Articles by Larry Anderson
Dark video images contain little or no information about the subject being surveilled. Absence of light can make it difficult to see a face, or to distinguish the color of clothing or of an automobile. Adding light to a scene is one solution, but there are also new technologies that empower modern video cameras to see better in any light. We asked this week’s Expert Panel Roundtable: what impact does lighting have on the performance of video systems?
If one employee stands less than six feet away from another employee, a fob attached to a lanyard around his or her neck emits an auditory beep – an immediate reminder to observe social distancing. If an employee were to be diagnosed with COVID-19, a cloud-based database provides a record of who at the company the sick employee had contact with. These capabilities of HID Location Services ensure social distancing and provide contact tracing to enable companies to return to work safely. Th...
Artificial intelligence (AI) and machine learning have made a big splash in the physical security market, transforming video analytics to a new level of accuracy. In fact, the terms have become common buzzwords throughout the industry. However, the potential for AI and machine learning to impact the physical security industry goes far beyond their ability to improve video analytics. We asked this week’s Expert Panel Roundtable: Beyond better video analytics, how can artificial intelligence...
The advent of a truly new market for the physical security industry is a rare occurrence. Particularly rare is a new market that is both fast-growing and provides an environment that is not just conducive to application of physical security technologies but that actually demands it. Such is the case with the market for legalised marijuana. We asked this week’s Expert Panel Roundtable: what are the security challenges of protecting the cannabis industry?
A shift toward touchless devices during the coronavirus pandemic has been a boon to the biometrics sector. Another factor in the recent increase in use of biometrics is lower prices, which are a symptom of a maturing market and of new technology capabilities. Increasingly, integration of biometrics with access control and other security systems is expanding use cases and sales numbers. For additional insights, we asked this week’s Expert Panel Roundtable: What are the new trends and opport...
Within days, a rule will take effect that bans from U.S. government contracts any companies that “use” video products from Chinese companies Hikvision and Dahua. The Federal Acquisition Regulation (FAR) rule implements the “blacklist” (or “Part B”) provision of the National Defense Authorization Act (NDAA), which is understood in the security industry as prohibiting dealers and integrators that do business with the federal government from selling Chinese-made...
As a cloud-based platform for service providers in the security, smart home and smart business markets, Alarm.com has adapted quickly to changing conditions during the coronavirus pandemic. In the recent dynamic environment, Alarm.com has kept focus on supporting their service provider partners so they can keep local communities protected. “We moved quickly to establish work-from-home protocols to protect our employees and minimise impact on our partners,” says Anne Ferguson, VP of...
The emergence of smart cities provides real-world evidence of the vast capabilities of the Internet of Things (IoT). Urban areas today can deploy a variety of IoT sensors to collect data that is then analysed to provide insights to drive better decision-making and ultimately to make modern cities more livable. Safety and security are an important aspect of smart cities, and the capabilities that drive smarter cities also enable technologies that make them safer. We asked this week’s Expert...
Retrofit projects provide new levels of physical security modernisation to existing facilities. However, retrofits come with their own set of challenges that can frustrate system designers and defy the efforts of equipment manufacturers. We asked this week’s Expert Panel Roundtable: What are the biggest challenges of retrofit projects, and how can they be overcome?
The general public doesn’t give much thought to the important role of security officers in creating and promoting safer environments. The low-profile work of security officers is vital to protecting people, places and property. During the pandemic, newer aspects to that role have emerged. Security personnel have been called on to perform diverse tasks such as managing queues at the supermarket, safeguarding testing centres and hospitals, ensuring food deliveries, and supporting police pa...
Trends in the alarm industry point to a need for a software system that accommodates business patterns such as recurring monthly revenue (RMR). Workhorse Service Company provides a software that combines customer relationship management (CRM), enterprise resource planning (ERP) and field service management (FSM) into a “cradle-to-grave” system designed specifically for the alarm industry. “Making an alarm sale is different than making a CCTV sale, and the processes for the sal...
The first half of 2020 has been full of surprises, to say the least, and many of them directly impacted the physical security market. The COVID-19 pandemic created endless new challenges, and the physical security market has done our part to meet those challenges by adapting technology solutions such as thermal cameras and access control systems. In the second half of 2020, we can all hope for a return to normalcy, even if it is a “new normal.” In any case, technology will continue t...
Returning to work after the global pandemic will not be business as usual, and security systems are an important asset when it comes to helping to keep occupants and buildings safe. For example, video analytics can provide insight into how spaces have previously been used and can help to predict where and when occupants encounter each other or congregate. These foot-traffic patterns can inform settings for a variety of devices – like ventilation and temperature controls – and even he...
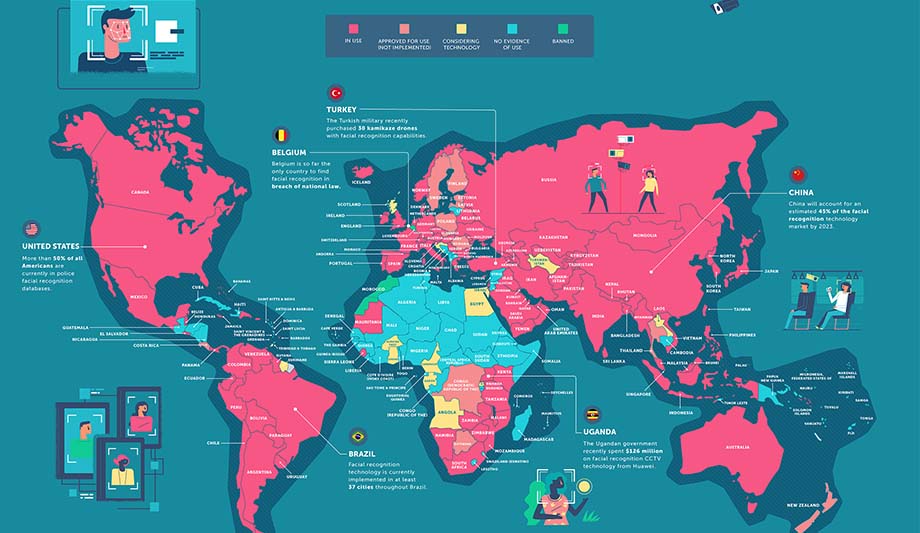
Governments around the world use facial recognition for applications such as identifying persons on public video feeds. The technology is also used by police for internal databases and as a component of ID verification for elections and/or airport security. In fact, the use of facial recognition technology is increasing globally. Surfshark, provider of virtual private networks (VPNs), collated the latest data on face surveillance around the world and distilled it into a map that shows which co...
Traditionally, dealer-installers and/or integrators provide the front line of support to end user customers after a sale. Because integrators assemble and provide the “solution” – often using products from multiple manufacturers – they are most familiar with the total system and can troubleshoot any problems. However, manufacturers may be better equipped to deal with specific problems after a sale and also to provide a variety of resources to end-users. It’s a delic...
Sooner or later (hopefully sooner), the novel coronavirus global pandemic will allow workplaces to reopen. But as we move into this recovery phase, there are many questions surrounding the transition. How can companies ensure facilities are in acceptable working order to reopen? How do they decide who is coming back and when? How will social distancing impact the operation of a company’s physical access control system? How can companies ensure that both visitors and employees are aware of...
Spread of the novel coronavirus has jolted awareness of hygiene as it relates to touching surfaces such as keypads. No longer in favour are contact-based modalities including use of personal identification numbers (PINs) and keypads, and the shift has been sudden and long-term. Both customers and manufacturers were taken by surprise by this aspect of the virus’s impact and are therefore scrambling for solutions. Immediate impact of the change includes suspension of time and attendance sys...
Protecting the oil and gas market is key to a thriving economy. The list of security challenges for oil and gas requires the best technology solutions our industry has to offer, from physical barriers to video systems to cybersecurity. We asked this week’s Expert Panel Roundtable: what are the security challenges of the oil and gas market?
The general public gets much of its understanding of security industry technology from watching movies and TV. However, there is a gap between reality and the fantasy world. Understanding of security technologies may also be shaped by news coverage, including expression of extreme or even exaggerated concerns about privacy. The first step in addressing any challenge is greater awareness, so we asked this week’s Expert Panel Roundtable: Which security industry technology is most misundersto...
Arteco’s VCA video analytics system is their latest new product, signalling a move from machine vision-based analytics to deep learning video analytics. A server – separate from the Arteco video management system (VMS) – manages the algorithms for the analytics. Arteco has been field-testing the product for a year and a half and had planned to launch it officially at ISC West in March (which was postponed). In lieu of the trade show launch, the company has been presenting the p...
Video management systems (VMS) have been around almost since the advent of IP cameras. During those years, VMSs have evolved from software that provides basic functionality to more user-friendly systems offering a growing list of capabilities, many of them related to analysing data as well as recording and displaying video. But the evolution is far from over. We asked this week’s Expert Panel Roundtable: What’s new with video management systems (VMS), and what are the new opportuniti...
The next step in the journey of digital transformation, the fifth generation of wireless communications technologies (5G) will have an enormous impact on mankind, and on every industry including security. In short, 5G will disrupt the way we live and work. To discuss the changes, we presented our questions to Benoît Jouffrey, VP 5G Expertise at Thales, which is at the forefront of the transformation with an emphasis on trust and security. Following are his responses. Q: In layman's terms,...
The COVID-19 global pandemic will have a profound and lasting impact on the physical security industry. It will boost adoption of new technologies to address new types of threats. It will map out a path for new involvement of physical security technologies in areas of public health. It will raise new notions of privacy and turn previous thinking about privacy on its head. And the aftermath of the pandemic will give rise to all these changes in a breathtakingly accelerated timeframe. In the wak...
We are all more aware than ever of the need for cybersecurity. The Internet of Things is a scary place when you think about all the potential for various cyber-attacks that can disrupt system operation and negatively impact a customer’s business. Because most physical security systems today are IP-based, the two formerly separate disciplines are more intertwined than ever. We asked this week’s Expert Panel Roundtable: How can cybersecurity challenges impact the physical security of a...
Cloud systems are among the fastest-growing segments of the physical security industry. The fortunes of integrators can improve when they embrace a recurring monthly revenue (RMR) model, and cloud systems are expanding the services and features manufacturers can provide, from remote diagnostics to simplified system design. But for all the success of cloud systems, there remains confusion in the market about the exact definition of “cloud”. Or does there? We asked this week’s Ex...
There was a time when men dominated the physical security industry. On second thought, that time is today. Even with increasing numbers of women entering our community, it’s an industry that is still mostly populated by men. But change is coming, and the industry as a whole is benefiting greatly from a surge in female voices. We asked this week’s Expert Panel Roundtable: What is the changing role of women in security?
The drive for learning doesn’t diminish, even in times of a global pandemic. To accommodate the demands of social distancing, more training today happens online. “We have seen unprecedented international demand for our portfolio of online training courses ranging from small installation companies to the largest organisations, across a wide range of sectors,” says Jerry Alfandari, Group Marketing Manager of Linx International Group, a U.K. training firm. “More than ever,...
Superior image quality has been the “holy grail” of the video surveillance business for several years. A transition to 4K images and a race to ever-higher pixel counts have dominated product development conversations for a while now. However, it’s now possible that the tide has turned. These days, data is sometimes more important than image quality, and increasing use of smaller-format mobile devices has helped to make image quality variations moot. As the industry changes, we...
Axis Communications has introduced a body-worn camera solution, which the company says represents a natural extension of their corporate vision, business strategy and core competence. The new body-worn cameras and other elements of the system will provide Axis new opportunities to grow by tapping into existing and new customers. The fast-growing body-worn camera market is an attractive one, and Axis sees opportunities to extend the use of body-worn cameras beyond the current core market of poli...
Even though ISC West 2020 was cancelled, many of the product introductions planned for the trade show still happened. For example, physical security and secure identification company Identiv introduced the Hirsch Velocity Cirrus and MobilisID. Hirsch Velocity Cirrus is a cloud-based Access Control as a Service (ACaaS) solution. It is an optimal solution for both end-users and integrators, with lower upfront costs, reduced maintenance, enhanced portability, and the future-proof assurance of auto...
You may also be interested in
A modern guide to data loss prevention
DownloadThe truth behind 9 mobile access myths
Download7 proven solutions for law enforcement key control and asset management
DownloadAccess control system planning phase 2
DownloadSecurity practices for hotels
Download