Check out our special report on Cybersecurity
Mercury Security Intelligent Controllers
Product Profile
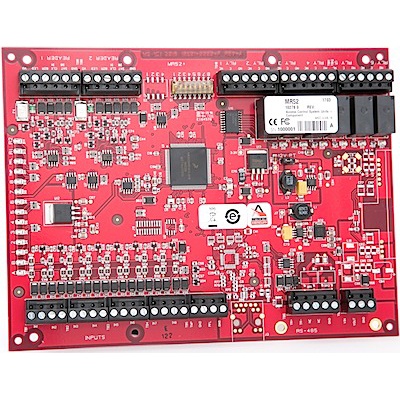
Mercury Security continues its commitment to open architecture access control with its intelligent controller platform that delivers extensive support for third-party applications, while offering advanced security and enhanced performance. Built on the Linux operating system, the new LP intelligent controllers offer the greatest flexibility for OEMs, channel partners and end customers to choose the controller configuration that best fits their needs.
Key Highlights:
- Open Architecture: High performance, reliable platform enables use of hardware with Mercury OEM partners’ software solutions
- Device Integration: Supports a wide range of third-party integrations and applications
- Enhanced Security: Embedded crypto memory chip and data-at-rest encryption provides a secured layer of protection of sensitive data.
- OSDP Protocol: Secure channel security for reader connectivity and extended applications such as biometrics and high assurance credential authentication
- Versatile Interoperability: Same reliable interface and identical footprint as the EP controllers, enabling seamless upgrades for existing deployments
For organisations seeking an open access control platform, the industry’s best reliability, cybersecurity, and an extensive device integration library, Mercury’s LP intelligent controllers are the clear choice.
Technical Specification
| Make | Mercury Security |
|---|---|
| Manufacturer | Mercury Security, part of HID Global |
| Category | Access Control>Access control controllers |
| Model code | LP4502 |
| Series | LP Intelligent Controllers |
| Controller Type | Networkable |
| Networkable | Yes |
| Electrical Specifications | Voltage: 12 ~ 24 V DC |
| Physical Specifications |
Dimensions mm: 203 x 152 x 25 Weight g: 302 |
| Environmental Specifications |
Operating Temp oC: 0 ~ 70 C (32 ~ 158 F) Operating Humidity %: 5 ~ 95 |
| Additional info |
Third Party Integration Supported
Security and Network
Card Reader Functions
|
You might be interested in these products
Related white papers
Three reasons for adopting open architecture access control solutions
Cybersecurity in keyless access management
Three essential reasons to upgrade your access control technology in 2022
One system, one card
DownloadEnhancing physical access control using a self-service model
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadHow to implement a physical security strategy with privacy in mind
Download