DSX Active Directory Authentication for authenticating operator logins
Technical Specification
- Make: DSX
- Model code: Active Directory Authentication
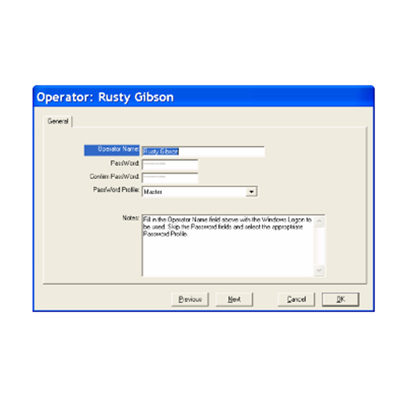
WinDSX SQL can now utilize complex logins and passwords facilitated by Active Directory in Windows™. Operator Logins can be authenticated by Active Directory instead of WinDSX. To configure this, the WinDSX SQL Operators use the same Login Name as they do in Windows™. Their Login name is entered like always under Operator Passwords. The Operator is assigned a Password Profile but is not assigned a Password. When WinDSX SQL receives a login from an operator that does not have a password in it’s database it sends the login request to Active Directory (AD) for authentication. If AD authenticates the operator they are given access to WinDSX SQL according to the Password Profile assigned to them.
Read more| Make | DSX |
|---|---|
| Manufacturer | DSX - Europe Ltd. |
| Category | Access Control>Access control software |
| Model code | Active Directory Authentication |
| Additional info |
WinDSX SQL can now utilize complex logins and passwords facilitated by Active Directory in Windows™. Operator Logins can be authenticated by Active Directory instead of WinDSX. To configure this, the WinDSX SQL Operators use the same Login Name as they do in Windows™. Their Login name is entered like always under Operator Passwords. The Operator is assigned a Password Profile but is not assigned a Password. When WinDSX SQL receives a login from an operator that does not have a password in it’s database it sends the login request to Active Directory (AD) for authentication. If AD authenticates the operator they are given access to WinDSX SQL according to the Password Profile assigned to them. |
You might be interested in these products
Related Whitepapers
Access and security in the age of hybrid working
Cybersecurity in keyless access management
The critical role of access control in K-12 school security
One system, one card
DownloadAligning physical and cyber defence for total protection
DownloadUnderstanding AI-powered video analytics
DownloadEnhancing physical access control using a self-service model
DownloadHow to implement a physical security strategy with privacy in mind
Download