for unforeseen events. Industry changes will accelerate and challenge everyone in the security market to keep up. Making specific predictions for the new year can be a struggle, but we asked our Expert Panel Roundtable: What will be the big news for security in the year ahead?
Protecting access control data is a core concept when it comes to safeguarding information assets, maintaining trust, and ensuring smooth operations. Guarding access to data also ensures compliance with regulations, prevents accidental misuse, and streamlines workflows. We asked this week’s Expert Panel Roundtable: What safeguards are in place to avoid unauthorised retrieval of access control data?
Machine learning (ML) is a field within Artificial Intelligence (AI) and one of the more common buzzwords in the physical security market. ML focuses on building computer systems that can learn and improve on their own, without being explicitly programmed for every scenario. Machine learning is poised to revolutionise physical security by offering a more proactive, data-driven approach to securing people and assets. We asked this week’s Expert Panel Roundtable: What is Machine Learning (ML) and how can it benefit physical security?
White papers

Machine Operator Authentication
Download
Understanding key control systems and best practices
Download
Smart surveillance in the workplace
Download
How end-to-end video security solutions can help your organisation with social distancing
Download
How to overcome the storage challenges of adopting surveillance AI
Download
7 proven solutions for law enforcement key control and asset management
Download
Physical access control
Download
Security practices for hotels
Download
Best practices for asset management
Download
Securing care closer to patients
Download
Machine Operator Authentication
Download
Understanding key control systems and best practices
Download
Smart surveillance in the workplace
Download
How end-to-end video security solutions can help your organisation with social distancing
Download
How to overcome the storage challenges of adopting surveillance AI
Download
7 proven solutions for law enforcement key control and asset management
Download
Physical access control
Download
Security practices for hotels
Download
Best practices for asset management
Download
Securing care closer to patients
Download


Using artificial intelligence (AI) to automate physical security systems
Download
A modern guide to data loss prevention
Download
7 proven solutions for law enforcement key control and asset management
Download
The truth behind 9 mobile access myths
Download
Access control system planning phase 2
Download