Ihar Kliashchou

Ihar Kliashchou
Chief Technology Officer, Regula Forensics (Regula)Ihar Kliashchou is the Chief Technology Officer at Regula. Previously Ihar Kliashchou was the Head of Software Development Department at Regula.
News mentions
With the recent update of its Document Reader SDK, Regula became the first identity verification (IDV) vendor to make it possible to verify all the dynamic security features of documents in...
Regula, a global developer of forensic devices and identity verification solutions, now has 15,000 templates in its identity document template database, the most comprehensive in the world. Thi...
With its latest update, Regula Document Reader SDK, a comprehensive software solution for identity document verification, ensures 100% support for the new ISO/IEC 39794-5 standard regulating the...
Leveraging its decades-long expertise in identity verification, Regula has made its advanced document verification software fully compatible with a wide range of third-party ID scanners and passport r...
Regula, a global developer of forensic devices and identity verification solutions, and CacaoTech, a pioneering technology consulting company in Ecuador, partnered to innovate the document signing pro...
Regula, a global developer of forensic devices and identity verification solutions, has improved the onboarding process for Maza, a fintech company dedicated to providing new immigrants in the U.S. wi...
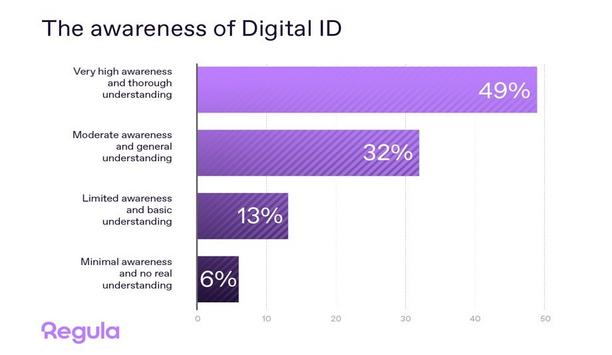
As more countries adopt the concept of digital identity, regulators are keen to showcase their plans and successes. But what do businesses think about this shift? To find out, Regula, a global develo...
The GSMA, a global organisation that conducts the world's largest exhibition and conference for the mobile ecosystem across different continents — the annual Mobile World Congress (MWC) —...
In a landscape saturated with staggering statistics, the need for innovative solutions to safeguard against the usage of stolen identities becomes more pronounced. The gravity of identity-related cr...
Before adopting an IDV system, it’s imperative to conduct thorough testing, especially for large-scale businesses. However, it is nearly impossible to obtain a reliable set of IDs with real NFC...
Regula, a global developer of forensic devices and identity verification solutions, has reached another milestone in enlarging its identity document templates database. The world’s largest comm...
According to Regula’s survey, 65% of organisations worldwide use digital document verification as one of their main methods of identity checks. And 94% of those who haven’t yet, plan to em...
According to Regula’s survey, for more than a quarter (28%) of organisations around the world, compliance and legal requirements are the major reason for implementing an identity verification so...
Fraudsters use many techniques to forge a document, and photo manipulation or replacement is not a rare one. For instance, they can morph a new picture and attach it to a valid document. The options a...
ID scam is on the rise in Africa. According to a survey conducted by FICO, a prominent analytics software company, in 2022, every seventh person experienced an identity fraud incident in South Africa....
Artificial intelligence can be used to create increasingly realistic and convincing deepfakes, making it more difficult to distinguish between genuine and manipulated content. Fake biometric artefacts...
In the age of sophisticated identity fraud, including fraud enabled by artificial intelligence (AI), it’s of paramount importance to establish a comprehensive and highly diverse verification pro...
A global survey conducted by Regula together with Sapio Research company from December 2022–January 2023 has revealed that the impact of identity fraud varies for organisations in the Financial...
Many companies struggle to implement and integrate a bunch of different solutions covering different parts of the IDV process. In fact, according to Regula’s survey, 40% of organisations cite th...
Key people from Regula Forensics (Regula)
Security experts
Using artificial intelligence (AI) to automate physical security systems
DownloadA modern guide to data loss prevention
Download7 proven solutions for law enforcement key control and asset management
DownloadThe truth behind 9 mobile access myths
DownloadAccess control system planning phase 2
Download