Technology & Trends - Access control software
The universe of biometric authentication applications is expanding rapidly invertical markets such as healthcare and retail Once used mostly to secure high-value government facilities, biometrics are now a basic tool used in a variety of vertical markets. This article will look at some of those opportunities. For healthcare organisations, for example, biometric authentication is being used for secure medical dispensing to streamline workflow and control drug diversion, and f...
NCS4’s research has mainly been on professional sports venues, but they alsodevelop best practices for all levels of sports – including high schools and colleges Some of the most profound changes in the way sporting events are secured have come about since the terrorist attacks on Sept. 11, 2001. A realisation that stadiums could be a target for terrorists has transformed sports security into a highly sophisticated profession that works closely with local and n...
As we face 2016, identity management has become more critical to successful security operations. Recent acts of terrorism, border security issues, and the refugee crisis are just a few examples that remind us of the potential risks we face today. As a result, identity management is now firmly cemented into prospective security models across the public and private sectors. In recent years, organisations and government bodies worldwide have begun to rely increasingly on biomet...
Facial and body behavior analytics can identify people “without interferingwith the pace of life” Biometrics companies throughout the security marketplace are expanding the functionality of their systems for a variety of uses. This article will take a look at what several companies are up to. SRI International’s identity solutions seek to bring convenience, speed and security to existing workflows. SRI’s Iris on the Move (IOM) biometric systems ca...
2015 has been a huge success for key and asset management company Traka. The manufacturer is predicting growth between 20 and 30 percent. It attributes a large part of its success to the extensive work completed in previous years in the U.S. markets, as the foundations set are now coming to fruition. However, Traka has also encountered a real culture shift within the industry. Where previously key management systems and intelligent lockers for asset management were seen as a...
HID Global is looking forward to a long term investment in a complete range of secure identity solutions. Also, focusing on its global partnership program will be on the agenda. An increasingly global market for identity and access management is undergoing very rapid development due to technological advances, particularly in communications, where digital mobile solutions are experiencing strong demand. The year 2015 was a good one for HID Global, which has a strong global position and is invest...
Farpointe Data started 2015 in newly relocated offices featuring a larger, more proficient layout that added new manufacturing equipment and increased its production and inventory capabilities. Shortly into the year, Farpointe introduced new WRR-22 and WRR-44 433 MHz receivers that use either 2-button or 4-button transmitters to open two or four different doors from ranges up to 200 feet (61 m). Each button outputs transmitter data over separate Wiegand outputs, yet the receiver installs just...
2015 was a notable year for Quantum Secure, culminating with the company becoming part of HID Global. Growth was seen in several sectors for us, led by the adoption of our SAFE software solutions in the finance and aviation markets, among others. For the industry in general as it relates to Quantum Secure, predictive security became a more prevalent theme as organisations were tasked with not only providing more data but making sense of the data for use in improving security operations. Another...
As the world faces new threats and challenges at the end of 2015, the security market looks more and more attractive for companies and employees around the world. Digital technology increasingly is replacing a traditional physical security approach, upgrading old-school analogue alarms and CCTV. Attractive security projects From AxxonSoft’s point of view, security projects seem very attractive because they normally can bring up to 30% profit for a standard security system installation....
The KISI system has been installed in hundreds of tech startups in New York City and is currently targeting other areas of the US Based in Brooklyn, New York., KISI Inc. is a relative newcomer to the access control industry, targeting tech companies and co-working spaces for it cloud-based system. With its first round of funding secured in March 2015, the company partnered with Cushman & Wakefield to roll out its mobile access control solution at the real estate firm&rsquo...
While the access control market typically moves at a near glacial pace, 2015 brought quite a bit of news to the marketplace, including the rise in advanced biometrics, the development of more and more mobile applications for access control and important acquisitions that put smaller manufacturers on the map. For Vanderbilt, 2015 was a big year as we brought the Siemens Security Products business into the fold, building our global brand and awareness of our award-winning solutions that have been...
The extraordinary global adoption of fingerprint based solutions, from mobile devices to credentials, will continue to expand and touch new markets in 2016. The trend to move away from passwords and PINs is really building momentum in logical and physical access. Widespread use of biometric security The security industry in 2015 continued to improve, along with the overall economy. Regulatory agencies are taking the lead as two-factor authentication is becoming a more mainstream concept. From...
Many security solutions available today have the problem of being insufficiently open, offering very limited flexibility. Integrating third-party products is practically impossible. Customers therefore very often have to make a long-term bet on just one vendor. Upgrading or expanding security systems is often complex, expensive and time-consuming. But the industry is changing. Initiatives like open standards and cooperation between suppliers are emerging to help companies react faster to changin...
2015 has been an eventful year for the physical security industry. As 2016 looms, the pace of industry change shows no sign of decreasing. Seeking insights into the state of the physical security market at year-end, SourceSecurity.com this month is publishing dozens of 2015 Review and 2016 Forecast articles submitted by manufacturers, integrators and other industry leaders. Taken together, the articles portray a mostly optimistic view of the industry’s present, and an...
SourceSecurity.com’s Expert Panel had a lot to say in 2015 on a variety of topics in our Roundtable discussions. Not surprisingly, the discussion topics that have generated the most interest (in terms of how much visitor traffic they generated) are the same hot topics we hear about every day in the industry. Our very most-clicked-on Roundtable discussion in 2015 was about the impact of video on privacy rights. Other hot topics that made the Top-10 list of Roundtable d...
Throughout 2015 the security industry saw the appearance of numerous mobile credential offerings, signalling the “beginning of the end” of card-based identity, and strengthening of mobile offerings in general. Overall, the security industry enjoyed healthy growth throughout 2015, as reflected in the better-than-index performance of most publicly traded security company stocks. Cloud companies, in particular, saw the market turning their way, as a number of security vendors ha...
Automated procedures reduce manual errors & help meet regulatory requirements End user demands are growing exponentially every day. Whether it is managing who has access to buildings or areas and when, recording events on video, managing incidents, meeting compliance requirements or demonstrating proof of compliance, the list goes on and on as to what end users must manage to keep their buildings, assets and people safe. Physical security equipment and an effective securi...
How do you get all of your various vendors, services, resources, manpower, and technology to integrate and work together? Creating an efficient operating environment in physical security is no small feat - especially when the organisation undertaking such an endeavour has a nationwide presence. How do you get all of your various vendors, services, resources, manpower, and technology to integrate and work together? How do you aggregate all of the data being recorded into in...
Organisations can develop security master plan internally or use the assistance of an independent security consultant Whether it’s a college campus, a healthcare facility or a large corporation, organisations often tackle issues related to security management, operations, programs and technology in a reactionary manner. They often fail to consider the need to plan and develop a written roadmap to define and provide direction for the big picture of their security programm...
The pre-seminar will also offer educational sessions on cutting-edge subjects It is that time of the year again, when security industry stalwarts gather together at ASIS to showcase the latest in physical security systems and other technological innovations. The event will focus on domestic threats as well as intelligence gathering tools to protect organisations against social media threats. The organisers of the ASIS International 61st Annual Seminar and Exhibits — ASI...
IP is here and is continuing to proliferate in the security industry and its next major advancement is in pure IP access control IP technologies in the security industry are nearly ubiquitous today. End users and integrators have adopted and embraced IP cameras, building automation systems, wireless mesh networks, alarms, monitoring, and regularly view all of these technologies from the palm of their hand, on their smart phone. The technologies are easier to install, oft...
9-11 caused a sharp refocus of attention on security assessment and risk management Fifteen to 20 years ago, security was a relatively sleepy, small-time business. Companies typically hired a guard or two to walk around the property, usually at night, sometimes during the day. If a guard spotted someone who wasn’t supposed to be there, he (it was usually a he) ran the person off. Larger companies had more sophisticated video and access control systems, but those system...
More and more commercial buildings today are replacing mechanical keyed locks with card access systems. The basic reason is familiar to security professionals: card systems, once installed, cost less to manage and maintain. “When people are let go, if you don’t get their keys back, you have to rekey the locks and give everyone new keys,” says Brett St. Pierre, director, education solutions with Austin, Texas-based HID Global. “With a card system, all y...
Customers are seeking systems integration as a solution rather than a component The migration of access control systems from conventional technology to IP has had a positive impact on TDSi’s sales for IP equipment. Increasing demand for biometric and face recognition applications has also paved the way for better and improved access control systems. According to John Davies, Managing Director of access control company TDSi, the state of any given market depends on...
A US Department of Homeland Security investigation showed that undercover agents defeated airport screening in 95 percent of cases by smuggling mock explosives and weapons past checkpoints. With admirable transparency, U.S. Office of Inspector General (OIG) has described how so-called “Red Teams” posed as regular passengers and exposed inadequate measures at some of the busiest airports across the United States. The revelations came a few days before Body Search 2...
Biometrics is most useful as an additional level of authentication — determining that you are who you say you are Over the years, the growth of biometric security technology has faced challenges of cost and pushback from users. Prices have been higher than more traditional technologies. In addition, users did not advocate storage of their personal biometric data by employers or the government. “I believe this is changing,” says Rueben Orr, CPP, vice preside...
Just how big is the home automation industry? One way to tell is by looking at the sheer number of companies – large and small—that have rushed to enter this fast-growing space. They include some of the world’s largest corporations – Apple and Google – along with the nation’s biggest cable and telecom companies – Comcast and AT&T. It includes big names in security like Honeywell and ADT. Then there are less known, but fast growing, contenders such as...
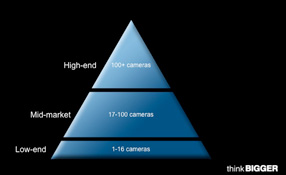
See bigger image Old pyramid w # of cams It’s clear that the network-based physical security industry has matured rapidly over the past few years. As the technology and other components of security solutions have advanced, so too have the customer’s expectations. Security solution companies must evolve in order to meet these new expectations. This requires an understanding of both the technology and the customers’ motivators, issues and hot buttons. Arr...
When asking exhibitors at IFSEC International 2015 about what drives their markets, many cite system integration as a key factor. And they want more of it. Integration as business “driving force” For example, John Davies of TDSI says customers are now seeking out system integration. “They want a solution rather than components, such as linking access control with building management systems or with an organisation’s IT network to control access to its computers,”...
Security beyond its traditional boundaries is a big theme at IFSEC 2015 The security landscape is changing. Touring exhibitors on the first day of IFSEC International in London, it seems an increasing number of vendors are offering products that go beyond what may be termed "security," offering solutions for applications such as health and safety and data collection. They are also offering more smart technology with mobile phones and tablets, and are selling smarter by tailori...
Browse expert commentaries
Related videos
OPTEX REDSCAN mini series protects The Londoner Hotel
Time challenge: installation of battery powered Aperio cylinder
IDIS launches efficient AI-powered security camera range
Verkada Command Connector for Camera Integration & Cloud Management
Hikvision One-Stop SMB Solutions
Dahua X-spans Wizmind Network PTZ Camera
Palm vein recognition
DownloadThe key to unlocking K12 school safety grants
DownloadSelecting the right network video recorder (NVR) for any vertical market
DownloadPhysical access control
DownloadCybersecurity for enterprise: The essential guide to protecting your business
Download