Check out our special report on Artificial Intelligence
Software House Web-based Client
Product Profile
Remote access control from anywhere
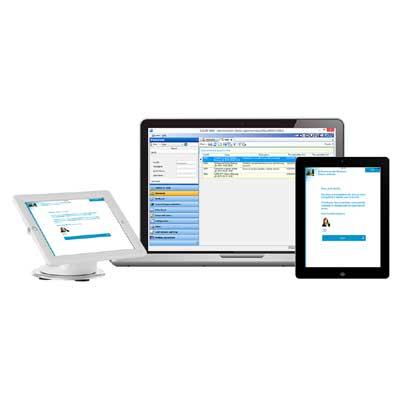
Built on a cybersecure web platform, the Software House C•CURE 9000 Web-Base client lets you manage personnel and monitor alarms from anywhere in the world on any PC with an internet browser. With an adaptive interface, you get the information that you need when you need it.
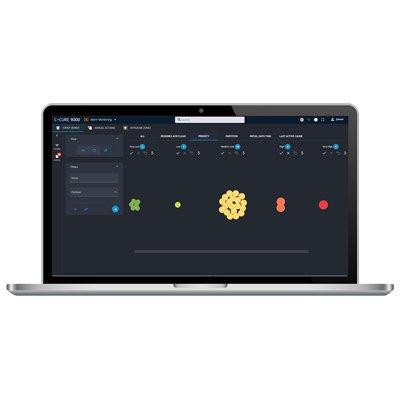
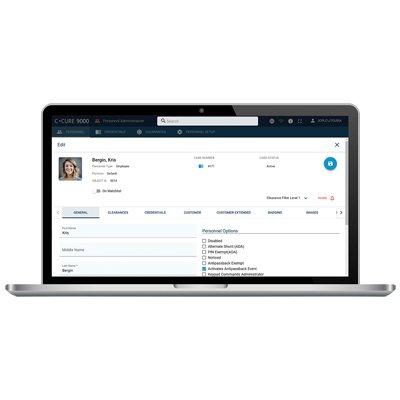
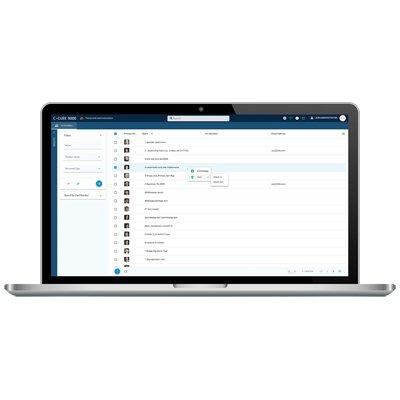
The C•CURE 9000 Web-Base client allows you to easily perform tasks such as configuring, editing, and viewing personnel records and user credentials, and assigning clearances and roles. Alarm monitoring is also made easy with color-coded bubble images for a visually dynamic user experience. Along with the Event Viewer, manual actions and intrusion zones have been designed to handle core alarm management functions for critical infrastructure projects.
Balancing security responsibilities
Customize what employees can view based on their roles within an organization using Web Views. This allows you to streamline productivity and balance both responsibility and workload. Corporate security administrators can delegate control to individual department managers allowing them to grant access in the physical areas for which they are responsible.
Customization for enhanced user experience
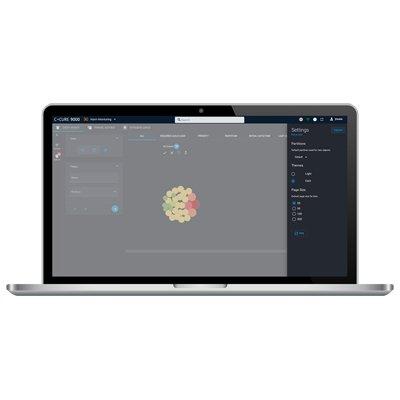
With the C•CURE 9000 web-based client, you can dynamically change the appearance of personnel screens, customizing the user interface to show different tabs, columns, and fields based on a user’s role within the organization. Simply drag and drop from a list of more than 100 fields to show only the fields you need to see, streamlining and enhancing the user experience. A responsive layout automatically adjusts and adapts to device screen size and orientation.
Technical Specification
| Make | Software House |
|---|---|
| Manufacturer | Software House |
| Category | Access Control>Access control software |
| Model code | C•CURE 9000 |
| Central / Remote Monitoring | Yes |
| Web-enabled software | Yes |
| System Requirements | Web Browser: Microsoft Edge v89 and above, Chrome v88 and above, Firefox v87 and above, Safari (v13) and above |
| Additional info |
|
You might be interested in these products
Related Whitepapers
Open credential standards and the impact on physical access control
System design considerations to optimize physical access control
Maximising enterprise security systems in the cloud
One system, one card
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadEnhancing physical access control using a self-service model
DownloadHow to implement a physical security strategy with privacy in mind
Download